Wi-Fi networks: penetration and protection. 1) materiel

Weather forecasters predict that by 2016 the
With this trend, it can
')
With this series of articles, I want to put together descriptions of existing protection technologies, their problems and workarounds, so that at the end the reader will be able to tell himself how to make his network impenetrable,
The article, as it was written, grew from 5 pages to 40, so I decided to break it apart. This cycle is not just an instruction, as it should and should not be done, but a detailed explanation of the reasons for this. Well, who wants instructions - they are:
Use WPA2-PSK-CCMP with a password of 12azcharacters (2000+ years busting on an ATI cluster). Change the default network name to something unique (protection from rainbow-tables). Disable WPS (just touch 10000 PIN combinations). Do not rely on MAC filtering and hiding the SSID.
Table of contents:
1) materiel
2) Kali. Hiding SSID. MAC filtering. WPS
3) WPA. OpenCL / CUDA. Pick statistics
But first - materiel.
Pass me the sugar
Imagine that you are a device that accepts instructions. Anyone can connect to you and give any command. Everything is good, but at some stage it was necessary to filter the personalities that can control you. This is where the fun begins.
How to understand who can give the command and who does not? The first thing that comes to mind is a password. Let each client pass a certain password before transferring a new command. Thus, you will only execute commands that are accompanied by the correct password.
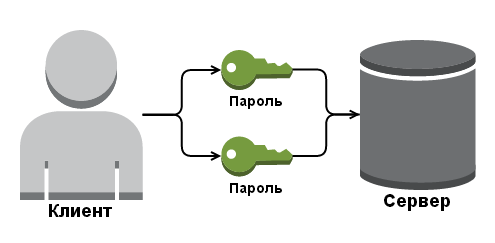
This is how HTTP (Auth Basic) basic authorization works:
AuthType Basic AuthName "My super secret zone!" AuthUserFile /home/.htpasswd Require valid-user 
After successful authorization, the browser will simply transfer a specific header for each request to a closed zone:
Authorization: Basic YWRtaW46cGFzcw== That is, the original:
echo -n 'admin:pass' | base64 # YWRtaW46cGFzcw== This approach has one big drawback - since the password (or login-password, which is essentially just two parts of the same password) is transmitted through the channel “as it is” - anyone can interlock between you and the client and get your password on a plate. And then use it and dispose of you as you like!
To prevent such a disgrace, you can resort to tricks: use any two-way encryption algorithm, where our password will be the private key, and you should never explicitly transmit it. However, this will not solve the problem - you only need to know the password once and you can decrypt any data transmitted in the past and the future, plus encrypt your own and successfully disguise yourself as a client. And given that the password is intended for a person, and people tend to use far from the whole set of 256 bytes in each character, and these characters are usually around 6-8 ... in general, the Komsomol does not approve.
What to do? And let's do what real conspirators do: at the first contact, we will invent a long random string (long enough so that it cannot be picked up while the sun is shining), remember it and will encrypt all further transmitted data using this “pseudonym” for a real password . And periodically to change this line -
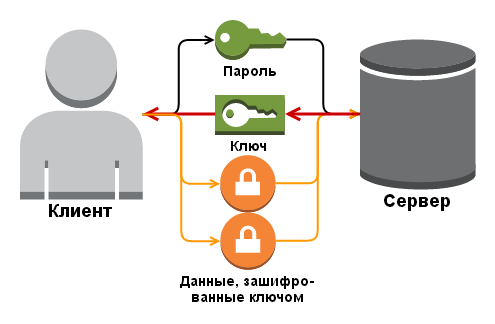
The first two transfers (the green icons in the figure above) are the handshake phase, when we first tell the server about our legitimacy, showing the correct password, to which the server responds with a random string, which we then use for encryption and transfer any data.
So, to select a key, a hacker will either need to find a vulnerability in its generation algorithm (as is the case with Dual_EC_DRBG ), or rent a hundred or two parallel universes and several thousand ATI farms to solve this problem during their lifetime. All this is due to the fact that a random key can be of any length and contain any codes of the available 256, because the human user will never have to work with it.
Such a scheme with a temporary key (session key, session key or ticket) in different variations is used today in many systems - including SSL / TLS and wireless security standards, which will be discussed.
Attack plan
Attentive readers, of course, noticed that no matter how tricky we are, we cannot get away from sending a password and a temporary key in an open or hashed form. As a result, it is enough for the hacker to intercept the transmission in this phase, and he will be able to read all the subsequent data, as well as participate in the process, inserting his five kopecks. And it is impossible to distinguish it, since all the information that the server could use to issue a temporary key or access check is based on exactly what was at the beginning of the transfer - a handshake. Therefore, the hacker knows everything the same as the server and the client, and can drive both by the nose until the temporary key expires.
Our task in hacking any program somehow comes down to intercepting a handshake, from which you can either pull out a temporary key, or the original password, or both. In general, this is quite a long time and requires some luck.
But it is in an ideal world ...
Wi-Fi Protection Mechanisms
Technologies are created by people and in almost all of them there are mistakes, sometimes critical enough to circumvent any of the best protection in theory. Below we will go through the list of existing mechanisms for protecting data transmission over the air (that is, without affecting SSL, VPN and other higher-level methods).
OPEN

OPEN is the lack of any protection. The access point and the client do not disguise the transfer of data. Almost any wireless adapter in any laptop with Linux can be set to a wiretapping mode, when instead of discarding packets not intended to it, it will record them and transfer them to the OS, where they can be safely viewed.
It is on this principle that wired networks work - they don’t have built-in protection and “crashing” into it or simply connecting to the hub / switch the network adapter will receive packets of all devices in this network segment in the open form. However, with a wireless network, you can “crash” from any place - 10-20-50 meters or more, and the distance depends not only on the power of your transmitter, but also on the length of the hacker's antenna. Therefore, open data transmission over a wireless network is much more dangerous.
In this series of articles, this type of network is not considered, since there is nothing to crack there. If you need to use an open network in a cafe or airport - use VPN (avoiding PPTP) and SSL (
https:// , but put HTTPS Everywhere , or paranoidly make sure that the lock does not disappear from the address bar if someone turns sslstrip - which, however, passwords will no longer save), and even all together. Then nobody sees your cats.WEP

WEP is the first Wi-Fi security standard. It stands for Wired Equivalent Privacy ("equivalent to protecting wired networks"), but in fact it gives much less protection than these wired networks, as it has many flaws and is cracked in many different ways, which, because of the distance covered by the transmitter, makes data more vulnerable. It should be avoided almost in the same way as open networks - it provides security only for a short time, after which any transmission can be fully disclosed, regardless of the complexity of the password. The situation is aggravated by the fact that WEP passwords are either 40 or 104 bits, which is an extremely short combination and can be picked up in seconds (this is without taking into account errors in the encryption itself).
WEP was invented in the late 90s, which justifies it, but those who still use it do not. I still consistently find at least one WEP network for 10-20 WPA networks.
In practice, there were several encryption algorithms for the transmitted data — Neesus, MD5, Apple — but all of them are somehow unsafe. Especially noteworthy is the first, the effective length of which is 21 bits (~ 5 characters).
The main problem of WEP is a fundamental design error. As illustrated in the beginning, stream encryption is done with a temporary key. WEP actually transfers several bytes of this key along with each data packet. Thus, regardless of the complexity of the key, any transmission can be revealed simply by having a sufficient number of intercepted packets (several tens of thousands, which is quite a small amount for an actively used network).
By the way, in 2004 IEEE declared WEP obsolete due to the fact that the standard “did not fulfill its goals [to ensure the security of wireless networks]”.
WPA and WPA2

WPA is the second generation to replace WEP. It stands for Wi-Fi Protected Access . Qualitatively different level of protection due to taking into account WEP errors. The password length is arbitrary, from 8 to 63 bytes, which greatly complicates its selection (compare with 3, 6 and 15 bytes in WEP).
The standard supports various encryption algorithms for transmitted data after a handshake: TKIP and CCMP. The first is a kind of bridge between WEP and WPA, which was invented while IEEE was busy creating a full-fledged CCMP algorithm. TKIP, like WEP, suffers from some types of attacks, and is generally not secure. Now it is rarely used (although it’s not clear why it’s used at all), and in general, using WPA with TKIP is almost the same as using simple WEP .
One of the interesting features of TKIP is the possibility of the so-called Michael-attack. For fast patching of some especially critical holes in WEP in TKIP, a rule was introduced that the access point is obliged to block all communications through itself (that is, “fall asleep”) for 60 seconds if an attack is found on the selection of a key (described in the second part). Michael-Attack is a simple transfer of “spoiled” packets to completely shut off the entire network. Moreover, in contrast to the usual DDoS, only two ( two ) packets are enough for guaranteed network outage for one minute.

WPA differs from WEP in that it encrypts each client's data separately. After the handshake, a temporary key is generated - PTK - which is used to encode the transfer of this client, but no other. Therefore, even if you have penetrated the network, you can only read the packets of other clients when you intercept their handshakes - each separately. Demonstrating this with Wireshark will be in the third part.
In addition to different encryption algorithms, WPA (2) supports two different modes of initial authentication (checking password for client access to the network) - PSK and Enterprise. PSK (sometimes called WPA Personal ) is a login using a single password that a client enters when connecting. This is simple and convenient, but in the case of large companies it can be a problem - let's say your employee has left and so that he can no longer get access to the network, you have to
In this cycle, the attack on WPA (2) -PSK will be discussed in detail, since Enterprise is a completely different story, as it is used only in large companies.
WPS / QSS

WPS , also
WPS allows a client to connect to an access point using an 8-digit code consisting of numbers (PIN). However, due to an error in the standard, only 4 of them need to be guessed. Thus, it suffices only 10,000 picking attempts, and regardless of the complexity of the password for accessing the wireless network, you automatically get this access, and with it in addition - this same password as it is.
Considering that this interaction occurs before any security checks, you can send 10-50 login requests via WPS per second, and in 3-15 hours (sometimes more, sometimes less) you will receive the keys
When this vulnerability was revealed, manufacturers began to introduce a limit on the number of attempts to enter (rate limit), after exceeding which the access point automatically for some time disables WPS - however, until now, such devices are no more than half from those already released without this protection. Even more - a temporary outage does not fundamentally change anything, since with one attempt to log in per minute we only need
10000/60/24 = 6,94 days. And the PIN is usually found before the whole cycle passes.I want to once again draw your attention to the fact that when WPS is enabled, your password will inevitably be revealed, regardless of its complexity. Therefore, if you need WPS at all - turn it on only when connecting to the network, and keep this backdoor off the rest of the time.
The attack on WPS will be discussed in the second part.
ps: since the topic is very extensive, errors and inaccuracies could creep into the material. Instead of shouting “the author does not understand anything,” it is better to use comments and drugs . It will only be welcome.
Table of contents:
1) materiel
2) Kali. Hiding SSID. MAC filtering. WPS
3) WPA. OpenCL / CUDA. Pick statistics
Source: https://habr.com/ru/post/224955/
All Articles