Encryption GOST 28147-89 in Acronis Backup 11.5
Hi Habr, today we will tell about the data encryption algorithm in backups and features of its use in the Acronis product line. As follows from the title, we will discuss the standard GOST 28147-89 (hereinafter referred to simply as “standard”).
Acronis Backup 11.5 is currently one of the few, if not the only backup solution (physical and virtual machines) on the Russian market that supports encryption according to GOST 28147-89 without the need to install additional encryption modules (often these modules are separate and very weighty money).

The GOST 28147-89 algorithm was developed in the USSR and is the encryption standard of the Russian Federation describing the principles of cryptographic data conversion for transmission over computer networks, individual computer complexes or computers, their encryption and the creation of digital signatures.
')
This algorithm is intended for both hardware and software implementations of encryption. It satisfies the necessary global standards for cryptographic security and does not impose restrictions on the level of secrecy of the protected information.
This standard is mandatory for organizations and companies of the Russian Federation that use cryptographic protection for data downloaded and / or transmitted through computer networks, individual computer complexes or personal computers. Therefore, the lack of support for this standard in software can be a serious obstacle to the use of this software in the enterprise. This is especially true of government organizations where compliance with standards is a key requirement for software.
The standard was translated into English and published in 1994, and is now widely used in software. Unlike his colleague, the DES algorithm adopted as the US federal standard, GOST 28147-89 (like AES) can be used more widely due to the lack of restrictions on the level of secrecy of the protected information.
This algorithm, like DES, works with blocks of 64 bits each, but this is where the similarity ends and the differences follow:
Acronis Backup 11.5 supports encryption of data in a backup, which allows you to protect user data from unauthorized access.
It supports AES encryption with a key length of 128/192 and 256 bits and encryption according to GOST 28147-89 with a key length of 256 bits. This type of encryption is available only in the Russian version of Acronis Backup 11.5, intended for users in the Russian Federation and the CIS countries.
All encryption algorithms use a randomly generated key of a user-specified size (128, 192 or 256 bits in case of choosing AES and 256 bits in case of selecting GOST 28147-89). The larger the key size, the longer it will take to encrypt the archive and the higher the degree of data security. The encryption key is then encrypted using the AES-256 algorithm, using the hash of the SHA-256 password entered by the user as the key. The password itself is not stored anywhere on the disk or in the backup file. To verify the password hash is used. Such a two-level protection scheme allows you to protect the backup data from unauthorized access, but recovering the lost password is impossible. Therefore, contacting the support service with a request to return access to the data in the encrypted archive when the password is lost is meaningless - we are physically unable to do this (well, except for 100,500 years, using the password brute force method).
The installer of Acronis Backup 11.5 automatically installs all the components necessary for encryption. The data is encrypted directly on the computer on which the backup operation takes place, and then sequentially transfers it to the backup storage: tape, network folder, etc.
Data compression can be used simultaneously with encryption. In this case, the data is first compressed and then encrypted. At the same time, the execution time of the backup procedure may slightly increase.
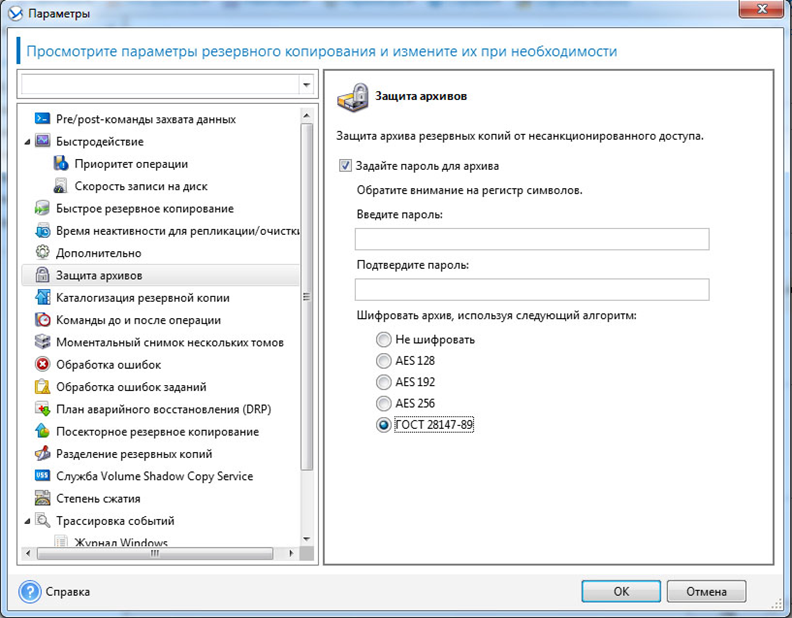
To enable the option of encrypting an archive in accordance with GOST 28147-89, when creating a backup plan, the user must go to the “archive protection” section in the “backup options” window, enable the “set password for archive” checkbox and select the appropriate algorithm.
Support for the GOST standard is part of the ideology of Acronis AnyData , which means the availability of encryption for any type of data in a backup — whether it is file archives, backup copies of physical or virtual machines, or application data.
We are ready to answer your questions regarding the implementation of the GOST standard or other encryption algorithms in Acronis products. Write in the comments what aspects should be covered in more detail (including in future articles), if this topic interests you.

Acronis Backup 11.5 is currently one of the few, if not the only backup solution (physical and virtual machines) on the Russian market that supports encryption according to GOST 28147-89 without the need to install additional encryption modules (often these modules are separate and very weighty money).

A bit of history
The GOST 28147-89 algorithm was developed in the USSR and is the encryption standard of the Russian Federation describing the principles of cryptographic data conversion for transmission over computer networks, individual computer complexes or computers, their encryption and the creation of digital signatures.
')
This algorithm is intended for both hardware and software implementations of encryption. It satisfies the necessary global standards for cryptographic security and does not impose restrictions on the level of secrecy of the protected information.
This standard is mandatory for organizations and companies of the Russian Federation that use cryptographic protection for data downloaded and / or transmitted through computer networks, individual computer complexes or personal computers. Therefore, the lack of support for this standard in software can be a serious obstacle to the use of this software in the enterprise. This is especially true of government organizations where compliance with standards is a key requirement for software.
The standard was translated into English and published in 1994, and is now widely used in software. Unlike his colleague, the DES algorithm adopted as the US federal standard, GOST 28147-89 (like AES) can be used more widely due to the lack of restrictions on the level of secrecy of the protected information.
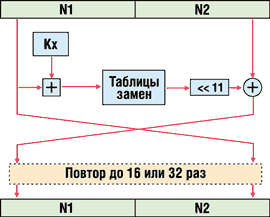
This algorithm, like DES, works with blocks of 64 bits each, but this is where the similarity ends and the differences follow:
- GOST 28147-89 contains 32 conversion cycles as opposed to 16 DES cycles.
- Each cycle in GOST 28147-89 consists of simpler operations than in DES.
- Unlike the DES standard with a key length of 56 bits, the GOST 28147-89 standard uses a 256-bit key.
- GOST 28147-89 is much faster than DES
Acronis Backup 11.5 Encryption
Acronis Backup 11.5 supports encryption of data in a backup, which allows you to protect user data from unauthorized access.
It supports AES encryption with a key length of 128/192 and 256 bits and encryption according to GOST 28147-89 with a key length of 256 bits. This type of encryption is available only in the Russian version of Acronis Backup 11.5, intended for users in the Russian Federation and the CIS countries.
All encryption algorithms use a randomly generated key of a user-specified size (128, 192 or 256 bits in case of choosing AES and 256 bits in case of selecting GOST 28147-89). The larger the key size, the longer it will take to encrypt the archive and the higher the degree of data security. The encryption key is then encrypted using the AES-256 algorithm, using the hash of the SHA-256 password entered by the user as the key. The password itself is not stored anywhere on the disk or in the backup file. To verify the password hash is used. Such a two-level protection scheme allows you to protect the backup data from unauthorized access, but recovering the lost password is impossible. Therefore, contacting the support service with a request to return access to the data in the encrypted archive when the password is lost is meaningless - we are physically unable to do this (well, except for 100,500 years, using the password brute force method).
The installer of Acronis Backup 11.5 automatically installs all the components necessary for encryption. The data is encrypted directly on the computer on which the backup operation takes place, and then sequentially transfers it to the backup storage: tape, network folder, etc.
Data compression can be used simultaneously with encryption. In this case, the data is first compressed and then encrypted. At the same time, the execution time of the backup procedure may slightly increase.
To enable the option of encrypting an archive in accordance with GOST 28147-89, when creating a backup plan, the user must go to the “archive protection” section in the “backup options” window, enable the “set password for archive” checkbox and select the appropriate algorithm.

Support for the GOST standard is part of the ideology of Acronis AnyData , which means the availability of encryption for any type of data in a backup — whether it is file archives, backup copies of physical or virtual machines, or application data.
We are ready to answer your questions regarding the implementation of the GOST standard or other encryption algorithms in Acronis products. Write in the comments what aspects should be covered in more detail (including in future articles), if this topic interests you.
Links
- Description GOST 28147-89 on Habré: Part 1 | Part 2
- Encryption algorithm GOST 28147-89, its use and implementation for computers platform Intel x86
- The strength of the algorithm GOST
- Wiki
Source: https://habr.com/ru/post/224541/
All Articles