Investigation of manipulations with the control panel. Part 2
Hello!
Today we continue the story about the methods of investigations and the collection of evidence to launch applets of the Windows Control Panel.
The first part of the material on this topic is available here.
Let me remind you that with the release of Windows 7, the UserAssist mechanism has undergone significant changes. Collecting reliable evidence of running applets is not supported on Windows7 | 8 systems; instead, we can use the so-called. jump lists (jumplists), a source of information containing traces of launching applets.
')
In modern Windows OS, conversion lists are one of the most important sources of information for investigations, including the necessary traces of launching Control Panel applets that we need. Author Harlan Carvey has written an excellent post on conversion lists. In it, he tells in detail about the structure and practical application of lists.
To collect information related to the Control Panel, we need a list with the ID 7e4dca80246863e3 (a list of all identifiers ). The full path to the list of transitions looks like this:
Please note that the conversion lists are unique for each user profile.
Look at the picture and note an important point: each Control Panel applet has a Windows class identifier (CLSID, in the JumpList program it is presented in the form of a global GUID). CLSID / GUIDs are used in jumplists in order to fix the execution of the applet. In our example, the identifier {E2E7934B-DCE5-43C4-9576-7FE4F75E7480} corresponds to the Date and Time applet (timedate.cpl). The MSDN library contains a map of all applets and their identifiers.

It is recommended to use identifiers of well-known applets to search for user actions. For example, as we see in the figure, the last launch of the Date and Time applet took place on April 5, 2013. at 06:53:33, and its owner launched this particular list. Unlike the Prefetch and UserAssist mechanisms, information about the time of the first launch and the number of launches cannot be obtained (this information can be obtained using shadow backups). The JumpLister tool was developed by Mark Woan, already known to us.
Now let's look at the big picture, imagine that in the process of parsing magazines you see this event:
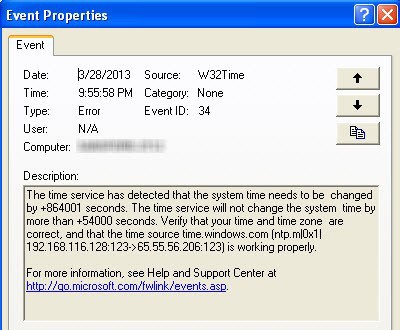
A simple calculation allows you to understand that 864001 second is just 10 days. You are looking for prefetch files that were modified approximately 10 days after the event from the log (ie, the date of the change should be 03/28/2013 + 10 days) and you see the following traces:

Thus, you have collected evidence that the system time has been changed. It remains to find who changed it? Using the UserAssist key corresponding to the account of the suspect, you find the missing 'evidence':

In case the audit policy has been configured so that system events are logged, you will see evidence of time manipulations in the security log. Full information will be displayed, including the user account that has transferred the time. Traces in the system make it possible to unambiguously identify the account on whose behalf any Control Panel applet opened. In order to define the attacker's goals, additional context may be required. For example, in case the user transferred time back to fake the date of the e-mail, we will need to analyze security logs, letter metadata and other additional tools and sources.
Today we continue the story about the methods of investigations and the collection of evidence to launch applets of the Windows Control Panel.
The first part of the material on this topic is available here.
Let me remind you that with the release of Windows 7, the UserAssist mechanism has undergone significant changes. Collecting reliable evidence of running applets is not supported on Windows7 | 8 systems; instead, we can use the so-called. jump lists (jumplists), a source of information containing traces of launching applets.
')
Jump Lists in Windows 7/8 (Jumplists)

In modern Windows OS, conversion lists are one of the most important sources of information for investigations, including the necessary traces of launching Control Panel applets that we need. Author Harlan Carvey has written an excellent post on conversion lists. In it, he tells in detail about the structure and practical application of lists.
To collect information related to the Control Panel, we need a list with the ID 7e4dca80246863e3 (a list of all identifiers ). The full path to the list of transitions looks like this:
%user profile%\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations \7e4dca80246863e3.automaticDestinations-ms Please note that the conversion lists are unique for each user profile.
Look at the picture and note an important point: each Control Panel applet has a Windows class identifier (CLSID, in the JumpList program it is presented in the form of a global GUID). CLSID / GUIDs are used in jumplists in order to fix the execution of the applet. In our example, the identifier {E2E7934B-DCE5-43C4-9576-7FE4F75E7480} corresponds to the Date and Time applet (timedate.cpl). The MSDN library contains a map of all applets and their identifiers.

It is recommended to use identifiers of well-known applets to search for user actions. For example, as we see in the figure, the last launch of the Date and Time applet took place on April 5, 2013. at 06:53:33, and its owner launched this particular list. Unlike the Prefetch and UserAssist mechanisms, information about the time of the first launch and the number of launches cannot be obtained (this information can be obtained using shadow backups). The JumpLister tool was developed by Mark Woan, already known to us.
Collect all the evidence and see the big picture.
Now let's look at the big picture, imagine that in the process of parsing magazines you see this event:

A simple calculation allows you to understand that 864001 second is just 10 days. You are looking for prefetch files that were modified approximately 10 days after the event from the log (ie, the date of the change should be 03/28/2013 + 10 days) and you see the following traces:

Thus, you have collected evidence that the system time has been changed. It remains to find who changed it? Using the UserAssist key corresponding to the account of the suspect, you find the missing 'evidence':

In case the audit policy has been configured so that system events are logged, you will see evidence of time manipulations in the security log. Full information will be displayed, including the user account that has transferred the time. Traces in the system make it possible to unambiguously identify the account on whose behalf any Control Panel applet opened. In order to define the attacker's goals, additional context may be required. For example, in case the user transferred time back to fake the date of the e-mail, we will need to analyze security logs, letter metadata and other additional tools and sources.
Source: https://habr.com/ru/post/222089/
All Articles