Data encryption in a public cloud - control and quiet sleep of the customer

In the modern world, more and more companies are considering the process of moving to the cloud, and many are stopping from choosing such a path the only question - the question of data security. Moreover, the source of this kind of concern are both business representatives and security departments, which are traditionally suspicious of everything new, especially if this is connected with a decrease in control or an increase in the list of people admitted to the data.
At the same time, the specific tasks that are put in front of the service provider are to ensure the protection of customer data from access by any unauthorized persons, whether employees of the service provider itself, or any third parties whose access to data the customer considers undesirable.
')
As a solution to this problem, encryption of all data located in the cloud is evident, however, how to implement such encryption when traditional solutions are either not supported in a virtual environment (such as bitlocker for boot disks) or not supported at all (such as free truecrypt ), and most importantly - create a huge management overhead to ensure their efficiency.
However, few people know that there are corporate solutions to this problem, which combine a high degree of protection with the convenience of management and use.
As a solution for providing data encryption in the cloud, we propose the use of Trend Micro's SecureCloud product, a world-renowned company whose main business profile is corporate security.
This solution provides controlled encryption of customer data located in public clouds and is compatible with most of the proposed types of public clouds, including VMware vCloud clouds that we use . Also, this solution is compatible with most operating systems that can be used in virtual machines.
The solution is provided directly by TrendMicro on the SaaS model, which allows, on the one hand, preserving the convenience for the customer of a cloud approach to IT services, with a billing model “by subscription”, no need to create and maintain your own servers, and for such a business-critical solution , and ensuring their high availability, on the other hand, leaves the management of encryption keys and data access beyond the control of the service provider.
The solution usage model assumes that virtual machine disks are encrypted using encryption keys that are stored in the SecureCloud system. The SecureCloud system initiates the processes of initial encryption or decryption of protected disks. When attempting to access data, the SecureCloud system is accessed, which, depending on the policies defined by the system, results in either an automatic one-time issuance of an encryption key to decrypt data (for example, to boot the OS), or the issuance of a key only after administrator approval.
For use in the cloudy environment, it is important that the ability to apply automatic key-issuing policies allows, on the one hand, increasing the availability of services by excluding the client’s administrator’s response time from rebooting the machine, for example, in the event of equipment failures and auto-rebooting on other servers, in cases carrying out coordinated planned work related to rebooting machines into the maintenance windows, while preserving the impossibility of obtaining the key by any software other than directly about the protected OS, or outside the specified operating conditions, the inability to access offline copies of the data and the ability to stop the automatic issuance of keys at any time.
In this article we will not go into the study of the encryption mechanisms used, their cryptographic strength, etc. and raise hollywar-s such subjects. In fact, all modern solutions for data encryption meet the needs of typical cloud providers, and the main task of the security system itself is to limit not the targeted use of data, and not to oppose attempts to decrypt state secrets by foreign intelligence services. More information on the details of the technologies used can be explored on the Internet. The main points to which we will pay attention are the mechanisms of management and integration into existing systems and processes.
Architecturally, the solution consists of a management system that is provided as a service with access through the management console and agents installed on the protected virtual machines. The SecureCloud management console is available on the web at console.securecloud.com and looks typical of most web consoles, and the agent is available for download from the trendmicro website.
The primary use of the service is to create user accounts that will manage encryption and access to encrypted data (including access policies and access requests).
SecureCloud can also be connected to the DeepSecurity installation to ensure that the machine is protected against viruses before making a decision on issuing a key:

To start using the system, you need to install an agent on the virtual machine and connect it to the management system. In this case, when using the key specified in the settings of the control system, the virtual machine will be automatically added to Inventory:

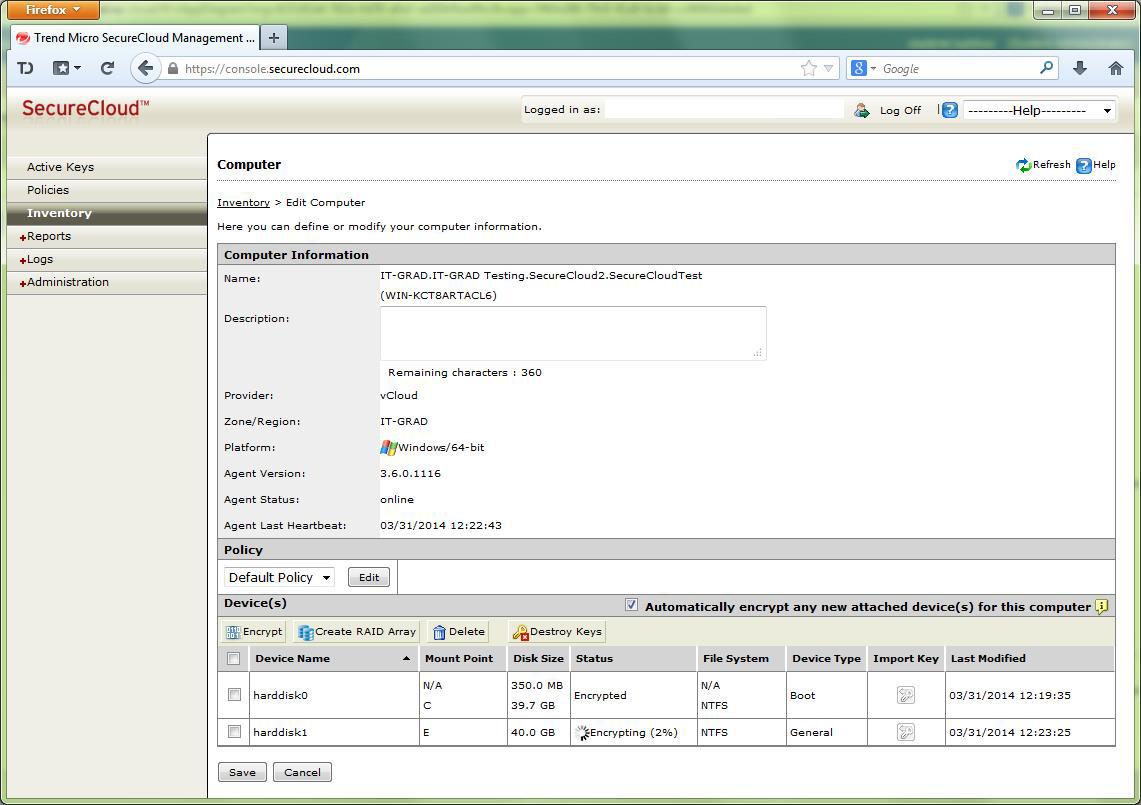
Also, you can initiate the initial data encryption (you can do this later through the management console):

After configuration, the corresponding entry is available through the management console, the progress of encryption is also reflected in the console:
If necessary, the keys can be exported for safekeeping on backup media and imported.
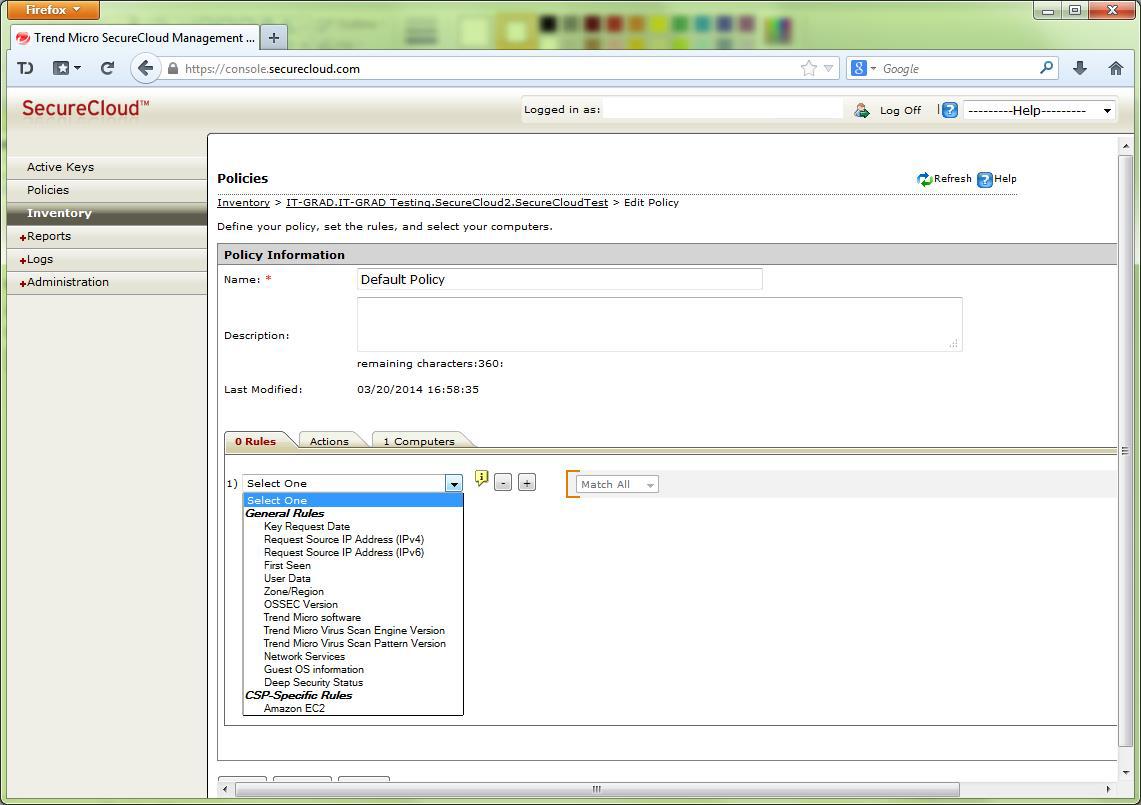
After the process is complete, the data on the disks is completely encrypted, with the key stored only in the SecureCloud system and the operating system OS of the virtual machine. To control the access to the keys, policies are used that allow you to determine the conditions under which automatic or manual issuance or revocation of the encryption key occurs. In addition to general conditions, such as the client’s ip address, the following parameters can be used: TrendMicro anti-virus settings:
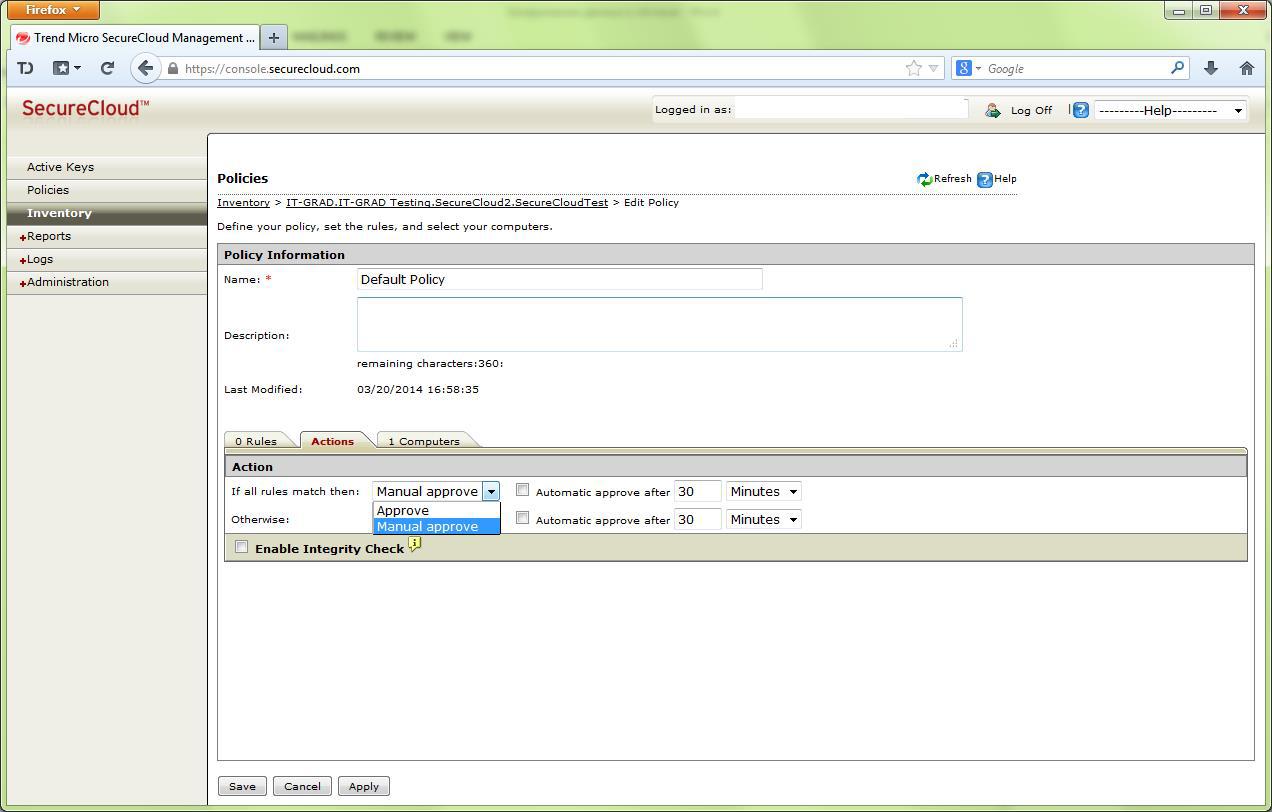
As a possible action on request - manual or automatic approval or refusal to issue a key
Also, it is possible to include a periodic verification of the machine’s compliance with the conditions specified in the policy, using the specified actions in case of a change in conditions.
When booting an encrypted machine, an agent is loaded before the OS, which, by establishing a secure connection to the SecureCloud system, makes a request for a key to access the data:

Further, depending on the established policies, either the key is automatically issued, or a request for a key appears in the SecureCloud system, requiring a manual response:
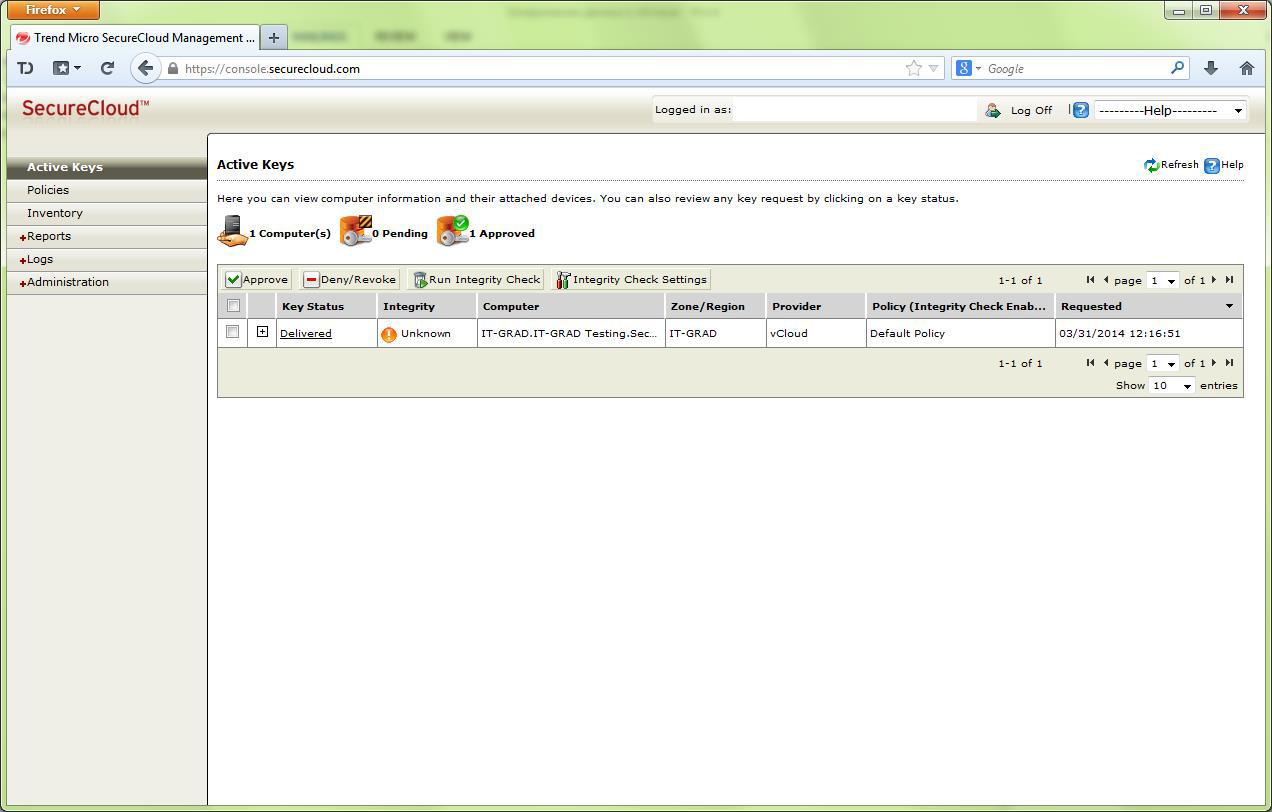
After the key is approved, system loading continues.
To ensure rapid response, the SecureCloud system supports a flexible notification mechanism for events requiring a response:

All information about events and actions performed in the system, either manually or automatically, is available for viewing through the logging system or for creating regular reports.
The simplicity of launching and using and, at the same time, a high level of control and security, in our opinion, make this system preferable for use by companies on the one hand interested in protecting their data from unauthorized access of any kind, and on the other hand interested in convenience and business -effectiveness of using cloud services as a replacement or to expand its own IT infrastructure.
Source: https://habr.com/ru/post/219905/
All Articles