Site TrueCrypt announces the closure of the project and offers to switch to BitLocker
 TrueCrypt developers answered: site | twitter
TrueCrypt developers answered: site | twitterDeveloper TrueCrypt "David": "We were happy that the audit did not reveal anything. We have been working hard on the project for 10 years, but nothing lasts forever. ”
Steven Barnhart: (rephrased) the developer believes that the fork will hurt even more: “The source code is available anyway, you can pry” (The source is still available as a reference though). "I asked, and it was obvious in the last answer that the developers consider fork as harmful, because only they themselves understand the code. " “He also said that he had no contact with the government, except when he was offered a“ support contract ”.
TrueCrypt developer "David": "Bitlocker is 'good enough' and Windows was the main goal of development"
Quoting the developer: "No more interest."
TL; DR: The “new” version can only decrypt the data, and may contain a trojan (although I did not find it, but you don’t take my word for it). The binary is signed with the correct developer key. All old versions are removed, the repository is also cleared.
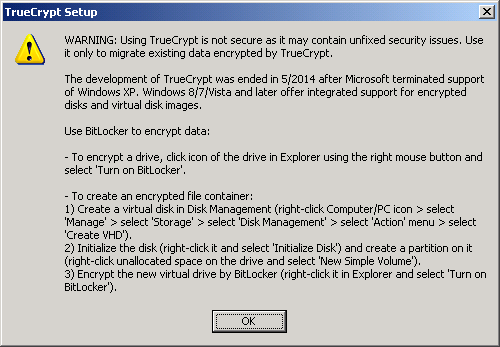
The page tells that the development of TrueCrypt was discontinued in May of this year, after Microsoft stopped supporting Windows XP, and that TrueCrypt is more insecure and may contain vulnerabilities.
Further, the page contains detailed instructions for migrating from TrueCrypt to BitLocker.
The site also has links to the TrueCrypt binary file, which lead to the SourceForge download section, along with a digital signature. This file is signed with the correct (old) key, and inside it:
')
On May 22, SourceForge changed the password hashing algorithm and suggested that they all be changed to use the new algorithm. Perhaps something went wrong.
SourceForge says nothing happened:
Providing some details from SourceForge:
1. We have had no contact with the TrueCrypt project team (and thus no complaints).
2. We see no indicator of account compromise; current usage is consistent with past usage.
3. Our recent SourceForge forced-by-infrastructure improvements were not a compromise. FMI see sourceforge.net/blog/forced-password-change
Thank you,
The SourceForge Team communityteam@sourceforge.net
Assumption # 1
Website hacked, keys compromised. Do not download this version and do not run. And do not switch to BitLocker.
Latest working version: 7.1a. Version 7.2 is a fake.
Why do I think so: a strange change of keys (first they filled in a new one, then deleted and returned the old one), and why the bitlocker?
Assumption # 2
Something happened to the developers (they threaten to kill them) or TrueCrypt itself (they found a serious vulnerability), which led to the release of such a version.
Why I think so: all files have the correct signature, all releases are released (Windows; Linux x86, x86_64, console versions, Mac OS, sources), the binaries seem to be compiled on the developer's PC (the paths to pdb, the compiler metadata are the same). The license text has also been changed (see diff below).
Why advice to use BitLocker looks outrageous? TrueCrypt has always been strong against TPM support, and BitLocker is widely used. Why not advise other open-source alternatives? It seems that the developer simply can not say anything in direct words. This is very similar to the testimony of the canary .
Unfortunately, this assumption still looks more realistic than the first. Sad but true.
Assumption number 3
Version 7.1a contains a trojan and the developer wants to prevent all users from using it.
Why I think so: there is such a truecryptcheck.wordpress.com blog with hash sums for all releases of version 7.1a. It has only one entry dated August 15, 2013. It is somewhat strange to make a site where there is only a hash sum of only one program and only one version of it.
Assumptions from the page on etcwiki :
Assumption number 4
The fundraising campaign for auditing TrueCrypt scored $ 62,000 to find out if there were loopholes in the code that allow you to decrypt the data. At the same time, the TrueCrypt Foundation received almost no donations, and the developers were disappointed that everyone was against them.
Why I think so: the developers of TrueCrypt almost did not receive donations. Of course, I do not know the specific numbers, but it is likely that the audit gained more than TrueCrypt during its existence. Since developers are anonymous, they do not receive any thanks. All this is suspicious, but probably it was done either by the developers themselves or by the TrueCrypt Foundation.
Assumption number 5
Developers are tired of developing a project, or they have difficulties in real life
Why I think so: it happens to everyone. The statement that TrueCrypt is no longer safe seems adequate, given that there will be no more updates. It seems that all changes were made by the developers.
Assumption number 6
The government is trying to find ("smoke out") developers. Someone got access to the logins and keys of the TrueCrypt developers, but could not find the developers themselves.
Why I think so: the government may have enough resources to crack the developer’s keys and get to the site. An absurd statement to switch to BitLocker can make this developer make a statement or respond in some other way.
As noted by postdig :
truecrypt.org.ua/news :
On April 12, 2014, the site was transferred to read only mode. User accounts have been deleted.
Thanks to everyone who participated in the development of the project!
As if it hints that the process is never sudden.
From Twitter Wikileaks :
(1/4) Truecrypt.sf.net
(2/4) the style of the announcement is very odd; however, it’s not a simple defacement.
(3/4) the new executable contains the same message and is cryptographically signed. We believe that there is either a power onflict ...
(4/4), or coersion of some form
From Matthew Green (one of TrueCrypt auditors):
@SteveBellovin @mattblaze @ 0xdaeda1a I think this is legit.
TrueCrypt Setup 7.1a.exe:
- sha1: 7689d038c76bd1df695d295c026961e50e4a62ea
- md5: 7a23ac83a0856c352025a6f7c9cc1526
TrueCrypt 7.1a Mac OS X.dmg:
- sha1: 16e6d7675d63fba9bb75a9983397e3fb610459a1
- md5: 89affdc42966ae5739f673ba5fb4b7c5
truecrypt-7.1a-linux-x86.tar.gz:
- sha1: 0e77b220dbbc6f14101f3f913966f2c818b0f588
- md5: 09355fb2e43cf51697a15421816899be
truecrypt-7.1a-linux-x64.tar.gz:
- sha1: 086cf24fad36c2c99a6ac32774833c74091acc4d
- md5: bb355096348383987447151eecd6dc0e
Other thoughts and interesting information:
www.reddit.com/r/crypto/comments/26px1i/truecrypt_shutting_down_development_of_truecrypt/chu5bhr
krebsonsecurity.com/2014/05/true-goodbye-using-truecrypt-is-not-secure/comment-page-1/#comment-255908
bradkovach.com/2014/05/the-death-of-truecrypt-a-symptom-of-a-greater-problem
boingboing.net/2014/05/29/mysterious-announcement-from-t.html
steve.grc.com/2014/05/29/an-imagined-letter-from-the-truecrypt-developers
Links to news and blog entries:
news.ycombinator.com/item?id=7812133
www.reddit.com/r/netsec/comments/26pz9b/truecrypt_development_has_ended_052814
www.reddit.com/r/sysadmin/comments/26pxol/truecrypt_is_dead
www.reddit.com/r/crypto/comments/26px1i/truecrypt_shutting_down_development_of_truecrypt
arstechnica.com/security/2014/05/truecrypt-is-not-secure-official-sourceforge-page-abruptly-warns
krebsonsecurity.com/2014/05/true-goodbye-using-truecrypt-is-not-secure
www.pcworld.com/article/2241300/truecrypt-now-encouraging-users-to-use-microsofts-bitlocker.html#tk.twt_pcworld
www.coindesk.com/popular-encryption-tool-truecrypt-mysteriously-shuts
business.kaspersky.com/truecrypt-unexplained-disappearance
www.forbes.com/sites/jameslyne/2014/05/29/open-source-crypto-truecrypt-disappears-with-suspicious-cloud-of-mystery - this one is pretty well written
news.softodrom.ru/ap/b19702.shtml - very good article (written, by the way, 05/15/2014)
pastebin.com/7LNQUsrA - some more info on developers
Twitter stream: twitter.com/search?q=truecrypt&src=typd
Diff between normal version 7.1a and "current" 7.2
diff on github
Link for your English-speaking friends
truecrypt.sourceforge.net
Source: https://habr.com/ru/post/224491/
All Articles