VPN: past, present, future
The terms "frame relay", "packet switching" and "dial-up" sounded weird in the 80s and 90s, but these technologies were the foundation that made remote point-to-point connections possible and on the basis of which Many enterprise-level network technologies have been developed. Having gone from prehistoric protocols like X.25, people are now using networks connected to the Internet to create data connections in the place and at the time when it is needed.
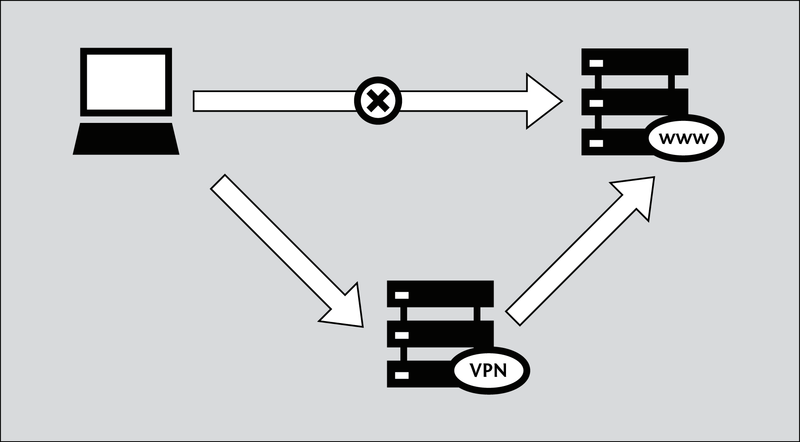
The Internet not only united humanity, but also allowed to create dedicated communications that are more in demand in the corporate environment. Virtual Private Networks (VPNs) work “on top of” public connections, while hiding the contents of communication is very convenient and functional. In practice, VPN is used to connect remote points — users, databases, or entire offices — to a secure enterprise network. VPN is much cheaper than buying a dedicated communication channel, and its convenience makes this technology an excellent choice for a business of almost any size.
')
VPN security
VPN security is achieved through encryption and tunneling. Data is encrypted at each end of the tunnel before transport begins; network addresses at both ends can also be masked. All this (encryption and synchronization) occurs at the second level of the seven-level OSI model.
Despite the fact that to establish such a connection is not so difficult, business representatives often have questions about the use of this technology. Here are three main ones:
Ipsec
Like a standard VPN, IPSec is a highly flexible and highly customizable tool that can be used to connect two networks (or a single computer) to a corporate network. Traffic transmitted over a VPN of this type is encrypted and protected with a password to protect against changes in the path from the sender to the addressee. IPSec functions at the protocol level of the OSI model, which makes this technology an ideal “VPN for common tasks”.
At the same time, despite the fact that IPSec is described as a standardized technology, some of its implementations may not be particularly compatible. IPSec is a good choice for companies that have resources for IT staff capable of supporting such connections.
SSL
SSL VPN connects a single computer to a gateway on the corporate network. Since, in the case of SSL VPN, the user's browser is used as the interface, most often it does not need to install additional software. This, in turn, simplifies installation and support, and also allows you to connect to computers running under different operating systems.
The downside here is the fact that, despite the ability to work through a browser, VPN connections via SSL can only be used with applications that work with HTML / HTTP. This limitation can be circumvented by installing special applications on the client computer, but this will limit flexibility, so it may be more beneficial to use IPSec VPN.
Mobile VPN
The third question of interest to business representatives is working in a mobile environment. Mobile VPN is often used in different industries, for example, in the field of security, and mVPN itself differs from the usual settings and operation scheme. The main difference is that the endpoint from which the connection is established is not fixed, therefore, mVPN must be able to restore the user connection when the client is moved.
Tom Davison, technical director of Check Point Software Technologies, says that modern VPN implementations are extremely flexible and can be integrated with the company's main security system.
Today, security is provided by a package of technologies that work on the IPSec Internet Protocol (IP), with the help of which, in particular, data is encrypted inside the VPN channel. This allows you to protect the connection between the remote computer and the main gateway at the company's headquarters. In the case of two offices (eg headquarters and branch office), a VPN connection is usually established between the gateways located in each of them. For users, of course, it is more convenient to implement without clients, since this removes the need to download and install additional software or use tokens for authentication.
Davison's company, Check Point, is developing VPN applications for iOS and Android. With their help, corporate users can connect to the company's network using the VPN settings specified by the IT department.
Best VPN for business
It is important to understand that there are many types of companies in the world, and each of them has its own characteristics. This means that the choice of VPN solution, ideally, should be based not on the size of the organization, but on how the business functions.
Network engineer at PEER 1 Hosting, Liam Entiknap, says that a VPN solution with flexible access policies and firewall rules may be suitable for customers who want to organize secure access to their servers from anywhere in the world.
Suppose we have a client-office VPN, a user can install a VPN client on his machine and connect to the office from anywhere on the planet. Here there are certain restrictions that depend on the hosting or firewall model - perhaps a different number of allowed simultaneous connections.
If we are talking about the “office-office” scheme, when a static tunnel is created between two offices and the firewalls located in them, then users may not worry about data integrity only when they are connected between these specific locations. The combination of the two methods described can better meet the needs of the business and provide greater flexibility.
In general, the reason that a company wants to use a VPN is the need for data security, control of their distribution, the ability to do all this from mobile devices.
Timico’s Trevor Davis CTO believes that, in a sense, VPN technology has not changed a bit over the years and has been replaced in various areas with mobile and cloud solutions that work no worse, but even better, providing a more reliable connection.
The proliferation of high-performance tablets and smartphones has led to an increase in the use of mobile VPN services. Mobile VPN typically encrypts data and sends it over a tunnel over the Internet to a corporate firewall. But there is a MAM-VPN (mobile access management), which works exclusively within a private network and is in no way connected to the Internet. Historically, MAM has been used by large businesses that could afford the associated costs. However, nowadays, many Internet service providers have partially integrated their systems with mobile operators, which allows them to divide MAM into segments that are cheaper and that small businesses can afford.
Elephant in a china shop
There are several types of VPNs, there are dedicated mobile communication channels, and there are still clouds. But will the clouds become the elephant that will spread the vase shop of VPN services? Juniper Networks Senior Marketing Solutions Director Paul Ganeam underlines the fact that many small businesses have bought into promises of cloud solutions from Amazon and Microsoft.
The flexibility of applications and payment schemes in combination with the outsourcing of some IT-tasks really seems to be quite a tempting offer. But can these new public products provide guaranteed security for business-standard VPN services? Now these two worlds are gradually mixing. Some VPN service providers are beginning to offer integrated cloud services along with VPNs. This allows businesses to access the cloud and at the same time ensure a secure connection.
Growth with VPN
Duncan Higgins, director of product and marketing for Virgin Media Business, advises business executives to think about future business growth as they choose the VPN provider and technology. There is no point in paying in advance for VPN solutions that after a few months either will not be needed or will not be able to solve all the arising tasks.
Last year, we conducted a small study of what policies of updating VPN services are followed by British leaders (in particular, CIO). It turned out that more than a third of them needed to update the VPN once a year, which each time results in spending at the level of £ 30,000. Do I have to say that small and medium businesses simply cannot afford such costs? They need a VPN that allows you to grow and continues to be relevant to the current tasks of the company.
VPN enables millions of people and businesses around the world to securely transfer information. Therefore, it is obvious that this technology will continue to play an equally important role in the foreseeable future. However, changes in the workflow of many companies and the ever-deeper penetration of cloud technologies will probably lead to the emergence of a new cloud-based variety - VPN 2.0. It may well be that we are witnessing the birth of this process now.
Source: https://habr.com/ru/post/221675/
All Articles