A few words about the interception of HTTP / HTTPS traffic iOS applications
 In this article I will talk about a simple method of
In this article I will talk about a simple method of We will need:
- iOS 7.0-7.0.4 device with evasi0n jailbreak and installed OpenSSH
- PC with Windows 7 and installed the latest version of Fiddler2
- iOS device and PC must be connected to the same Wi-Fi network
Perhaps on other versions of iOS and / or Windows will also work, I have not tried. In any case, whatever configuration of OS / hardware you have, you do all further actions at your own peril and risk! The author is not responsible for possible harm, blah blah blah ... Well, a standard warning, you understand.
The instructions for setting up Fiddler2 are quite simple: open “Tools” → “Fiddler Options” and set it up like in the picture:
')


Close the settings, then click the icon in the upper right corner of the main Fiddler2 window and note the address of your PC in the Wi-Fi network. There will be something like this:
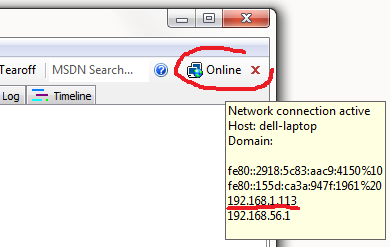
Now instructions for setting up iOS device. It is a bit more complicated, but also not rocket science. In addition, it needs to be done only once, and then just use:
- Via Cydia, install MobileSubstrate and PreferenceLoader, if not already installed (both packages are in default repositories)
- From https://github.com/iSECPartners/ios-ssl-kill-switch/releases download the package com.isecpartners.nabla.sslkillswitch_v0.6-iOS_7.0.deb to some folder on your PC, and then from this folders via ftps copy the package to the root of your iOS device using any ftp manager that can do this (under Windows, I personally prefer WinSCP , but of course it’s a matter of taste)
- Login to your iOS device over SSH as root and execute the following commands:
# dpkg -i /com.isecpartners.nabla.sslkillswitch_v0.6-iOS_7.0.deb # killall -HUP SpringBoard # rm /com.isecpartners.nabla.sslkillswitch_v0.6-iOS_7.0.deb - On your iOS device, go to “Settings” and find the “SSL Kill Switch” section (yes, it was not there before, but if everything went well at the previous step, it appeared there) and enable the “Disable Certificate Validation” setting
- Reboot your iOS device (by hand or command
rebootvia SSH) - Go to the Wi-Fi settings of the network to which your iOS device is connected, set the HTTP proxy to “Manual” and set
- Server: Your PC's IP address (yeah! You forgot it!)
- Port: 8888
- Authentification: off
Now, if everything went well, Fiddler2 will run HTTP / HTTPS traffic from your iOS device. Moreover, even the traffic of those applications that use certificate pinning will be visible: thanks to the patch com.isecpartners.nabla.sslkillswitch_v0.6-iOS_7.0.deb, which we installed on our iOS device, 99% of iOS apps have a certificate check with success the certificate would not be slipped to the application (in our case, Fiddler2 slips its application).
That's all. No manual generation of certificates, cramming them into iOS (which, as a rule, still does not help against certificate pinning) and other hemorrhoids. True, there is one “but” ... if after your experiments you leave the “Disable Certificate Validation” setting enabled, applications on your iOS device may become vulnerable to MITM attacks - after all, thanks to the patch, they accept any certificates, remember? Therefore, if you use your personal iPhone for your experiments, turn off the “Disable Certificate Validation”
Happy sniffing!
Source: https://habr.com/ru/post/223561/
All Articles