Stolen Apple ID used to block iDevice
Last week and this week, the media repeatedly published information that users of iPod Touch, iPhone and iPad in many countries found their devices blocked. The attackers used the stolen Apple ID, as well as the iCloud function, called Lost Mode . It remains unclear how the attackers managed to get a login / password from Apple ID accounts and whether a vulnerability was used for this in one of the Apple services. It should be noted that when Apple ID is compromised, the attacker gets access to all Apple services for this user (including iCloud, iTunes, AppStore) and, theoretically, can perform the necessary actions on this account (except for those that require confirmation by secret questions).
A few hours ago, ZDNet published the first comment from Apple officials on this issue:
')
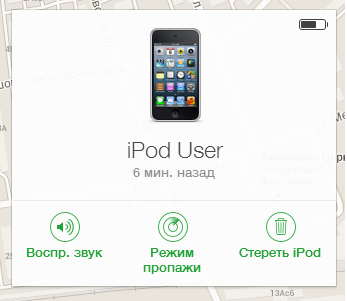
Fig. The function of "Loss Mode" is available in the service icloud.com. To detect the device, it should work on iOS6 +, have access to the Internet, as well as the active “Find iPhone” (iPod) option.
The loss mode allows you to remotely block the above-listed iDevice devices with Internet access enabled. In this case, the lock is accompanied by a message that is set by the user himself (or those who have access to the Apple ID). To unlock (unlock), you need to use a special code, however, if the device is protected by a password, then to unlock it is enough to type your usual password . Otherwise (on iOS, password protection is not used), to unlock, you need to contact Apple technical support. It is precisely the second scenario that the attackers are counting on when they offer to send the necessary amount to a specific number (extortion). If you saw such a message demanding ransom, in any case, do not be fooled by the intruders. Go to appleid.apple.com to change your account password since it has been compromised. Next, to unlock the device itself, you can contact Apple technical support or use Apple's recommendation for restoring it from your iTunes backup.
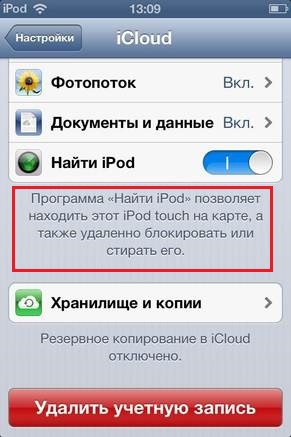
Fig. The “Find an iPod” setting on the device must be enabled in order to use the “Lost Mode” feature. Enabled by default.
According to information not confirmed by Apple, to compromise Apple ID, a vulnerability in the implementation of SSL in some versions of the iTunes client for Windows could be exploited through a successful Man-in-the-Middle attack.
In order to ensure the proper level of security for your iDevice and Apple ID, use the following tips.
On iOS7, Apple has introduced an additional security setting for Find iPhone mode, called Activation Lock. It imposes additional restrictions (Apple ID request) on the use of device-critical functions. Activation Lock is activated when activating the “Find iPhone” setting, which was mentioned above.

be secure.
A few hours ago, ZDNet published the first comment from Apple officials on this issue:
ICloud was not compromised during this incident . It is possible to change their user IDs for multiple services. Anyone can help their local Apple Retail Store.
')

Fig. The function of "Loss Mode" is available in the service icloud.com. To detect the device, it should work on iOS6 +, have access to the Internet, as well as the active “Find iPhone” (iPod) option.
The loss mode allows you to remotely block the above-listed iDevice devices with Internet access enabled. In this case, the lock is accompanied by a message that is set by the user himself (or those who have access to the Apple ID). To unlock (unlock), you need to use a special code, however, if the device is protected by a password, then to unlock it is enough to type your usual password . Otherwise (on iOS, password protection is not used), to unlock, you need to contact Apple technical support. It is precisely the second scenario that the attackers are counting on when they offer to send the necessary amount to a specific number (extortion). If you saw such a message demanding ransom, in any case, do not be fooled by the intruders. Go to appleid.apple.com to change your account password since it has been compromised. Next, to unlock the device itself, you can contact Apple technical support or use Apple's recommendation for restoring it from your iTunes backup.

Fig. The “Find an iPod” setting on the device must be enabled in order to use the “Lost Mode” feature. Enabled by default.
According to information not confirmed by Apple, to compromise Apple ID, a vulnerability in the implementation of SSL in some versions of the iTunes client for Windows could be exploited through a successful Man-in-the-Middle attack.
In order to ensure the proper level of security for your iDevice and Apple ID, use the following tips.
- Use your unlock password on your device. This will protect your device if it falls into the hands of third parties. In addition, if the attackers compromise your Apple ID and try to remotely lock the device, you can use your code to unlock it.
- Do not respond to phishing emails from supposedly Apple, which call to send in the reply message a login / password from your account, or other information about the account, for example, security questions.
- Regularly update iOS and OS X & Windows desktop applications that work with Apple ID. Apple regularly closes security vulnerabilities that could compromise the device.
- Do not use Apple ID Services. You cannot guarantee the “security” of such an Apple ID, which is obtained from a third-party source. Use only your Apple ID, which belongs to you and whose security you are the ones providing.
- Check if you have the "Find iPhone" feature. If a device is lost, you can use iCloud to block it or delete your data from the device.
- Use two-factor authentication . It allows you to enable confirmation of SMS-based transactions with Apple ID.
On iOS7, Apple has introduced an additional security setting for Find iPhone mode, called Activation Lock. It imposes additional restrictions (Apple ID request) on the use of device-critical functions. Activation Lock is activated when activating the “Find iPhone” setting, which was mentioned above.

be secure.
Source: https://habr.com/ru/post/224417/
All Articles