Zero-day attacks, APT attacks and protection against them using Check Point solutions

Many security systems today are matching systems (signatures) and behavior patterns of already known threats. They are powerless against new attacks, for which there are still no signatures and patches from the manufacturer. Moreover, new attacks, as a rule, do not have the goal of causing appreciable damage, but are designed for the inconspicuous, secretive performance of harmful actions.
This article will look at the anatomy of malware intrusion into IT infrastructures, as well as Check Point solutions that can be used to protect against this type of attack.
')
So, how does the zero-day attack penetration stage in IT infrastructure?
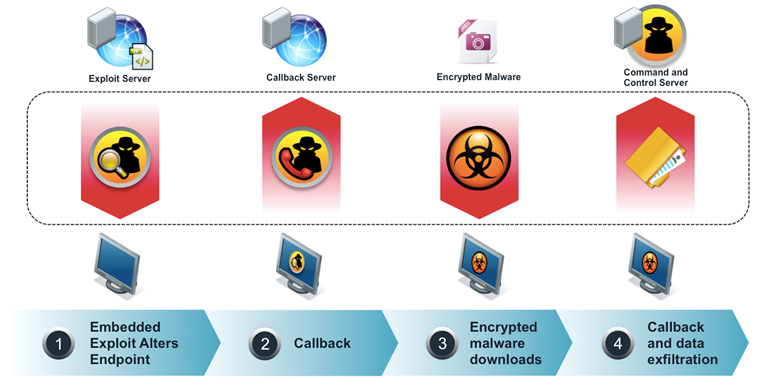
1. An email arrives to a specific employee using targeted phishing, which contains an attachment (file, archive), usually an Adobe Reader file (because the most vulnerable corporate application is Adobe Reader) or an MS DOC file with an embedded exploit for the application used . As soon as the user opens it or performs a preview, the exploit has already begun to take effect. It overflows the buffer of the application that opened the file, and receives local administrative rights, placing the appropriate command for execution.
2. After this, the malicious code generates an outbound callback to the control server (Command & Control Server).
3. Having information about the installed software and the OS used by the victim, malicious code is downloaded using the wget method from the C & C server, usually encrypted and integrated into the file with the jpg extension to avoid deleting the web gateway (in most cases, downloading .exe files is prohibited corporate policy).
4. The downloaded file is decrypted, installed in the system and begins to perform data exfiltration, i.e. find personal data (logins, passwords, personal files), corporate data (accounts, invoices, etc.) and send them to a specific address (usually via an encrypted channel)
5. The last step - the spread and infection of other systems. Knowing the passwords from personal communications services (installing a keylogger on a compromised system), you can send malicious links on behalf of the victim to anyone who communicates with her.
All these actions are displayed in Figure 1.
Figure 1. The process of penetration of malware in the IT infrastructure
Defining zero-day attacks and advanced persistent threats
Let's now look at how Check Point solutions detect such penetration attempts and what are the key factors when analyzing such attacks.
Start by looking at the malware detection task.
As previously discussed, the user initially receives an attachment in an email with the contents of the exploit. How to know if an attachment is infected or not?
The answer is to conduct a static and, if necessary, dynamic analysis of all documents and attachments in emails on the content of threats.
Static analysis consists of checking for compliance with Check Point Antivirus signatures.
If no threats are detected in web objects and documents, they are checked for suspicion by:
• heuristic analysis;
• checking SNORT and YARA rules;
• verification of the presence of a trusted digital signature of the document;
If the document is suspicious, a dynamic analysis is performed — run in an emulated user environment, which is a virtual machine with pre-installed main applications. Next, the Check Point system monitors the behavior of a running document (creating additional files, changing keys in the registry, establishing communications with C & C servers).
Next, a verdict about the harmfulness of the document. If it is infected, then such a document is blocked. No - skipped to user.
The regulated delay in checking with static and dynamic analysis is up to 2 minutes.
This solution in Check Point is presented in two forms:
• cloud service
• device at the customer site
Service
When connecting the service there are several types of quotas, which are displayed in Table 1.
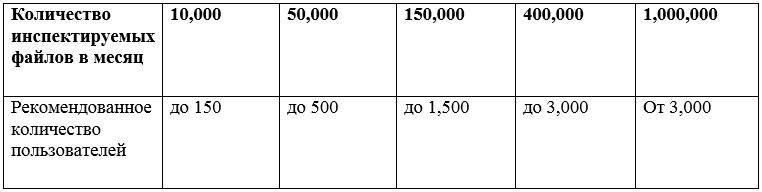
Table 1 Quoting of Check Point email attachment cloud service for content of zero-day attacks and APT attacks
Supported platforms and Check Point operating environments for connecting the service are shown in the table below.
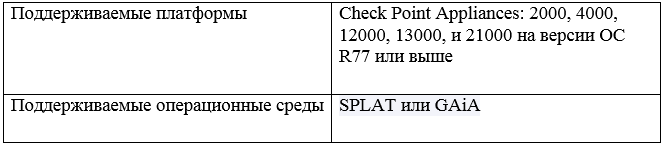
The connection of this service does not depend on the number of Check Point gateways in the existing IT infrastructure.
Device at the customer site
If there is no desire to connect the cloud service for one reason or another, you can take a Check Point device specifically designed for this.
There are two Check Point devices for this task. Quoting also occurs according to the number of files inspected per month. The number of users is a recommended parameter, but not as important as the number of files. These devices and their parameters are displayed in Fig.2.
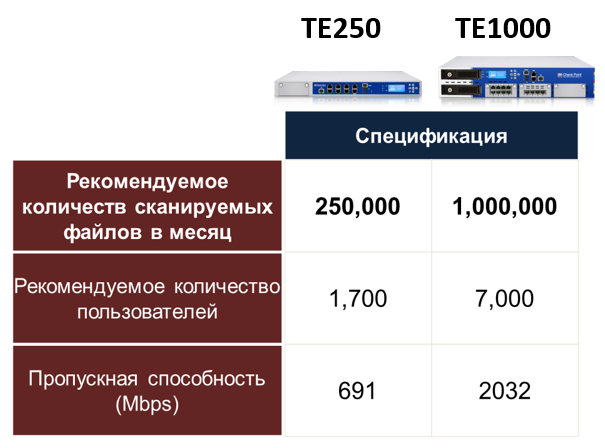
Fig.2. Check Point devices for inspecting email attachments for content of zero-day attacks and APT attacks
Both the service and the device have the same technical specifications for the types of files being inspected and the emulated operating environments supported. The specification for these parameters is presented in Table 2.
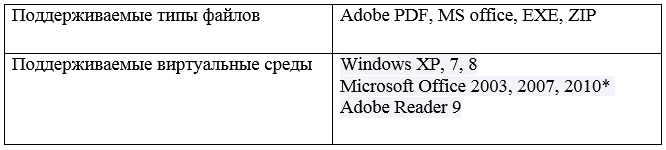
Table 2 Supported file formats and virtual environments for inspecting email attachments
There is also a test online service that can be used to analyze a file for the presence of malware and, in a positive case, its actions will be displayed in an emulated user environment. This service is available at the web link below.
threatemulation.checkpoint.com/teb/upload.jsp
Total
In all cases, an exploit is used, which gains control over the victim's PC and establishes outgoing network communication to the C & C server, which then transmits malicious software that performs a variety of actions.
It is extremely difficult to notice such attacks, as they are not yet aware of them and almost all modern security systems operate on the principle of searching for coincidences and known behavior patterns. Detecting in most cases is also difficult, since they clearly do not show their actions, but imperceptibly send data to the attacker.
Source: https://habr.com/ru/post/220657/
All Articles