Exploiting the conceptual flaws of wireless networks

Wireless networks surround us everywhere, around millions of gadgets, constantly sharing information with the World Wide Web. As you know, information rules the world, which means there may always be someone very interested in the data that your wireless devices transmit.
This may be a criminal interest, or a legitimate security research company with all preconditions. For such researchers, this short article was written, because an extra point of information collection during pentest will not interfere.
')
1. The fundamental insecurity of Wi-Fi networks

Few people think, but Wi-Fi networks are unsafe at their most basic, or rather there is a terrible imbalance between the security of the access point and the client of wireless networks. Much attention is paid to the fact that no outsider can connect to the access point, create methods for encrypting the connection, introduce filtering lists for various hardware parameters, but absolutely nothing has been done to protect client devices from being forced to connect to an unwanted access point. What is the main problem of client connection? In the only sufficient authorization sign of connection to the access point known to the client - SSID. We will exploit this fundamental flaw today.
2. How to impose your access point on the “victim”?
There are three ways to reduce the victim’s involvement in the interception process:
a) Open access point

The most primitive option, calculated by an ordinary hipster who is tired of sitting through the mobile Internet and he decided to look for where to stick to the freebies.
Using this method will give you a steady influx of completely uninteresting users, among whom are unlikely to be employees of the company whose security testing you are doing.
b) An open point with a multi-SSID (DD-WRT firmware, for example, can do such tricks) in which the most common names of open access points are crammed, such as asus, default, Dlink, Beeline_wifi_free and the like.
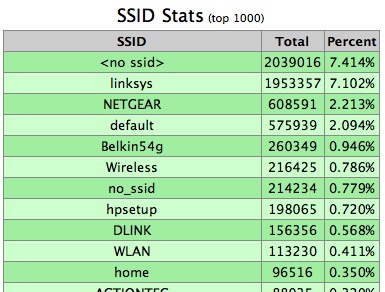
It is a variation of the previous one, with the only difference that there appears some probability of automatic connection of the victim's device to the old memory (as noted earlier, the coincidence of the SSID memorized by the client is sufficient and the only condition for connecting to an open point). Coverage has grown slightly and there is already some chance of catching an interesting clientele, but again, in the case of real work it is unlikely
c) Using KARMA.
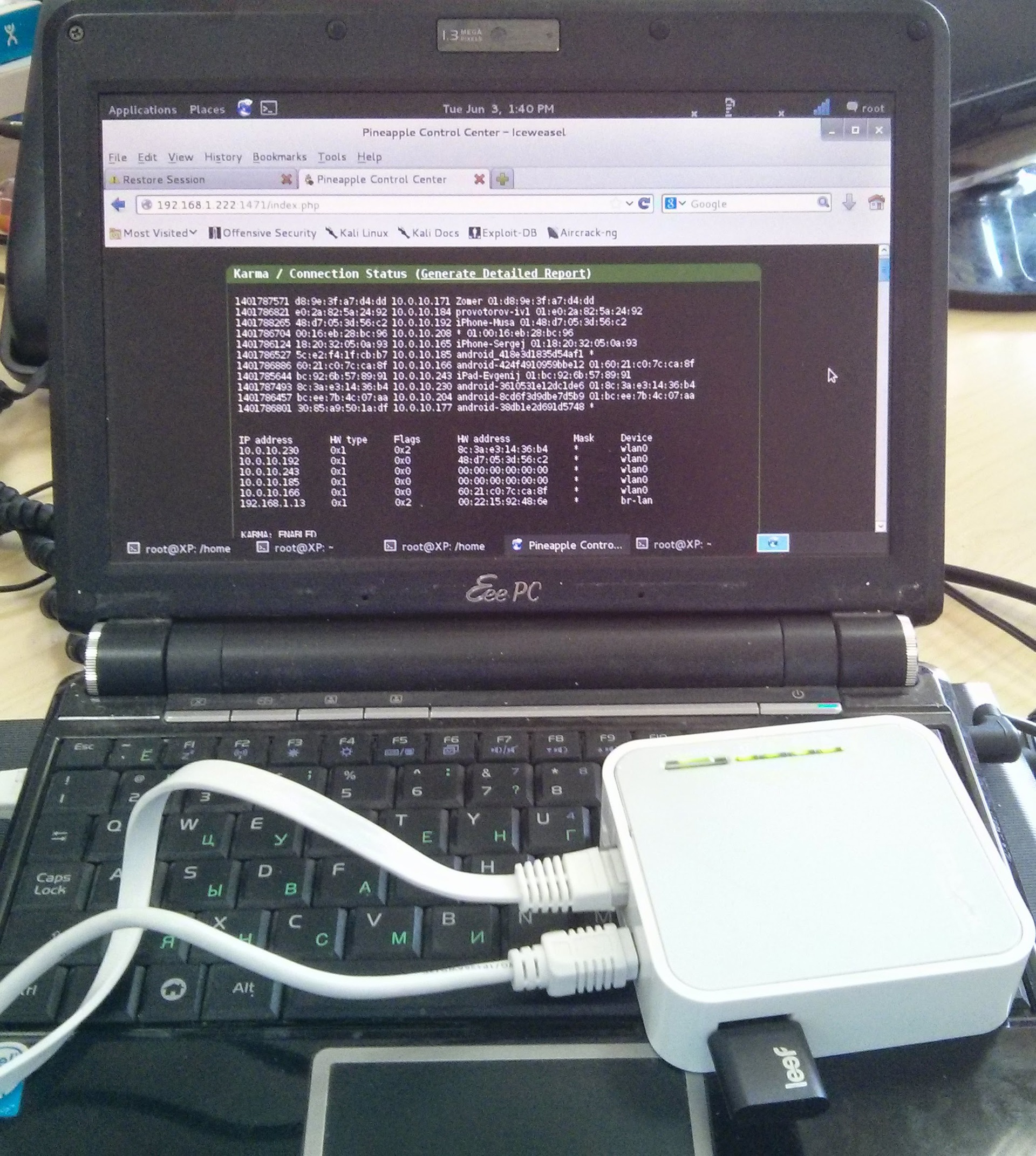
The most interesting thing for the sake of which this article was actually started is that this software comes as part of the WiFi Pineapple hardware-software complex designed to hack and intercept wireless networks in semi-automatic mode. Fortunately, the firmware of the original device, after a certain shamanism, gets up on super-cheap routers, which, in combination with an old netbook, gives a decent station with a high probability of intercepting clients of wireless networks. How does this ( KARMA ) work? Each client device in the standby mode constantly sends out so-called beacons trying to find one of the previously stored wireless networks next to it. A device running KARMA intercepts these beacons and appears to clients as the access point it is looking for. At the same time, it does not matter at all what security parameters, passwords and encryption type of the point memorized by the device - the connection will happen unnoticed and over an open channel. All this is wonderful SSID magic and some dark shamanism of the creators of such a wonderful product. The probability of associating a victim with such an access point is higher, the better reception is between them, but it is very high and all modern wireless devices are susceptible to it (although it is said that new versions of Android OS and iOS are deprived of this drawback - research suggests otherwise).
3. Conclusion - reap the rewards.
As soon as the client jumped into your access point and went through it to the Internet, you have an abyss of possibilities for intercepting and stealing data, ranging from intercepting open traffic using tcpdump, dsniff and similar methods, to intercepting secure ssl traffic through sslstrip and using the method of changing pages.
Of course, you cannot count on 100% success - not every “fishing” ends with the result in the form of ready-made passwords or at least hashes, more often you will get access_token authorization of mobile applications through OAuth2.0. There are ways to exploit this data in nature, but this is a topic for another big conversation.
There are few imputed security methods - I don’t suggest disabling wireless networks, but getting into the Karma coverage area can be determined by a sudden connection of your phone to an access point, which is not nearby, and the connection is password-free, and you just remember that the point is closed by WPA2 encryption .
To maximize the likelihood of success "fishing" is to combine all three ways to bait.
Source: https://habr.com/ru/post/225059/
All Articles