Configuring LDAP Authentication in InterSystems Caché Based on Microsoft Active Directory
On the one hand, setting up LDAP authentication in Caché is not very complicated - the documentation describes this process in six points. On the other hand, if the LDAP server is based on Microsoft Active Directory, then there are several not obvious points that need to be configured on the LDAP server side. Also for those who are not often engaged in similar settings, there is a chance to get lost in the Caché security settings. In this article we will step by step describe the process of setting up LDAP authentication, as well as methods for diagnosing problems in case something goes wrong.
1. Create a user in ActiveDirectory, with which Caché will connect and search for information in the LDAP database. This user must be strictly in the root of the domain.
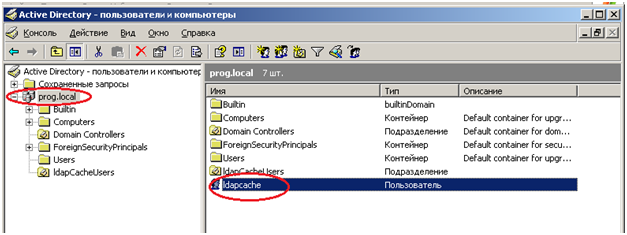
2. For users who will connect to Caché, we will create a separate division. Let's call it "IdapCacheUsers"
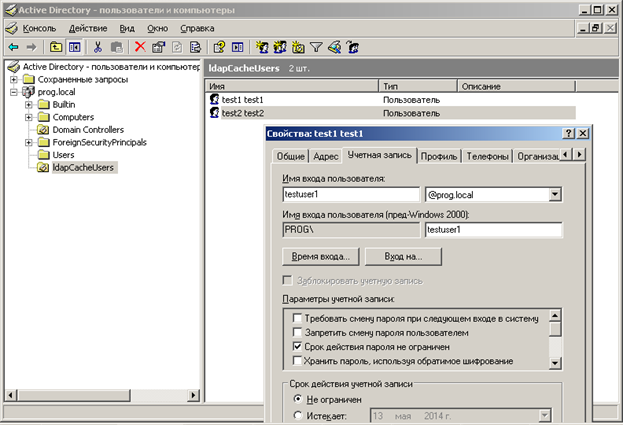
3. We register users there
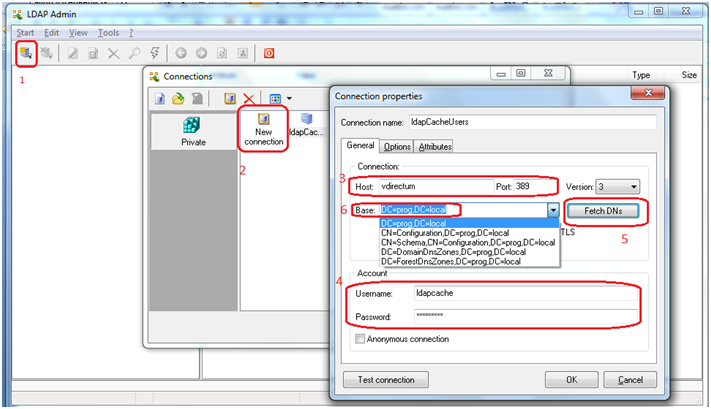
4. Test the accessibility of the LDAP database using the ldapAdmin program. Download ee here .
')
5. Configure the connection to the LDAP server:
6. Connected. We looked that everything works:
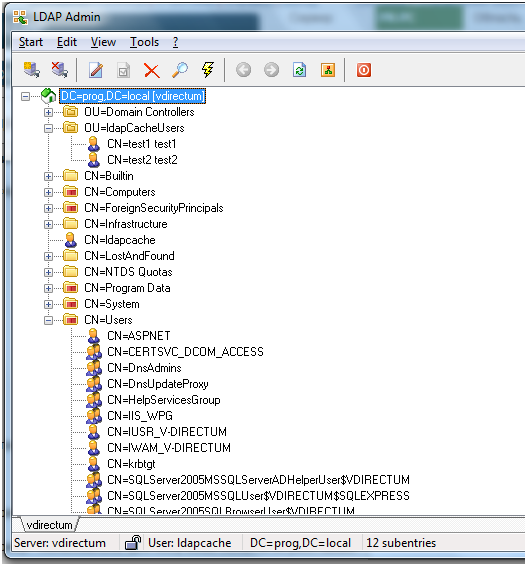
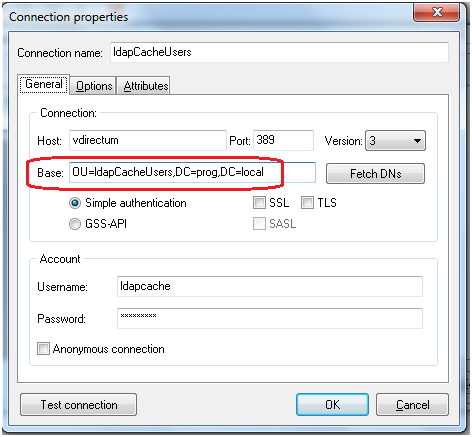
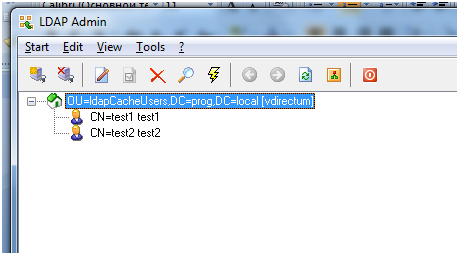
7. Since the users who will connect to Caché are located in the “ldapCacheUsers” division, we will limit the search to this division only.
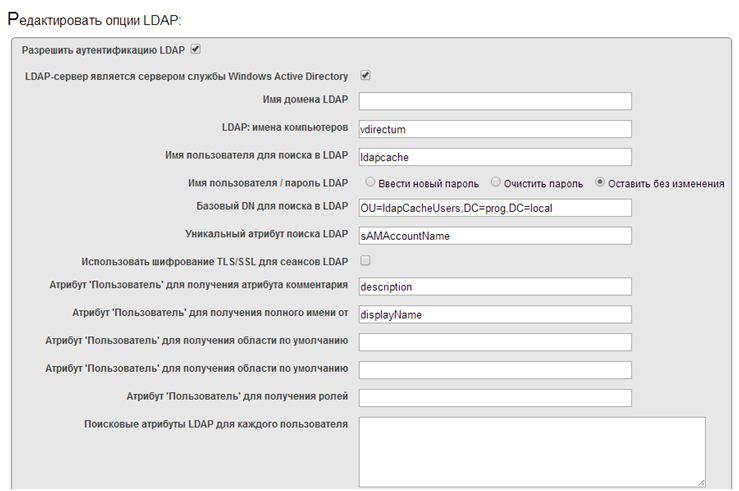
8. The LDAP server is ready, now go to the settings on the side of Caché. Go to the management portal -> System Administration -> Security -> System Security -> LDAP Options. The fields “User attribute to retrieve default namespace)”, “User attribute to retrieve default routine” and “User attribute to retrieve roles” »Cleared, as these attributes are not yet in the LDAP database.
9. We allow LDAP authentication in the System Administration section -> Security -> System Security -> Authentication / CSP Session Settings
10. We allow LDAP authentication in services. The% Service_CSP service is responsible for connecting the web applications, the% Service_Console service is responsible for connecting through the terminal.
11. Configure LDAP authentication in web applications.

12. For now, to verify that the connection is working, we will configure it so that new users in Caché have full permissions. To do this, the _PUBLIC user needs to add the% All role. In the future, we will finalize this moment ... ...

13. We try to open the configured web application, it should open.
14. The terminal also opens

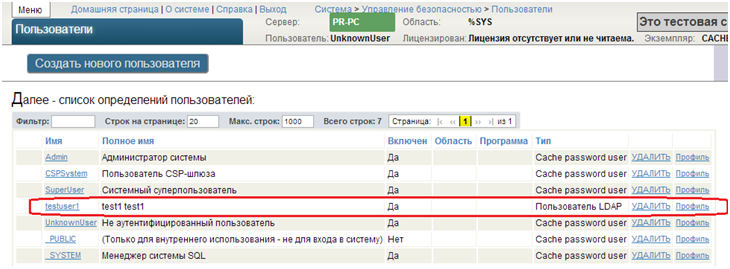
15. When connecting, LDAP users will appear in Caché users.
16. However, with this configuration, all new users get full access to the system. To eliminate this gap, you need to add an attribute in the LDAP database, where we will store the name of the role that will be assigned to the user when connecting to Caché. You must first make a backup of the domain controller, so that if the configuration fails, do not break the entire network.
17. To modify the ActiveDirectory schema, on the server where ActiveDirectory is located, install the ActiveDirectory schema snap-in (by default it is not installed). The instruction is here.
18. Create an attribute named intersystems-Roles, OID 1.2.840.113556.1.8000.2448.2.3, string, case sensitive, multi-valued attribute.
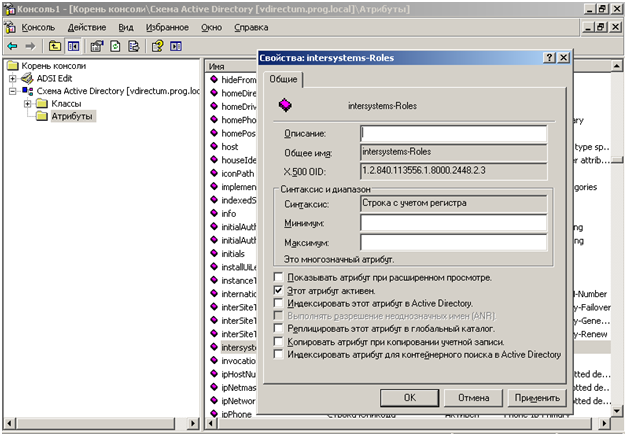
19. Next, add this attribute to the user class.

20. Next, we’ll make the column “Role in InterSystems Cache” displayed when viewing the list of users in the subdivision. To do this, click Start-> Run, enter adsiedit.msc. Connect to the Configuration naming context
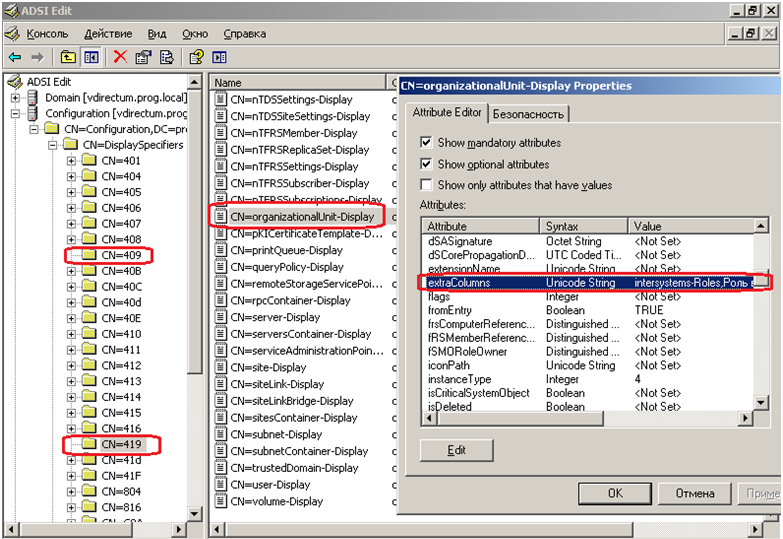
21. Go to the container CN = 409, CN = DisplaySpecifiers, CN = Configuration and select the type of container, when viewing which will be displayed additional user attributes. Select the display at the department level (OU), for which we need the container organisationalUnit-Display. In the properties we find the extraColumns attribute and enter the value “intersystems-Roles, Role in IntersystemsCache, 1,200.0” there. The principle of filling is as follows: Attribute name, column name in which the attribute will be displayed, whether the column width in pixels will be selected by default, reserved value. Another remark CN = 409 indicates the language code: in the CN = 409 branch for the English version, CN = 419 for the Russian version of the console.
22. Now you can fill in the name of the role that will be assigned to the user when connecting to Caché. If Active Directory is based on Windows Server 2003, then there are no regular tools for editing this field. You can use the ldapAdmin program (see clause 4) to edit the value in this attribute. If Windows is a more recent version, then the attribute can be edited in the “Additional functions” mode - the user will have an additional tab for editing attributes.

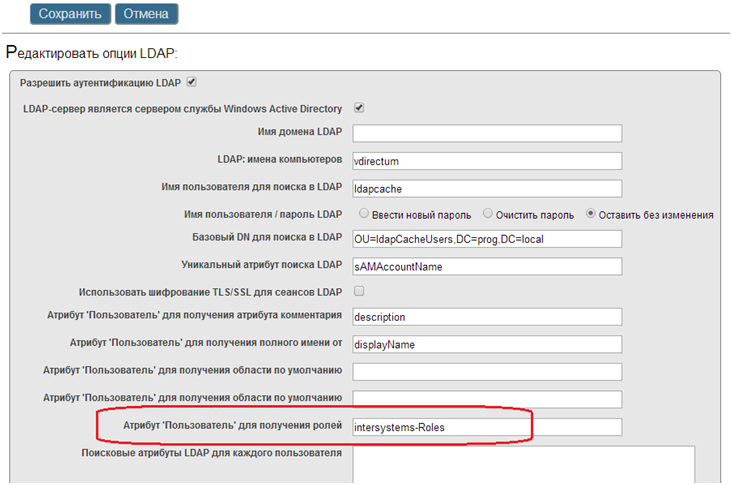
23. After that, in the Caché management portal, in the LDAP options, specify the name of this attribute.
24. Create the ldapRole role with the necessary privileges
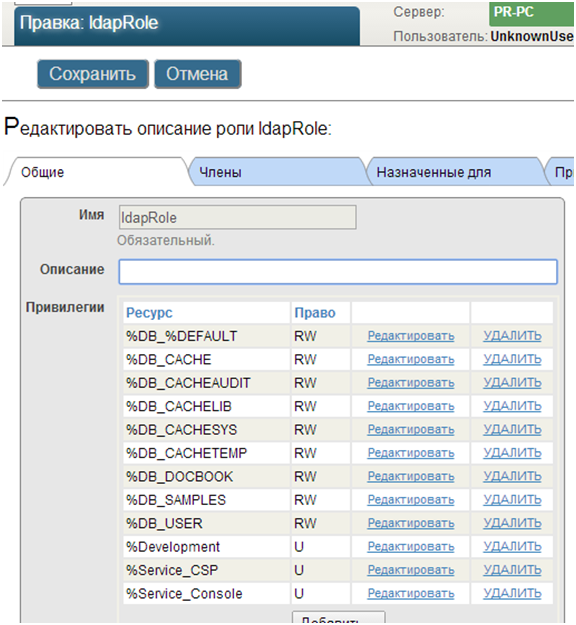
25. Remove the% ALL role from the _PUBLIC user
26. Everything is ready, try to connect to the system.
27. If it fails, enable and configure auditing.
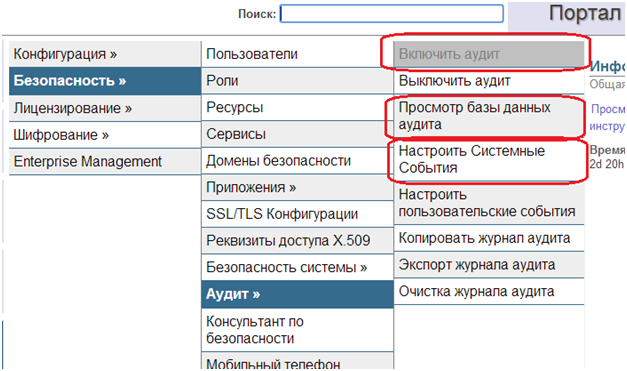
28. Audit Settings
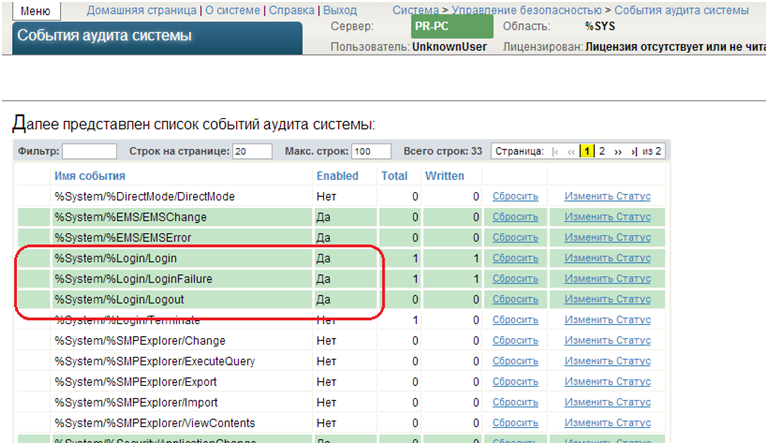
29. View the audit database.

In practice, it often happens that to work in an application, it is not necessary to configure different roles for different users. If it is enough that when entering, for example, into a web application, all users are assigned a certain set of roles, then points 16 to 23 can be disregarded. It is enough to add these roles in the settings of the web application on the "Application Roles" tab and remove all types of authentication, except LDAP. In this case, only a user who is registered on the LDAP server can enter the web application, and when the user logs into it, Caché automatically assigns him the roles that are required to work in the application.
Configure LDAP server
1. Create a user in ActiveDirectory, with which Caché will connect and search for information in the LDAP database. This user must be strictly in the root of the domain.

2. For users who will connect to Caché, we will create a separate division. Let's call it "IdapCacheUsers"
3. We register users there

4. Test the accessibility of the LDAP database using the ldapAdmin program. Download ee here .
')
5. Configure the connection to the LDAP server:

6. Connected. We looked that everything works:

7. Since the users who will connect to Caché are located in the “ldapCacheUsers” division, we will limit the search to this division only.


Setup on the side of Caché
8. The LDAP server is ready, now go to the settings on the side of Caché. Go to the management portal -> System Administration -> Security -> System Security -> LDAP Options. The fields “User attribute to retrieve default namespace)”, “User attribute to retrieve default routine” and “User attribute to retrieve roles” »Cleared, as these attributes are not yet in the LDAP database.
Translation comment
True, in this place the Russian translation is not entirely successful; it would be better to translate so: “User Attribute to Receive Default Area”, “User Attribute to Get Default Program” and “User Attribute to Get Roles”.

9. We allow LDAP authentication in the System Administration section -> Security -> System Security -> Authentication / CSP Session Settings
10. We allow LDAP authentication in services. The% Service_CSP service is responsible for connecting the web applications, the% Service_Console service is responsible for connecting through the terminal.
11. Configure LDAP authentication in web applications.

12. For now, to verify that the connection is working, we will configure it so that new users in Caché have full permissions. To do this, the _PUBLIC user needs to add the% All role. In the future, we will finalize this moment ... ...

13. We try to open the configured web application, it should open.
14. The terminal also opens

15. When connecting, LDAP users will appear in Caché users.

16. However, with this configuration, all new users get full access to the system. To eliminate this gap, you need to add an attribute in the LDAP database, where we will store the name of the role that will be assigned to the user when connecting to Caché. You must first make a backup of the domain controller, so that if the configuration fails, do not break the entire network.
17. To modify the ActiveDirectory schema, on the server where ActiveDirectory is located, install the ActiveDirectory schema snap-in (by default it is not installed). The instruction is here.
18. Create an attribute named intersystems-Roles, OID 1.2.840.113556.1.8000.2448.2.3, string, case sensitive, multi-valued attribute.

19. Next, add this attribute to the user class.

20. Next, we’ll make the column “Role in InterSystems Cache” displayed when viewing the list of users in the subdivision. To do this, click Start-> Run, enter adsiedit.msc. Connect to the Configuration naming context

21. Go to the container CN = 409, CN = DisplaySpecifiers, CN = Configuration and select the type of container, when viewing which will be displayed additional user attributes. Select the display at the department level (OU), for which we need the container organisationalUnit-Display. In the properties we find the extraColumns attribute and enter the value “intersystems-Roles, Role in IntersystemsCache, 1,200.0” there. The principle of filling is as follows: Attribute name, column name in which the attribute will be displayed, whether the column width in pixels will be selected by default, reserved value. Another remark CN = 409 indicates the language code: in the CN = 409 branch for the English version, CN = 419 for the Russian version of the console.

22. Now you can fill in the name of the role that will be assigned to the user when connecting to Caché. If Active Directory is based on Windows Server 2003, then there are no regular tools for editing this field. You can use the ldapAdmin program (see clause 4) to edit the value in this attribute. If Windows is a more recent version, then the attribute can be edited in the “Additional functions” mode - the user will have an additional tab for editing attributes.

23. After that, in the Caché management portal, in the LDAP options, specify the name of this attribute.

24. Create the ldapRole role with the necessary privileges

25. Remove the% ALL role from the _PUBLIC user
26. Everything is ready, try to connect to the system.
27. If it fails, enable and configure auditing.

28. Audit Settings

29. View the audit database.

Conclusion
In practice, it often happens that to work in an application, it is not necessary to configure different roles for different users. If it is enough that when entering, for example, into a web application, all users are assigned a certain set of roles, then points 16 to 23 can be disregarded. It is enough to add these roles in the settings of the web application on the "Application Roles" tab and remove all types of authentication, except LDAP. In this case, only a user who is registered on the LDAP server can enter the web application, and when the user logs into it, Caché automatically assigns him the roles that are required to work in the application.
Source: https://habr.com/ru/post/221347/
All Articles