How and how to protect your data on PCs and drives today?
At present, it is almost impossible to guarantee the safety of corporate or user information on various mail services, personal computers and cloud storages. Mail can be hacked, information from your computer or from a computer of colleagues can be copied by employees of the company and used for their own purposes. Is there any way to protect information? 100% guarantee of data protection today does not give any company, make a good step towards saving their data, of course, you can. Typically used to protect data encryption.
Encryption is symmetric and asymmetric, the difference is only in the number of keys used for encryption and decryption. Symmetric encryption uses one key to encode and decode information. The laws of the Russian Federation without licensing their activities allow the use of a symmetric key long
no more than 56 bits. For asymmetric encryption, two keys are used: one key for encryption (public) and one for decoding
(closed). For asymmetric encryption, the laws of the Russian Federation, depending on the algorithms, allow a maximum key length of 256 bits.
Consider some devices to protect information on removable
drives:
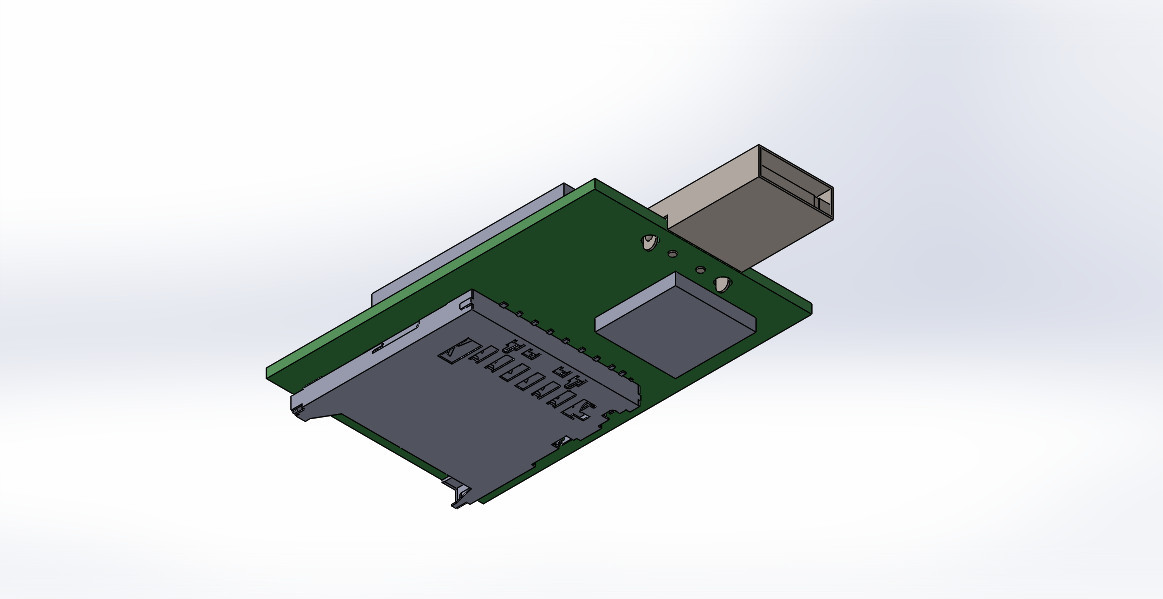
Klyuch_P1 is made with three connectors: USB - socket and plug, as well as a connector for SD cards.

The initial functions of the device (further, the software is expanded, see below for additional functionality):
')
More description of the functions of the device will be later in this article. Encryption keys are stored in the flash memory of the processor of the device in question.
Klyuch_P1 can work with an unlimited number of drives and on an unlimited number of personal computers, there is no binding to a specific PC.
Block diagram of the entire system:
Description of structure elements:
Let us consider in more detail the main functions of the device.
To get started with the device you need:
The PIN input window looks like this (draft version):
In addition to the individual version, the corporate version will also be available:
Company employees download the Key_P1 Manager program from a corporate server or from removable media and install it on their OS. Then download the keys generated by the security service or IT-service company. Further, by analogy with the individual version, the Key_P1 and the drive are initialized. Unlike the custom version, in a corporate multi-department manager can choose for which department to encrypt files. The list of departments is formed by authorized employees of the company.

Inside the department, employees can exchange encrypted information by encoding files using Key_P1 Manager and Key_P1. The enterprise security service has the ability to create different demarcations of rights across departments (for example, the “Programmers” department will be able to encrypt files for the “Accounting” department). In addition, an enterprise can put in the device an algorithm for generating one-time passwords for authentication on servers, computers, etc., in order to increase security and ensure protection of commercial and other types of secrets.
As an additional functionality of the device:
From this list, the most interesting is the storage of usernames and passwords from various resources. The only question is how convenient it is to do it. Perform automatic substitution of the login and password pairs or enable the user, after entering the PIN code, to view the login and password in clear text, as allowed by Google Chrome browser.
Now we turn to the consideration of the hardware level of the device.
The main functions of the device are encryption and protection against unauthorized operation of drives.
Consider ways to encrypt data device:
Also, the function of notifying the user about the change of the file size will be available, in case of replacing the existing file on the drive with a new one with the same name. The device has a “read only” mode to protect against unauthorized copying of information to the drive when working on a PC infected with viruses.
To cut off spyware Klyuch_P1 filters the service commands sent to the drives, which protects the drive from being infected with a hardware virus, and the Klyuch_P1 device analyzes the descriptor table sent by the drive and, based on this information, drives that try to introduce themselves to the PC system as a combined device (for example, a keyboard and a drive) or any device other than a drive.
Consider the implementation of the device at the circuit level.
The device is based on the Russian multicellular processor P1. To interact with the USB host interface, the stm32f205 processor is introduced into the circuit. The multicellular processor is clocked by the stm32f205 processor, the firmware is loaded via the spi interface. The P1 processor assumes all the basic functions of encrypting and hashing information. One of the interesting features of most encryption algorithms is their good parallelization. Due to this fact, it is rational to use a processor with hardware parallelizing operations.

As a result of the device upgrade, the following scheme is assumed:
Interaction with the USB host can be provided by the FTDI chip.
The device has connectors that allow you to work with USB drives and microSD, SD cards.
Advantages:
Disadvantages: non-specialized building, lack of protection against opening (Although protection against opening is not decisive for such habr users as BarsMonster :)
PS As an additional functionality, the idea of creating an application for secure exchange was considered, by analogy with skype, qip, but only directly, to specific users without a connecting server, but for some reason, it was decided not to affect this area.
In addition, from March 25, a project started on Kickstarter.com dedicated to this device.
Encryption is symmetric and asymmetric, the difference is only in the number of keys used for encryption and decryption. Symmetric encryption uses one key to encode and decode information. The laws of the Russian Federation without licensing their activities allow the use of a symmetric key long
no more than 56 bits. For asymmetric encryption, two keys are used: one key for encryption (public) and one for decoding
(closed). For asymmetric encryption, the laws of the Russian Federation, depending on the algorithms, allow a maximum key length of 256 bits.
Consider some devices to protect information on removable
drives:
- DatAshur from the British company iStorage is a USB flash drive with buttons on the case. The device performs hardware encryption using AES256 symmetric algorithm. There are 10 attempts to enter a PIN code, in case of an incorrect input, the data on the device will
destroyed. The device includes a battery for entering the PIN code before connecting to a PC.
Advantages: durable case, protection against brute-force PIN, data destruction.
Disadvantages: it is not clear what will happen if the battery is discharged; You can try to pick up the PIN-code by the worn buttons or simply delete all the competitor's data and remain unnoticed, and this, in my opinion, is potentially more harmful than copying the data by the competitor (although it is possible to do protection). - Samurai is a Moscow-based company, I suppose that they work in cooperation with iStorage or their distributors, but also make their products, for example, Samurai Nano Drive. Use 256-bit encryption, produce various devices, aimed more at the destruction of information.
Advantages and disadvantages are similar to DatAshur. - Cryptographic USB flash drive reader FLASH-cards from the company Milandr with encryption function, allows you to encrypt information on microSD cards. The device is made on the company's own processor. Made as a regular flash drive.
Advantages : GOST-89 encryption algorithm with a key length of 56 bits (it is not clear from the documentation how GOST-89 was converted to 256 bits), work with an unlimited number of microSD cards.
Disadvantages: the device works only with microSD cards, it is not known whether there is a possibility of transition to more robust encryption algorithms. - Key_P1 Multiclet - a device for protecting information from OAO Multiklet, a processor developer. Consider the device in more detail (hereinafter, we denote the device as Key_P1).
Klyuch_P1 is made with three connectors: USB - socket and plug, as well as a connector for SD cards.

The initial functions of the device (further, the software is expanded, see below for additional functionality):
- protection against modified (spyware) flash drives.
- encryption of information using the DES algorithm for a key length of 56 bits
(after obtaining the license AES and GOST-89 with a long key of 256 bits). - the ability to recover information in the event of the loss of the device Key_P1 and the drive.
- the ability to synchronize keys for sharing files between users.
- display of device off time Key_P1.
')
More description of the functions of the device will be later in this article. Encryption keys are stored in the flash memory of the processor of the device in question.
Klyuch_P1 can work with an unlimited number of drives and on an unlimited number of personal computers, there is no binding to a specific PC.
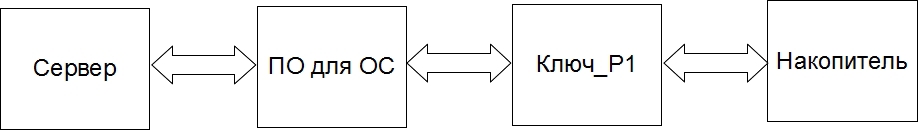
Block diagram of the entire system:

Description of structure elements:
- The server generates the firmware, updates the Key_P1 Manager, firmware and applications Key_P1_for_Windows (or Key_P1_for_Linux) for the user's drive (flash drive).
- (OS software) Key_P1 Manager - performs component updates, initializes Key_P1, generates a set of keys for Key_P1, etc.
- firmware Key_P1 - is a program running on the device Key_P1.
- drive application - Key_P1_for_Windows (Key_P1_for_Linux) (both applications are loaded onto the user's USB flash drive and authorize the user and display the device’s last disconnection time for Windows and Linux).
Let us consider in more detail the main functions of the device.
- Encryption of information is carried out not by one key, but by several (maximum 1024). Encryption occurs by sector for each drive. Thus, a single file can be encrypted with several dozen keys.
- Protection against modified drives occurs due to control of service information transmitted using SCSI commands
- Recovery information:
- The keys are generated by the user on the PC using the Key_P1 program. The manager (in this case, the user) can make a backup copy of their keys in case of recovery.
- Keys are generated by the Key_P1 device. In this case, the user cannot backup their keys.
- User can backup his encrypted information.
- Synchronization of keys is the formation of identical keys for different users for a given initial value and the selected algorithm. The key_P1 device provides the ability to store 50 keys for synchronization. Those. users can store a label of 8 bytes and the key itself. To synchronize keys and start sharing encrypted files, users need to:
- transmit to each other through a verbal agreement, a phone call, sms, e-mail or writing on the sand initial value for key initialization, as well as a key generation algorithm;
- generate a key and assign a label - no more than 8 characters (bytes);
- copy the key to the device Key_P1;
- Encrypted files can be exchanged from any PC, i.e. when downloading the software and installing it on any “alien” PC with the Klyuch_R1 device connected, after entering the PIN code, the user will see the keys and their corresponding tags and will be able to encrypt files with another user for the exchange with another user.
- Device Key_P1 displays, after starting the program key_p1_for_windows.exe (for Windows) or key_p1_for_linux (for Linux), information about the time of the last device shutdown with an accuracy of two minutes. This function allows the user and / or the company's security service to establish the fact and determine the time of unauthorized disconnection of Klyuch_P1, which complicates the actions of the attacker and facilitates his search.
To get started with the device you need:
- Install software, download firmware from server
- Initialize Key_P1 (install firmware, set PIN, PUK codes)
- Initialize the drive (splitting the drive into two sections: open and closed, which is available only after entering the PIN code)
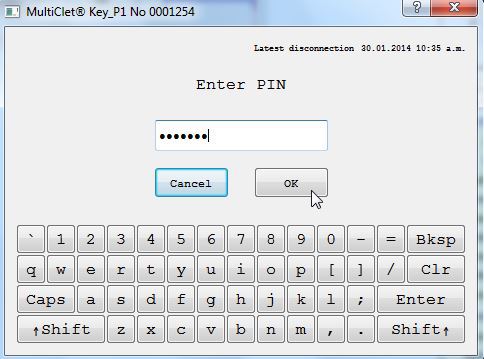
The PIN input window looks like this (draft version):

In addition to the individual version, the corporate version will also be available:
Company employees download the Key_P1 Manager program from a corporate server or from removable media and install it on their OS. Then download the keys generated by the security service or IT-service company. Further, by analogy with the individual version, the Key_P1 and the drive are initialized. Unlike the custom version, in a corporate multi-department manager can choose for which department to encrypt files. The list of departments is formed by authorized employees of the company.

Inside the department, employees can exchange encrypted information by encoding files using Key_P1 Manager and Key_P1. The enterprise security service has the ability to create different demarcations of rights across departments (for example, the “Programmers” department will be able to encrypt files for the “Accounting” department). In addition, an enterprise can put in the device an algorithm for generating one-time passwords for authentication on servers, computers, etc., in order to increase security and ensure protection of commercial and other types of secrets.
As an additional functionality of the device:
- Mac OS support;
- In Klyuch_P1 can be laid the function of generating one-time passwords for the organization of two-factor authentication on servers
various services. Two-factor authentication provides additional protection for your account. To do this, when logging in, not only the username and password are requested, but also unique “verification codes”. Even if the attacker finds out your password, he will not be able to access the account. - personal data storage with automatic substitution during authentication in social networks, payment systems, etc.
- use of the device for authorization on the PC.
From this list, the most interesting is the storage of usernames and passwords from various resources. The only question is how convenient it is to do it. Perform automatic substitution of the login and password pairs or enable the user, after entering the PIN code, to view the login and password in clear text, as allowed by Google Chrome browser.
Now we turn to the consideration of the hardware level of the device.
The main functions of the device are encryption and protection against unauthorized operation of drives.
Consider ways to encrypt data device:
- encrypt the file on the drive - in this case the file will not be encrypted with one random key, but depending on the file size and sector size of the drive (this is the smallest addressable drive memory cell) the file will be encrypted with several keys across the drive sectors;
- encrypt the file on the PC - in this case, the file will be encrypted with a randomly selected key on the device and the contents of the file will be returned to the PC by the device in an encrypted form, in addition, this content will be “wrapped” in a special container containing the key number with which the file was encrypted;
- Encrypt the file for another user - in this case, the file with the previously generated key with the corresponding label (for example, “colleagues1”) will be encrypted by the device without any container and the contents of the file will be returned to the PC.
Also, the function of notifying the user about the change of the file size will be available, in case of replacing the existing file on the drive with a new one with the same name. The device has a “read only” mode to protect against unauthorized copying of information to the drive when working on a PC infected with viruses.
To cut off spyware Klyuch_P1 filters the service commands sent to the drives, which protects the drive from being infected with a hardware virus, and the Klyuch_P1 device analyzes the descriptor table sent by the drive and, based on this information, drives that try to introduce themselves to the PC system as a combined device (for example, a keyboard and a drive) or any device other than a drive.
Consider the implementation of the device at the circuit level.
The device is based on the Russian multicellular processor P1. To interact with the USB host interface, the stm32f205 processor is introduced into the circuit. The multicellular processor is clocked by the stm32f205 processor, the firmware is loaded via the spi interface. The P1 processor assumes all the basic functions of encrypting and hashing information. One of the interesting features of most encryption algorithms is their good parallelization. Due to this fact, it is rational to use a processor with hardware parallelizing operations.

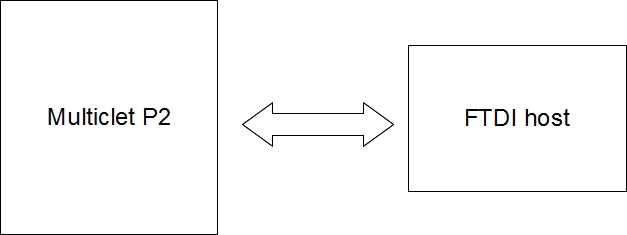
As a result of the device upgrade, the following scheme is assumed:

Interaction with the USB host can be provided by the FTDI chip.
The device has connectors that allow you to work with USB drives and microSD, SD cards.


Advantages:
- encryption with a large set of keys at the hardware level by drive sectors
- control of service teams between the PC and the drive
- storage of the login-password pair
- work in read-only mode
- support for USB drives, SD, microSD cards
- work with an unlimited number of drives
- corporate version
- ability to recover information
Disadvantages: non-specialized building, lack of protection against opening (Although protection against opening is not decisive for such habr users as BarsMonster :)
PS As an additional functionality, the idea of creating an application for secure exchange was considered, by analogy with skype, qip, but only directly, to specific users without a connecting server, but for some reason, it was decided not to affect this area.
In addition, from March 25, a project started on Kickstarter.com dedicated to this device.
Source: https://habr.com/ru/post/217123/
All Articles