EMET, prevention of operation and non-obvious settings
We have already written many times about EMET [ 1 , 2 , 3 , 4 ] and about the "Advanced Protected Mode" (EPM) of the Internet Explorer 10+ [ 1 , 2 ], and about 64-bit processes for tabs [ 1 , 2 ], and innovations Windows 8 / 8.1 [ 1 ], which use protection against exploitation. Despite the fact that Microsoft, in recent times, has devoted enough effort to integrate protection against exploits in Windows, many of the settings entered are turned off by default. Obviously, the approach practiced by the company is that it puts the compatibility of applications with the OS in the first place, and the inclusion of security settings leaves on the shoulders of users (because of the declared compatibility problems).

For example, a recent post on the MSRC for SA 2963983 contains the following sentence.
This is despite the fact that the company released last year an update MS13-088 (see KB2907803 ), which disables the use of EPM by default for Internet Explorer 11 with the wording:
')
Thus, before using Internet Explorer for the first time, be sure to check if your security settings are enabled, which the company declares as “basic to be safe”, but which are disabled by default.
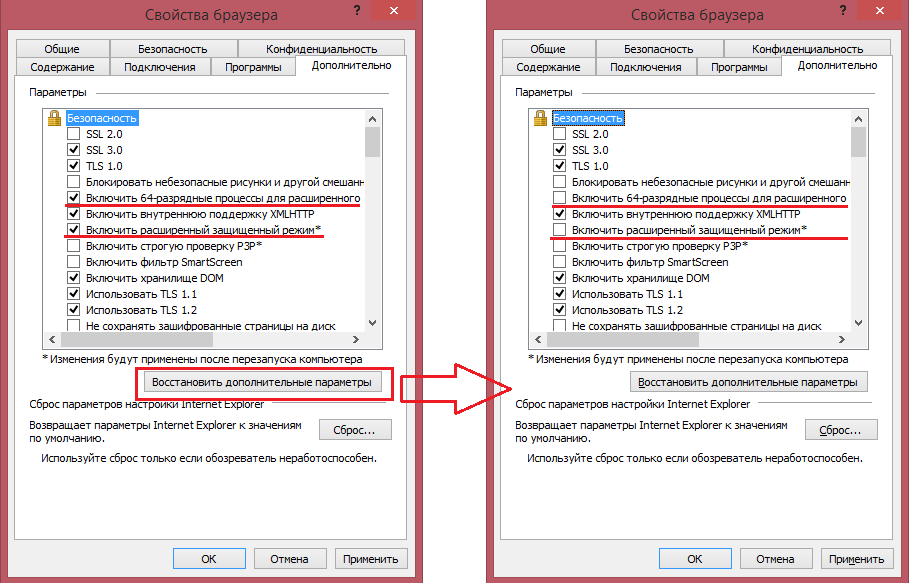
Fig. IE11 on Windows 8.1 with MS13-088 installed, on the left, manually installed security options, then the restore default settings function was activated.
Similar settings exist in EMET.
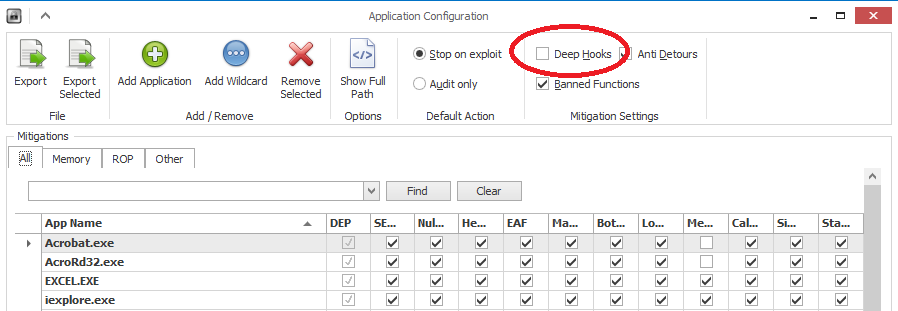
Fig. EMET v4.1 Release in “Maximum security settings” mode, “Deep Hooks” setting is disabled. Used to block exploit actions for CVE-2014-1776. See More Details about Security Advisory 2963983 IE 0day .
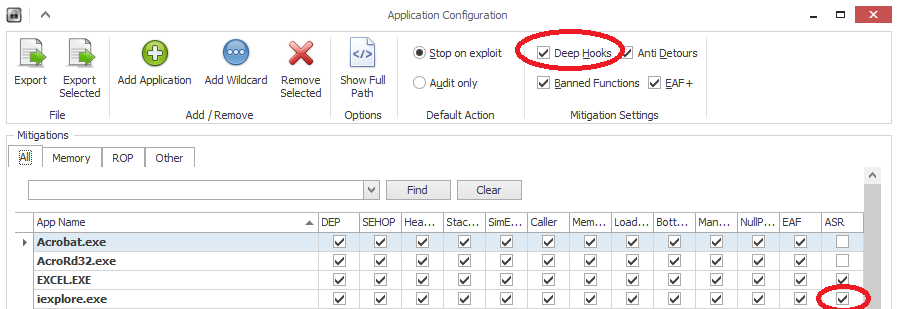
Fig. EMET v5.0 TP, the default settings are Deep Hooks and ASR.
We have not stopped in detail on EMET 5.0 TP, users can download it from the MS Security TechCenter website . This version contains two new options called Attack Surface Reduction (ASR) and Export Address Table Filtering Plus (EAF +) . As seen in the screenshot above, ASR is enabled for Internet Explorer and can be used to prevent the use of CVE-2014-1776. Due to the fact that this version of EMET has the status of Technical Preview, the company delivers it with the “Deep Hooks” setting already enabled.
Attack Surface Reduction
In a narrower sense, ASR applies to Internet Explorer and uses browser-based URL Security Zones to block or allow the execution of plug-ins, such as Oracle Java or Adobe Flash Player, depending on which zone a user is visiting. More broadly, it is applied to applications in order to forcibly prohibit for them the activation of the corresponding plug-ins that can be used for operation.
Fig. Security Zones URLs that distinguish IE and are used for EMET Attack Surface Reduction.
The main meaning of ASR EMET for IE is that it allows the use of potentially unsafe Java and Flash Player plug-ins for websites that are on the organization’s network (intranet) and prohibits them for the Internet, where the content may be potentially unsafe. In addition, plug-ins are allowed to use in the Trusted zone (Trusted sites), see below.
By default, EMET 5.0 TP includes ASR for the following applications:
Blocking of plug-ins is done by mask, or by the full name of the library.
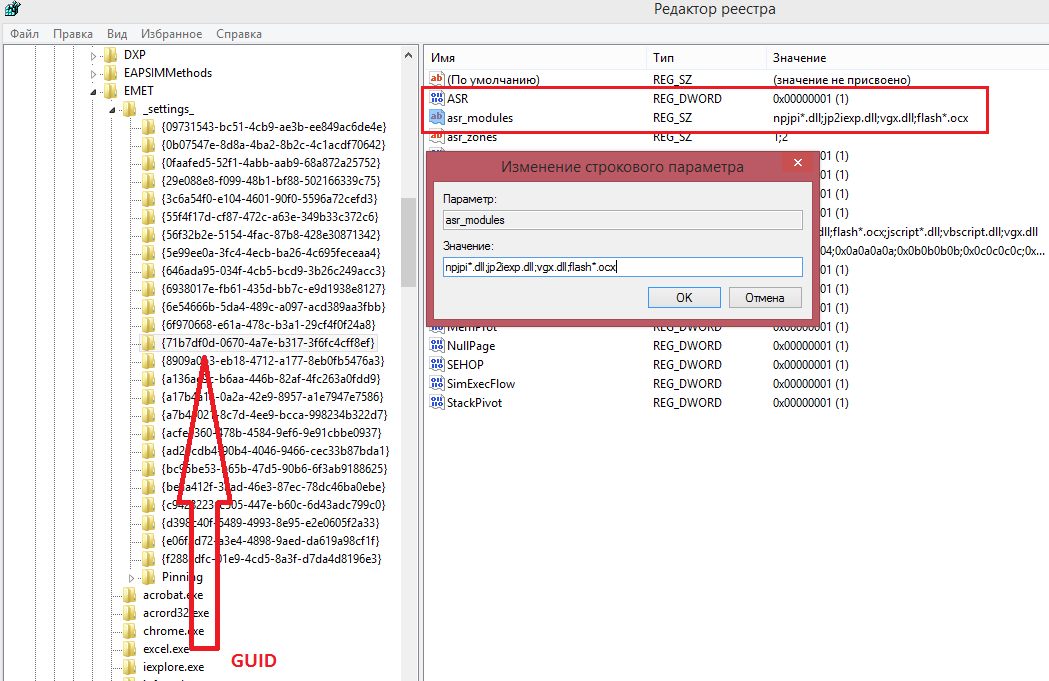
Fig. ASR for IE blocks Java activation (npjpi * .dll, jp2iexp.dll), Vector Markup Language DLL (vgx.dll) (see SA 2963983 ) and Flash Player (flash * .ocx).
ASR in EMET 5.0 TP can work only for the three programs listed above.

The zone setting is set by the asr_zones registry parameter, which can have the following values: Local (0), Intranet (1), Trusted (2), Internet (3), Untrusted (4).
In such a configuration, when you try to open a document with a Flash Player (SWF) object in Word or Excel, it will be forcibly blocked (or the user will be notified, see Application Configuration — Stop on exploit or Audit only).
Export Address Table Filtering Plus
Customization requiring more detailed technical considerations, see Announcing EMET 5.0 Technical Preview . Extends the existing EAF setting , which is used to protect against the shell code and allows access to exports of system library modules (kernel32.dll & ntdll.dll) only to the code of known EMET executable modules.
EAF + adds to the list of checked libraries and kernelbase.dll (the list can be expanded, see the setting below).

Fig. EAF + is activated by default for EMET 5.0 TP. But it is used only for the Internet Explorer browser , see the screenshot below.
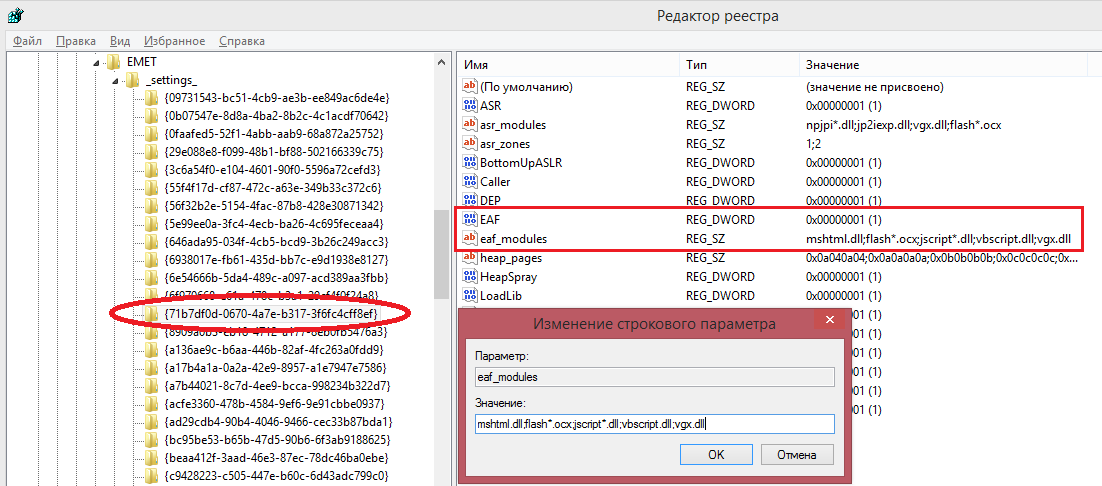
Fig. By default, EAF + is activated only for IE and is configured to protect the kernelbase, kernel32 and ntdll export tables from the code of the following modules: Image Rendering DLL (mshtml.dll), Flash Player objects (flash * .ocx), JScript DLL (jscript.dll), VBScript DLL (vbscript.dll) and Vector Markup Language DLL (vgx.dll). Modules were used in attacks to build chains of ROPs.
EAF + also blocks access to import tables for a suspicious code that has already been used in attacks (for example, see IE CVE-2013-3163 and CVE-2014-0322) when accessing export addresses via ActionScript (SWF). See option EAF + .
Normal EAF is activated for all applications from the list, see the Application Configuration -> Other -> EAF parameter and is used to protect only kernel32 and ntdll.
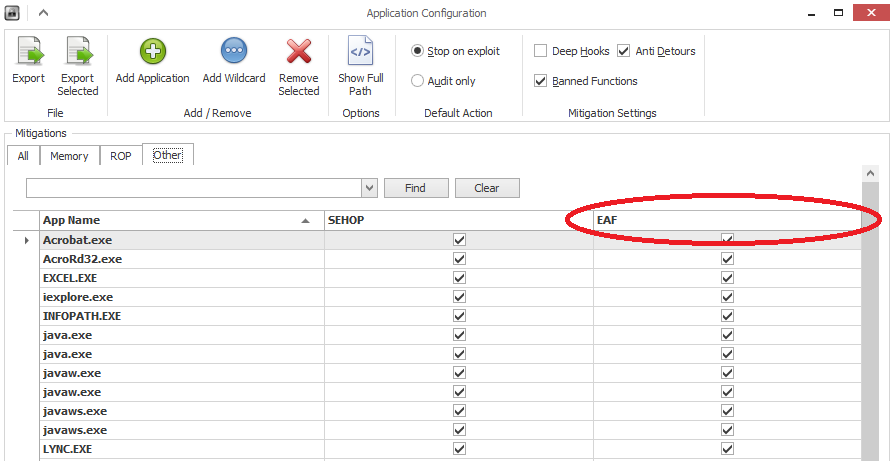
Fig. EAF in EMET 4.1 Release is active by default for all processes and is used to block unauthorized access to the EAT (export tables) of the kernel32 and ntdll libraries.

For example, a recent post on the MSRC for SA 2963983 contains the following sentence.
Our online review has revealed that it has been an experience of the Internet Explorer 10 and Internet Explorer 11.
This is despite the fact that the company released last year an update MS13-088 (see KB2907803 ), which disables the use of EPM by default for Internet Explorer 11 with the wording:
')
During the preview of Internet Explorer 11, it has been enabled by the Internet Explorer. This is what you’re incompatible with Enhanced Protected Mode.
Thus, before using Internet Explorer for the first time, be sure to check if your security settings are enabled, which the company declares as “basic to be safe”, but which are disabled by default.

Fig. IE11 on Windows 8.1 with MS13-088 installed, on the left, manually installed security options, then the restore default settings function was activated.
Similar settings exist in EMET.

Fig. EMET v4.1 Release in “Maximum security settings” mode, “Deep Hooks” setting is disabled. Used to block exploit actions for CVE-2014-1776. See More Details about Security Advisory 2963983 IE 0day .

Fig. EMET v5.0 TP, the default settings are Deep Hooks and ASR.
We have not stopped in detail on EMET 5.0 TP, users can download it from the MS Security TechCenter website . This version contains two new options called Attack Surface Reduction (ASR) and Export Address Table Filtering Plus (EAF +) . As seen in the screenshot above, ASR is enabled for Internet Explorer and can be used to prevent the use of CVE-2014-1776. Due to the fact that this version of EMET has the status of Technical Preview, the company delivers it with the “Deep Hooks” setting already enabled.
Attack Surface Reduction
In a narrower sense, ASR applies to Internet Explorer and uses browser-based URL Security Zones to block or allow the execution of plug-ins, such as Oracle Java or Adobe Flash Player, depending on which zone a user is visiting. More broadly, it is applied to applications in order to forcibly prohibit for them the activation of the corresponding plug-ins that can be used for operation.

Fig. Security Zones URLs that distinguish IE and are used for EMET Attack Surface Reduction.
The main meaning of ASR EMET for IE is that it allows the use of potentially unsafe Java and Flash Player plug-ins for websites that are on the organization’s network (intranet) and prohibits them for the Internet, where the content may be potentially unsafe. In addition, plug-ins are allowed to use in the Trusted zone (Trusted sites), see below.
By default, EMET 5.0 TP includes ASR for the following applications:
- MS Internet Explorer;
- MS Excel;
- MS Word.
Blocking of plug-ins is done by mask, or by the full name of the library.

Fig. ASR for IE blocks Java activation (npjpi * .dll, jp2iexp.dll), Vector Markup Language DLL (vgx.dll) (see SA 2963983 ) and Flash Player (flash * .ocx).
ASR in EMET 5.0 TP can work only for the three programs listed above.

The zone setting is set by the asr_zones registry parameter, which can have the following values: Local (0), Intranet (1), Trusted (2), Internet (3), Untrusted (4).
In such a configuration, when you try to open a document with a Flash Player (SWF) object in Word or Excel, it will be forcibly blocked (or the user will be notified, see Application Configuration — Stop on exploit or Audit only).
Export Address Table Filtering Plus
Customization requiring more detailed technical considerations, see Announcing EMET 5.0 Technical Preview . Extends the existing EAF setting , which is used to protect against the shell code and allows access to exports of system library modules (kernel32.dll & ntdll.dll) only to the code of known EMET executable modules.
EAF + adds to the list of checked libraries and kernelbase.dll (the list can be expanded, see the setting below).

Fig. EAF + is activated by default for EMET 5.0 TP. But it is used only for the Internet Explorer browser , see the screenshot below.

Fig. By default, EAF + is activated only for IE and is configured to protect the kernelbase, kernel32 and ntdll export tables from the code of the following modules: Image Rendering DLL (mshtml.dll), Flash Player objects (flash * .ocx), JScript DLL (jscript.dll), VBScript DLL (vbscript.dll) and Vector Markup Language DLL (vgx.dll). Modules were used in attacks to build chains of ROPs.
EAF + also blocks access to import tables for a suspicious code that has already been used in attacks (for example, see IE CVE-2013-3163 and CVE-2014-0322) when accessing export addresses via ActionScript (SWF). See option EAF + .
... this is where the mitigation is used.
Normal EAF is activated for all applications from the list, see the Application Configuration -> Other -> EAF parameter and is used to protect only kernel32 and ntdll.

Fig. EAF in EMET 4.1 Release is active by default for all processes and is used to block unauthorized access to the EAT (export tables) of the kernel32 and ntdll libraries.
Source: https://habr.com/ru/post/221129/
All Articles