Heartbleed vulnerability: our recommendations to users
The Heartbleed vulnerability , which is present in the heartbeat component of some versions of OpenSSL, has already been written in sufficient detail. Its main feature is that the attacker can read a certain range of memory addresses (64KB in length) in the process on the server that uses this library. Using this vulnerability, attackers by sending a specially crafted request can:
Attackers can compromise HTTPS later (through a known MitM- type attack), having a private SSL / TLS key in their hands (to introduce themselves as a server).
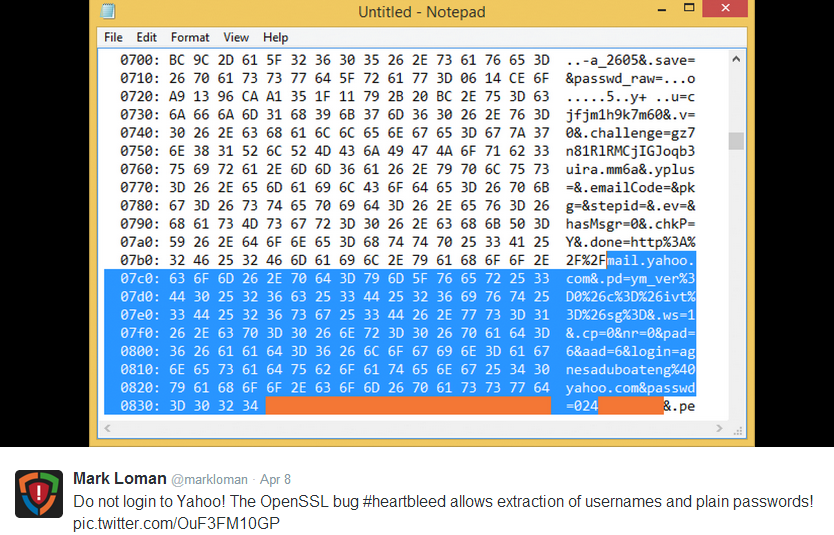
An example of successful exploitation is Yahoo, which has been affected by this vulnerability. Using Heartbleed, it was possible to quickly access user logins and passwords in clear text. [The vulnerability has been fixed and the certificate for HTTPS has been re-released] .
')
We advise users to:
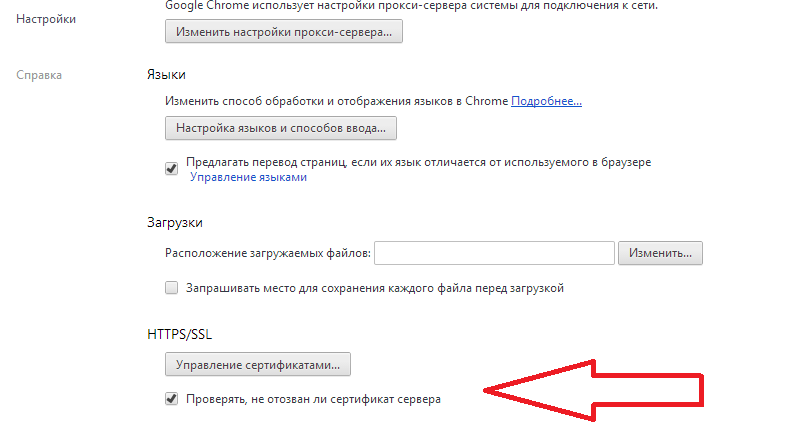
If you are using Google Chrome, activate the option "Check if the server certificate has been revoked" to update the information about the website certificate in the browser. By default, this setting is disabled.
Administrators:
- Steal passwords / logins from your services.
- Get access to a confidential cookie.
- To steal the private SSL / TLS key of the server you are working on via HTTPS (compromise HTTPS).
- Steal any sensitive information that HTTPS protects (read letters, server messages, etc.).
Attackers can compromise HTTPS later (through a known MitM- type attack), having a private SSL / TLS key in their hands (to introduce themselves as a server).
An example of successful exploitation is Yahoo, which has been affected by this vulnerability. Using Heartbleed, it was possible to quickly access user logins and passwords in clear text. [The vulnerability has been fixed and the certificate for HTTPS has been re-released] .
')

We advise users to:
- Contact those. support of Internet services of companies where you have accounts (including mail, online banking) to clarify the situation regarding the potential vulnerability of these services.
- If you received confirmation of the presence of a vulnerability or suspect that the service has been compromised, change your password there.
- Track your online banking operations for any suspicious activity.
If you are using Google Chrome, activate the option "Check if the server certificate has been revoked" to update the information about the website certificate in the browser. By default, this setting is disabled.

Administrators:
- If you are using OpenSSL version 1.0.1 - 1.0.1f, upgrade to the latest version 1.0.1g, which contains a fix for the heartbeat component.
- After you upgrade to the fixed version of OpenSSL, generate new private keys and an SSL / TLS certificate.
- Revoke the old certificate.
- Notify service users to change passwords, as they may have been compromised.
Source: https://habr.com/ru/post/218907/
All Articles