SQL Injection for eBay

Timing of events:
- Date of discovery 05/19/2014
- EBay bug report date: 05/19/2014
- Bug fix date: 05/24/2014
While searching for vulnerabilities on eBay, I accidentally stumbled upon the domain 3.ebay.com.au and its mirror imode.ebay.de/ , imode.ebay.fr/ . It seems that it was a domain for users of the old " Troika " phones, but I'm not sure. (Note: Troika is a mobile operator that was bought by Vodafone)
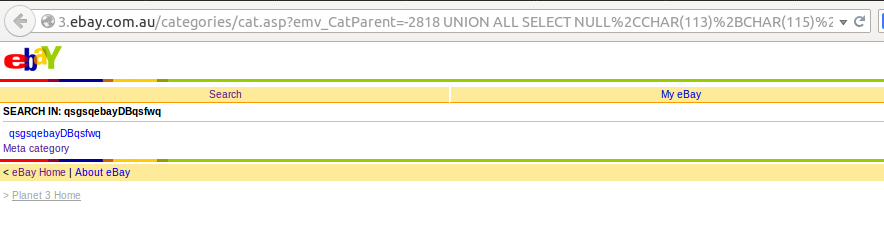
On the third line of the page I found the link - "Categories". In this section, there were several drop-down lists in which the “sub-categories” of the product were contained (Whoever visited eBay before would understand what I mean).
Immediately, it became clear that several $ _GET parameters would be used there, so I just put an apostrophe at the end of the first emv_CatParent parameter.
Fantastic, but incomplete page returned. This meant that in front of me was a typical blind SQL injection.
')
Further, during the exploration of the vulnerability, I came to the conclusion that eBay uses Microsoft SQL Server, and this became a problem for me. Since I have no experience with MSDB, I had to use sqlmap and do everything through it.
The first thing I did was scan the parameter that I found to make sure my guess was correct.
And then it started ...
[INFO] GET parameter 'emv_CatParent' is 'Generic UNION query (NULL) - 1 to 10 columns' injectableAnd that was not all:
[01:34:38] [INFO] GET parameter 'emv_CatParent' seems to be 'Microsoft SQL Server/Sybase stacked queries' injectableThis means that there was an opportunity to read and write files. Having looked through some more column names, I stopped my research and went to write a bug report.
Screenshots:
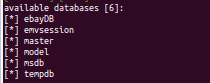
EbayDB database
Database
Available tables in "ebayDB".
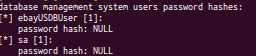
The list of columns in the "payment_old" table.
No hash for admin user? .. And you, I look risky guys.
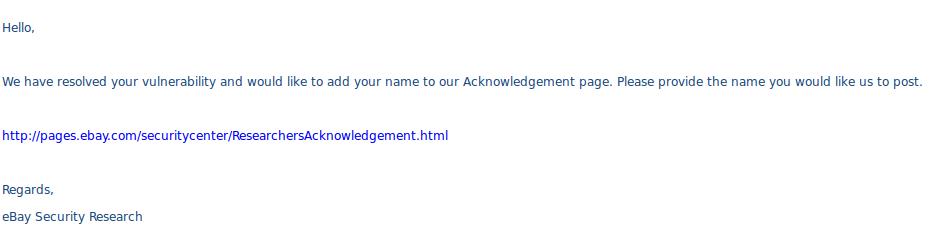
And lastly a letter from eBay.
UPD.
Fixed bug fix date, thanks to ghosthope and MKrivosheev
UPD 2.
Thanks for the help in correcting errors in the text customtema and lliyplliuk
Source: https://habr.com/ru/post/225269/
All Articles