How Host-tracker helped to quickly detect malicious code
Our site monitoring service, in addition to the availability of servers, also allows you to monitor site content . For example, if you need to receive notifications that a certain keyword has appeared on the site, or vice versa, if it is missing.
Today we want to tell how using the Host-tracker our client struggled with detecting malicious code so as not to fall into the ban of Yandex.
Presentation on behalf of the client:
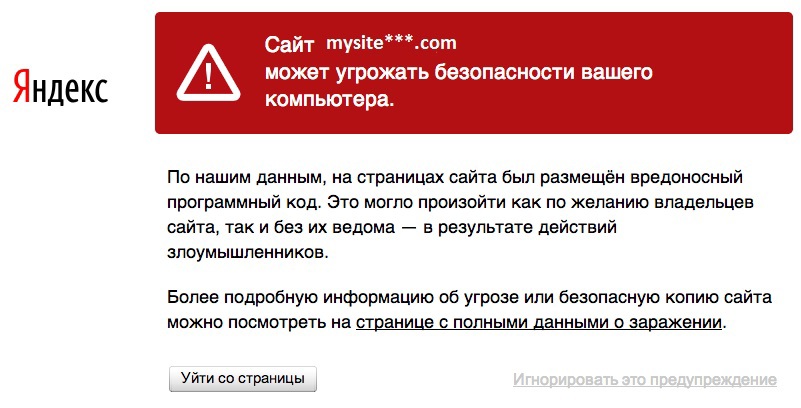
One day, while trying to access the mysite ***. Com site, a warning appeared that the site could threaten the security of the computer.
And also a letter came from Yandex: A potentially dangerous code was found on the site:
A code has been found on the pages of your mysite ***. Com site that could be dangerous for visitors. Execution of this code when visiting the site may lead to undesirable consequences for the user: computer infection by malware, unauthorized use of its resources, damage or theft of personal data.
The site is currently displayed in search results labeled "This site may threaten the security of your computer."
Yandex does not evaluate the content of the site and warns users that the site could be infected without the knowledge of its owners.
Please remove the malicious code. If during the new check the code is not found, the mark in the search results will be removed. In order to remove the mark as quickly as possible, immediately after removing the code, you can request a re-check of the site.
In the Yandex webmaster panel there was a message:
Random check result
Last inspection date
Page mysite ***. Html
Verdict Behavioral analysis.
')
Naturally, the site was immediately checked by various online antiviruses, but no threats were detected. After that, I thought it was some kind of misunderstanding and wrote a letter in support of Yandex, asking to clarify the situation, indicating that the online antiviruses did not find any threats. They replied that one of the files, common.js, was infected on the site. I also noticed that links to some "left" sites appeared from the main page. I suppose some kind of link exchange found a good method to sell links of unsuspecting owners. Opening the file, I actually found malicious code in it:
Overjoyed with such an easy solution to the problem, I took the file from the old backup, uploaded it to the server, and wrote to Yandex, that I had fixed everything, you can remove it from the ban.
Yandex really removed the site from the ban, and in the webmaster’s panel it was indicated that everything was OK. But a couple of days passed and the picture repeated. I immediately checked the file that was infected earlier, made sure that the malicious code was there, and replaced it with a file from backup.
I immediately wrote to the hoster that I had such a problem. They replied that only I have a problem, but they are fine, they advised me to change passwords for the admin panel, ftp and to the database. I did it all, put a clean file from backup, but it was literally a couple of hours and the file was again infected.
I also decided to check my neighbors by IP. Randomly opened 5 sites, and not how many was not surprised that they also have external links from the main one, using an iframe. Naturally, I immediately wrote to the hoster about this, and received the answer that everything is OK, no more than 5% of client accounts are infected and there are no alleged problems. He answered them that for nonsense he argued that there was a problem, then they gave a more detailed answer with a proposal to restore the backup. Also recommended to put access to files 444 and 555 directories, which I did. But it was literally a day, access was returned to 644 and 755, respectively, and the malicious code in the file.
Found on the forums a description of the same problem. The people described the same symptoms and the same methods of struggle. Moreover, one of the victims suggested that the hoster change all its passwords for a couple of days so that he does not know them, and make sure that the malicious code appears. In a word, the hoster admitted that there is a problem on their side and they are trying to solve it.
The deadlines for solving the problem were not announced, and the site constantly got into the ban of Yandex and, accordingly, during this time has already lost its position in the issue.
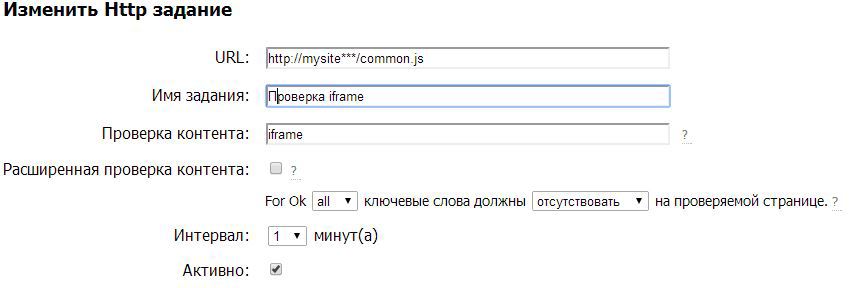
For specific files that knew that they were infected almost every couple of hours, they used the Host-tracker function - search by content . I chose Http check, I registered the URL: the path to the mysite *** / common.js file, which was constantly infected, I registered to monitor by the keyword “iframe”, which was present in the enemy code, I chose: all keywords should be absent on the checked page . Now, when the enemy code appeared, I received an SMS and a notification to an e-mail in just a minute (I chose a polling interval of 1 min).
At first, I had to promptly correct it myself, so that Yandex did not ban. Then I noticed that a notification is coming that common.js contains malicious code, and literally in a couple of minutes the files are already without malicious code. The hoster finally began to self-healing files. This lasted for another couple of days, until the infection reports stopped coming.
For myself, I have additionally implemented a simple method for controlling changes to * .js files:
Files must be of any enemy code. For example, in the morning, we save the checksum of files with the necessary extension .js, .php, etc.
and repeat the procedure in the evening
then I compare these two files for discrepancies in checksums:
If something has changed, check the reason for changing the files.
After this incident, I found several automated solutions that allow you to track changes for certain types of files, and use them.
Today we want to tell how using the Host-tracker our client struggled with detecting malicious code so as not to fall into the ban of Yandex.

Presentation on behalf of the client:
The site hit the ban of Yandex
One day, while trying to access the mysite ***. Com site, a warning appeared that the site could threaten the security of the computer.
And also a letter came from Yandex: A potentially dangerous code was found on the site:
A code has been found on the pages of your mysite ***. Com site that could be dangerous for visitors. Execution of this code when visiting the site may lead to undesirable consequences for the user: computer infection by malware, unauthorized use of its resources, damage or theft of personal data.
The site is currently displayed in search results labeled "This site may threaten the security of your computer."
Yandex does not evaluate the content of the site and warns users that the site could be infected without the knowledge of its owners.
Please remove the malicious code. If during the new check the code is not found, the mark in the search results will be removed. In order to remove the mark as quickly as possible, immediately after removing the code, you can request a re-check of the site.
In the Yandex webmaster panel there was a message:
Random check result
Last inspection date
Page mysite ***. Html
Verdict Behavioral analysis.
')
Malware Detection
Naturally, the site was immediately checked by various online antiviruses, but no threats were detected. After that, I thought it was some kind of misunderstanding and wrote a letter in support of Yandex, asking to clarify the situation, indicating that the online antiviruses did not find any threats. They replied that one of the files, common.js, was infected on the site. I also noticed that links to some "left" sites appeared from the main page. I suppose some kind of link exchange found a good method to sell links of unsuspecting owners. Opening the file, I actually found malicious code in it:
/>...Anti-malware
Overjoyed with such an easy solution to the problem, I took the file from the old backup, uploaded it to the server, and wrote to Yandex, that I had fixed everything, you can remove it from the ban.
Yandex really removed the site from the ban, and in the webmaster’s panel it was indicated that everything was OK. But a couple of days passed and the picture repeated. I immediately checked the file that was infected earlier, made sure that the malicious code was there, and replaced it with a file from backup.
I immediately wrote to the hoster that I had such a problem. They replied that only I have a problem, but they are fine, they advised me to change passwords for the admin panel, ftp and to the database. I did it all, put a clean file from backup, but it was literally a couple of hours and the file was again infected.
I also decided to check my neighbors by IP. Randomly opened 5 sites, and not how many was not surprised that they also have external links from the main one, using an iframe. Naturally, I immediately wrote to the hoster about this, and received the answer that everything is OK, no more than 5% of client accounts are infected and there are no alleged problems. He answered them that for nonsense he argued that there was a problem, then they gave a more detailed answer with a proposal to restore the backup. Also recommended to put access to files 444 and 555 directories, which I did. But it was literally a day, access was returned to 644 and 755, respectively, and the malicious code in the file.
Found on the forums a description of the same problem. The people described the same symptoms and the same methods of struggle. Moreover, one of the victims suggested that the hoster change all its passwords for a couple of days so that he does not know them, and make sure that the malicious code appears. In a word, the hoster admitted that there is a problem on their side and they are trying to solve it.
The deadlines for solving the problem were not announced, and the site constantly got into the ban of Yandex and, accordingly, during this time has already lost its position in the issue.
Content Search
For specific files that knew that they were infected almost every couple of hours, they used the Host-tracker function - search by content . I chose Http check, I registered the URL: the path to the mysite *** / common.js file, which was constantly infected, I registered to monitor by the keyword “iframe”, which was present in the enemy code, I chose: all keywords should be absent on the checked page . Now, when the enemy code appeared, I received an SMS and a notification to an e-mail in just a minute (I chose a polling interval of 1 min).

At first, I had to promptly correct it myself, so that Yandex did not ban. Then I noticed that a notification is coming that common.js contains malicious code, and literally in a couple of minutes the files are already without malicious code. The hoster finally began to self-healing files. This lasted for another couple of days, until the infection reports stopped coming.
Checksum check
For myself, I have additionally implemented a simple method for controlling changes to * .js files:
Files must be of any enemy code. For example, in the morning, we save the checksum of files with the necessary extension .js, .php, etc.
find . -type f -name "*.js" -exec md5sum {} \; > file-js1.txtand repeat the procedure in the evening
find . -type f -name "*.js" -exec md5sum {} \; > file-js2.txtthen I compare these two files for discrepancies in checksums:
diff -u file-js1.txt file-js2.txt.If something has changed, check the reason for changing the files.
After this incident, I found several automated solutions that allow you to track changes for certain types of files, and use them.
Source: https://habr.com/ru/post/223877/
All Articles