Current trends in the development of DDoS attacks and protection against them using DefensePro Radware

At the present time, when political and economic tensions in countries are growing, the information war has long been going on at full speed on the Internet and DDoS attacks are well-known to one of the first places.
First of all, they are exposed to state and news web-resources, which to some extent lighten the events not only in the above-mentioned countries, but also in the world as a whole.
')
Let's take a closer look at which DDoS attacks are now becoming the most popular and their development trends in the coming years. Under habrakat my thoughts about attacks and the review of the solution of protection from Radware
Increasing the number of vectors in DDoS attacks
The first thing that distinguishes DDoS attacks of 2013/2014 from previous ones is that several vulnerability vectors are used. Since only one vector is enough to hit a target and inflict the resulting damage, this is why the probability of an attack’s success increases if you use multiple vectors in one attack. In addition, this tactic confuses the IT staff of the attacked organization.
Considering DDoS attacks as a whole, in 2014 attacks targeting web resources will continue to prevail as the most high-speed vector. Since 2013, there has been a clear increase in DDoS attacks on applications as a result of the presence of anti-network DDoS attacks deployed in organizations in recent years, which is shown in Figure 1. Moreover, network attacks are much easier to resist, and they never belonged to categories of hard reflected attacks.
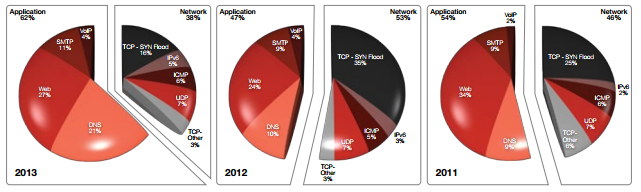
Fig.1. Percentage distribution of vectors of DDoS attacks from 2011 to 2013
As mentioned above, many means of repelling attacks have been fairly developed and organizations can withstand for quite a long time DDoS attacks directed at the network and applications without compromising the IT infrastructure. But attackers can use a multitude of attack vectors to search for those that are not provided for by repelling DDoS attacks deployed in an organization. More than half of the cases are DDoS attacks with five or more vectors, as indicated in Figure 2.
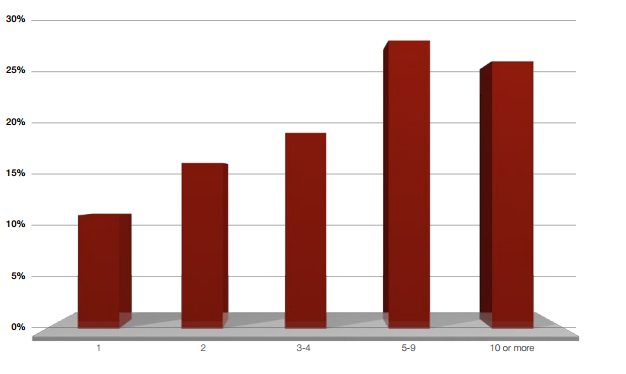
Fig.2. Number of attack vectors used in a single DoS / DDoS attack campaign
Very often, attackers will not use the entire arsenal at once, allowing the victim to process attack vectors sequentially. When one attack vector is blocked, the attacker will launch the next attacker. During a massive attack, an organization can block four or five attacking vectors, but there will be one attack vector that cannot be reflected and inflict final damage.
The goals of modern DDoS attacks
In most cases, the result of a DDoS attack is a web server that is not working or is slow responding. But in fact, DDoS attacks are aimed not only at the web server. The figure below shows the main objectives of the DDoS attack - this is the Internet channel, as well as the firewall. The following figure 3 shows all network components that are subject to DDoS attacks.
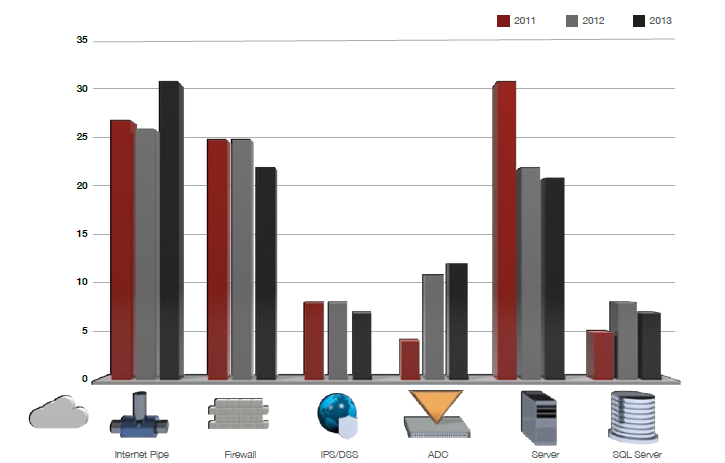
Fig.3. Attacked Network Components
The periods between attacks are significantly reduced.
It is no secret to anyone that the attacker and information security experts are playing a permanent cat-and-mouse game. This is an endless ring: the attackers are developing new attacks, security experts are developing countermeasures, and the attackers, in turn, invent new methods to bypass the defense systems.
But in 2013-2014, the cycles of inventing new methods of circumventing protection systems were significantly reduced. One of the main vectors that led to this is an HTTP flood attack. They begin when an attacker sends a large number of HTTP GET / POST requests, depleting server resources.
SSL attacks continue to threaten organizations
Although HTTP attacks remain the most common, SSL-encrypted attacks are still dangerous because they are difficult to resist.
Fraud, hacker activity, as well as a long list of privacy requirements led to organizations using the HTTPS protocol and encrypted communications by default. According to a number of market studies, more than 90% of enterprises use HTTPS for any publicly accessible web interaction. Usually, HTTPS messages are decrypted at a very late stage within the organization’s network. This is shown in Figure 4, where the decryption occurs on the load balancer, deep within the organization's network.

Fig.4. Bypassing organization security systems using SSL-encrypted DDoS attacks
Attackers use this encrypted message feature as a technique to bypass security solutions (anti-DoS / DDoS, firewall and IPS / IDS), which ultimately remain blind to the attack. At this point, you can suggest moving the SSL-termination functionality to the perimeter of the organization’s network. However, such a decision may lead to a distortion of network segmentation, since the concept of network segmentation is crucial to meeting the requirements of various security regulations, such as PCI-DSS. Also, network segments that deal with confidential data may be subject to severe restrictions and auditing.
Another interesting feature based on SSL DoS / DDoS attacks is the asymmetric nature of SSL encryption, which is that the decryption of a message takes almost ten times more resources than its encryption.
Using this asymmetric feature, attackers can create a very destructive attack with relatively low resources. Using the circumvention methods described above, attackers, using special tools, manage to deliver malicious messages deep inside the network, where servers and various modules are more vulnerable to high traffic to observe unacceptable delays or a complete shutdown. SSL encrypted attacks are a new trend that will grow over the years and according to forecasts, in 2017 more than half of DDoS attacks will be SSL encrypted.
You can continue to continue for a long time about the trends of attackers in the field of DDoS-attacks, which will greatly increase the article, but let's look at the solutions that are in their power to resist.
Overview of DefencePro Radware as a way to protect against modern DDoS attacks
DefencePro combines classic IPS and automatic protection against DDoS attacks in one solution, working without operator intervention to repel an attack. Distinctive features are high performance (the attack can reach 25,000,000 packets per second, and automatically repels in 18 seconds!) And no damage to the work of legitimate users during the attack. In devices of the entire DefencePro line, hardware acceleration of network traffic occurs due to specialized ASIC and FPGA processors.
In the model range there are devices without built-in IPS, as well as with built-in IPS, which for the most part relies on a high-performance context processor for hardware acceleration of signature analysis of network packets.
The processing of network traffic is carried out in stages using various protection mechanisms. In this case, the total delay time of the network packet for all DefencePro lines does not exceed 60 microseconds.
The built-in protection mechanisms of the Radware DefensePro system are as follows:
• Behavioral DDoS Protection
• TCP SYN Flood Protection
• Connection Limit
• HTTP Mitigator
• Behavioral Server-Cracking Protection
• Bandwidth Management
• Signature Protection
• Stateful Inspection
• Anti-Scanning Engine Protection
• Stateful Firewall (ACL)
Also available actions:
• Drop packet
• reset (source, destination, both)
• suspend (source, src port, destination, port or any combination)
• Challenge-Response for HTTP and DNS attacks
The advantages of DefencePro are, first of all, the possibility of a licensed increase in performance as needed without changing equipment, stopping the service without any reconfiguration of the device. DefencePro also comes with a level of technical support, which includes the help of the ERT (Emergency Response Team) team from Radware. This team is a group of specialists who, in the case of large DDoS attacks, connect to the device and perform real-time control to repel the attack.
Another important advantage of Radware DefensePro is the redirection service for all incoming traffic during a DDoS attack, which exceeds the bandwidth of the company's Internet channel to the Radware cloud, after which the traffic that has already been cleared returns to the organization. This service has the name Defense Pipe, and its work is clearly displayed in Figure 5.
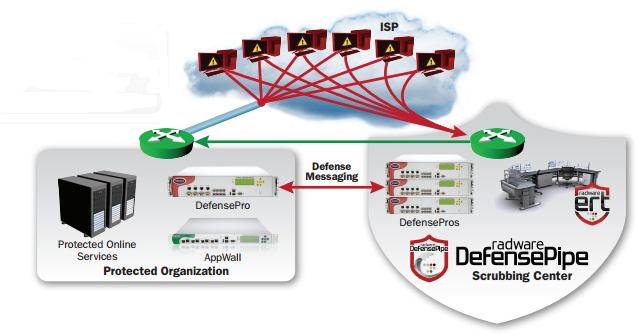
Figure 6. Redirecting all traffic in a DDoS attack exceeding the bandwidth of the Internet channel to the Radware cloud for cleaning
The Radware DefensePro device line consists of the following series:
• x420

• x412

• x16

• x06

In turn, each series of devices includes several models, which are shown in Figure 6.

Fig.6. Radware DefensePro devices line
In summary, DDoS attacks have been and will be in the coming years the most popular tool for inflicting economic damage from the downtime of online services, as well as for reducing the reputation of political formations by refusing to maintain official websites. These attacks received a special development increment with increasing political tensions in the world, which makes them more sophisticated and unpredictable. All the above factors make organizations, sooner or later, consider the acquisition of protection systems against such attacks. In order not to suffer financial losses and not to lose political reputation in the modern highly competitive world.
Contact info
For all questions radware@muk.ua
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
Source: https://habr.com/ru/post/217695/
All Articles