Very difficult choice: 3 ways to protect a virtual machine
 Protecting or not protecting virtual environments from malware is a question that has been closed for the first option for a long time without special discussion. Another thing is how to protect ? We have developed the concept of an agentless antivirus for the VMware platform for quite some time: you can read more about it in this post by Evgeny Kaspersky. But technology is not in place. Virtualization attracts new applied IT-directions, and with the growth of its applicability, the specific protection requirements are also expanding. Obviously, one is needed for a virtual desktop, a second for a database, a third for websites, and so on. At the same time, agentless antivirus is far from the only option of protection, and VMware is the most popular, but not the only virtualization platform.
Protecting or not protecting virtual environments from malware is a question that has been closed for the first option for a long time without special discussion. Another thing is how to protect ? We have developed the concept of an agentless antivirus for the VMware platform for quite some time: you can read more about it in this post by Evgeny Kaspersky. But technology is not in place. Virtualization attracts new applied IT-directions, and with the growth of its applicability, the specific protection requirements are also expanding. Obviously, one is needed for a virtual desktop, a second for a database, a third for websites, and so on. At the same time, agentless antivirus is far from the only option of protection, and VMware is the most popular, but not the only virtualization platform.What are the alternatives and which one is more suitable?
Agentless (agentless) concept.
There will be a “summary of the previous series”, because there is already exhaustive material on this issue (see the link above).
')
In the virtual infrastructure, a special machine is allocated on which the anti-virus engine is installed. Its connection with the rest of the virtual machines and scanned objects is provided by the native VMware vShield technology. In addition, vShield communicates with the antivirus management system to configure, apply policies, enable / disable protection, optimize load, etc.
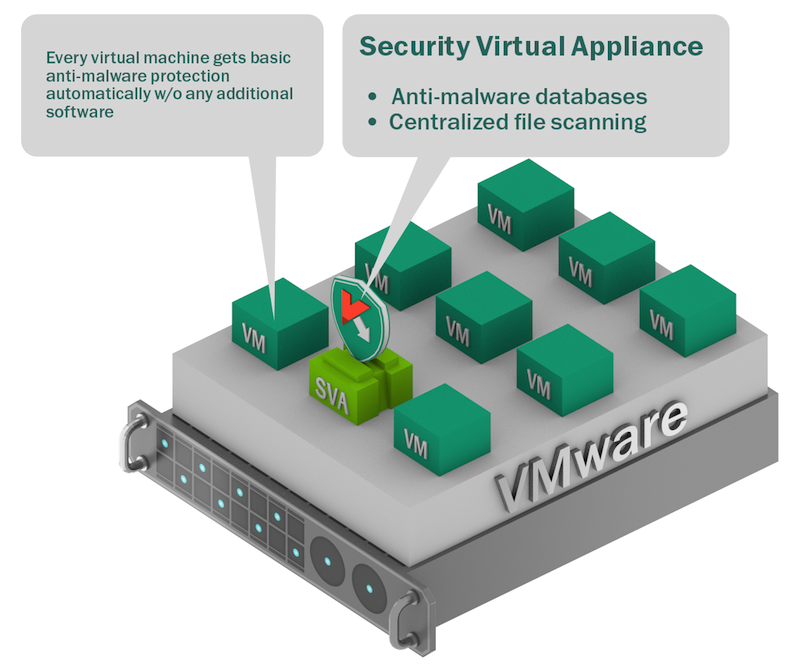
Sounds like a panacea, but this concept has a
These are features , because, apparently, in VMware they were not going to give a full-fledged interface for all protective functions. In principle, this approach also has an application, but more on that below.
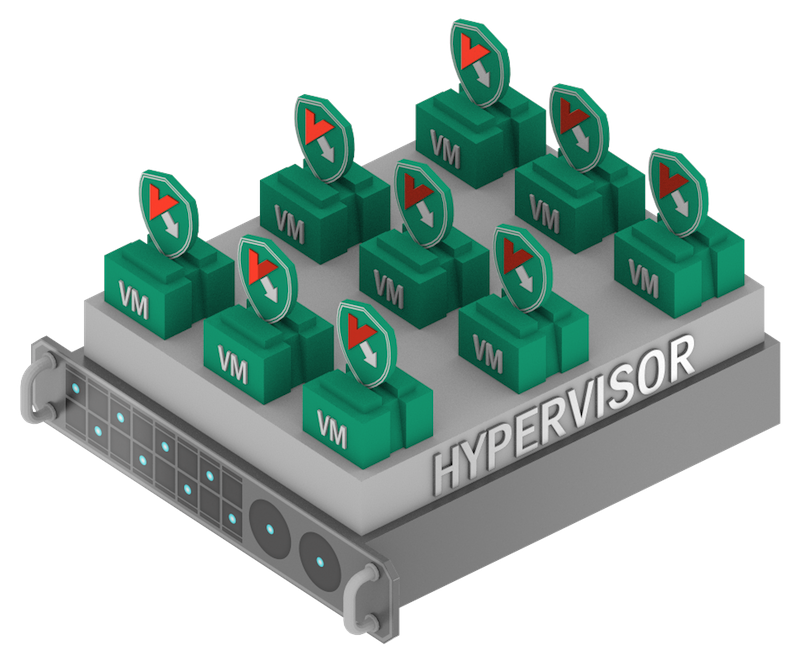
Now let's look at the following concept - Light Agent (“Light Agent”).
In this embodiment, instead of vShield, a light agent interacts with the antivirus engine, which is installed on each protected virtual machine. So we remove the limitations of the VMware interface to use the full defense potential. And at the same time, we retain the advantages of an agentless approach - moderate appetite for resources, manageability, and resistance to “storms” (degradation of cluster performance due to simultaneous updating or testing of many machines at once).

Yes, despite the name, the easy agent will be "heavier" without an agent-based solution - it requires both memory in each virtual machine, and processor resources, and new machine images with a pre-installed agent. On the other hand, with today's capacities this is a very modest appetite, especially provided that it works even faster in some standard operations. And with the growth of the quality of protection, it becomes clear that the game is worth the candle.
Well, OK, and what to do if the antivirus works only with Windows as a guest OS on a virtual machine, plus - I really want to have the most complete set of security technologies, including cryptography ? Then you need a traditional endpoint product . Yes, it will be problematic to sharpen the entire virtual infrastructure, and this solution will require more attention, but there are cases when this approach is appropriate.
And now - to practice. We recently released the third version of our product for virtual environments , having implemented both protection concepts (Agentless and Light Agent). In addition to VMware, we now support Citrix XenServer and Microsoft Hyper-V . To the already existing agentless solution for VMware, a protection variant using a light agent for all three platforms has been added. At the same time, all products are managed from a single console , which is especially important for multi-hypervisory environments, so as not to create a console zoo.
So which tasks, which option is best suited?
In general, the logic of security choice is as follows: for maximum protection, guest Windows needs a light agent , on other OS (Linux, OS X) - a product for endpoints . Alas, in the second version, the application is limited due to considerations of performance and the interaction of the antivirus with the features of the virtual environment itself. We are working on the support of other OS with a light agent. And if performance is critical, the value and diversity of the data is low and access to it is limited from the outside — then an agent-free solution is appropriate.
We analyzed typical application tasks with the use of virtualization and compiled such an interesting tablet.

This is not an exhaustive and not unambiguous picture - in different organizations conditions may change, but the list of tasks expands. Its goal is to show the threat model and methodology for assessing tasks and priorities.
We return to the title. Well, what, the choice, it turns out, is not even at all difficult!
Source: https://habr.com/ru/post/223729/
All Articles