Overview of Multifactor Authentication in the Microsoft Azure Cloud
The Microsoft (then Windows) security system of Azure has recently introduced new functionality — multifactor authentication. WFP, of course, is needed in order to build an additional protection contour around the account or cloud services of both Microsoft and third-party solutions or applications and services that use Microsoft Azure Active Directory as an authentication system. Local infrastructure can also be protected — for example, our Multifactor Authentication Server can be integrated into a RADIUS loop. Interesting? Under the cut - a description of the solution to the situation when we need to protect access to an Azure subscription not only with a login and password, and a little bit about where to go for more complex things.
Multifactor Authentication Windows Azure provides an additional layer of authentication in addition to user credentials. At the same time, multifactor authentication can be used to protect access to both on-premise and cloud applications. Possible options for multifactor authentication include:
• mobile applications,
• phone calls
• text messages,
Users can choose what is convenient for them, both independently and forcibly - the administrator can regulate it. In the context of securing local applications, multifactor authentication can be used to protect remote access VPNs, RADIUS, and Web applications using a special SDK. If the cloud application uses Active Directory Federation Services, then the developer can set up synchronization with Windows Server Active Directory or another LDAP directory. As for other Microsoft services, multifactor authentication is useful for protecting access to Microsoft Azure, Microsoft Online Services, Office 365, and Dynamics CRM Online.
')
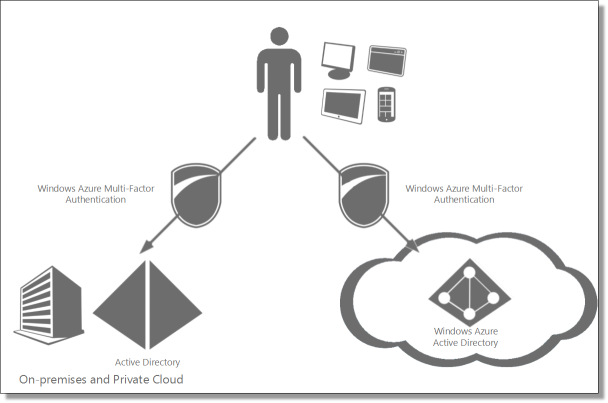
Let's see how to prepare multifactor authentication in Windows Azure.
What you need to repeat the demo:
• Windows Azure subscription - enough trial: free trial
• Tenant Windows Azure Active Directory
First, create an MFA provider: on the Active Directory tab of the Azure Management Portal, go to the SUPPLIER'S MULTI-FACTOR AUTHENTICATION VERIFICATION page. Click Create, and enter the data - the name of the supplier (logical), "on the enabled user" and select the directory to which you want to bind the supplier. Now we will create a new user on the Users page - this is necessary in order to activate the MFA, since the MFA does not work for the Microsoft Account (organizational only).
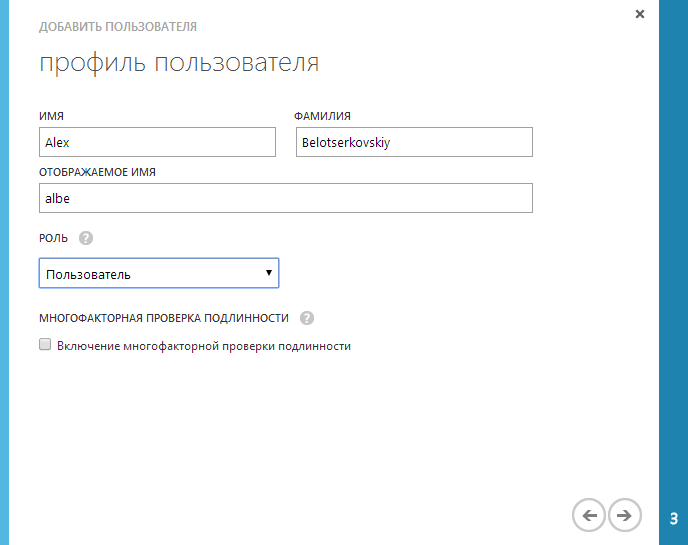
Adding a user is a three-step process: type of user account ...

... His roles in the organization and tenant (set the role of a global administrator and tick the option to enable multifactor authentication) ...
... and setting a temporary password.

Create a new password and complete the configuration of the new user. Under this user, we will log in later. After creating a user, go to his page and enter a mobile phone - note that the country code is also indicated in the drop-down menu - you do not need to write it in the field.
Excellent - the infrastructure tasks for our simple scenario are over. Now we will try to exit the portal and log in again, but under a new user. A new option will appear - Set it up now, which means that the tenant administrator has forced the use of MFA for our user.
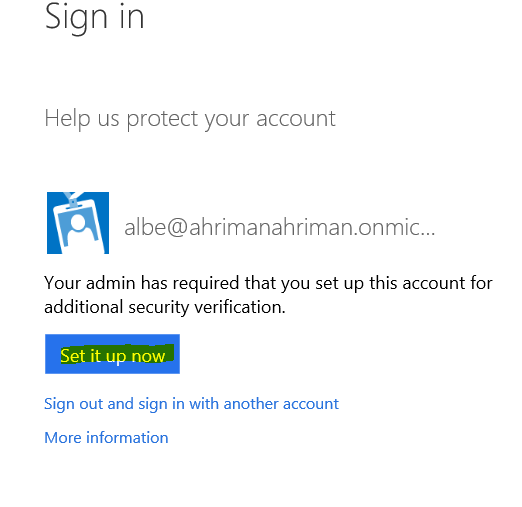
On the MFA configuration page for our user there are all the necessary fields - the choice of authentication type, phone number, and the choice between SMS and call.
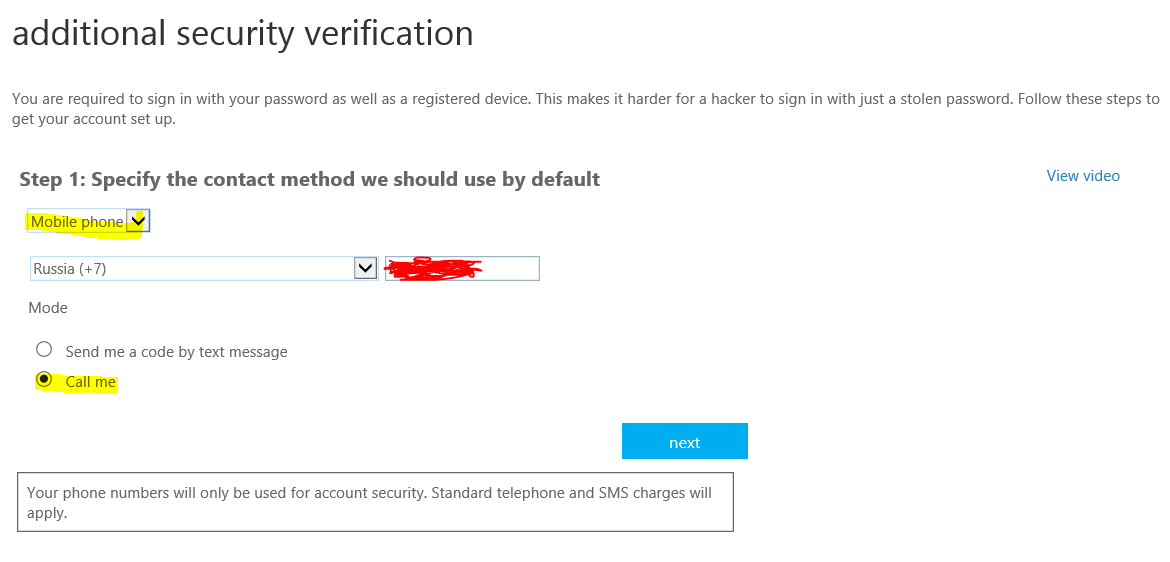
On the next page we will be prompted to verify the selected type of authentication. In our case, a pleasant female voice on the phone will tell you what to click in order to go through the additional security loop. Try logging into your Azure account with a new account - the experience is the same.
Now let's look at more complex scenarios - using MFA for the catalog and On-Premise.
In order to use MFA On-Premise — for example, integrate with IIS, RADIUS, Windows auth, or even LDAP — we need to download and install a Multi-Factor Authentication Server. It is loaded, if you click on the MFA provider created earlier, go to manage this provider and click Server || Loading.
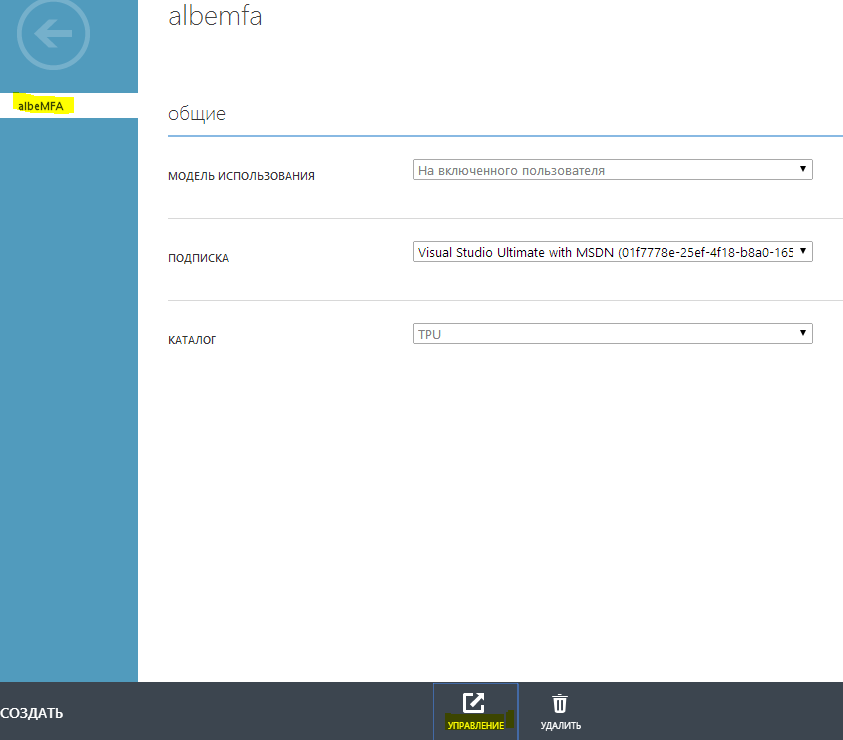
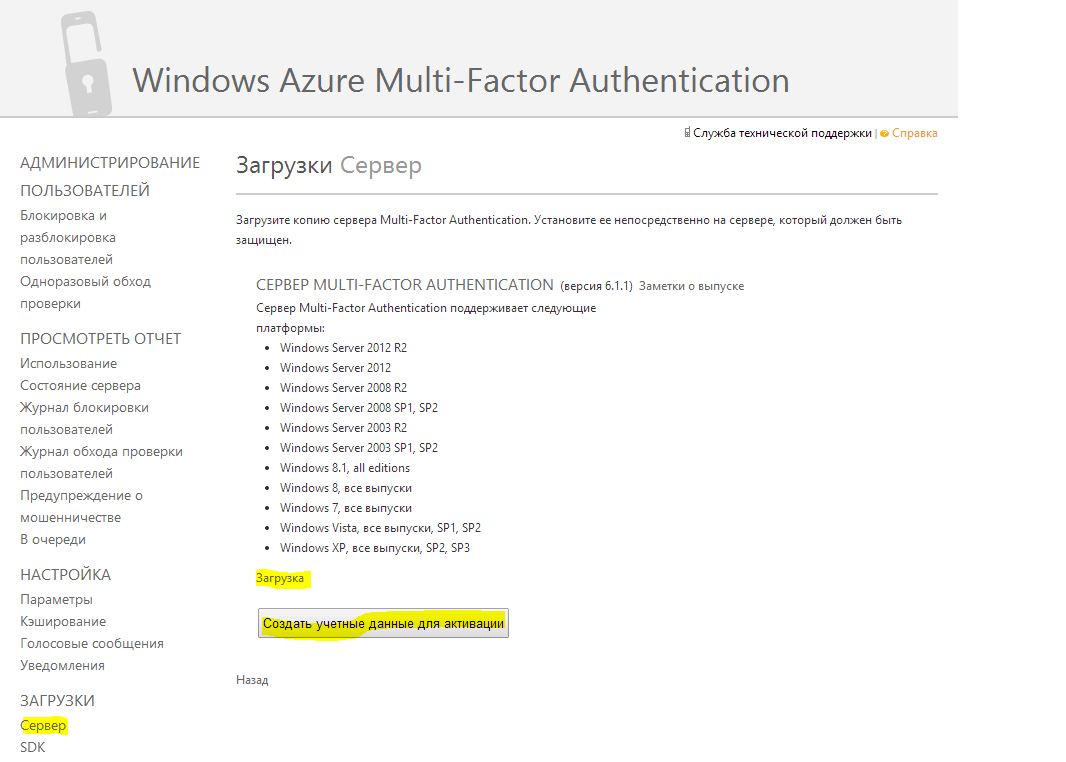
While the server is loading, we also click “Create credentials for activation” - they will be needed to activate the server after installation.
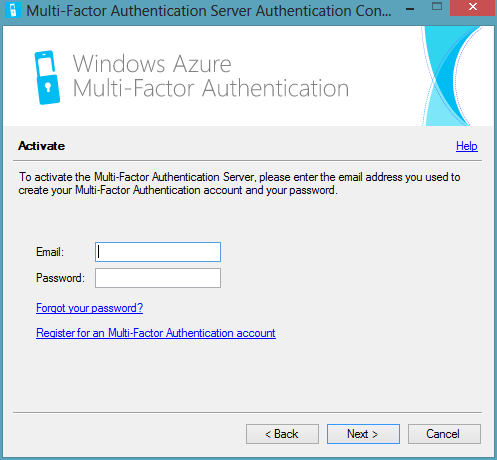
Install and activate the server. Please note - the password is valid 10 minutes after its creation, so do not delay the activation process.
In the process of setting up the server, you will see many interesting options - for example, on the Applications tab you can configure which services and applications are protected by the MFA.

The MFA server is configured on the AD directory by default, but to reconfigure or add another directory is not a problem at all - just select Synchronization on the Directory Integration tab and click ADD, then configure synchronization and its frequency.

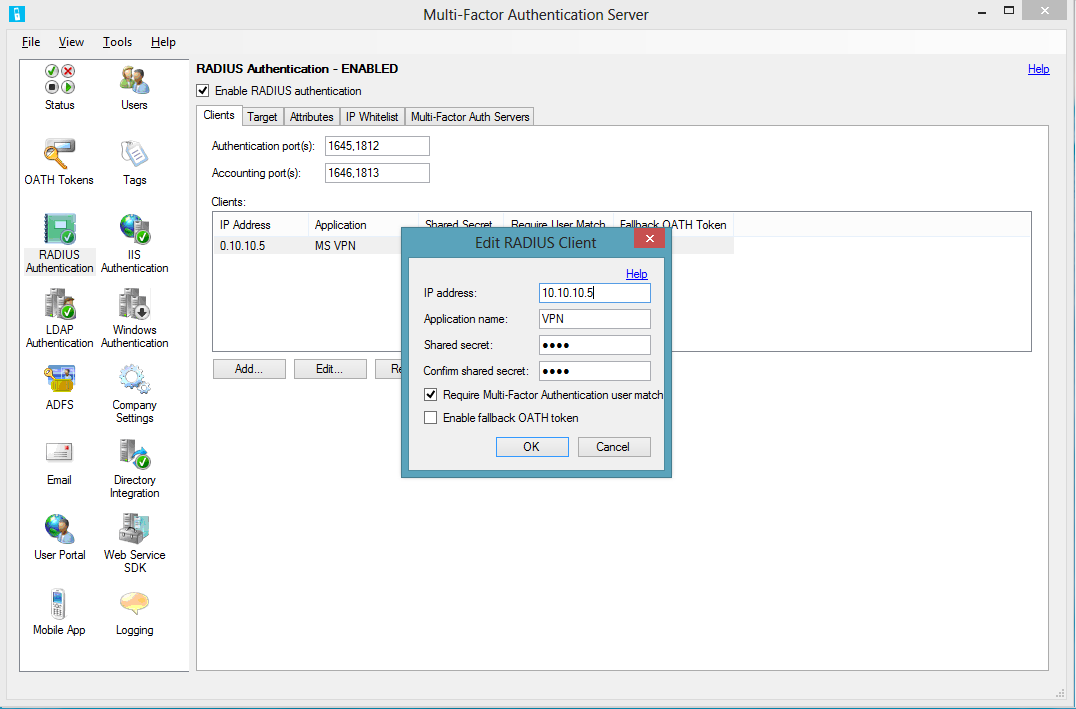
Another typical corporate utility is the integration of MFA with RADIUS to protect VPN and other features like Microsoft Unified Access Gateway, TMG, or even RDG. Configure integration on the RADIUS Authentication tab.
We looked at the Windows Azure Active Directory feature - Multi-Factor Authentication. The process of setting it up is much simpler compared to the period when it just came out, and now there are no special problems in configuring MFA both in the simplest scenarios such as providing an additional security layer for logging in to the Windows Azure subscription, and in the most complex corporate - integration with RADIUS. About other scenarios - later.
Multifactor Authentication Windows Azure provides an additional layer of authentication in addition to user credentials. At the same time, multifactor authentication can be used to protect access to both on-premise and cloud applications. Possible options for multifactor authentication include:
• mobile applications,
• phone calls
• text messages,
Users can choose what is convenient for them, both independently and forcibly - the administrator can regulate it. In the context of securing local applications, multifactor authentication can be used to protect remote access VPNs, RADIUS, and Web applications using a special SDK. If the cloud application uses Active Directory Federation Services, then the developer can set up synchronization with Windows Server Active Directory or another LDAP directory. As for other Microsoft services, multifactor authentication is useful for protecting access to Microsoft Azure, Microsoft Online Services, Office 365, and Dynamics CRM Online.
')

Let's see how to prepare multifactor authentication in Windows Azure.
What you need to repeat the demo:
• Windows Azure subscription - enough trial: free trial
• Tenant Windows Azure Active Directory
First, create an MFA provider: on the Active Directory tab of the Azure Management Portal, go to the SUPPLIER'S MULTI-FACTOR AUTHENTICATION VERIFICATION page. Click Create, and enter the data - the name of the supplier (logical), "on the enabled user" and select the directory to which you want to bind the supplier. Now we will create a new user on the Users page - this is necessary in order to activate the MFA, since the MFA does not work for the Microsoft Account (organizational only).

Adding a user is a three-step process: type of user account ...

... His roles in the organization and tenant (set the role of a global administrator and tick the option to enable multifactor authentication) ...

... and setting a temporary password.

Create a new password and complete the configuration of the new user. Under this user, we will log in later. After creating a user, go to his page and enter a mobile phone - note that the country code is also indicated in the drop-down menu - you do not need to write it in the field.
Excellent - the infrastructure tasks for our simple scenario are over. Now we will try to exit the portal and log in again, but under a new user. A new option will appear - Set it up now, which means that the tenant administrator has forced the use of MFA for our user.

On the MFA configuration page for our user there are all the necessary fields - the choice of authentication type, phone number, and the choice between SMS and call.

On the next page we will be prompted to verify the selected type of authentication. In our case, a pleasant female voice on the phone will tell you what to click in order to go through the additional security loop. Try logging into your Azure account with a new account - the experience is the same.
Now let's look at more complex scenarios - using MFA for the catalog and On-Premise.
In order to use MFA On-Premise — for example, integrate with IIS, RADIUS, Windows auth, or even LDAP — we need to download and install a Multi-Factor Authentication Server. It is loaded, if you click on the MFA provider created earlier, go to manage this provider and click Server || Loading.


While the server is loading, we also click “Create credentials for activation” - they will be needed to activate the server after installation.
Install and activate the server. Please note - the password is valid 10 minutes after its creation, so do not delay the activation process.

In the process of setting up the server, you will see many interesting options - for example, on the Applications tab you can configure which services and applications are protected by the MFA.

The MFA server is configured on the AD directory by default, but to reconfigure or add another directory is not a problem at all - just select Synchronization on the Directory Integration tab and click ADD, then configure synchronization and its frequency.

Another typical corporate utility is the integration of MFA with RADIUS to protect VPN and other features like Microsoft Unified Access Gateway, TMG, or even RDG. Configure integration on the RADIUS Authentication tab.

Summary
We looked at the Windows Azure Active Directory feature - Multi-Factor Authentication. The process of setting it up is much simpler compared to the period when it just came out, and now there are no special problems in configuring MFA both in the simplest scenarios such as providing an additional security layer for logging in to the Windows Azure subscription, and in the most complex corporate - integration with RADIUS. About other scenarios - later.
Source: https://habr.com/ru/post/217685/
All Articles