Notes on the results of university career day
Hello% username%!
The well-known expression “Personnel solves everything” in IT companies is relevant, as in no other industry. Much has been written on the topic of staff recruitment, and we would like to focus on the phenomenon of university “Career Day”. Recently, we had the opportunity to participate in a similar event at the faculty of the UMC MSU. In this post we want to share some impressions of what he saw.

')
As you know, to get a competent professional to an employer, you can go in two directions:
Both ways have their advantages and disadvantages. Most companies (and we are among them) in their work combine these approaches. And if everything is more or less clear with the search for a trained professional, then where can we get young and early, able to grow to the required level in a reasonable time?
In this regard, companies that have established links with universities have certain advantages. An expert reading a special course or supervising a graduation project will certainly find contact and establish communication with a budding student. But this option is never massive and deployed in time for many months.
In order to expand the potential “contact zone” between future employees and potential employers, “career days” were invented - such special events in which both sides of the process can quickly understand who is worth something and start a relationship that with proper attention and responsibility can be long and happy .
In general, if “career days” exist, it is not a sin to use them. We decided to work on the faculty of the Moscow Metro University, and with positive experience, to extend it to other educational institutions.

An employer to become a member of the Career Day is easy. These events are announced in advance, they are organized by specially appointed people - in our case, these were specialists from the Center for Employment of the VMC. After short negotiations, we were part of the companies participating in Career Day 2014 (there were sixteen such companies altogether).
There is usually not much time for preparation. Here a very good help is the experience of participation in exhibitions, forums, conferences and other similar public events. The point of presence of the company at the Career Day is a stand with its representatives, promotional materials and equipment. Only the products and services are not advertised on the stand, but the organization itself as an employer. And of course the stand is the place where you can look at the potential contingent of beginning specialists.
We are not going to “discover America” in matters of booth preparation. Unless the specifics of the materials should be appropriate - going to the Career Day, the employer should stock up at least with descriptions of vacancies and internships that he can offer to those interested. Some of our colleagues issued forms of questionnaires for those who wish to fill out - this is also a good decision. Any accompanying buns such as small corporate gifts, sweets and cookies are certainly welcomed by the grateful student community.
A big plus would be the presence on the stand of a pretty, friendly girl. In addition to jokes, many shy students (at the VMK there are those!) Are more comfortable to start communicating with the lady rather than with the brave unshaven IT brutal present here.

Of course, it is necessary to prepare in advance for answering the questions “What does the company do”, “What are the working conditions”, and also “What color are the chairs in the office” (aha, exactly such questions are advised to ask here .
In principle, the work of company representatives on the Career Day is made up of obvious things - communication, answers to questions, exchange of contacts, etc. So let me not go deep here, but say a few words about the chips.
In order for these reciprocal bridegazines to be (a) more productive and (b) more interesting, we decided at the event described to arrange small technical competitions for visitors of Career Day. For the company - the simplest filter that selects active and intelligent, for visitors - the ability to show themselves, stretch their brains and the prize (sic!) To receive.
Competition tasks we come up from three different areas of interest to us as an employer. The first task was devoted to working with social networks, the second - the security of wireless LANs, and the third - the restoration of information on the media. The level of difficulty in the preparation of tasks for themselves identified as generally low, because everything happens in parallel with the educational process and very few people have enough time for competitions.
At the request of booth visitors, we publish information on contests.
At once we will say that, despite our expectations, this task did not become a hit. Perhaps, the students considered the first task of the proposed list to be difficult, or maybe the reason is something else. The competition involved a number of tasks for the construction and analysis of a social graph (this piece has a lot of applications in marketing). The graph was going to be formed on the basis of data provided by the users of one of the popular social networks.
So, the starting task of the competition “VMK in VK” was the collection of basic data for a social graph. She sounded like this:
Write or find an application that will allow you to get from the social network "Vkontakte" a list of students of the VMK MSU of your year of graduation, information from their profiles (at least - first name, last name and gender) and their connection with each other.
Since the API can be used to collect data from Vkontakte, the participants were supposed to follow the next path. First, register the Standalone application by reference . After creating the application, a page with information about it will open, the application ID is indicated in the page URL, and you can also find it on the Settings tab. To authorize the application and get the token, you need to open the page, substituting the received application ID instead of
the address bar will be
The value
Authorization is needed to use the
To work with the API, you can use the Ruby library VK-ruby . The following simple script is intended to obtain information about users who have indicated the VMK of Moscow State University as a teaching faculty and their friends (we expected to see something like this among the participants). Data is collected for users indicating the 2012–2021 release date.
The data is saved in JSON format, which has the following form.
For further use of graph analysis tools (and this is almost all the remaining tasks of the competition “VMC in VK”), it is necessary to convert the collected data into another format. The code below allows you to get a list of the edges of the graph of friends of users for each of the specified release years.
Each line of received CSV files will have the following format
Data of this format can be downloaded in most graph analysis tools.
(In principle, we carried out work on obtaining these data in advance and were ready to share them on the stand. Tips were announced, but there was no line for them - so much for your interest in social networks from modern youth)
Task number 2 assumed the implementation of the minimum analysis of the data: gender composition, users with the largest number of friends, the average number of friends per user. It was expected that the problem would be solved using simple scripts. There are many approaches to writing them; we will not focus on this. Cymes task (and additional points) - in another. Where is the analyst who would come to us and say: “Yes, bots and some left-wing personalities are nemeryan here?” This conclusion is in general simple, rather look at the collected information more closely, or rather, at the lists of “friends” .
As the name implies, task number 3 - “Drawing Lesson” - consisted in visualizing the acquired by overworking in solving the first task. “Probably everyone will use Gephi , there shouldn't be any problems,” we thought. But did not grow together. We didn’t wait for the images of the social graph of the VMC in the VC from our contestants. By the way, the social graphs of the current courses of the faculty, drawn in i2 Analyst's Notebook, were shown as an example for the participants (unlike the free Gephi, this is a commercial product from IBM).
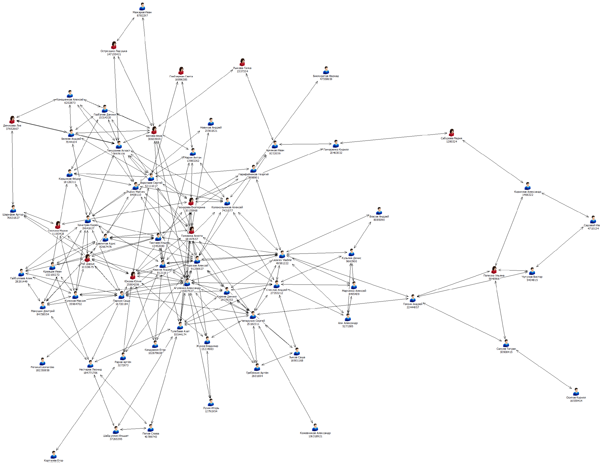
In general, if desired, it was possible to find other tools for visualizing the social graph.
Finally, the final task number 4 of this competition was the most “mathematical”: the diameter of the maximum connected component of the graph, the density of the graph, the centrality metrics of the vertices, the centrality of its own vector, the centrality of the “intermediateness” ... All the same Gephi to help, or rather its built tools for analyzing social graph.
The conclusion of the first competition is this: despite the expected personal interest ("yes, this is about us!") And the general interest in the topic of social networks - the tasks "did not go." Either time to google and a little bit was not enough, or the task seemed too academic. Or perhaps the interest was interrupted by other contests - it was there that it was suggested that terrorist rascal terrorists should be caught and puzzles solved on a flash drive!
As follows from the assignment, the dog is buried in a wireless network. We launched this network for the period of the Career Day in the lobby of the faculty. They drove over the network (via HTTP) from one laptop to another in GIF format. The pictures were QR codes that hid the coordinates of “objects of interest” in Moscow and St. Petersburg (for example, the House of Government of the Russian Federation, Sheremetyevo Airport, the Foreign Ministry, Luzhniki, the All-Russian Exhibition Center, the cruiser Aurora, and so on, ending with the Moscow Zoo). A small script was responsible for repeating the transmission of a series of 20 drawings with a frequency of once every 30 seconds.
Further kul-hackers and veterans of ward-riding may not be very exciting, but for those who "guessed all the letters, but could not name the word" - a small comment.
Turning on the WiFi adapter on a laptop and trying to “listen to the broadcast”, the contestants who took on this task easily discovered an unprotected WiFi network called vulkan. To intercept open traffic on the WiFi network, it was supposed to use tools like Wireshark , tcpdump and tede by the participants. It is probably not entirely appropriate to talk about how to use this software, it is easier to look here and here .
After intercepting traffic in it, it was possible to detect images of the following form:

A further logical step is the recognition of the received QR codes and obtaining information about the geographical coordinates (latitude and longitude) of objects. At the final stage - we enter the coordinates into a search engine or into a geo-service, we get a point on the map and ...
Alex hoped for Eustace not in vain. Congratulations to the winners! By the way, nobody seems to have saved the zoo.
This competition was perhaps the most popular. Perhaps because in addition to the flyer with the task the contestant was awarded a flash drive. Yes, and the task fit into one sentence: in the depths of the flash drive "carefully" hidden files: image, text and archive - find them! But behind the apparent simplicity was a real brain explosion. Why?
When preparing the contest, it was necessary to figure out how to hide the information. Different ideas were expressed: to make a “lost” section on the carrier and save information to it, to make a steganocontainer from a picture ... A necessary condition was the combination of “open” information (our advertisement, yes) and “hidden”. We stopped at the idea when the information is recorded outside the section. To simplify information retrieval, the carrier must be initially initialized with zeros. We decided to record some of the information before the section, and some after. Regarding approaches to recovery, three levels of difficulty were identified: recovery in automatic mode (using data recovery utilities), manually (hex editors of disks), and for dessert - simple steganography.
The object of the first level of complexity was a jpeg-file. It was “put” in 1024 sector from the end of the partition in the form of a continuous block. In the end, against the background of zeros, it should have been noticeable.
The object for manual recovery was the text (borrowed some pearls on bash.im). And the text is fragmented. At the end of each fragment, we recorded the number of the sector in which the next fragment is located. To prevent the task from appearing too simple, Unicode was used for the main text, and the pointer to the next sector was presented as a decimal number in ASCII. As a starting sector for the chain took sector number 1024. Here we must say that our section began with sector No. 2048. We placed the fragments in the following chain: 1024 => 964 => 475 => 235 => 1800 => 1720 => 823 => 615 => 1100 => 1920 => 345 => 1418 => 1634 => 1980 => 1320 In the first fragment was the text "Vulkan - task.", And at the end - information that "Here you have reached the end of the task ..."
The object of the third level of complexity is the rar archive, added to the end of the jpeg file. As you know, the rar archiver searches for its initial signature across the entire file, which allows you to save the rar archive at the end of an arbitrary file, for example jpeg. When automatically restore jpeg file size will be determined by the title, and the rest will be cut off, and only the curious will be able to determine the presence of the archive. In the archive, we put a document "Vulkan.docx" with a quote from the respected by all IT specialists A.S. Pushkin. At the last moment we decided to password-protect the archive with the word “Vulkan” (the phrase “Vulcan is the“ key ”to everything” as a hint of the password to the archive and the initial fragment was posted on the task sheet).
We assumed that the participants in the competition would first restore the image, then the text, and there it was within reach of the archive. But realizing that in conditions of limited time, something could “go wrong” - we prepared several tips.
The search for the signature of the rar archive should have brought the participants to the end of the jpeg file. The end of the archive could be determined by a sequence of zeros written at the end. Highlighting the archive, the participants were faced with the need to specify the correct password (ninth tip to help).
In general, yes, the organizers are clearly namudri)
The competition decided to participate a few dozen people. Having tried to find information on their own, the students began to organize teams of two or three people. Someone went on assignment to a lecture, and then complained that they had forbidden to “play” on laptops in class. Lack of time was on the face ...
What are the results? The object of the first difficulty level was found by two single participants and three creative duos. The object of the second level was not given to anyone. Finally, one team was close to finding the third object 10 minutes before the debriefing, but the guys had a problem with determining the end of the file.
Nevertheless, the awards found their heroes - the participants who achieved the best results - both in this and in two other competitions.
It all ended with abath and barbecue a mini-lecture on low-level work with machine carriers.
We believe that the event was a success. The atmosphere is spiritual, the interest is genuine. The results will become clear later, but we can already say that with proper preparation, such meetings can be very productive. Career days attract literally everyone - from freshmen to graduate students. We even had a chance to talk with a graduate of the year before last, who decided to look for something new for himself on the Career Day of his native department.
To be honest, we tried to put a piece of our IT soul into this event. We hope that everyone was satisfied and received considerable benefit from the incident.
The well-known expression “Personnel solves everything” in IT companies is relevant, as in no other industry. Much has been written on the topic of staff recruitment, and we would like to focus on the phenomenon of university “Career Day”. Recently, we had the opportunity to participate in a similar event at the faculty of the UMC MSU. In this post we want to share some impressions of what he saw.

Content
')
Part One, Organizational
As you know, to get a competent professional to an employer, you can go in two directions:
- find a ready-made specialist in the market;
- independently “grow” an employee with the required competencies.
Both ways have their advantages and disadvantages. Most companies (and we are among them) in their work combine these approaches. And if everything is more or less clear with the search for a trained professional, then where can we get young and early, able to grow to the required level in a reasonable time?
In this regard, companies that have established links with universities have certain advantages. An expert reading a special course or supervising a graduation project will certainly find contact and establish communication with a budding student. But this option is never massive and deployed in time for many months.
In order to expand the potential “contact zone” between future employees and potential employers, “career days” were invented - such special events in which both sides of the process can quickly understand who is worth something and start a relationship that with proper attention and responsibility can be long and happy .
In general, if “career days” exist, it is not a sin to use them. We decided to work on the faculty of the Moscow Metro University, and with positive experience, to extend it to other educational institutions.

An employer to become a member of the Career Day is easy. These events are announced in advance, they are organized by specially appointed people - in our case, these were specialists from the Center for Employment of the VMC. After short negotiations, we were part of the companies participating in Career Day 2014 (there were sixteen such companies altogether).
There is usually not much time for preparation. Here a very good help is the experience of participation in exhibitions, forums, conferences and other similar public events. The point of presence of the company at the Career Day is a stand with its representatives, promotional materials and equipment. Only the products and services are not advertised on the stand, but the organization itself as an employer. And of course the stand is the place where you can look at the potential contingent of beginning specialists.
We are not going to “discover America” in matters of booth preparation. Unless the specifics of the materials should be appropriate - going to the Career Day, the employer should stock up at least with descriptions of vacancies and internships that he can offer to those interested. Some of our colleagues issued forms of questionnaires for those who wish to fill out - this is also a good decision. Any accompanying buns such as small corporate gifts, sweets and cookies are certainly welcomed by the grateful student community.
A big plus would be the presence on the stand of a pretty, friendly girl. In addition to jokes, many shy students (at the VMK there are those!) Are more comfortable to start communicating with the lady rather than with the brave unshaven IT brutal present here.

Of course, it is necessary to prepare in advance for answering the questions “What does the company do”, “What are the working conditions”, and also “What color are the chairs in the office” (aha, exactly such questions are advised to ask here .
In principle, the work of company representatives on the Career Day is made up of obvious things - communication, answers to questions, exchange of contacts, etc. So let me not go deep here, but say a few words about the chips.
Part two, practical
In order for these reciprocal bridegazines to be (a) more productive and (b) more interesting, we decided at the event described to arrange small technical competitions for visitors of Career Day. For the company - the simplest filter that selects active and intelligent, for visitors - the ability to show themselves, stretch their brains and the prize (sic!) To receive.
Competition tasks we come up from three different areas of interest to us as an employer. The first task was devoted to working with social networks, the second - the security of wireless LANs, and the third - the restoration of information on the media. The level of difficulty in the preparation of tasks for themselves identified as generally low, because everything happens in parallel with the educational process and very few people have enough time for competitions.
At the request of booth visitors, we publish information on contests.
The first competition. "VMK in VK"
At once we will say that, despite our expectations, this task did not become a hit. Perhaps, the students considered the first task of the proposed list to be difficult, or maybe the reason is something else. The competition involved a number of tasks for the construction and analysis of a social graph (this piece has a lot of applications in marketing). The graph was going to be formed on the basis of data provided by the users of one of the popular social networks.
So, the starting task of the competition “VMK in VK” was the collection of basic data for a social graph. She sounded like this:
Write or find an application that will allow you to get from the social network "Vkontakte" a list of students of the VMK MSU of your year of graduation, information from their profiles (at least - first name, last name and gender) and their connection with each other.
Since the API can be used to collect data from Vkontakte, the participants were supposed to follow the next path. First, register the Standalone application by reference . After creating the application, a page with information about it will open, the application ID is indicated in the page URL, and you can also find it on the Settings tab. To authorize the application and get the token, you need to open the page, substituting the received application ID instead of
%ID%oauth.vk.com/oauth/authorize?client_id=%ID%&response_type=token&_hash=0the address bar will be
oauth.vk.com/blank.html#access_token=%TOKEN%&expires_in=86400&user_id=%UID%The value
%TOKEN% must be saved for future use.Authorization is needed to use the
users.search method to search for specified users. Lists of friends can be obtained without authorization by reference. api.vk.com/method/friends.get?user_id=%UID% api.vk.com/method/friends.get?user_id=%UID% in JSON.To work with the API, you can use the Ruby library VK-ruby . The following simple script is intended to obtain information about users who have indicated the VMK of Moscow State University as a teaching faculty and their friends (we expected to see something like this among the participants). Data is collected for users indicating the 2012–2021 release date.
Script to get data
require 'open-uri' require 'vk-ruby' require 'json' token = "%TOKEN%" (2012..2021).each do |year| app = VK::Application.new access_token: "#{token}" users = [] offset = 0 begin us = app.users.search(university: 2, university_faculty: 23, university_year: year, count: 1000, fields: 'sex', offset: offset) users += us[1..-1] offset += 1000 end while us.length > 1 cmc_uids = Set.new users.map{|u| u['uid']} users.map! do |u| uid = u['uid'] page = open("https://api.vk.com/method/friends.get?user_id=#{uid}").read friends_ids = Set.new JSON.parse(page)['response'] u['friends'] = friends_ids.to_a cmc_friends = friends_ids.intersection cmc_uids u['cmc_friends'] = cmc_friends.to_a u end File.open('cmc_' + year.to_s + '.json', 'w') { |file| file.write(users.to_json.gsub(/,\{/, ",\n{")) } end The data is saved in JSON format, which has the following form.
[{"uid":%UID%, "first_name":"%_%", "last_name":"%_%", "sex":%%, "friends":[%ID_%], "cmc_friends":[%ID_______%]},...] For further use of graph analysis tools (and this is almost all the remaining tasks of the competition “VMC in VK”), it is necessary to convert the collected data into another format. The code below allows you to get a list of the edges of the graph of friends of users for each of the specified release years.
Script to convert to csv
require 'json' require 'csv' (2012..2021).each do |year| users = JSON.parse File.read('cmc_' + year.to_s + '.json') names_hash = Hash[users.map{|u| [u['uid'], "#{u['last_name']} #{u['first_name']}"]}] sex_hash = Hash[users.map{|u| [u['uid'], u['sex']]}] res = users.map do |u| u['cmc_friends'].map do |id2| ["#{u['last_name']} #{u['first_name']}", u['sex'], u['uid'], id2] end end.flatten(1) CSV.open("#{year}.csv", 'w'){|csv| res.each{|u| csv << u}} end Each line of received CSV files will have the following format
%_%,%%,%ID_%,%ID_%Data of this format can be downloaded in most graph analysis tools.
(In principle, we carried out work on obtaining these data in advance and were ready to share them on the stand. Tips were announced, but there was no line for them - so much for your interest in social networks from modern youth)
Task number 2 assumed the implementation of the minimum analysis of the data: gender composition, users with the largest number of friends, the average number of friends per user. It was expected that the problem would be solved using simple scripts. There are many approaches to writing them; we will not focus on this. Cymes task (and additional points) - in another. Where is the analyst who would come to us and say: “Yes, bots and some left-wing personalities are nemeryan here?” This conclusion is in general simple, rather look at the collected information more closely, or rather, at the lists of “friends” .
As the name implies, task number 3 - “Drawing Lesson” - consisted in visualizing the acquired by overworking in solving the first task. “Probably everyone will use Gephi , there shouldn't be any problems,” we thought. But did not grow together. We didn’t wait for the images of the social graph of the VMC in the VC from our contestants. By the way, the social graphs of the current courses of the faculty, drawn in i2 Analyst's Notebook, were shown as an example for the participants (unlike the free Gephi, this is a commercial product from IBM).

In general, if desired, it was possible to find other tools for visualizing the social graph.
Finally, the final task number 4 of this competition was the most “mathematical”: the diameter of the maximum connected component of the graph, the density of the graph, the centrality metrics of the vertices, the centrality of its own vector, the centrality of the “intermediateness” ... All the same Gephi to help, or rather its built tools for analyzing social graph.
The conclusion of the first competition is this: despite the expected personal interest ("yes, this is about us!") And the general interest in the topic of social networks - the tasks "did not go." Either time to google and a little bit was not enough, or the task seemed too academic. Or perhaps the interest was interrupted by other contests - it was there that it was suggested that terrorist rascal terrorists should be caught and puzzles solved on a flash drive!
Second contest. Alex Yustau
As follows from the assignment, the dog is buried in a wireless network. We launched this network for the period of the Career Day in the lobby of the faculty. They drove over the network (via HTTP) from one laptop to another in GIF format. The pictures were QR codes that hid the coordinates of “objects of interest” in Moscow and St. Petersburg (for example, the House of Government of the Russian Federation, Sheremetyevo Airport, the Foreign Ministry, Luzhniki, the All-Russian Exhibition Center, the cruiser Aurora, and so on, ending with the Moscow Zoo). A small script was responsible for repeating the transmission of a series of 20 drawings with a frequency of once every 30 seconds.
Further kul-hackers and veterans of ward-riding may not be very exciting, but for those who "guessed all the letters, but could not name the word" - a small comment.
Turning on the WiFi adapter on a laptop and trying to “listen to the broadcast”, the contestants who took on this task easily discovered an unprotected WiFi network called vulkan. To intercept open traffic on the WiFi network, it was supposed to use tools like Wireshark , tcpdump and tede by the participants. It is probably not entirely appropriate to talk about how to use this software, it is easier to look here and here .
After intercepting traffic in it, it was possible to detect images of the following form:

A further logical step is the recognition of the received QR codes and obtaining information about the geographical coordinates (latitude and longitude) of objects. At the final stage - we enter the coordinates into a search engine or into a geo-service, we get a point on the map and ...
Alex hoped for Eustace not in vain. Congratulations to the winners! By the way, nobody seems to have saved the zoo.
The third competition. “Hide and Seek on a Flash Drive”
This competition was perhaps the most popular. Perhaps because in addition to the flyer with the task the contestant was awarded a flash drive. Yes, and the task fit into one sentence: in the depths of the flash drive "carefully" hidden files: image, text and archive - find them! But behind the apparent simplicity was a real brain explosion. Why?
When preparing the contest, it was necessary to figure out how to hide the information. Different ideas were expressed: to make a “lost” section on the carrier and save information to it, to make a steganocontainer from a picture ... A necessary condition was the combination of “open” information (our advertisement, yes) and “hidden”. We stopped at the idea when the information is recorded outside the section. To simplify information retrieval, the carrier must be initially initialized with zeros. We decided to record some of the information before the section, and some after. Regarding approaches to recovery, three levels of difficulty were identified: recovery in automatic mode (using data recovery utilities), manually (hex editors of disks), and for dessert - simple steganography.
The object of the first level of complexity was a jpeg-file. It was “put” in 1024 sector from the end of the partition in the form of a continuous block. In the end, against the background of zeros, it should have been noticeable.
The object for manual recovery was the text (borrowed some pearls on bash.im). And the text is fragmented. At the end of each fragment, we recorded the number of the sector in which the next fragment is located. To prevent the task from appearing too simple, Unicode was used for the main text, and the pointer to the next sector was presented as a decimal number in ASCII. As a starting sector for the chain took sector number 1024. Here we must say that our section began with sector No. 2048. We placed the fragments in the following chain: 1024 => 964 => 475 => 235 => 1800 => 1720 => 823 => 615 => 1100 => 1920 => 345 => 1418 => 1634 => 1980 => 1320 In the first fragment was the text "Vulkan - task.", And at the end - information that "Here you have reached the end of the task ..."
The object of the third level of complexity is the rar archive, added to the end of the jpeg file. As you know, the rar archiver searches for its initial signature across the entire file, which allows you to save the rar archive at the end of an arbitrary file, for example jpeg. When automatically restore jpeg file size will be determined by the title, and the rest will be cut off, and only the curious will be able to determine the presence of the archive. In the archive, we put a document "Vulkan.docx" with a quote from the respected by all IT specialists A.S. Pushkin. At the last moment we decided to password-protect the archive with the word “Vulkan” (the phrase “Vulcan is the“ key ”to everything” as a hint of the password to the archive and the initial fragment was posted on the task sheet).
We assumed that the participants in the competition would first restore the image, then the text, and there it was within reach of the archive. But realizing that in conditions of limited time, something could “go wrong” - we prepared several tips.
Tips
The first hint indicated the possibility of recovery with automatic utilities (with an indication of the appropriate programs). As they say, take it and use it!
The second hint indicated the need for media analysis using disk hex editors (some of them were listed as an example).
The third hint said that at the beginning of the disk is the MBR, which indicates the free and busy sectors. We hoped that the participants would pay attention to the interval from 1 to 2047 sectors, in which "suddenly" there were data.
The fourth hint suggested that a text document could be a sequence of characters in some encoding.
The fifth hint said that the characters can be represented in both UNICODE and ASCII. Switching between the display types of encodings in the HEX editor should help to see the text and numbers at the end. To attract attention, the symbol “=” was used.
The sixth hint said that in any file system the sequence in which the sectors were read was set, and once again there was a reminder about the fifth hint and the need to search for the initial fragment.
A review by the hex editors of the open section (hint # 2) should have shown participants the lack of additional information in the open section and encouraged them to search outside the section (hint # 3). The beginning of the section from the 2048 sector should have paid attention to the section from 1 to 2047 sectors. Of course, someone could accidentally bump into a block of data, but we did not expect such accidents. Since the carrier was “clearly zeroed out,” it was necessary to compare this section with the zero region. Then the participant will immediately see the sector with the data. To simplify the interpretation of the data, prompts 4 and 5 were made. Tip 6 helped to switch to ASCII at the end of the UNICODE part.
The seventh hint indicated the different file types and their signatures. Among them was the signature of the rar-archive.
The eighth hint pointed to the initial sectors of the text file and the jpeg file.
The ninth hint is the repetition of the “hint” from the task-leaflet: “Vulkan is the“ key ”to everything!”
The second hint indicated the need for media analysis using disk hex editors (some of them were listed as an example).
The third hint said that at the beginning of the disk is the MBR, which indicates the free and busy sectors. We hoped that the participants would pay attention to the interval from 1 to 2047 sectors, in which "suddenly" there were data.
The fourth hint suggested that a text document could be a sequence of characters in some encoding.
The fifth hint said that the characters can be represented in both UNICODE and ASCII. Switching between the display types of encodings in the HEX editor should help to see the text and numbers at the end. To attract attention, the symbol “=” was used.
The sixth hint said that in any file system the sequence in which the sectors were read was set, and once again there was a reminder about the fifth hint and the need to search for the initial fragment.
A review by the hex editors of the open section (hint # 2) should have shown participants the lack of additional information in the open section and encouraged them to search outside the section (hint # 3). The beginning of the section from the 2048 sector should have paid attention to the section from 1 to 2047 sectors. Of course, someone could accidentally bump into a block of data, but we did not expect such accidents. Since the carrier was “clearly zeroed out,” it was necessary to compare this section with the zero region. Then the participant will immediately see the sector with the data. To simplify the interpretation of the data, prompts 4 and 5 were made. Tip 6 helped to switch to ASCII at the end of the UNICODE part.
The seventh hint indicated the different file types and their signatures. Among them was the signature of the rar-archive.
The eighth hint pointed to the initial sectors of the text file and the jpeg file.
The ninth hint is the repetition of the “hint” from the task-leaflet: “Vulkan is the“ key ”to everything!”
The search for the signature of the rar archive should have brought the participants to the end of the jpeg file. The end of the archive could be determined by a sequence of zeros written at the end. Highlighting the archive, the participants were faced with the need to specify the correct password (ninth tip to help).
In general, yes, the organizers are clearly namudri)
The competition decided to participate a few dozen people. Having tried to find information on their own, the students began to organize teams of two or three people. Someone went on assignment to a lecture, and then complained that they had forbidden to “play” on laptops in class. Lack of time was on the face ...
What are the results? The object of the first difficulty level was found by two single participants and three creative duos. The object of the second level was not given to anyone. Finally, one team was close to finding the third object 10 minutes before the debriefing, but the guys had a problem with determining the end of the file.
Nevertheless, the awards found their heroes - the participants who achieved the best results - both in this and in two other competitions.
It all ended with a
Conclusion
We believe that the event was a success. The atmosphere is spiritual, the interest is genuine. The results will become clear later, but we can already say that with proper preparation, such meetings can be very productive. Career days attract literally everyone - from freshmen to graduate students. We even had a chance to talk with a graduate of the year before last, who decided to look for something new for himself on the Career Day of his native department.
To be honest, we tried to put a piece of our IT soul into this event. We hope that everyone was satisfied and received considerable benefit from the incident.
Source: https://habr.com/ru/post/222919/
All Articles


