New vulnerability Internet Explorer is exploited in-the-wild
Microsoft has issued a security alert ( SA 2963983 ), which states that the new 0day Remote Code Execution vulnerability CVE-2014-1776 is present in all versions of MS Internet Explorer 6-11 and is used by attackers in targeted attacks to deliver malicious code (drive- by download). Attackers use a specially crafted webpage and a Flash Player object to exploit this vulnerability.

')
Thus, users of Internet Explorer 10 & 11 on Windows 7 x64 & Windows 8 / 8.1 with the Enhanced Protected Mode (EPM) setting enabled are protected from the actions of this exploit. In addition, users of EMET 4.1 and 5.0 TP are also protected. These versions of EMET include the browser process as protected by default. Recall that EPM enhances browser immunity to exploits by launching tab processes in a special limited AppContainer mode on Windows 8+ (AppContainer is also used by default for all Modern UI applications).

Fig. The browser process is in the list of protected in the EMET settings (applications in bold type are included in the default list).
Microsoft will release the corresponding update, which closes this vulnerability in the next patch tuesday, or as out-of-cycle, i.e., unplanned.
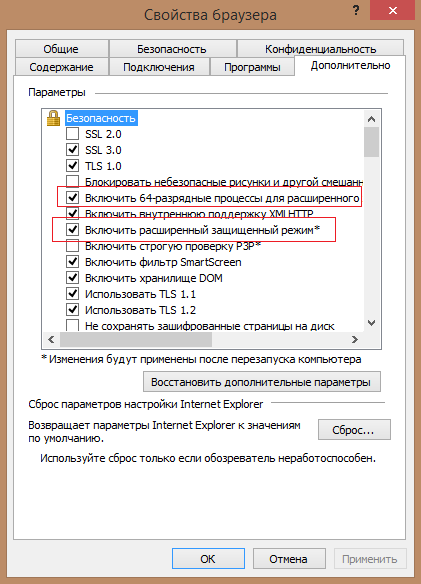
Fig. The safest IE11 mode with sandboxing enabled (Advanced Protected Mode) and 64-bit tab-based anti-heap-spray processes on Windows 8.1 x64.
It has been shown that it has been updated for the first time. risk.

')
Thus, users of Internet Explorer 10 & 11 on Windows 7 x64 & Windows 8 / 8.1 with the Enhanced Protected Mode (EPM) setting enabled are protected from the actions of this exploit. In addition, users of EMET 4.1 and 5.0 TP are also protected. These versions of EMET include the browser process as protected by default. Recall that EPM enhances browser immunity to exploits by launching tab processes in a special limited AppContainer mode on Windows 8+ (AppContainer is also used by default for all Modern UI applications).

Fig. The browser process is in the list of protected in the EMET settings (applications in bold type are included in the default list).
Microsoft will release the corresponding update, which closes this vulnerability in the next patch tuesday, or as out-of-cycle, i.e., unplanned.

Fig. The safest IE11 mode with sandboxing enabled (Advanced Protected Mode) and 64-bit tab-based anti-heap-spray processes on Windows 8.1 x64.
Source: https://habr.com/ru/post/221025/
All Articles