A place where you can test the strength of enterprise-software in the center of Symantec solutions
There are tasks that can be viewed on the finished infrastructure in a large company. A large number of Enterprise-level programs are written for a specific system or platform - and therefore they are so little known. More precisely, they are known for leaflets, and in them, it seems, no one writes that they have little work.
Everyone says that everything works perfectly. You read, and you feel, in what wonderful world you live. Already on tear tears through.
Below, I explain in simple terms how and what works for large companies and what large-scale tasks can be on the example of the Symantec Solution Center, where a simulator of large business infrastructure is deployed. Backup, security, work with mail, tracking problems on thousands of nodes and so on.
')
You can come and test at what level marketers are honest.
But most importantly, you can understand how this or that system is applicable in your particular case, and not to buy a cat in a bag.
It's simple. Users have PST files and they are growing uncontrollably. Previously, the frequent cause of dramas, for example, was the output of a file for 4Gb - Outlook simply could not open it. Many problems with local space and performance, plus a lot of well-archived and duplicate information. The logical solution is centralized storage. All big companies sooner or later do this and store mail somewhere in a single system, sending old messages to the archive. Also one. In the West, the evolution of postal systems went to this branch of official investigations: there the level of industrial espionage is such that if you did not try to steal something in a day, it means that you were not attentive enough. So, the security men loved to browse corporate mail, and they did it from the central repository. In Russia, more questions arise with job stability and resource savings.

Both tasks — convenience and security — are solved by Symantec Enterprise Vault. In our infrastructure simulator of a large company, it works in conjunction with Microsoft Exchange. Mail messages are imported from pst files on users' work computers to the Enterprise Vault archive storage. Convenient and practical.
Imagine that you have 5,000 people. Users send your documents by mail, VKontakte, upload to Dropbox, drag on flash drives, write a podcast with them or invent something else. I want to block it all if possible. A particularly inventive catch after the fact and tear off their hands.
There is a solution that allows you to build a comprehensive solution for detecting confidential information regardless of its location: in the network, data stores, on servers or user devices. Its functionality makes it possible to create and apply various policies governing the protection and transmission of confidential data based on their content and risk assessment of information security. The solution is based on the product Symantec Data Loss Prevention.
In general, here I wanted to attach a picture of a hammer, but my colleagues said that you might think that this has to do with what happens with the information being merged.
In other words, it is a complex expert system that is trained to look for data that you consider confidential. It learns, takes into account various tricks of users and allows you to securely protect its infrastructure. Better than her, perhaps, can only Comrade Major, who will read all traffic at all. Only then will you need somewhere a couple of thousands of such majors.
In case there is someone too clever, and the data will flow away - you can always find out the name of the security hole. A good system, in Russia we love and appreciate it, as in the West. Only here we love and appreciate it before the incidents (the benefit of paranoia is higher), and there, as a rule, after.
Backup is the first thing an experienced administrator does. There are a lot of backup solutions, and all of them are good in their own way. In my practice, Symantec NetBackup is used when everything else does not help, and there is still money. This combine is able to back up everything, including the banking database, which cannot be simply taken and copied because of thousands of transactions every second. You can’t put such a system with a swoop, you need qualifications, so we, as an integrator, are doing this.
It allows you to deduplicate information, replicate ready backups to backup data center, quickly copy and restore virtual servers. The solution also automates the process of creating snapshots (snapshots) of hardware and software systems. We have NetBackup as software deployed in the center, as well as a PACK NetBackup Appliance. And there is a second backup solution - Symantec Backup Exec. NetBackup is if you are a bank or a telecom, or just a big business. Backup Exec - for relatively small enterprises, built mainly on Windows and Linux-based platforms.

Somewhere here is a draft of my post, and if you need it - the security officer will get it in half a minute. By the way, there is a gift for him.
Yes, modern backup solutions have agents for all popular software, DBMS and virtual environments. Simply put - understand what data and how to take, how to store and offer the user. It depends on the forethought of the software whether the agent will be able to pick up the base “on the fly” without stopping the service, whether the admin will be able to restore one record in the database in 15 seconds, and whether the blonde user will be able to independently retrieve a letter that he accidentally deleted two years ago. Very important.
I will illustrate . The customer has grown infrastructure, and has grown greatly. A “zoo” of software and hardware appeared, when there are many vendors, many generations of different equipment, many different systems and tasks. Backup tools have become ineffective. First, there are a lot of them: one by one for the subsystem. A separate admin for each case: it’s very hard to monitor everything, to keep the focus, because, as a rule, there are still not enough resources. There are about three hundred consoles for individual installations. And it begins: somewhere something was missed, somewhere something was not seen, then something fell, and now, when it is necessary to recover, it turns out that, oops, 2 months backups are no longer coming! And this, in fact, is quite a life situation. We put one product. He has one administrator. One console. Admin came, looked, opened, all night backups went, everything is fine. And he is sure that everything is fine, that is, if it is necessary, he will recover.
These are things that even cost no data like an airplane. And if you screw one, then you can safely go hang yourself - most likely there were not only pictures of your users, but also a couple of terabytes of important financial data. The situation is aggravated by the wonderful fact that many storage systems are connected to servers that constantly need this information. You can not just take and replace such a system, just as you can not just take something quickly there to change. Just the case when "do not fit - kill!".
Therefore, there is such a thing Veritas Storage Foundation. It is needed for different hardware from different manufacturers so that you can do your admin or even service work without stopping the work of business applications. What to do? Anything: change the size and structure of logical volumes, create snapshots or full copies of systems, replicate data.
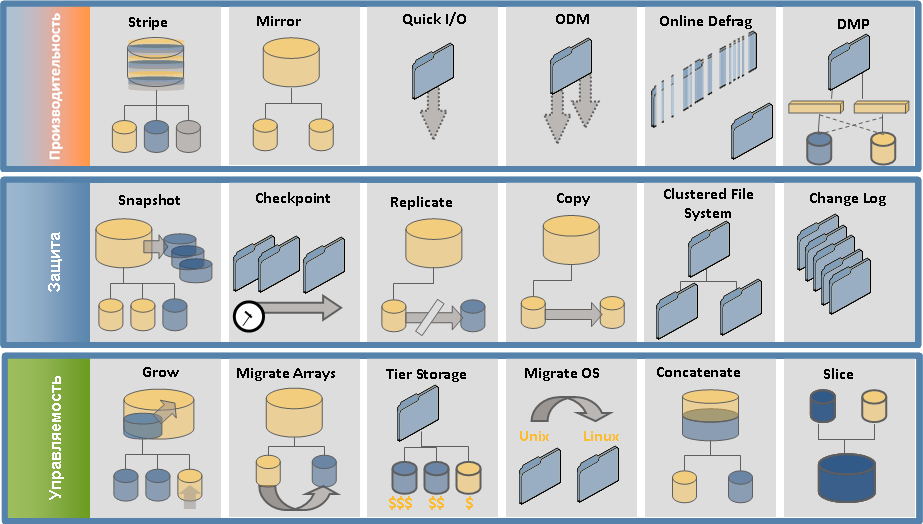
For each picture - the story of at least one facac from someone else's practice
Once we changed a very old storage system on a system to which it was almost impossible to touch. A mere couple of seconds meant losses of 200–300 thousand dollars. About. In general, we connected the second storage system from another vendor, set up their work in the “mirror” mode using Veritas Storage Foundation, i.e. Got like RAID1, parts of which were two storage systems. Then they waited for data synchronization and simply disconnected the old one. The server did not even notice. You can also make reliable fast data migration between different platforms - HP-UX, Oracle Solaris, IBM AIX. At the same time, the transfer of a large database from one platform to another takes minutes or hours in semi-automatic mode. If you do without such software, it takes days or weeks.
Failures occur at all and often. Seriously, we even have permanent flights (which are undated, the most expensive) for some engineers. Something somewhere in the country broke down - and he jumps on the subway, then to the aeroexpress, then to the plane, and after 4–5 hours on the spot. If necessary.
It helps not to fly once again (and to the customer - not to go into a simple one) package of Veritas Cluster Server. It allows you to quickly respond to the failure of the application, operating system, network or a single node. As soon as a failure is detected, the software happily goes on doing automatic recovery of critical business services at the backup site, regardless of its distance from the main facility. It can be said that the cluster nodes are talking to each other, constantly reporting on their condition. And if an incorrect answer comes from one of them, or there is no answer at all, the second one quickly deploys the reserve. You, as a rule, have time to read a disturbing SMS at the very moment when the work of the services already switches to the backup data center.
The software "out of the box" is integrated with almost all DBMS and OS of corporate level.
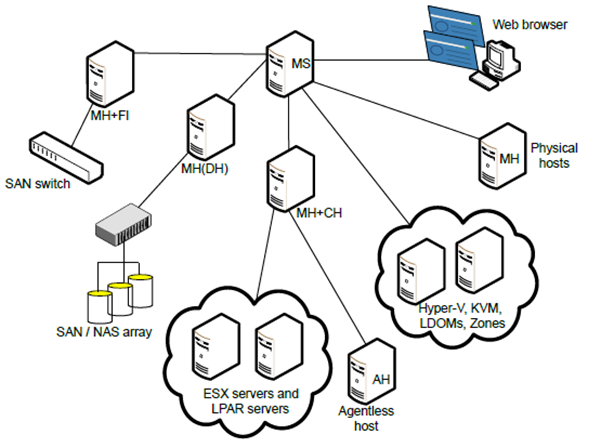
When you have only a hundred clusters, problems begin with administration. Most often we are talking about infrastructure such as telecom, a major provider or bank, as well as insurance or major retail. In general, where there can be dozens of storage systems, thousands of normal nodes and several data centers.
The main thing in such an infrastructure is not to miss the moment. In the sense that a problem can sneak up on sight, and its search requires a lot of time. Taking into account that usually all this is also handed down “by inheritance” to new admins, problems happen.
There are Veritas Operations Manager (VOM) and OpsCenter. VOM brings all the consoles of all clusters and logical volume managers into one convenient web-interface. There is also a “traffic light” - it helps to look for problems where they, according to the product, may arise. Which characterizes, helps, and helps great. OpsCenter does roughly the same for individual consoles of backup software.
But, of course, if you like dozens of consoles, then there are no problems to walk directly.
String with the intriguing and proud name of Symantec Critical System Protection makes it exactly Critical System Protection. The solution is a highly accurate tool for controlling vulnerabilities, detecting and preventing intrusions. All the same good old expert system that looks for interconnections, strange events, builds profiles of various kinds of activities and can find a possible problem using three or four weak signals. By the way, it is run in Symantec Cyber Challenge - one of the world's largest security competitions, when hackers from around the world break the corporation's network simulator in several stages. Last year, in the EMEA region, a Russian student v0s won - now his patterns, as well as the patterns of the other participants, have expanded the attack library. About how the complex works in theory, my colleague wrote separately here in the educational program on modern information security.
So, we have a kind of infrastructure simulator of a large company (with its large databases, littered machines, clogged storage in branches, complex cases and restless users, more precisely, the results of their work). All this is deployed not only in virtual machines, but also on the physical hardware of six different manufacturers, and on top of all this are installed Symantec solutions that you can come in and touch. Moreover, you can bring your test databases to watch Symantec say “hrrr” on them.
Therefore, drop in for a visit if you need serious software or a PACK. So that it is specifically clear what exactly he is doing, how exactly and where his weak points are. You already know the strengths, but what awaits you after a year of practice in your infrastructure is the most important question. My colleagues and I help answer such questions and show everything as it is, immediately warning about the rake. Fortunately, it is not in our interest to promise something extra - after all, we will have to support all this.
You can find me by mail ADubskiy@croc.ru or register in the center here .
Everyone says that everything works perfectly. You read, and you feel, in what wonderful world you live. Already on tear tears through.
Below, I explain in simple terms how and what works for large companies and what large-scale tasks can be on the example of the Symantec Solution Center, where a simulator of large business infrastructure is deployed. Backup, security, work with mail, tracking problems on thousands of nodes and so on.
')
You can come and test at what level marketers are honest.
But most importantly, you can understand how this or that system is applicable in your particular case, and not to buy a cat in a bag.
post office
It's simple. Users have PST files and they are growing uncontrollably. Previously, the frequent cause of dramas, for example, was the output of a file for 4Gb - Outlook simply could not open it. Many problems with local space and performance, plus a lot of well-archived and duplicate information. The logical solution is centralized storage. All big companies sooner or later do this and store mail somewhere in a single system, sending old messages to the archive. Also one. In the West, the evolution of postal systems went to this branch of official investigations: there the level of industrial espionage is such that if you did not try to steal something in a day, it means that you were not attentive enough. So, the security men loved to browse corporate mail, and they did it from the central repository. In Russia, more questions arise with job stability and resource savings.

Both tasks — convenience and security — are solved by Symantec Enterprise Vault. In our infrastructure simulator of a large company, it works in conjunction with Microsoft Exchange. Mail messages are imported from pst files on users' work computers to the Enterprise Vault archive storage. Convenient and practical.
Preventing leakage of confidential information
Imagine that you have 5,000 people. Users send your documents by mail, VKontakte, upload to Dropbox, drag on flash drives, write a podcast with them or invent something else. I want to block it all if possible. A particularly inventive catch after the fact and tear off their hands.
There is a solution that allows you to build a comprehensive solution for detecting confidential information regardless of its location: in the network, data stores, on servers or user devices. Its functionality makes it possible to create and apply various policies governing the protection and transmission of confidential data based on their content and risk assessment of information security. The solution is based on the product Symantec Data Loss Prevention.

In general, here I wanted to attach a picture of a hammer, but my colleagues said that you might think that this has to do with what happens with the information being merged.
In other words, it is a complex expert system that is trained to look for data that you consider confidential. It learns, takes into account various tricks of users and allows you to securely protect its infrastructure. Better than her, perhaps, can only Comrade Major, who will read all traffic at all. Only then will you need somewhere a couple of thousands of such majors.
In case there is someone too clever, and the data will flow away - you can always find out the name of the security hole. A good system, in Russia we love and appreciate it, as in the West. Only here we love and appreciate it before the incidents (the benefit of paranoia is higher), and there, as a rule, after.
Backup and deduplication
Backup is the first thing an experienced administrator does. There are a lot of backup solutions, and all of them are good in their own way. In my practice, Symantec NetBackup is used when everything else does not help, and there is still money. This combine is able to back up everything, including the banking database, which cannot be simply taken and copied because of thousands of transactions every second. You can’t put such a system with a swoop, you need qualifications, so we, as an integrator, are doing this.
It allows you to deduplicate information, replicate ready backups to backup data center, quickly copy and restore virtual servers. The solution also automates the process of creating snapshots (snapshots) of hardware and software systems. We have NetBackup as software deployed in the center, as well as a PACK NetBackup Appliance. And there is a second backup solution - Symantec Backup Exec. NetBackup is if you are a bank or a telecom, or just a big business. Backup Exec - for relatively small enterprises, built mainly on Windows and Linux-based platforms.

Somewhere here is a draft of my post, and if you need it - the security officer will get it in half a minute. By the way, there is a gift for him.
Yes, modern backup solutions have agents for all popular software, DBMS and virtual environments. Simply put - understand what data and how to take, how to store and offer the user. It depends on the forethought of the software whether the agent will be able to pick up the base “on the fly” without stopping the service, whether the admin will be able to restore one record in the database in 15 seconds, and whether the blonde user will be able to independently retrieve a letter that he accidentally deleted two years ago. Very important.
I will illustrate . The customer has grown infrastructure, and has grown greatly. A “zoo” of software and hardware appeared, when there are many vendors, many generations of different equipment, many different systems and tasks. Backup tools have become ineffective. First, there are a lot of them: one by one for the subsystem. A separate admin for each case: it’s very hard to monitor everything, to keep the focus, because, as a rule, there are still not enough resources. There are about three hundred consoles for individual installations. And it begins: somewhere something was missed, somewhere something was not seen, then something fell, and now, when it is necessary to recover, it turns out that, oops, 2 months backups are no longer coming! And this, in fact, is quite a life situation. We put one product. He has one administrator. One console. Admin came, looked, opened, all night backups went, everything is fine. And he is sure that everything is fine, that is, if it is necessary, he will recover.
Work with storage systems
These are things that even cost no data like an airplane. And if you screw one, then you can safely go hang yourself - most likely there were not only pictures of your users, but also a couple of terabytes of important financial data. The situation is aggravated by the wonderful fact that many storage systems are connected to servers that constantly need this information. You can not just take and replace such a system, just as you can not just take something quickly there to change. Just the case when "do not fit - kill!".
Therefore, there is such a thing Veritas Storage Foundation. It is needed for different hardware from different manufacturers so that you can do your admin or even service work without stopping the work of business applications. What to do? Anything: change the size and structure of logical volumes, create snapshots or full copies of systems, replicate data.

For each picture - the story of at least one facac from someone else's practice
Once we changed a very old storage system on a system to which it was almost impossible to touch. A mere couple of seconds meant losses of 200–300 thousand dollars. About. In general, we connected the second storage system from another vendor, set up their work in the “mirror” mode using Veritas Storage Foundation, i.e. Got like RAID1, parts of which were two storage systems. Then they waited for data synchronization and simply disconnected the old one. The server did not even notice. You can also make reliable fast data migration between different platforms - HP-UX, Oracle Solaris, IBM AIX. At the same time, the transfer of a large database from one platform to another takes minutes or hours in semi-automatic mode. If you do without such software, it takes days or weeks.
Business Application Continuity
Failures occur at all and often. Seriously, we even have permanent flights (which are undated, the most expensive) for some engineers. Something somewhere in the country broke down - and he jumps on the subway, then to the aeroexpress, then to the plane, and after 4–5 hours on the spot. If necessary.
It helps not to fly once again (and to the customer - not to go into a simple one) package of Veritas Cluster Server. It allows you to quickly respond to the failure of the application, operating system, network or a single node. As soon as a failure is detected, the software happily goes on doing automatic recovery of critical business services at the backup site, regardless of its distance from the main facility. It can be said that the cluster nodes are talking to each other, constantly reporting on their condition. And if an incorrect answer comes from one of them, or there is no answer at all, the second one quickly deploys the reserve. You, as a rule, have time to read a disturbing SMS at the very moment when the work of the services already switches to the backup data center.
The software "out of the box" is integrated with almost all DBMS and OS of corporate level.
Complex Infrastructure Management
When you have only a hundred clusters, problems begin with administration. Most often we are talking about infrastructure such as telecom, a major provider or bank, as well as insurance or major retail. In general, where there can be dozens of storage systems, thousands of normal nodes and several data centers.
The main thing in such an infrastructure is not to miss the moment. In the sense that a problem can sneak up on sight, and its search requires a lot of time. Taking into account that usually all this is also handed down “by inheritance” to new admins, problems happen.
There are Veritas Operations Manager (VOM) and OpsCenter. VOM brings all the consoles of all clusters and logical volume managers into one convenient web-interface. There is also a “traffic light” - it helps to look for problems where they, according to the product, may arise. Which characterizes, helps, and helps great. OpsCenter does roughly the same for individual consoles of backup software.
But, of course, if you like dozens of consoles, then there are no problems to walk directly.

Server Security
String with the intriguing and proud name of Symantec Critical System Protection makes it exactly Critical System Protection. The solution is a highly accurate tool for controlling vulnerabilities, detecting and preventing intrusions. All the same good old expert system that looks for interconnections, strange events, builds profiles of various kinds of activities and can find a possible problem using three or four weak signals. By the way, it is run in Symantec Cyber Challenge - one of the world's largest security competitions, when hackers from around the world break the corporation's network simulator in several stages. Last year, in the EMEA region, a Russian student v0s won - now his patterns, as well as the patterns of the other participants, have expanded the attack library. About how the complex works in theory, my colleague wrote separately here in the educational program on modern information security.
Solution Center
So, we have a kind of infrastructure simulator of a large company (with its large databases, littered machines, clogged storage in branches, complex cases and restless users, more precisely, the results of their work). All this is deployed not only in virtual machines, but also on the physical hardware of six different manufacturers, and on top of all this are installed Symantec solutions that you can come in and touch. Moreover, you can bring your test databases to watch Symantec say “hrrr” on them.
Therefore, drop in for a visit if you need serious software or a PACK. So that it is specifically clear what exactly he is doing, how exactly and where his weak points are. You already know the strengths, but what awaits you after a year of practice in your infrastructure is the most important question. My colleagues and I help answer such questions and show everything as it is, immediately warning about the rake. Fortunately, it is not in our interest to promise something extra - after all, we will have to support all this.
You can find me by mail ADubskiy@croc.ru or register in the center here .
Source: https://habr.com/ru/post/223457/
All Articles