What tasks do the IAM systems solve?
What tasks do the IAM systems solve?
Terminology
Most often we come across the term Identity Management (IdM), which means managing user accounts or electronic submissions. As a rule, IdM systems are required to manage not only user accounts, but also access to systems. Therefore, generally speaking of IdM, Identity and Access Management is implied.
')
Identity and Access Management (IAM) is a set of technologies and software products that meet the tasks of managing the life cycle of accounts and controlling access to various systems in a company. Analytical agencies (Gartner, Forrester, KuppingerCole) and IAM systems developers identify at least two areas within IAM: User Administration and Provisioning (UAP) and Identity and Access governance (IAG). A modern IAM solution should provide functionality in both areas.
UAP solutions appeared in the late 1990s as a means of automating the work with directory services. UAP solves the tasks of automating the creation, modification and deletion of accounts in the organization’s information systems, and also provides access to the applications and resources that the user needs for work.
Sample IAM Tasks
UAP tasks
Imagine the process of organizing access to IT-resources (applications, data, services) in a company without automation. Employee when hiring a personnel department makes a 1C. Then information about him gets into the IT department. The IT department creates an account in the Active Directory directory service. A new employee receives access to folders, applications, mailings by contacting the system administrator or e-mail support service; in some cases, the consent of the manager or owner of the resource is required. At the same time, the employee never asks to “take away access” and over the years of work in the company can “acquire” access to various systems.
If in a small company, the organization of access is decided by direct communications and a newcomer can gain access to everything that is required for work during a day, then in a geographically distributed company with a staff of more than 500 people this may take days.
Employees may change positions, phone numbers, last names, and these changes should be reflected in information systems. Some companies have contract or seasonal workers. Upon termination of the contract or change of position, access to resources should be terminated.
If there are several information systems in a company, for example, a document flow system, an accounting system, an external portal, the task of managing passwords appears. Each system is controlled by different people. A password is created separately in each system (i.e. personal passwords are assigned). It is difficult for the user to remember several passwords, and this leads to the fact that they are stored on paper. If the password needs to be changed, you need to find the owner of the application, which can be on vacation, and access is needed now.
Imagine a situation where an employee on a business trip decided to connect access to mail on a mobile phone and made a mistake when entering a password. His account will be blocked with repeated attempts to enter incorrect data, and he will not be able to independently access the mail.
When an employee is dismissed, it is necessary to block his access to all the company's systems; sometimes it is important to do this within a minute.
Such a process across a large organization takes a lot of time from the IT department, inevitably leads to errors and, as a result, financial losses.
Quite often on the Internet you can read about court cases related to the fact that a dismissed employee has access to enterprise systems, for example:
www.kuzbass85.ru/2012/04/11/uvolennyiy-sistemnyiy-administrator-udalil-chetyirehletniy-arhiv-buhucheta-byivshego-predpriyatiya
The court found that in July 2011, Prikhodko, while at his home in Kemerovo, had made unauthorized access to the mail server of the enterprise where he had previously worked. Then he removed the program "1C Enterprise" for the period from 2007 to 2011. As a result, the accounting data on the servers of three companies of the holding company located in Prokopyevsk were destroyed.
We will not learn about many such cases, since banks or insurance companies prefer not to advertise such incidents.
Now let's see what the automated process looks like.
After the account appears in the personnel system, the UAP solution automatically creates accounts in the connected systems, and gives access based on user attributes (for example, position and department) and groups. UAP-system allows you to check the values of attributes for compliance with the rules and prohibit the creation of "wrong entries", in particular, with an empty position. When changes are enough to make them in one place - and they will automatically be reflected in all connected systems. So, for example, a user, changing the password in AD, automatically receives the same password on all systems. When transferring or dismissing an employee, the system selects access in all systems almost instantly.
It is important to note that UAP initially focused more on solving the routine tasks of IT departments in the administration of users and resources. However, such solutions were not intended for the organization of access control to the systems and were not intended for non-IT users. That is, UAP-systems automatically gave access and selected it, but could not answer the question to which resources the user has access to now. It was also important to give users the opportunity to independently request access to resources (applications, data, services), and their managers (or resource owners) to confirm eligibility of access when requesting, to organize appraisals for checking who has access to a particular resource.
These needs were first closed by a set of extended functionality of UAP products, but it was clear that such tasks require new solutions.
IAG Tasks
In the mid-2000s, specialized IAG proposals began to appear. The IAG system solves the tasks of requesting, confirming, certifying, and auditing access to applications, data, and services, and also provides control and business analytics for the processes of creating accounts, managing these records, and how these records were used to access. Unlike UAP, where rights in systems are tied directly to accounts, IAG solutions operate on roles that are associated with the organizational structure of the enterprise. We can say that in the UAP solutions, the IT department was responsible for issuing access, and the IAG systems returned the reins of access control to business users.
Let's look at specific examples of using IAG solutions. Suppose you want to use Adobe Photoshop on your work computer. First, the user sends a request to the technical support service. Its employees are waiting for the confirmation of the head, which is added to the correspondence. As a result, the user gets an installed application, spending a couple of days on it. It happens that several people are involved in the agreement (so in order to get a new laptop, you need confirmation from the manager and director).
IAG solutions offer automation of such processes using a web portal where you can request a resource, then an “invisible” process will start, which, if necessary, will ask for confirmation from the manager and after receiving it will automatically make the required changes.
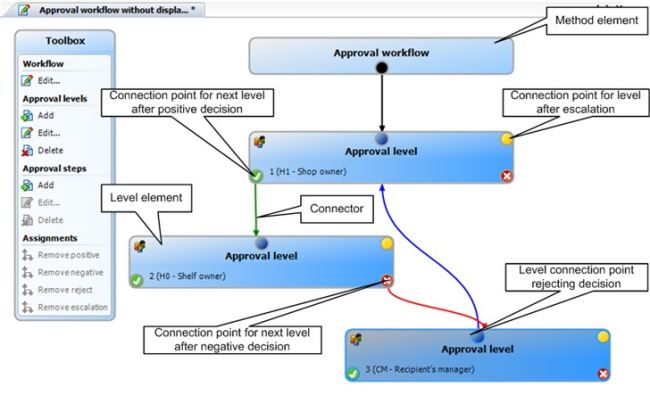
The IAG system allows the manager or security officer to see which systems the user has access to and also control this access.
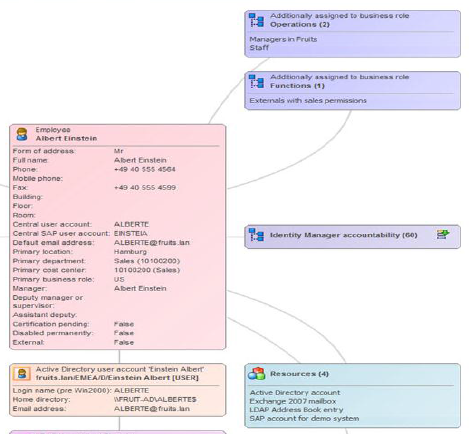
Access can also be provided on the basis of “calculated” rules, that is, if an employee is assigned to work on a specific project and has a corresponding role, he will automatically get access to the required documentation, thus avoiding “manual approvals”.
If a user has extra rights (for example, an Active Directory administrator has added a user to a group) that do not correspond to his role, the security service will be notified of this and may confirm the exception or take steps to eliminate it.
An important part of the role management process is the Separation of Duties (SoD) policy or separation of powers. These policies prohibit the combination of certain roles. For example, an employee who forms an order should not participate in financial transactions.
Some directions for the development of IAM
IAM solutions are evolving rapidly, covering new areas such as content-based data management, mobile device management, risk-based authorization, and many others.
As we can see, existing IAM-solutions well allow you to control access to centralized resources. However, in modern companies there are huge amounts of unstructured data stored on users' computers in network folders. The user can easily copy valuable data to his computer and then distribute it uncontrollably.
To solve this problem, modules appear in IAM products that allow data to be classified by content and attributes of a document and provide access based on a comparison of data provided by the user (who is the user and which device he uses) and document classification data (what data the document contains).
Another promising direction is the management and interaction with mobile devices. In modern companies, users use for work not only stationary computers, but also smartphones and tablets. In many cases, these are not corporate devices, but personal ones. The BYOD policy (Bring your own device, or bring your device) is gaining popularity by reducing the company's costs of supporting infrastructure, purchasing devices. With the popularization of this policy, new challenges appear. How to protect company data stored on the device, but at the same time respect the privacy of the employee?
The technology of using the login and password to access the company's resources has been criticized for a long time, but no one could offer a worthy replacement. Two-factor authentication methods (for example, a combination of the traditional method and SMS) are not widely used. Now suppliers of IAM solutions are moving in the direction of authentication based on context data about the user, device, application, where the request came from. This data is analyzed and a decision is made about the user's identity. Such an algorithm works in some social networks. So, when you enter a login from another country, you can get an offer to specify additional data (phone number, for example).
How to choose a suitable IAM system
IAM Solutions Market
The IAM market is actively developing, mergers and acquisitions occur. The complexity of IAM-systems increases significantly every year. To assess the current IAM-proposals requires a serious examination not only in the field of information technology, but also in the field of business intelligence.
There are several analytical agencies that specialize in research and comparisons of IAM solutions: Forrester, KuppingerCole, Gartner. They, as a rule, issue an annual report on the market of IAM-solutions, as well as separate documents on trends in the industry, questionnaires to help you choose the most appropriate system. If annual reports can be found on the websites of solution providers, then specialized documentation, as a rule, costs from hundreds to tens of thousands of dollars.
For the annual reports, each of the agencies has its own method of comparison and visual presentation of the results.
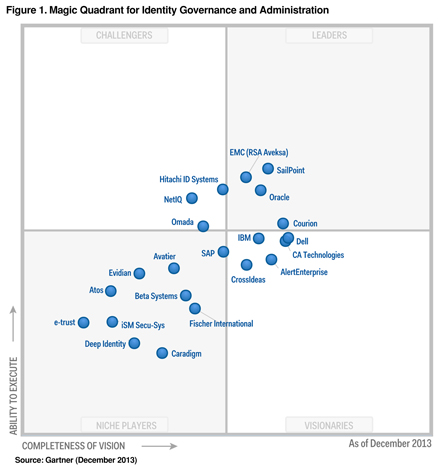
For example, Gartner assesses IAM suppliers on the Vision scale (a vision of how the market develops and develops, the ability to innovate) and “Ability to realize” (ability to take market share, sell the system).
There are several charts in the KuppingerCole report where IAM solution providers are ranked on a single scale (overall product rating in the screenshot below).
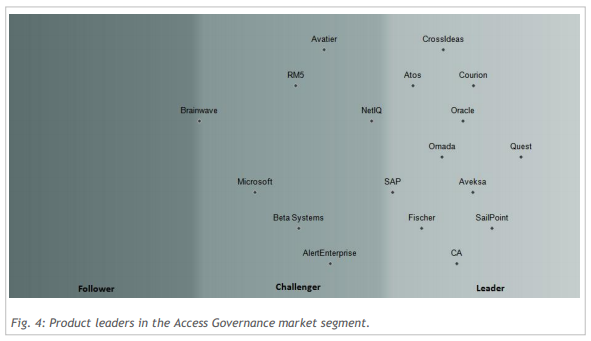
Such reports provide insights into the subject area, market trends, and a general understanding of the major players in the IAM market.
It is important to understand that in the Russian market many systems are not represented at all. There may also be local solutions that are quite successful in the Russian market, but which have no distribution in the world.
System Selection Criteria
As there are no two identical enterprises with the same set of applications and business processes, there are no universal and very best IAM systems. Each IAM system has a unique set of functionality, connectors to target systems, and frameworks for extending functionality.
You can start the selection with formal requirements, such as cost of ownership (cost of licenses, implementation and support for several years), licensing policy, the presence of successfully completed projects in enterprises of similar size / industry, the presence of specialists in implementation and support in Russia.
Technical requirements can also help: availability of connectors for common systems used in the enterprise, a web interface for business users, automation of business processes (for example, approvals), certification mechanism, requirements for open functionality extension (when the system can be expanded without a manufacturer) .
By selecting several of the most suitable suppliers, you can see how the system works with the main and most important scenarios that need to be automated.
These are usually scenarios of an employee's life cycle: hiring, transfer to another department or office, vacation, dismissal. The set of access control scenarios is also important: issuing temporary and permanent access to systems on request, automatically or by agreement based on roles in a company or project, access control on a schedule (certification) and request.
When working with account data, it is important to check their correctness (for example, the format of a phone number), as well as to convert the data during synchronization, in particular, to transliterate names when synchronizing the personnel system and Active Directory.
To automate the life cycle of users in target systems, connectors are usually used. These are dedicated IAM modules that interact with an external system, creating, modifying, deleting accounts and issuing access by transferring roles in the IAM system to a set of rights that are understandable for the target system, for example, a group. Connectors change frequently due to changes in the target system. Will IAM support the new version of 1C or SalesForce? How expensive is the redesign of the connector?
It is important to understand that the IAM-system is not a boxed product and in most projects the cost of services may be several times higher than the cost of licenses. IAM projects never end (except for unsuccessful ones), since the target systems running the IAM offer are constantly changing and need to be reconfigured, updated or refined. Therefore, system extensibility is a very important selection criterion. Will you need to involve supplier specialists for every change, or can administrators and business users of the customer handle this?
Sample scenarios for evaluating the IAM system
Recruitment
Scenario: After the personnel department gets an account of a new employee in the personnel system (for example, 1C), the employee must get accounts and sets of rights in all systems according to his role no later than in n minutes.
Result:
An employee can use all the systems within the scope of his role.
Request access to the resource
Scenario: After an employee requests a resource through a web portal, he should receive a response within n hours. Temporary access to the resource is regulated by manual approval. That is, the request is received by the owner of the resource and / or his deputy. If the request is not answered within the specified time, an escalation occurs.
Result:
a) The employee gets access to the resource;
b) Employee receives a refusal.
Certification
Scenario: Once a month, the owner of the resource conducts certification of the list of those who have access to the resource. For each member of the list, he extends or terminates access.
Result: Certification was carried out, only employees confirmed by the owner have access to the resource.
Vacation
Scenario: Employee access on vacation should automatically be terminated during his absence. Termination of access does not require manual actions.
Result: The employee does not have access to the company's systems during the holidays.
Dismissal
Scenario: An employee should be denied access to all enterprise systems no later than n minutes after the process was initiated by the manager on the web portal.
Result: The employee does not have access to the company's systems.
Separation of powers
Scenario: A manager assigns a role to an employee that is incompatible with existing roles. An employee cannot combine mutually exclusive roles.
Result: The system refuses to change and fixes a policy violation.
Password reset
Scenario: Employee forgot password.
He enters the website, where, by answering questions from the system, he initiates a password reset and receives a new password in the form of SMS. The new password should automatically be synchronized to the connected systems.
Result: The employee receives a new password, which can be used in all systems where he has access.
This is the first part of the article, will be continued ...
Author: Alexander Tsvetkov, Dell Software Engineer
Source: https://habr.com/ru/post/221159/
All Articles