In the footsteps of the Bremen musicians, or "How do we build the information protection of Russia" correctly

Laughter prolongs life
As you know, yesterday we enjoyed either super-sarcastic , or gag, or "the author has a spring aggravation" - on the topic
Let's try to make out - what is in the proposed "not so." As you know - you do not know how to state the material - stick to the manuals.
- What is it?
- Who is it for?
- How to use it?
And only after that you can go to the details.
')
Alas, there was no important preamble in the source code. Sorry - but from whom are we going to defend ourselves? What for? What kind of threats do we need to stop or at least weaken?
The author never reported to us - what kind of green men are those, the struggle with which means the destruction of all IT Co. in the Russian Federation. Here in terms of destruction - yes, items are painted with skill.
Let's try to assess the situation. For laughter - in the text will be abundant material from the perspective of sofa analysts . I deliberately do not select emoticons and other special characters, but traditionally you can laugh after the word “shovel”.

External threats
Let's start with horror stories. We are surrounded by enemies with alpha centauri, evil green men. They led our antipodes and they sow sensible, kind, eternal, even in our sovereign territory.
Organizational threats
At the moment, zashit apologists love to operate with such concepts as “well, potentially yes”. As in the joke , we are potentially millionaires, but in practice there are two prostitutes in the house.
That is, potentially, manufacturers of android / i-axis can embed any scary bookmarks into their systems.
Can? And how. But.
In order to assess the need for protection against such “potential” measures, let us imagine that the bookmarks are there and they worked. Does this disrupt the management of the Ministry of Emergency Situations? Ambulance and MIA work? Wired communication on decade-step PBX? And, all who need a mobile connection - will get from a store of VHF radio?
And then what is the threat, suddenly, instead of the brainchild of Pavel Durov, the product of Zuckerberg will open?
So with the mental ray, we find out that “handing over mobiles on the border” is not required.
But the development of its own "software", recorded directly in the SIM cards and allowing you to stop the encroachments of the antipodes in case of anything, is completely entitled to life. And for the categories of citizens with the first admission it would not hurt to issue them under compulsion.
Deliberate threats and not only
This does not mean that we deny all types of threats - not at all. The scale, however, is not the same, and it is necessary to “take it to the safe” precisely in those places where the presence of uncontrolled communication systems can lead not to leakage of records of evil birds, but to divulging state secrets. That is, in offices, bases and storage areas for military equipment, military units, and so on.
Moreover, a cheap “jammer” will provide an acceptable level of security, and a rusty nail will guarantee the absence of unauthorized photo shoots in secret places.
And antipod spies with shahid belts are caught by the same archaic methods - carrying out operational search activities, implementing agents, and monitoring the media. If you remember, it was exactly this anti-Podspek intelligence activity that was discovered by someone Snowden.
Threats friendly fire
We also touch on interesting side effects. Obviously, if in the State Duma the assistant to the deputy became ill, then (because of the jammers) he cannot take the smartphone out of his pocket and call an ambulance. He will have to crawl to a landline phone.
So you should always remember - the introduction of protection not only reduces the risks against which is directed, but always creates new ones. And they also need to be assessed and minimized. Fans of “forbid” often try to circumvent this dashing cavalry maneuver, because in many cases super-security systems do not only add unacceptable risks, but also cost more than the potential damage from leaks or even deliberately destructive actions.
Therefore, many who actually will be against the NSA wiretapping system. Just because although it does not carry a seemingly new threat, such a risk of leakage in the NSA itself appears! Plus abuse and corruption.
But blocking websites with a list is a destructive measure that complicates life for conscientious users, and gives a lot of room for abuse, and carries much more risks.
Social threats
In the century of webdvanol (C), so beloved by all social networks are new threats. For example - unfaithful spouses publish in them proofs of their marital infidelity. Themselves, voluntarily.
In the same way, protection schemes for nuclear power plants (a real case), maps, photos of the latest technology, and so on, fall into the social network. And what is interesting, social network ban is already unrealistic. And it is all the more unrealistic to teach users the basics of social hygiene.
Therefore, only automated monitoring (see Kribrum and analogues) and targeted work.
Instead, lovers of delusional methods of protection from green men offer to go out to greedy students only with a passport scan. I wonder how it will protect from "I climbed into the hole and sfotkal Topol-M"? Young people of post pubertal age will not guess to attach a scan of a neighbor on the desk?
But “85 rubles kremlebotev” is useful for the purpose of disavowing both the source and materials. If there is a pack of materials on the “poplar” picture, “yes, this is a pipe driven by a tractor to the substation, I drove past the house an hour ago!” - then the value of the photo sharply decreases. And also it can be done automatically.

Technical threats
Here I would like to remind such simple things as DDoS, spam, carding and other tricks of black hats. As well as targeted attacks on certain points of infrastructure and potential carriers of monetized secrets.
Fortunately, almost none (except for spam and database theft with credit cards) does not allow for a purely economic payback of a serious attack. Which in turn prevents a fully-fledged market for the division of labor among cybercrime. Agents - and here they are, malware, in full view.
All you need is to bring your agents to positions closer to the immediate receipt of money.
And of course, the usual work on the interception of botnets with the involvement of civilian specialists.
But attempts to "use only domestic" on the contrary - reduce security. What should the same bankers do without SSL / TLS? Without client certificates and secret code generators? Without all these applets and client banks? Obviously, yes queues and blurred round seals. But forgive me - in the age of the scanner with photoshop from what can a round seal protect? Advising in the 1990s, she did not protect.

Mental threats
Yes, yes, these are psychological tricks, Internet memes, “Albany” and other techniques for influencing minds.
What does this have to do with security? Yes, no.
Except for the fact that it is from this “threat” that all kinds of free Internet leagues and deputy Mizulina are actively “protected”.
Let me remind you again - there are no magic defenses without new risks.
So, protection from pedophiles (C) in the “decaying west” is better developed than in the Russian Federation, the same Google suggests including content filtering for both search and smartphones. The problem is common - approaches and solutions should also be common. But on one side is the development of semantic analysis, photo recognition, and the integration of all this into parental control, and on the other, global blacklists.
From the point of view of a purely technical, blacklists for mail do not in any way cancel content filtering, but only complement it as an additional point to the overall assessment of text and headings. Single blacklists have not worked for a very long time, and there are no prerequisites that the situation will be better for sites.

Internal threats
Having slightly dealt with external threats, let us turn to the renegades and the hires of the antipodes in our own camp.
It is these evil insiders who can easily bring the terrible thing on a flash drive, take a video recorder, take a picture with a smartphone. And post terrible secrets in the true tru social network "greedy-graders" or even in the "Learn". What will inflict agromenny damage.
If no joke, the danger is different - after all, you can not only make a picture of Anna Semenovich on a flash drive or smartphone, but also take out a secret drawing, instruction, or even an order with the stamp "top secret". And unlike antipod's spies, which can be seen from afar ( “Grandma, how did you determine that I am an American spy? Why, my dear, we do not have blacks in the village!” ) They are clothed with service access.
And here it is necessary to use a much larger arsenal - from test purchases to DLP and the correct regulations of the Security Council.

Organizational threats
Something gave out Stierlitz - whether budennovka with a red star, or a parachute ...
In fact, we are dealing with the most dangerous class of vulnerabilities - holes in the perimeter, incorrectly assessed perimeter, incorrectly assessed risks, and so on. It is this class of mistakes that creates the very fertile environment for all other classes.
It is important to remember that security holes can be either from a devil-may-care attitude to security (“everyone has access to the network globe”, “only cowards do backups” and so on) and from excessive diligence (“mail doesn’t happen with attachments over 100 kilobytes ", As a result, all employees send confidential letters via mail).
At the moment, the only correct method of building protection systems is the principle of damage minimization.
How much will a dead antipod presidents loss if our specialist Vasya takes the customer base to a competitor? And how many - the implementation of a security policy, in which the list of clients lies in the database and is visible only to "their" managers? This difference in money is the only correct measure of the introduction of protection or non-introduction of protection. In the plus come out?
Unfortunately, the current situation on the defense market is largely (fortunately not always) built on aggressive marketing using mental tricks. If you don’t install an antivirus, your money will be stolen! How? I have no money in the computer? Believe us and fear.
And as an “apotheosis apotheosis”, we get the typical situation of “watchman syndrome”, where ordinary employees have to bring work on flash drives to their homes, or even come with their laptop with iota to perform their direct duties.
But on the authorities, who took into operation a set of jokes and marasmus instead of competent regulations, these restrictions do not apply to the word at all. Thus, subordinates get the esoteric knowledge of “boss password is 111” and much more access than they need. That allows them to put various proxies and other tunnels on the server or director’s computer. And disable the antivirus so as not to interfere. The result is sad - that there is protection, that it does not exist, everything is one.
So, only a competent understanding of all risks and hazards, only the design of the system without exceptions will allow to achieve the minimum necessary level of security. Minimally! For there is no need to spend mountains of money on something that can not be protected.

Social threats
It would seem that there are threats similar to the paragraph above? Not really.
Here comes to the fore social engineering. As part of the procedure for verifying password strength - let your current phone! Many report, even knowing that it is impossible to do so. Well, just because how did a stranger recognize an internal telephone? This is the security people testing us! And they can.
And they really test it ... sometimes.
Here you can also remember the password written on the monitor, stickers in the table with secret information and so on.
Only systematic training and testing of personnel saves this, but it is advisable to test it so that nobody guesses about it. And it turns out not quite what they tested.
Strangely enough - but this item is often ignored simply because of its serious cost. Personnel training takes him away from work, requires hiring external trainers, close contact with the vendor of your DLP and constant adherence to the rules.
As one big boss explained to me, when we buy an antivirus, a monitoring system, and so on, we put this on a balance, this is our asset. And spending on training is a write-off in a liability, no one likes and no one likes.
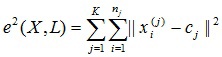
Technical threats
We briefly indicate their large range, from a voice recorder or camera in a smartphone to professional equipment.
Therefore, if you want to protect yourself, if not from all, then from the majority, then it is easier to rent an office in a basement without windows, in an industrial zone, and the communication lines are tightly encrypted. And also hung with jammers of both cellular communication and sound. In general, clean the room from any sources of radio emission.
At the entrance to plant the colonel of the KGB or the FSB, give him a rusty nail, and oblige everyone to hand in smartphones and laptops at the entrance. And if you need a smartphone for work - punch the lens with a nail.
Computers regularly pass for examination. Software to use only marginal or very outdated. List update centrally. Permissions cut back to a minimum.
Do not forget to have an autonomous water and sewage system, as well as a boiler room.
Some kind of strange picture turns out, right? Whether Arzamas-16, or something else. And in such places and transfer all the most important developments.

Conclusion
And here is a shovel!
Of course, in such a long sheet, we were only able to list some threats, examine typical mistakes, and in some places even outline some steps to improve the situation. However, as it turns out, the solutions for each and every threat are different , localized in time and space . The need for some kind of external super-solution is not visible.
Probably I missed something important in a hurry, so please correct and prompt, I will be grateful for any constructive criticism.
UPD ( bypasser ): In general, the formulation of the task of the “information security of Russia” type looks strange. For the cut it is, but in practice - the grotesque.
Information security should be at the individual enterprises and / or specialists. This makes it easier to identify possible threats and rational ways to counter.
By the way, “do nothing” - in some cases, a completely rational way of reacting, for example, to threats with extremely low probability of realization or with low financial losses. As in the store, starting from a certain moment, the “nesuns” cause damage less than we begin to spend on “security”.
Source: https://habr.com/ru/post/218685/
All Articles