WebSphere and multiple Windows domains
In our office, we have a business application that works with WebSphere version 7.1, users in this application are authorized via Active Directory. To do this, we used the authorization method in WebSphere Separate LDAP registry . In this case, you can specify a domain or another LDAP directory for authorization. With the advent of the second domain, it was necessary to authorize users from both domains. For these purposes, we will change the authorization method to Unified Storage . And below I will describe how to set it up.
In general, in WebSphere, you can use 4 authorization options, they are well described with pictures here .
Authorization methods are configured here.

As already mentioned, we will use the option of authorization Unified Storage for authorization from several domains. We have SDK_GARANT domains, raised in the north of sdkserv , and SDK.LAN on the sdkpdc server. We need a user from each domain to authorize WS. These users do not need any special rights. It is important that their names are different and not repeated in both domains. In the SDK_GARANT domain, there is already such a db2admin user, I created the wasadmin user in the SDK.LAN .
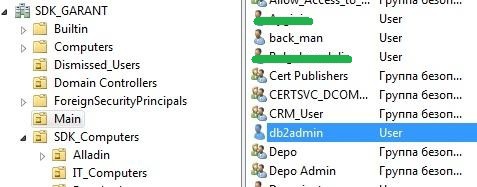
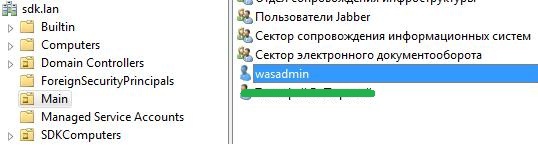
Further we work with the WS console. In the menu shown in the first screenshot, click the Configure button opposite the Unified Vaults . Here is what we will see:
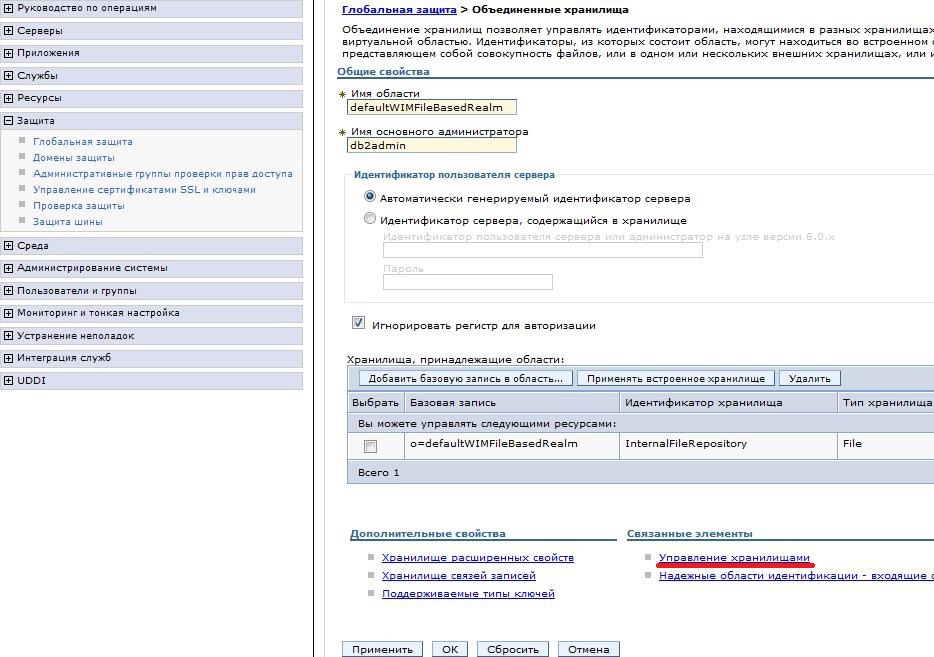
')
Click Storage Manager - Add , fill in the image. The distinguished name of the binding must be specified fully cn = db2admin, ou = Main, dc = sdk_garant . Click OK .
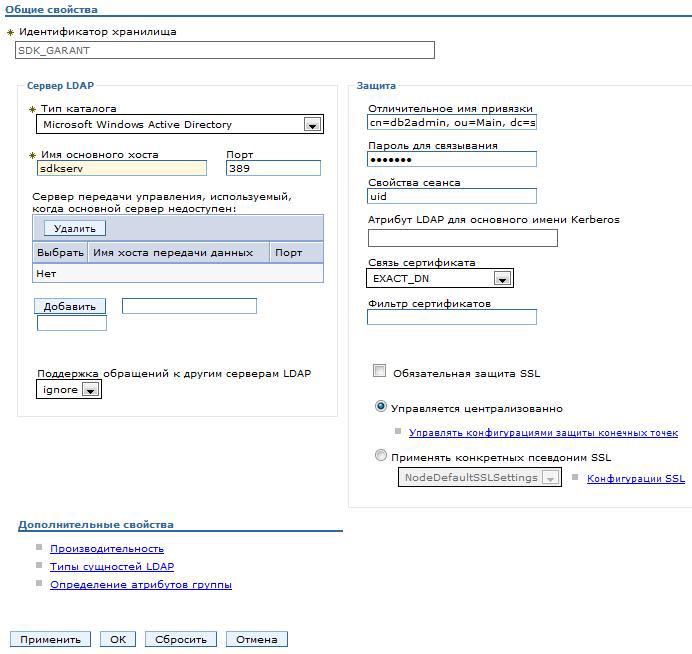
Again, click Add and add the repository to communicate with our second domain. The distinguished name of the binding cn = wasadmin, ou = Main, dc = sdk, dc = lan .

Everything is saved, we return to the setting of the United repositories . And press the button Add base entry to the area.

Here we select the SDK_GARANT repository and specify the user for the connection cn = db2admin, ou = Main, dc = sdk_garant and the distinguished name of the base entry ou = Main, dc = sdk_garant , as the path to the Organization Unit where in AD users lie.
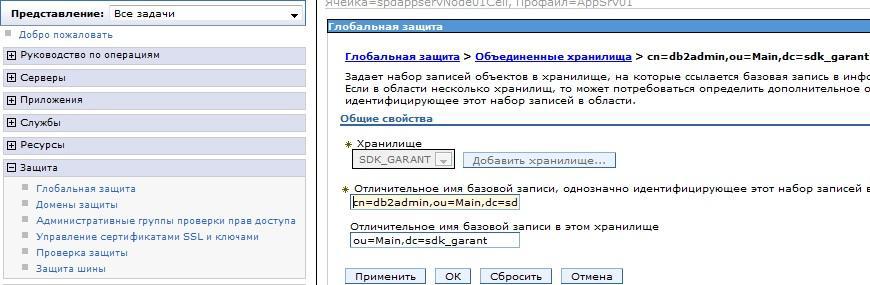
Save and add another base entry cn = wasadmin, ou = Main, dc = sdk, dc = lan and the distinguished name of the base entry ou = Main, dc = sdk, dc = lan

Remove default storage

We drive in the name of the region, the name of the administrator ( db2admin from one domain or wasadmin from another). We save.
Click OK. At the top of the Save page. From the drop-down list, select the United repositories and click Set as current. Apply.
Restart the profile and log in to the console under the domain user. If everything is fine and you are logged into the console, check that the list of users or groups and both domains is hooked. To do this, go to Users and Groups - Administrative user roles - Add . Here, for convenience, put the number of displayed results more and click Search . The list should contain users from both domains.
If something went wrong and the console does not start up. You need to take the * ProfileDir * / Config / cells / * NodeName * / wim / config / wimconfig.xml file from the working profile and replace it with a broken one. Then the login password will be reset to default. For testing, it's not a bad option to add one storage first, rearrange the profile and try to log in. Then remove this storage and add another, also checking.
In general, in WebSphere, you can use 4 authorization options, they are well described with pictures here .
Authorization methods are configured here.

As already mentioned, we will use the option of authorization Unified Storage for authorization from several domains. We have SDK_GARANT domains, raised in the north of sdkserv , and SDK.LAN on the sdkpdc server. We need a user from each domain to authorize WS. These users do not need any special rights. It is important that their names are different and not repeated in both domains. In the SDK_GARANT domain, there is already such a db2admin user, I created the wasadmin user in the SDK.LAN .


Further we work with the WS console. In the menu shown in the first screenshot, click the Configure button opposite the Unified Vaults . Here is what we will see:

')
Click Storage Manager - Add , fill in the image. The distinguished name of the binding must be specified fully cn = db2admin, ou = Main, dc = sdk_garant . Click OK .

Again, click Add and add the repository to communicate with our second domain. The distinguished name of the binding cn = wasadmin, ou = Main, dc = sdk, dc = lan .

Everything is saved, we return to the setting of the United repositories . And press the button Add base entry to the area.

Here we select the SDK_GARANT repository and specify the user for the connection cn = db2admin, ou = Main, dc = sdk_garant and the distinguished name of the base entry ou = Main, dc = sdk_garant , as the path to the Organization Unit where in AD users lie.

Save and add another base entry cn = wasadmin, ou = Main, dc = sdk, dc = lan and the distinguished name of the base entry ou = Main, dc = sdk, dc = lan

Remove default storage

We drive in the name of the region, the name of the administrator ( db2admin from one domain or wasadmin from another). We save.
Click OK. At the top of the Save page. From the drop-down list, select the United repositories and click Set as current. Apply.
Restart the profile and log in to the console under the domain user. If everything is fine and you are logged into the console, check that the list of users or groups and both domains is hooked. To do this, go to Users and Groups - Administrative user roles - Add . Here, for convenience, put the number of displayed results more and click Search . The list should contain users from both domains.
If something went wrong and the console does not start up. You need to take the * ProfileDir * / Config / cells / * NodeName * / wim / config / wimconfig.xml file from the working profile and replace it with a broken one. Then the login password will be reset to default. For testing, it's not a bad option to add one storage first, rearrange the profile and try to log in. Then remove this storage and add another, also checking.
Source: https://habr.com/ru/post/219049/
All Articles