Who does BillGates attack?

It seems that the BillGates botnet is spreading more and more - already 4 familiar people have asked me how to get rid of it, and what it is.
I managed to get a fresh version that worked fine on my system (I got commands from the server and DOS-silt), and it's fun!
What changed?
The “Gates” module now consists of 2 modules: “Beikong” and “Monitor (moni)” . If it runs along the path / usr / bin / pojie (in my case), then moni runs, if on some other path, then Beikong. Beikong, in essence, is a hrenoten who reconfigures and updates other modules, and moni monitors the status of all modules (and restarts them if necessary), collects statistics from them and sends it to the server via Beikong. If / usr / bin / pojie does not exist, then Beikong will copy itself there and launch it.
')
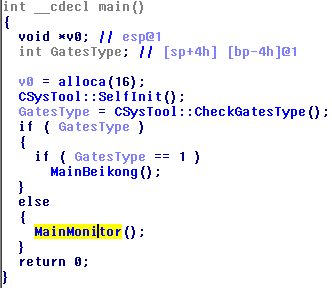
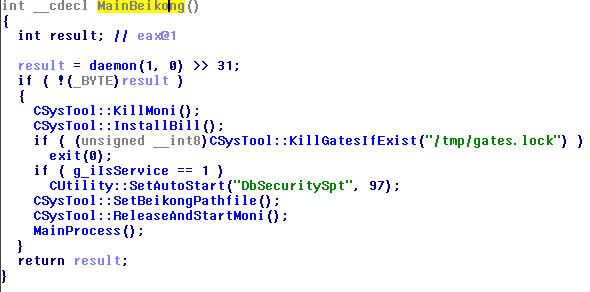
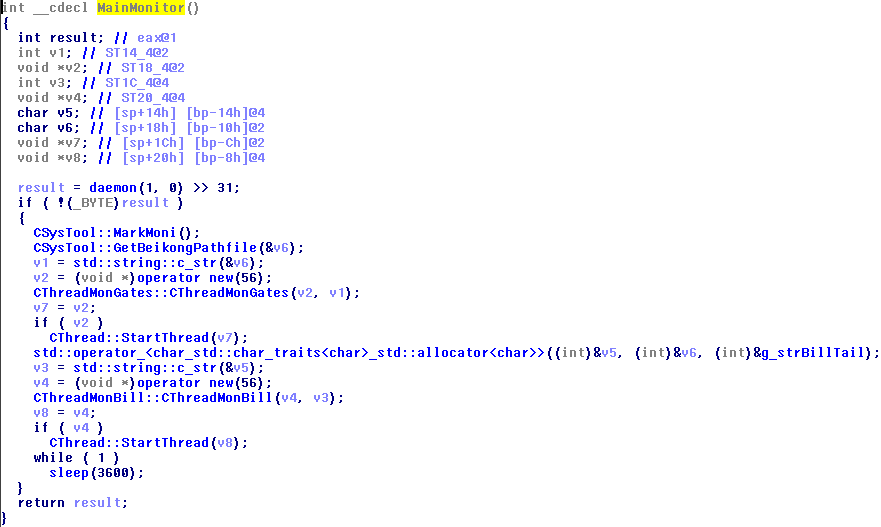
Beikong writes the path to itself in /tmp/notify.file , and moni writes its PID to /tmp/moni.lock .
Gates is still dropping a simple DDoS module packed with UPX (in my case, it was again called cupsddh).
No more major changes.
Time to have fun!
Since the botnet was working on my computer and even started attacking someone, I decided to see how traffic flows between CnC servers and bots. As expected, there was no encryption, and everything went in the clear.
It should be noted that Gates uses one type of CnC servers (for the Bill module and sending statistics via moni), and “Melinda” (the module I called “knocking” in the previous article. In fact, this is an advanced DDoS module , and I was wrong. There was no name in the code, and I decided to give this) different, and they have a different communication protocol, but there are similarities.
At startup, both modules connect to their servers and send a HELLO package: for Gates, it contains the OS name, the kernel, the name and version of the module, and Melinda only the OS name and the kernel.
The data in the packages I replaced in accordance with the recommendations of the famous video .

Then, they exchange PING packets with each other.
Gates CnC can send multiple servers at once to attack via cupsddh. The module is not very smart, it can attack only via TCP and cannot forge packets, which cannot be said about Melinda, which can attack via TCP, UDP, ICMP and 2 types of DNS.
Tracking
In general, I decided to write a tracker for this botnet: a client that would connect to CnC servers and receive commands on DDoS. The tracker works with both Gates servers and Melinda. And wrote.
github.com/ValdikSS/billgates-botnet-tracker
For about a week, I tracked the botnet’s actions and wrote the results into the database.
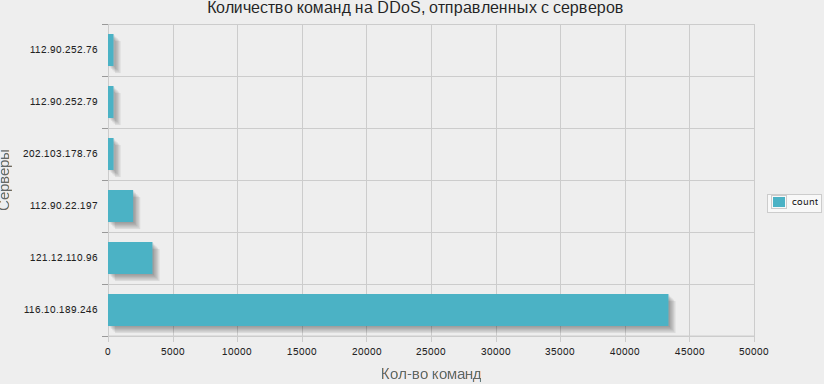
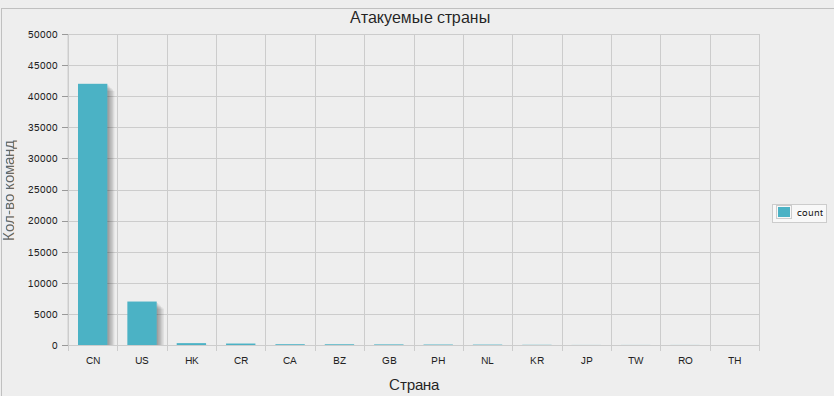
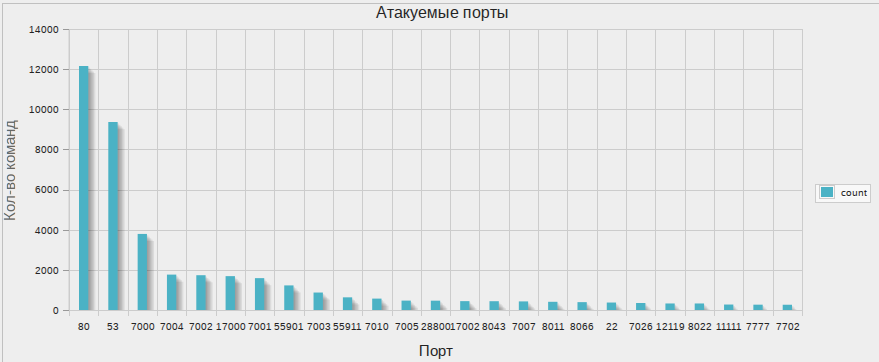

Yes, I'm so lazy that the graphics drew me phpmyadmin.
You can track the botnet's actions in real time here:
billgates.valdikss.org.ru
Take care of your servers.
Source: https://habr.com/ru/post/220027/
All Articles