How browsers implement digital certificate revocation
In our post on the Heartbleed vulnerability, we pointed out that one of the additional security measures for working with HTTPS connections is the option of checking a revoked digital certificate in the browser. For Heartbleed, this is especially important, since after updating the vulnerable version of OpenSSL on the server, the company's specialists need to re-acquire the new private key (SSL / TLS) and generate a new certificate and revoke the old one. Browsers should distinguish such situations (use of a revoked digital certificate in HTTPS) and notify their users that their connection to the server is no longer trusted.
SSL or TLS digital certificates are used to bind a cryptographic public key to information about an organization (company, service, etc.). Thus, being issued by a Certification Authority, he guarantees to the client of this organization that the public encryption key used belongs to this particular organization. A secure HTTPS connection takes advantage of such a public key encryption system, in which SSL / TLS certificates, as well as the server's private key, are used to establish a completely secure connection that the user can unconditionally trust when transferring his data.
Previously, information was published that researchers using the Heartbleed vulnerability successfully managed to compromise such protected services as CloudFlare, OpenVPN, as well as Yahoo mail. Having stolen the secret key, attackers can decrypt user session data and later introduce themselves as a server, and the user will think that he is working with a legitimate source. In such a case, the public key certificate itself is compromised and the CA that issued the certificate cannot guarantee that the user is working with the real server.
')
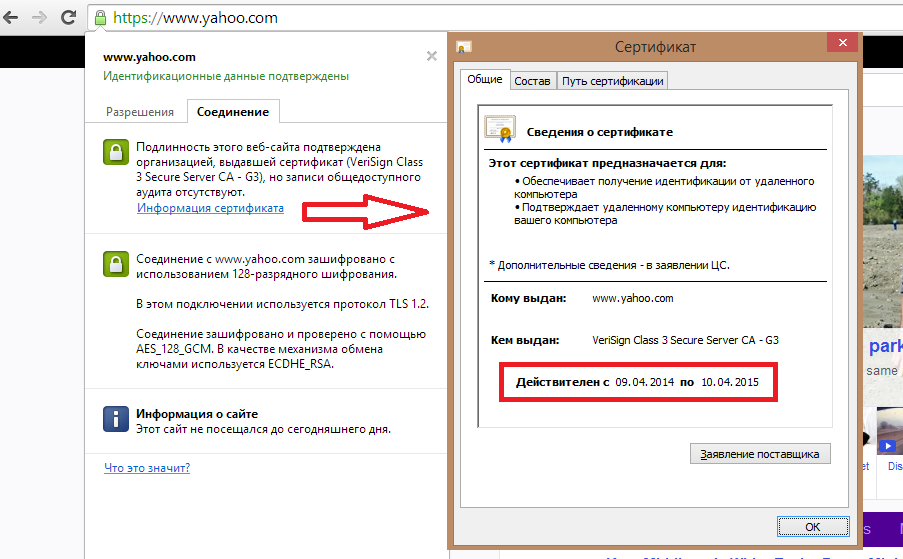
Fig. Yahoo re-issued digital certificate.
When the server upgraded one of the vulnerable versions of OpenSSL to the required 1.0.1g, a new public key certificate was obtained (and the corresponding private key of the server), the old certificate was revoked, and the user changed the password to his account, he can still be vulnerable. working with your browser. We pointed out that attackers could later use the stolen private key in order to introduce themselves as a server or organize a Man-in-the-Middle attack, thus compromising HTTPS. This can happen because the browser used has not updated the information about the revoked digital certificate and continues to consider it trusted.
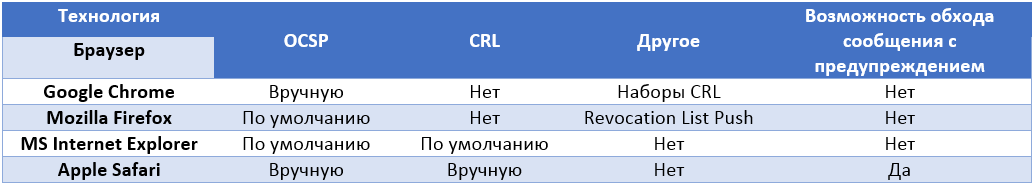
There are two main ways that a browser can check certificate status information (i.e., whether it is valid or revoked): certificate status protocol ( Online Certificate Status Protocol, OCSP ) and certificate revocation list ( CRL) ). Through OCSP, the client can receive information from the CA about the status of the certificate before making an HTTPS connection with the corresponding server. CRL contains a list of revoked digital certificates, and this list is cached by the browser during work.
Google chrome
In February 2012, Google turned off verification of revoked digital certificates for Chrome in new browser versions. This decision was due to the slowness and time delays that are needed to process the request for obtaining the status of a certificate through OCSP. The status check took about 300 milliseconds or almost a second for each new HTTPS connection. Google also considered that such a delay could prevent the transition of services to the use of HTTPS due to the fact that very few of their customers would like such a delay each time they connect to the server (set up a new connection). The company also refused to permanently monitor the status of certificates, since studies have shown that most of the certificates were withdrawn not because of compromise by the attackers, but because of other administrative decisions of the companies.
The browser checks the status of certificates using CRL revocation certificate lists (set of CRLs), but this practice is related to caching, and the browser will not have the latest information about the certificates used. In order to enable the timely verification of digital certificates before using them in HTTPS, you must set the option “Check if the server certificate has been revoked” in the browser settings. By default, this option is disabled. When this setting is activated, the browser will use the OCSP-mentioned requests to check the status of certificates when trying to establish a new HTTPS connection. The browser will not allow the user to view the web page with the revoked certificate, displaying a warning.
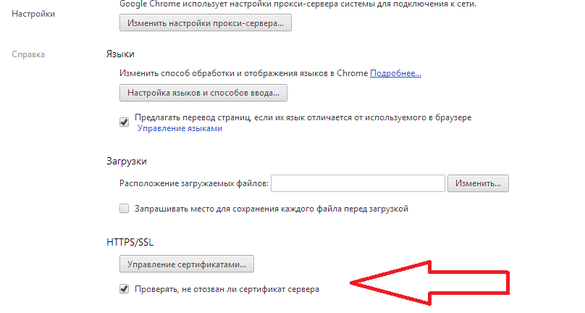
Fig. Customize Google Chrome.
Mozilla firefox
Firefox developers have refused to permanently check the status of certificates using CRLs in recent browser versions, instead they use the OCSP protocol, which is enabled by default . At the same time, the CRLs in the browser are still present and the information for them is updated on a regular basis (asynchronously, regardless of the connections to be established, through the so-called Revocation List Push mechanism). Like Chrome, Firefox warns the user about the revocation of the certificate by the server, thus blocking the user's access to the requested page. As you can see in the screenshot below, the browser contains the option “If the connection to the OCSP error occurs, treat the certificate as invalid”, which is disabled by default. Thus, if the requested CA is unavailable, to check the status of the certificate, the user will receive an error message when working with any certificate, since it is impossible to say whether it is valid or revoked.
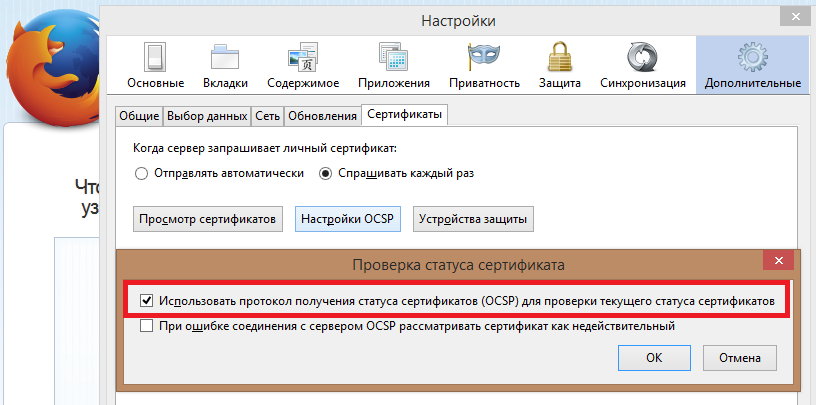
Fig. The corresponding option is to check the status of a digital certificate with Mozilla Firefox.
MS Internet Explorer
The behavior of the browser depends on the version and OS you are using. On modern releases of Windows 7 and Windows 8, Internet Explorer (starting with version 8) supports checking certificates of new connections through OCSP, and also uses CRLs as a fallback. By default, OCSP is used to check the status of a certificate. Like Google Chrome and Mozilla Firefox, Internet Explorer does not allow the user to browse the web pages that use a revoked digital certificate to connect to.
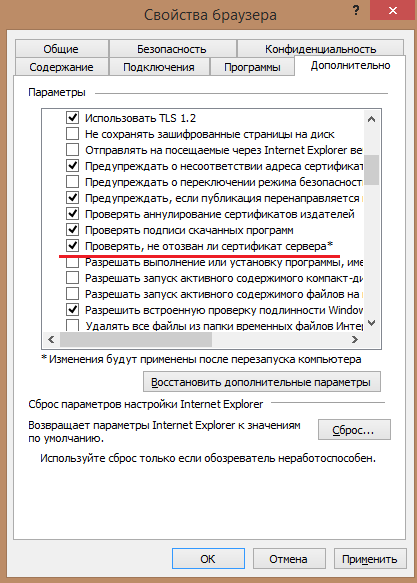
Fig. Configure certificate revocation checking in IE 8+ on Windows 7+ ( enabled by default ).
Apple safari
This browser does not have built-in certificate revocation checking mechanisms. Instead, he uses the so-called. Apple Keychain Access . Settings related to verification of revoked certificates are located in the “Settings” -> “Certificates” menu. The "Best Attempt" setting is used to set certificate checks using OCSP and CRL checks. By default, certificate checking is disabled . Unlike the three browsers mentioned above, Safari allows the user to skip the certificate revocation warning. To do this, the user needs to click on the “Continue” item in the pop-up window.
Based on the original source: blog.cisecurity.org/how-browsers-handle-certificate-revocation
SSL or TLS digital certificates are used to bind a cryptographic public key to information about an organization (company, service, etc.). Thus, being issued by a Certification Authority, he guarantees to the client of this organization that the public encryption key used belongs to this particular organization. A secure HTTPS connection takes advantage of such a public key encryption system, in which SSL / TLS certificates, as well as the server's private key, are used to establish a completely secure connection that the user can unconditionally trust when transferring his data.
Previously, information was published that researchers using the Heartbleed vulnerability successfully managed to compromise such protected services as CloudFlare, OpenVPN, as well as Yahoo mail. Having stolen the secret key, attackers can decrypt user session data and later introduce themselves as a server, and the user will think that he is working with a legitimate source. In such a case, the public key certificate itself is compromised and the CA that issued the certificate cannot guarantee that the user is working with the real server.
')

Fig. Yahoo re-issued digital certificate.
When the server upgraded one of the vulnerable versions of OpenSSL to the required 1.0.1g, a new public key certificate was obtained (and the corresponding private key of the server), the old certificate was revoked, and the user changed the password to his account, he can still be vulnerable. working with your browser. We pointed out that attackers could later use the stolen private key in order to introduce themselves as a server or organize a Man-in-the-Middle attack, thus compromising HTTPS. This can happen because the browser used has not updated the information about the revoked digital certificate and continues to consider it trusted.
There are two main ways that a browser can check certificate status information (i.e., whether it is valid or revoked): certificate status protocol ( Online Certificate Status Protocol, OCSP ) and certificate revocation list ( CRL) ). Through OCSP, the client can receive information from the CA about the status of the certificate before making an HTTPS connection with the corresponding server. CRL contains a list of revoked digital certificates, and this list is cached by the browser during work.
Google chrome
In February 2012, Google turned off verification of revoked digital certificates for Chrome in new browser versions. This decision was due to the slowness and time delays that are needed to process the request for obtaining the status of a certificate through OCSP. The status check took about 300 milliseconds or almost a second for each new HTTPS connection. Google also considered that such a delay could prevent the transition of services to the use of HTTPS due to the fact that very few of their customers would like such a delay each time they connect to the server (set up a new connection). The company also refused to permanently monitor the status of certificates, since studies have shown that most of the certificates were withdrawn not because of compromise by the attackers, but because of other administrative decisions of the companies.
The browser checks the status of certificates using CRL revocation certificate lists (set of CRLs), but this practice is related to caching, and the browser will not have the latest information about the certificates used. In order to enable the timely verification of digital certificates before using them in HTTPS, you must set the option “Check if the server certificate has been revoked” in the browser settings. By default, this option is disabled. When this setting is activated, the browser will use the OCSP-mentioned requests to check the status of certificates when trying to establish a new HTTPS connection. The browser will not allow the user to view the web page with the revoked certificate, displaying a warning.

Fig. Customize Google Chrome.
Mozilla firefox
Firefox developers have refused to permanently check the status of certificates using CRLs in recent browser versions, instead they use the OCSP protocol, which is enabled by default . At the same time, the CRLs in the browser are still present and the information for them is updated on a regular basis (asynchronously, regardless of the connections to be established, through the so-called Revocation List Push mechanism). Like Chrome, Firefox warns the user about the revocation of the certificate by the server, thus blocking the user's access to the requested page. As you can see in the screenshot below, the browser contains the option “If the connection to the OCSP error occurs, treat the certificate as invalid”, which is disabled by default. Thus, if the requested CA is unavailable, to check the status of the certificate, the user will receive an error message when working with any certificate, since it is impossible to say whether it is valid or revoked.

Fig. The corresponding option is to check the status of a digital certificate with Mozilla Firefox.
MS Internet Explorer
The behavior of the browser depends on the version and OS you are using. On modern releases of Windows 7 and Windows 8, Internet Explorer (starting with version 8) supports checking certificates of new connections through OCSP, and also uses CRLs as a fallback. By default, OCSP is used to check the status of a certificate. Like Google Chrome and Mozilla Firefox, Internet Explorer does not allow the user to browse the web pages that use a revoked digital certificate to connect to.

Fig. Configure certificate revocation checking in IE 8+ on Windows 7+ ( enabled by default ).
Apple safari
This browser does not have built-in certificate revocation checking mechanisms. Instead, he uses the so-called. Apple Keychain Access . Settings related to verification of revoked certificates are located in the “Settings” -> “Certificates” menu. The "Best Attempt" setting is used to set certificate checks using OCSP and CRL checks. By default, certificate checking is disabled . Unlike the three browsers mentioned above, Safari allows the user to skip the certificate revocation warning. To do this, the user needs to click on the “Continue” item in the pop-up window.

Based on the original source: blog.cisecurity.org/how-browsers-handle-certificate-revocation
Source: https://habr.com/ru/post/220003/
All Articles