Use of encryption in Russian companies
Introduction
A little more than two decades ago, cryptography in Russia was approximately at the same level of secrecy as weapons production technology - its practical application belonged exclusively to the military and special services, that is, it was completely under the control of the state. It was not possible to meet any publications and scientific papers on this issue in the open access - the topic of cryptography was closed.
The situation changed only in 1990, when the encryption standard GOST 28147-89 was introduced. Initially, the algorithm had the chipboard and officially "completely open" became only in 1994.
It is difficult to say exactly when it was in the domestic cryptography that the information breakthrough was made. Most likely, this happened with the advent of the general public access to the Internet, after which the network began to publish numerous materials with descriptions of cryptographic algorithms and protocols, articles on cytoanalysis and other information related to encryption.
')
Under current conditions, cryptography could no longer remain the prerogative of the state alone. In addition, the development of information technology and communications has necessitated the use of cryptographic protection by commercial companies and organizations.

Today, the means of cryptographic protection of information (CIPS) include: encryption tools, imitation protection tools, electronic digital signature tools, encryption tools, tools for producing key documents and key documents themselves. [4, p2-3.]
Further in the article we will talk about the practical use of encryption and ICPT at the moment found in Russian companies and organizations. The following directions will be considered:
- protection of personal data information systems;
- protection of confidential company information;
- corporate email encryption;
- create and verify digital signatures.
The use of cryptography and SKZI in Russian companies
1. Introduction of cryptographic tools in personal data protection systems
The activity of almost any Russian company today is associated with the storage and processing of personal data (PDN) of various categories, for which the legislation of the Russian Federation puts forward a number of requirements [1]. To accomplish them, the company’s management, first of all, faces the need to form a model of threats to personal data and develop a personal data protection system on its basis, which should include a means of cryptographic information protection. [2, from 1.]
The following requirements are put forward to the CIPP, introduced into the personal data protection system:
- A cryptographic tool must function properly in conjunction with hardware and software that can affect the fulfillment of its requirements. [3, p. 15.]
- To ensure the security of personal data during their processing, cryptographs certified in the certification system of the Federal Security Service of Russia should be used. [3, p. 15.]
A cryptographic tool, depending on the level of protection it provides, can be assigned to one of six classes (1, 2, 3, 1, 2, 1). The introduction of a cryptographic medium of a particular class with the protection system is determined by the category of the intruder (subject of the attack), which is determined by the operator in the threat model.
Thus, the means of cryptographic protection are now effectively used by companies and organizations for the protection of personal data of Russian citizens and are one of the most important components in personal data protection systems.
2. Protection of corporate information
If in clause 1, the use of antiharphic drugs is primarily due to the requirements of the legislation of the Russian Federation, then in this case the management of the company itself is interested in applying SKZI. With the help of an encryption tool, a company gets the opportunity to protect its corporate information - information that represents commercial secrets, intellectual property, operational and technical information, etc.
Today, for effective use in a corporate environment, the encryption program should provide:
- data encryption on a remote server;
- support for asymmetric cryptography;
- transparent encryption;
- network folder encryption;
- the possibility of differentiation of access rights to confidential information between employees of the company;
- the ability of employees to store private keys on external storage media (tokens).
So, the second application of CIPF is the protection of confidential company information. An encryption tool that supports the above possibilities can provide sufficiently reliable protection, but it must be used as part of an integrated approach to information security. This approach additionally involves the use of firewalls, antiviruses and firewalls, and also includes the development of a model of information security threats, the development of necessary information security policies, the appointment of those responsible for information security, control of electronic document management, control and monitoring of employees, etc.
3. Electronic signature
Electronic signature (ES) today is a full-fledged analogue of a handwritten signature and can be used by legal entities and individuals in order to provide a document in digital format with legal force. The use of electronic signature in electronic document management systems significantly increases the speed of concluding commercial transactions, reduces the volume of paper accounting documents, saves employees time. In addition, the ES reduces the costs of an enterprise to enter into contracts, draw up payment documents, receive various certificates from government agencies and much more.
Means of cryptographic protection, as a rule, have in their composition functions for the creation and verification of electronic signatures. Russian legislation to such SKZI put forward the following requirements [5, p. 3.]:
When creating an ES, they should:
- show to the person signing the electronic document the content of the information he signs;
- create an ES only after confirmation by the person signing the electronic document of the operation for creating an ES;
- unequivocally show that the EA is created.
When checking the ES, they should:
- show the content of an electronic document signed by ES;
- show information on making changes to the electronic document signed by EDS;
- point to the person using the electronic signature key of which electronic documents are signed.
4. Email Encryption
For most companies, email is the primary means of communication between employees. It's no secret that a huge amount of confidential information is being sent today via corporate e-mail: contracts, invoices, information about products and pricing policies of a company, financial indicators, etc. If such information is available to competitors, this can cause significant damage to the company until the termination of its activities.
Therefore, the protection of corporate mail is an extremely important component in ensuring the information security of a company, the implementation of which becomes possible also through the use of cryptography and encryption tools.
Most email clients such as Outlook, Thinderbird, The Bat! etc., allow you to customize the exchange of encrypted messages based on public-key and private-key certificates (certificates in X.509 and PKCS # 12 formats, respectively) created using cryptographic protection tools.
It is also worth mentioning the possibility of cryptographic tools to work as certification authorities (CAs). The main purpose of the certification center is to issue encryption certificates and confirm the authenticity of encryption keys. In accordance with Russian legislation, CAs are divided into classes (1, 2, 3, 1, 2, 1), each of which has a number of requirements [5]. At the same time, the class of SKZI, used in the facilities of the CA, should not be lower than the corresponding class of CA [5, p. 14.].
Using CyberSafe Enterprise
In developing the CyberSafe Enterprise program, we tried to take into account all the above possibilities, including them in the functional set of the program. So, it supports the functions listed in paragraph 2 of this article, encryption of e-mail, creation and verification of digital signatures, as well as work as a certification center.
The presence of a public key server in CyberSafe allows companies to organize convenient key exchange between their employees, where each of them can publish their own public key, as well as download the public keys of other users.
Next, we will dwell on the possibility of introducing CyberSafe Enterprise into personal data protection systems. This feature is possible thanks to the support of the CryptoPro CSP crypto-provider program certified by the Federal Security Service of the Russian Federation as KS1, KS2, KS2 and KS3 classes (depending on the version) and specified in clause 5.1 of the “Guidelines for ensuring personal data security with cryptographic tools” :
“The embedding of cryptographic tools of class KS1 and KS2 is carried out without control from the FSB of Russia (if this control is not provided for by the technical task for the development (modernization) of the information system)”.
Thus, having in its structure the built-in cryptographic cryptographic information system CryptoPro CSP, the CyberSafe Enterprise program can be used in the system of protection of personal data of KC1 and KC2 classes.
After installing CryptoPro CSP on a user's computer, when creating a certificate in CyberSafe Enterprise, it will be possible to create a CryptoPRO certificate:
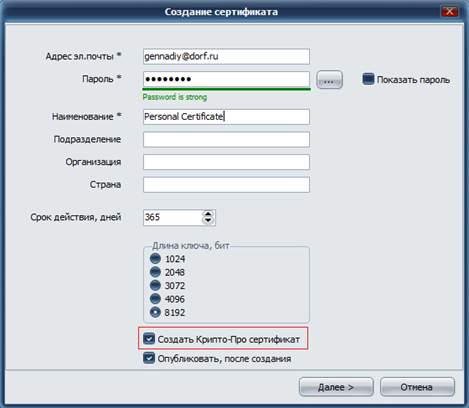
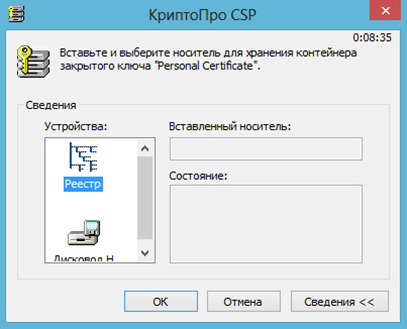
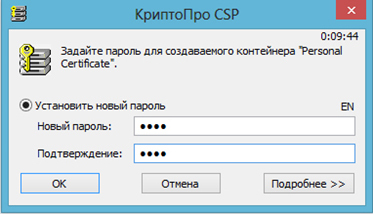
Next, you need to select the storage location of the CryptoPro private key container and set a password for the container. For storage, the operating system registry or removable media (token) can be used:
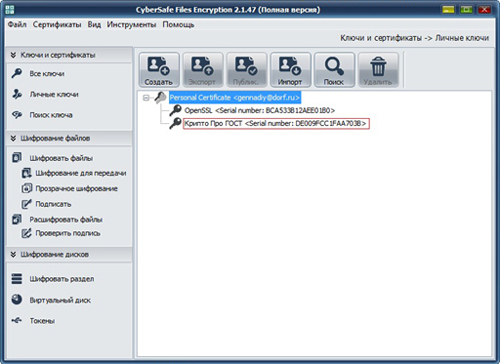
After completing the creation of a CyberSafe certificate, the CryptoPRO keys are also created, displayed on your bundle, and are available for use:
In the event that it becomes necessary to export the CryptoPro keys to a separate file, this can be done through the standard CyberSafe key export function:
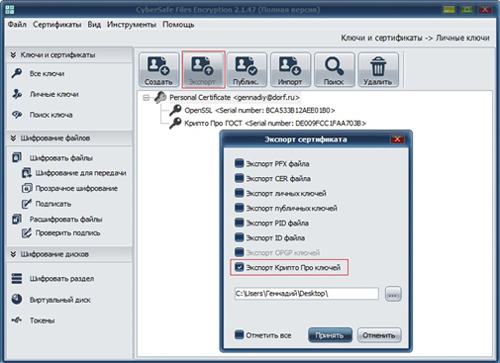
If you want to encrypt files for transfer to other users (or sign them with your digital signature) and use CryptoPro keys for this, you should choose CryptoPro from the list of available crypto-providers:
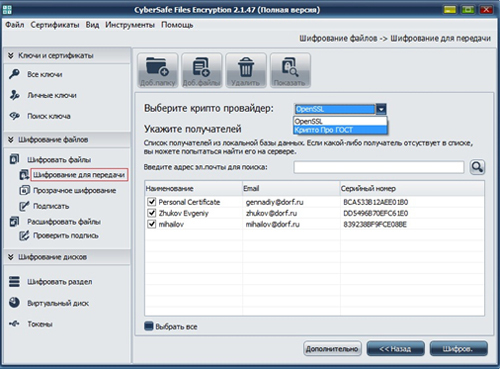
In the event that you want to use CryptoPro keys for transparent file encryption, CryptoPro should also be specified in the window for selecting certificates as a crypto-provider:
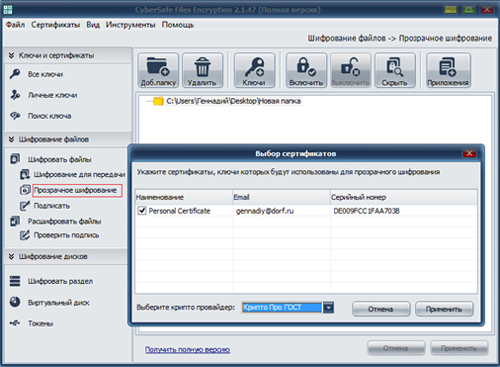
In CyberSafe, it is possible to use CryptoPRO and the GOST algorithm for encrypting logical disks / partitions and creating virtual encrypted disks:
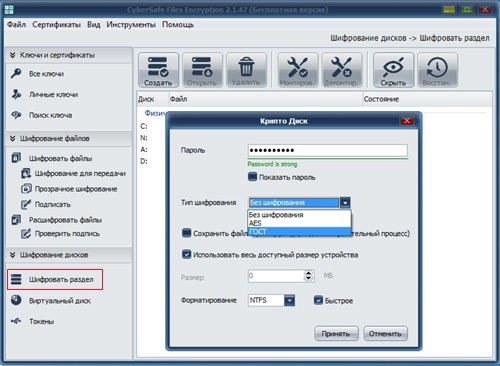
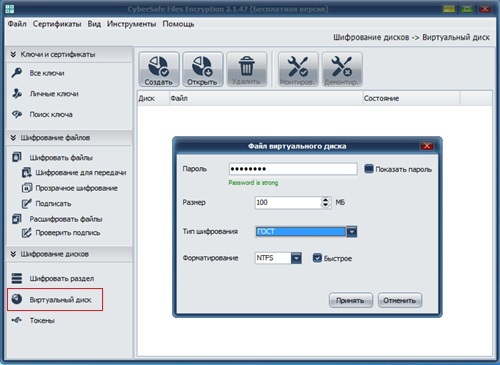
Also, based on CryptoPro certificates, email encryption can be configured. In KpriptoPro CSP, the algorithms for generating and verifying electronic signature are implemented in accordance with the requirements of GOST R 34.10-2012, the data encryption / decryption algorithm is implemented in accordance with the requirements of GOST 28147-89.
Today CyberSafe is the only program that combines the functions of encrypting files, network folders, logical drives, e-mail and the ability to work as a certification center with support for encryption standards GOST 28147-89 and GOST R 34.10-2012.
Documents:
1. Federal Law “On Personal Data” No. 152- dated July 27, 2006.
2. The provision on ensuring the security of personal data during their processing in personal data information systems , approved by the Decree of the Government of the Russian Federation of November 17, 2007 No. 781.
3. Methodical recommendations on ensuring the security of personal data using crypto tools when processing them in personal data information systems using automation equipment approved by the management of the 8th Center of the Federal Security Service of Russia on February 21, 2008 No. 149 / 54-144.
4. Regulations on the development, production, sale and operation of encryption (cryptographic) information security tools , approved by the Order of the Federal Security Service of the Russian Federation of February 9, 2005 No. 66.
5. Requirements for means of electronic signature and Requirements for means of certification center , approved by Order of the Federal Security Service of the Russian Federation dated December 27, 2011 No. 796.
Source: https://habr.com/ru/post/220023/
All Articles