What is HP TippingPoint in simple terms?
I often come across the fact that introducing a complex product on IT security, many do not remember how it all began, how it developed, etc. In this review, I want to remind you that all processes have their own logic, that the reactive model of IT security loses the proactive model, etc.
I’ll say right away that TippingPoint can live in and of itself - as a separate domain, and as part of HP’s cloud technologies.
')
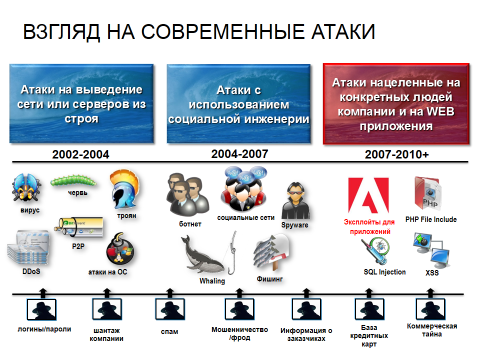
If we look at the development of the market, we will see that the market almost all the time “depended” directly on vulnerabilities. Let's go through the history of these bugs:
2002 is mostly worms and viruses. Antivirus coped with this.
2004 - 2007 - due to the advent of social networks, social engineering related vulnerabilities were developed. Every kind of phishing. No penetration to the forehead, like a virus. More workarounds are used, more sophisticated. Spyver, statistics, etc.
2010+ already in our time, hackers have switched not to general information, but to something specific, these are exploits for applications. For this reason, they began to refuse the Adobe Flash Player plugin because hackers chose it as an ideal hacking point.
The objects of the current attacks are not specific people, they are attacks on the web (clouds), on companies. Everyone knows that there is a black market where you can order a hacking of some company, which, of course, depends on the customers' material injections.
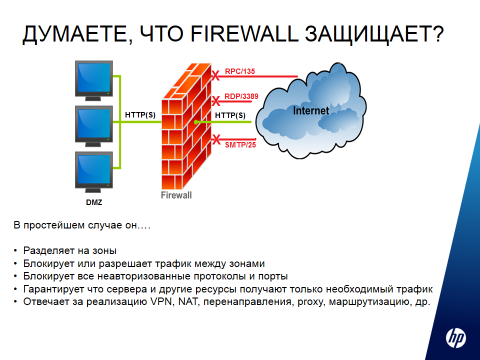
Yes, there is, but the fact is that the malicious code does not follow any unusual paths, it goes through normal HTTP traffic. Codes go through port 80, which is always open, as companies, no matter how cool you need, the Internet does not protect.
Antivirus is reactive protection. It protects against already known hacks and attacks. Here is a table showing that there is a software that even antivirus parsit.

Take the most famous. RSA is a company that issues certificates. It was enough to crack the root certificate in order to generate your own, which will be accepted in all companies where RSA gave its certificates - go wherever you want. And how the hacking was carried out - it was not an ordinary “head-on attack”, it was social engineering. The file came, and got into spam, but for some reason one of the employees decided to see what was there (hands to tear off!), And opened this file. An exploit unknown and unknown to any antivirus, and the company became infected. It is clear how it hit the company's business, not to mention the image. This led to the company changing even tokens.
In general, any software, if you pick it intently, has vulnerabilities. Because people, not gods, write programs. Already, the software has written so much that finding a hole is practically no problem.
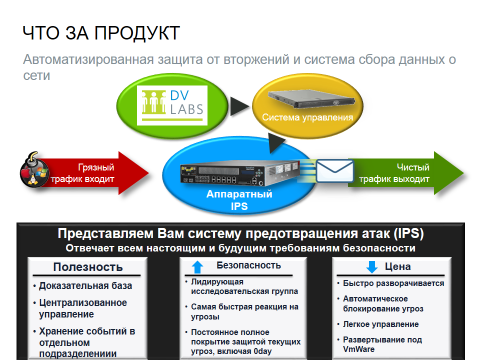
Attack Prevention System is a software and hardware system for detecting and blocking attacks that allow firewalls to pass through. Modern IPSs not only block attacks, but also control network connections and protocols. IPS software versions are used to protect virtualization (and cloud services).
How an ordinary antivirus works - it searches for signatures. And, having found, he says - this is a virus. IPS is looking for exploits, not looking for the results of hacks (which is late), but for suspicious activity. And looks at the general vulnerability. Since the vulnerabilities are also not the same and are used in different ways by crackers. What is meant: there is some N vulnerability, one virus can use 50% of this vulnerability - this part was found, some of the “hole” was patched, but another virus uses another 50% of the “hole” that was not fully patched, etc. . IPS - immediately sees all 100% of the vulnerability.
He constantly lets all traffic through him, works as a filter — it goes “dirty” and pure traffic comes out of it. In the network infrastructure, it looks like a virtual cable. And very easy to administer.
It does not track the virus itself (although, of course, it can track infected exe files), but track the hacking attempt itself: port scans, network anomalies, and service when the site is bombed.
Besides the fact that he filters the Internet, he can investigate traffic within the company - you can find out who is “naughty” within the company's network. Legally, it also closes many problems — for example, Visa requires compliance with its standards. When you install IPS, you automatically close the requirements for these standards.
Why do I need an IPS?
- Enterprise Management
• Timely detection of network problems
- to the financier
• Reducing the cost of eliminating the effects of attacks
• Reduced incident investigation costs
• Reduced TCO, CapEx and OpEx
- Internal audit or risk management
• Risk reduction
- IT security
• Detection and reflection of attacks on various services and resources of the enterprise
• Network protocol control
- IT specialist
• Ensuring high availability and resiliency of internal and external Internet resources
• Bandwidth Management




Admins were interviewed about the ease of TP installation. We put, go to the site, and as in the Google store, you can choose what you need, for example: "the most popular hacks in March 2014" - and immediately closed all vulnerabilities. Or choose what you want to protect: server, site, etc.
Initially, it was a separate product. Then 3Com bought it, and when HP acquired 3Com, the product was further developed. He is now in the Gartner quadrant.

As I already wrote, from the point of view of a hacker it is “more profitable” to use not the entire hole, but only a part of it. There is a vulnerability, something is written under it: an exe-file, a batch file or something else. This does not mean that the entire vulnerability is used, only part of it is used. Anti-Virus, if familiar with the exploit, will protect against a known (part) vulnerability + false positive, where it can paranoidly ban normal programs for itself. A new exploit may use another part of the same vulnerability - the antivirus will not even notice it. TippingPoint does not treat exploits, but vulnerabilities. Through continuous monitoring of traffic. He sees that such-and-such activity (attack) is on such a vulnerability (which he knows) and closes all vulnerability, not part of it.
One of the important factors why TP has become a leader is a 0-action initiative. There are many researchers who constantly monitor the code. At some point, TP began to just pay hackers for those who found vulnerabilities. For example, a hacker has found some kind of vulnerability, he has no benefit from this in order to sell this “hole” - he needs to take a risk - suddenly it is the FBI who buys or someone else is bad. TP “says” to a hacker — you drain your vulnerability to me — I give you $ 5,000. If you do this all the time, I'll pay you $ 10,000 for the vulnerability. And if you are my special partner - then 30,000 each. Then the hacker immediately receives his reward - he does not need to sell / take anything. Then it is profitable for him to become a laboratory researcher of vulnerabilities from a hacker.

Magazine "Hacker" released a review of the project ZDI
www.xakep.ru/post/54743/default.asp
Bronze:
+ 10% cash rewards for all the bugs next year
$ 1000 bonus
Silver:
+ 15% to cash rewards for all the bugs next year
+ 25% to accrued reward points next year
$ 5000 bonus
Paid ticket (flight + check-in) at DEFCON in Las Vegas
Gold:
+ 20% to cash rewards for all the bugs next year
+ 50% to accrued reward points next year
$ 10,000 bonus
Paid ticket (flight + check-in) at BlackHat and DEFCON in Las Vegas
Platinum:
+ 25% to cash rewards for all the bugs next year
+ 100% to accrued reward points next year.
$ 20,000 bonus
Paid ticket (flight + check-in) for BlackHat and DEFCON in Las Vegas + enrollment for BlackHat courses

ZDI helps Microsoft find vulnerabilities the most
Leading Security Research - DVLabs Microsoft Security Bulletin
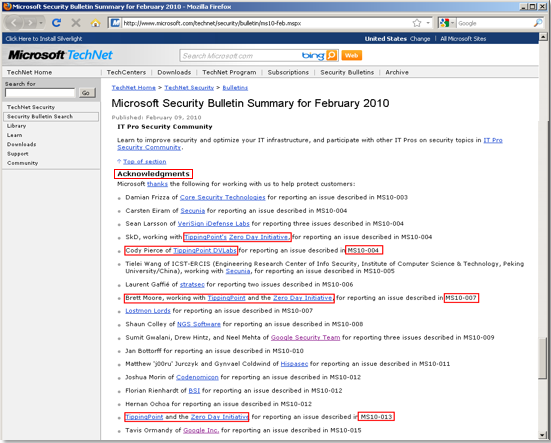
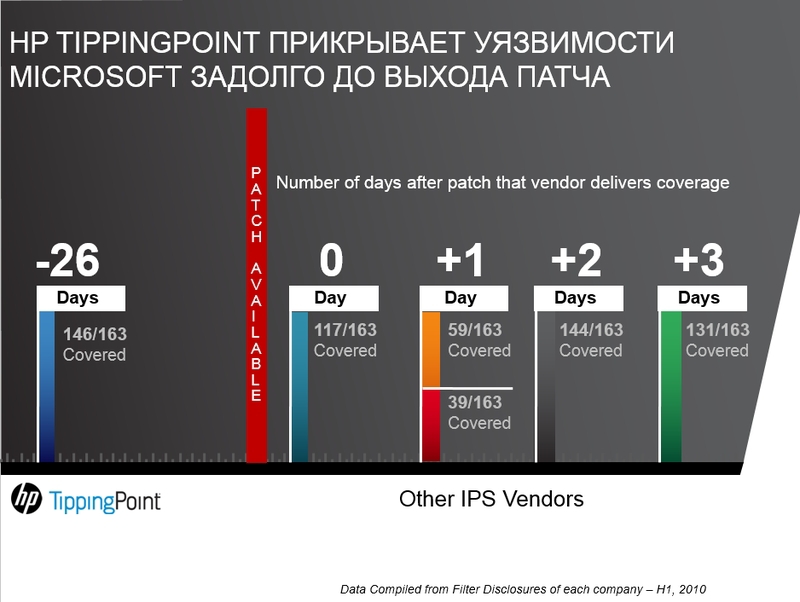
Due to the fact that ZDI finds vulnerabilities, ZDI can do so. virtual patch It transmits information about this vulnerability to its devices, and for the hacker the system looks like there is no such vulnerability on this system. Those. closes the vulnerability while Microsoft makes a patch where it fixes the error.

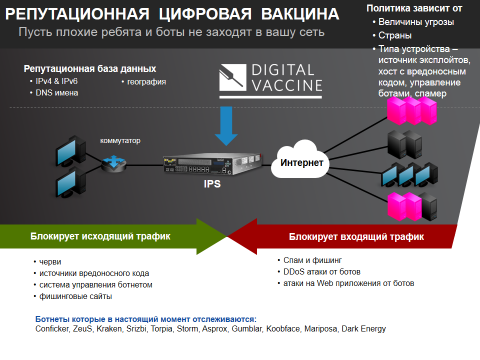
How it works? Need to download packages. After all, the hardware itself is useless, it should regularly enter the TP database and download all the exploits from which it protects. This is the so-called. digital vaccine. In addition, everything that is done in the company's network is being investigated: IPs, suspicious sites, etc. are being tracked. A reputation database is being compiled, which is updated 1 time in 4 hours (data not only on the internal network, but also on the Internet as a whole). Up to the point that you can go to the TP site to drive your IP and you will be shown how protected you are.
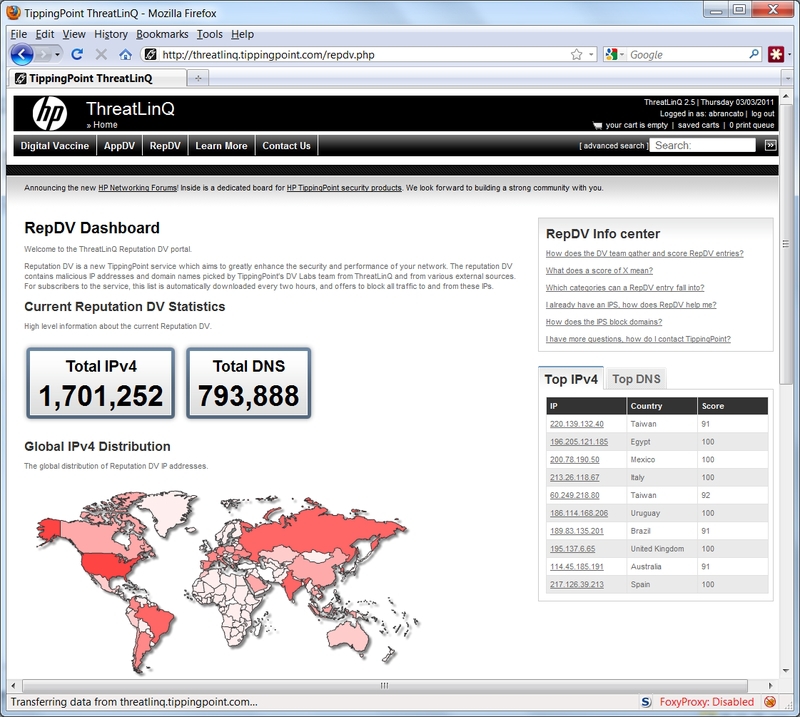
It looks like a DNS north. Shows where the most dangerous traffic. You can even find out what IP is spam, attacks, etc. And within the network, even the devices themselves can create such reputation databases.

Externally, the device looks like a switch
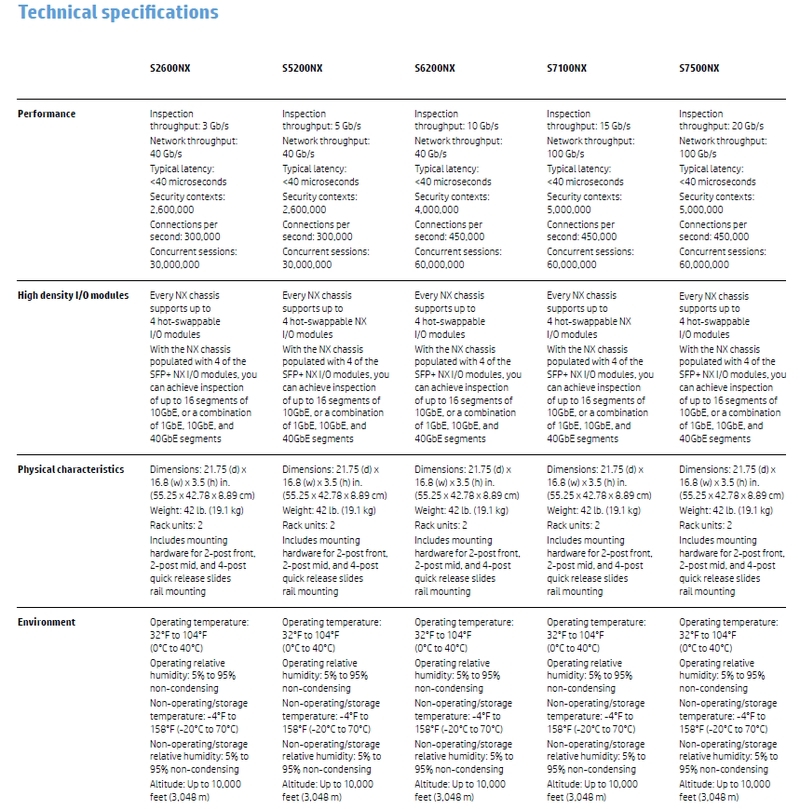
NX Series Specification
Since it is a virtual cable, even if the power is turned off, traffic still goes through it.
What is unique about it? It has a chip that hardware accelerates traffic filtering (they are also called FOP). Trikk made their chip, which allows you to quickly monitor traffic. If, let's say, traffic comes in at 1GB, then not only does he have to skip it, but also investigate, check for exploits, etc. Therefore, the chip must work twice as much.

One device can monitor multiple networks at once.

Wide range of TP integration . For example, with ArcSight, TP can act as a sensor for ArcSight - it tells the admin that it has been hacked (the administrator may not know about the hacking) and if you want to stop the leakage, do this - pull this switch, pull out this cord, etc. Those. it is not just reported that you have been hacked, but it is protected, IP is entered into the black list and the IP number is reported to the firewall. There is a quarantine WLAN - a network that does not lead anywhere - let the viruses breed there themselves - they do not interfere with anyone.
Findings:
• TP does not protect against viruses, but from hacking.
• High accuracy - the lowest number of false positives.
• High availability due to architecture
• Great speeds with the least amount of energy consumption - a unique chip, sharpened for this
• Easy installation and easy setup. Training admin on this technology - a maximum of 3 days.
• Integration with virtual machines. What is a cloud is a website that can be hacked, so you need your own IPA
Where is it implemented in Ukraine:
- Telecom
- Banking sector
Yes, of course, in this decision the hardware itself is cheap, but the update is not cheap. But here in Ukraine, security is not very concerned. They say - “yes, they break ?! What do you mean? just like movies ?! ”. Much depends on the size of the company and the nature of the data it works with - large companies are already protected. The rest - while they think. I must say, we do not develop network security education. Everyone is waiting "until thunder breaks out." Despite the fact that this niche is not very well understood, but the Internet is developing more and more, it means that this market will also develop.
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
I’ll say right away that TippingPoint can live in and of itself - as a separate domain, and as part of HP’s cloud technologies.

')
Reactive IT security model: antivirus and firewall installed - and we consider ourselves protected
If we look at the development of the market, we will see that the market almost all the time “depended” directly on vulnerabilities. Let's go through the history of these bugs:
2002 is mostly worms and viruses. Antivirus coped with this.
2004 - 2007 - due to the advent of social networks, social engineering related vulnerabilities were developed. Every kind of phishing. No penetration to the forehead, like a virus. More workarounds are used, more sophisticated. Spyver, statistics, etc.
2010+ already in our time, hackers have switched not to general information, but to something specific, these are exploits for applications. For this reason, they began to refuse the Adobe Flash Player plugin because hackers chose it as an ideal hacking point.
The objects of the current attacks are not specific people, they are attacks on the web (clouds), on companies. Everyone knows that there is a black market where you can order a hacking of some company, which, of course, depends on the customers' material injections.
Admin will say: I have a firewall!

Yes, there is, but the fact is that the malicious code does not follow any unusual paths, it goes through normal HTTP traffic. Codes go through port 80, which is always open, as companies, no matter how cool you need, the Internet does not protect.
Antivirus is reactive protection. It protects against already known hacks and attacks. Here is a table showing that there is a software that even antivirus parsit.

Sensational Vulnerabilities
Take the most famous. RSA is a company that issues certificates. It was enough to crack the root certificate in order to generate your own, which will be accepted in all companies where RSA gave its certificates - go wherever you want. And how the hacking was carried out - it was not an ordinary “head-on attack”, it was social engineering. The file came, and got into spam, but for some reason one of the employees decided to see what was there (hands to tear off!), And opened this file. An exploit unknown and unknown to any antivirus, and the company became infected. It is clear how it hit the company's business, not to mention the image. This led to the company changing even tokens.
Disclaimer
In general, any software, if you pick it intently, has vulnerabilities. Because people, not gods, write programs. Already, the software has written so much that finding a hole is practically no problem.
What is the NETWORK Intrusion Prevention System?

Attack Prevention System is a software and hardware system for detecting and blocking attacks that allow firewalls to pass through. Modern IPSs not only block attacks, but also control network connections and protocols. IPS software versions are used to protect virtualization (and cloud services).
How an ordinary antivirus works - it searches for signatures. And, having found, he says - this is a virus. IPS is looking for exploits, not looking for the results of hacks (which is late), but for suspicious activity. And looks at the general vulnerability. Since the vulnerabilities are also not the same and are used in different ways by crackers. What is meant: there is some N vulnerability, one virus can use 50% of this vulnerability - this part was found, some of the “hole” was patched, but another virus uses another 50% of the “hole” that was not fully patched, etc. . IPS - immediately sees all 100% of the vulnerability.
He constantly lets all traffic through him, works as a filter — it goes “dirty” and pure traffic comes out of it. In the network infrastructure, it looks like a virtual cable. And very easy to administer.
It does not track the virus itself (although, of course, it can track infected exe files), but track the hacking attempt itself: port scans, network anomalies, and service when the site is bombed.
Besides the fact that he filters the Internet, he can investigate traffic within the company - you can find out who is “naughty” within the company's network. Legally, it also closes many problems — for example, Visa requires compliance with its standards. When you install IPS, you automatically close the requirements for these standards.
Why do I need an IPS?
- Enterprise Management
• Timely detection of network problems
- to the financier
• Reducing the cost of eliminating the effects of attacks
• Reduced incident investigation costs
• Reduced TCO, CapEx and OpEx
- Internal audit or risk management
• Risk reduction
- IT security
• Detection and reflection of attacks on various services and resources of the enterprise
• Network protocol control
- IT specialist
• Ensuring high availability and resiliency of internal and external Internet resources
• Bandwidth Management



Ease of installation

Admins were interviewed about the ease of TP installation. We put, go to the site, and as in the Google store, you can choose what you need, for example: "the most popular hacks in March 2014" - and immediately closed all vulnerabilities. Or choose what you want to protect: server, site, etc.
Origin TippingPoint
Initially, it was a separate product. Then 3Com bought it, and when HP acquired 3Com, the product was further developed. He is now in the Gartner quadrant.

Vulnerability is not homogeneous.
As I already wrote, from the point of view of a hacker it is “more profitable” to use not the entire hole, but only a part of it. There is a vulnerability, something is written under it: an exe-file, a batch file or something else. This does not mean that the entire vulnerability is used, only part of it is used. Anti-Virus, if familiar with the exploit, will protect against a known (part) vulnerability + false positive, where it can paranoidly ban normal programs for itself. A new exploit may use another part of the same vulnerability - the antivirus will not even notice it. TippingPoint does not treat exploits, but vulnerabilities. Through continuous monitoring of traffic. He sees that such-and-such activity (attack) is on such a vulnerability (which he knows) and closes all vulnerability, not part of it.
One of the important factors why TP has become a leader is a 0-action initiative. There are many researchers who constantly monitor the code. At some point, TP began to just pay hackers for those who found vulnerabilities. For example, a hacker has found some kind of vulnerability, he has no benefit from this in order to sell this “hole” - he needs to take a risk - suddenly it is the FBI who buys or someone else is bad. TP “says” to a hacker — you drain your vulnerability to me — I give you $ 5,000. If you do this all the time, I'll pay you $ 10,000 for the vulnerability. And if you are my special partner - then 30,000 each. Then the hacker immediately receives his reward - he does not need to sell / take anything. Then it is profitable for him to become a laboratory researcher of vulnerabilities from a hacker.

Magazine "Hacker" released a review of the project ZDI
www.xakep.ru/post/54743/default.asp
Bronze:
+ 10% cash rewards for all the bugs next year
$ 1000 bonus
Silver:
+ 15% to cash rewards for all the bugs next year
+ 25% to accrued reward points next year
$ 5000 bonus
Paid ticket (flight + check-in) at DEFCON in Las Vegas
Gold:
+ 20% to cash rewards for all the bugs next year
+ 50% to accrued reward points next year
$ 10,000 bonus
Paid ticket (flight + check-in) at BlackHat and DEFCON in Las Vegas
Platinum:
+ 25% to cash rewards for all the bugs next year
+ 100% to accrued reward points next year.
$ 20,000 bonus
Paid ticket (flight + check-in) for BlackHat and DEFCON in Las Vegas + enrollment for BlackHat courses

ZDI helps Microsoft find vulnerabilities the most
Leading Security Research - DVLabs Microsoft Security Bulletin


Due to the fact that ZDI finds vulnerabilities, ZDI can do so. virtual patch It transmits information about this vulnerability to its devices, and for the hacker the system looks like there is no such vulnerability on this system. Those. closes the vulnerability while Microsoft makes a patch where it fixes the error.


How it works? Need to download packages. After all, the hardware itself is useless, it should regularly enter the TP database and download all the exploits from which it protects. This is the so-called. digital vaccine. In addition, everything that is done in the company's network is being investigated: IPs, suspicious sites, etc. are being tracked. A reputation database is being compiled, which is updated 1 time in 4 hours (data not only on the internal network, but also on the Internet as a whole). Up to the point that you can go to the TP site to drive your IP and you will be shown how protected you are.

It looks like a DNS north. Shows where the most dangerous traffic. You can even find out what IP is spam, attacks, etc. And within the network, even the devices themselves can create such reputation databases.

Externally, the device looks like a switch

NX Series Specification
Since it is a virtual cable, even if the power is turned off, traffic still goes through it.
What is unique about it? It has a chip that hardware accelerates traffic filtering (they are also called FOP). Trikk made their chip, which allows you to quickly monitor traffic. If, let's say, traffic comes in at 1GB, then not only does he have to skip it, but also investigate, check for exploits, etc. Therefore, the chip must work twice as much.

One device can monitor multiple networks at once.

Wide range of TP integration . For example, with ArcSight, TP can act as a sensor for ArcSight - it tells the admin that it has been hacked (the administrator may not know about the hacking) and if you want to stop the leakage, do this - pull this switch, pull out this cord, etc. Those. it is not just reported that you have been hacked, but it is protected, IP is entered into the black list and the IP number is reported to the firewall. There is a quarantine WLAN - a network that does not lead anywhere - let the viruses breed there themselves - they do not interfere with anyone.
Findings:
• TP does not protect against viruses, but from hacking.
• High accuracy - the lowest number of false positives.
• High availability due to architecture
• Great speeds with the least amount of energy consumption - a unique chip, sharpened for this
• Easy installation and easy setup. Training admin on this technology - a maximum of 3 days.
• Integration with virtual machines. What is a cloud is a website that can be hacked, so you need your own IPA
Where is it implemented in Ukraine:
- Telecom
- Banking sector
Yes, of course, in this decision the hardware itself is cheap, but the update is not cheap. But here in Ukraine, security is not very concerned. They say - “yes, they break ?! What do you mean? just like movies ?! ”. Much depends on the size of the company and the nature of the data it works with - large companies are already protected. The rest - while they think. I must say, we do not develop network security education. Everyone is waiting "until thunder breaks out." Despite the fact that this niche is not very well understood, but the Internet is developing more and more, it means that this market will also develop.
Contact info
For all questions: hp@muk.ua
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
Source: https://habr.com/ru/post/221947/
All Articles