Operation windigo
In this post, we publish information about the malicious campaign “Windigo”, with which the attackers compromised thousands of Linux and UNIX servers. Compromised servers were used to steal SSH credentials, redirect web services users to malicious code, and send spam. This operation began at least in 2011 and led to the compromise of various large servers and companies, including the well-known cPanel - the company that develops the eponymous well-known hosting control panel. Another major victim of this campaign was the well-known resource kernel.org , which is the main source code repository for the Linux kernel.

We already partially wrote about the malicious programs that were used in these campaigns, in our reports last year and this year [ 1 , 2 , 3 ], however, now we have a more complete picture of what is happening, as well as an analysis of other malicious programs that used by intruders. Previously, Linux / Ebury and Linux / Cdorked backdoors were mentioned, which were used to steal the credentials of various services on the server, as well as to redirect visitors to web services to malicious resources. In addition to these, the Perl / Calfbot malware was involved in the Windigo operation, with which infected servers could generate millions of spam messages per day.
')
Key findings
general information
Windigo was discovered by ESET with CERT-Bund , SNIC Research Center and the European Organization for Nuclear Research (CERN). To gain access to the attackers' servers, no exploits were used for remote code execution, instead, distributions of various Linux programs that were compromised by malicious content, as well as the authentication credentials of user accounts used to log on to the server, were used. In the future, the database of stolen account data to compromise the new servers was replenished by newly infected machines.
Attackers have benefited from this campaign by performing the following malicious operations:

Fig. The interaction of various components of malware and services used in Windigo.
The following malware was used by intruders in Operation Windigo:
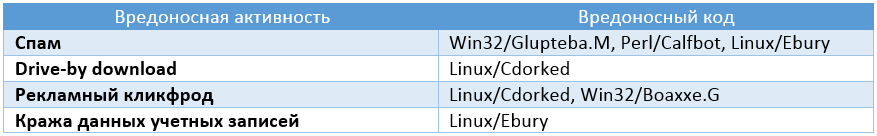
Below is a chronology of events related to Windigo.
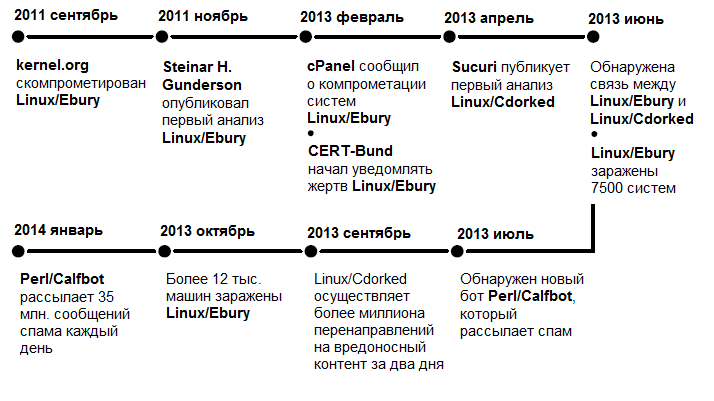
Account Data Theft
As we mentioned above, the theft of SSH credentials is the only method found that the attackers used to extend Windigo’s operation and gain access to new victims. There are two typical SSH credential theft scenarios. The first is to steal this data when the user performs a successful login to the infected server. Another scenario involves theft of data when a user (or administrator) uses an infected server to log on to any other system. Linux / Ebury is a key element in the Windigo operation, as it is responsible for stealing account data.
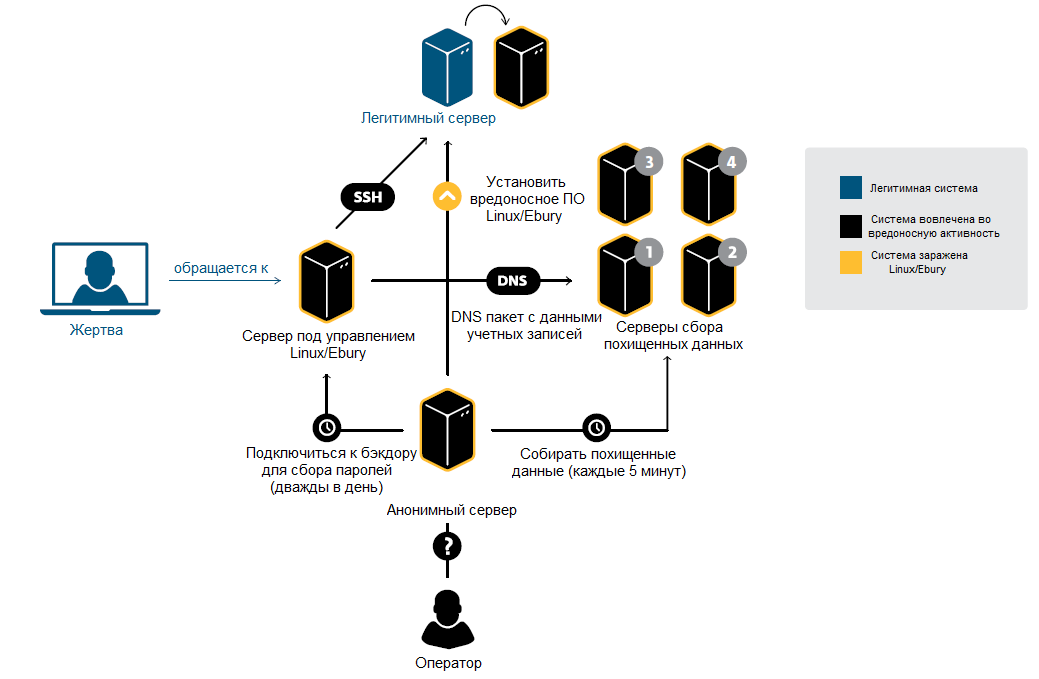
Fig. The scheme of theft of these accounts using Linux / Ebury.
Intercepted Linux / Ebury data is sent to special servers to collect stolen data (exfiltration servers) through special DNS queries. These credentials will then be used by attackers to further spread infections. A group of attackers uses special anonymous tunnel services (anonymizing tunnel services) on one of the compromised servers to perform the connection operation to the servers from which account data was obtained. This allows them to go unnoticed for more time. The server is also used to retrieve stolen account data.
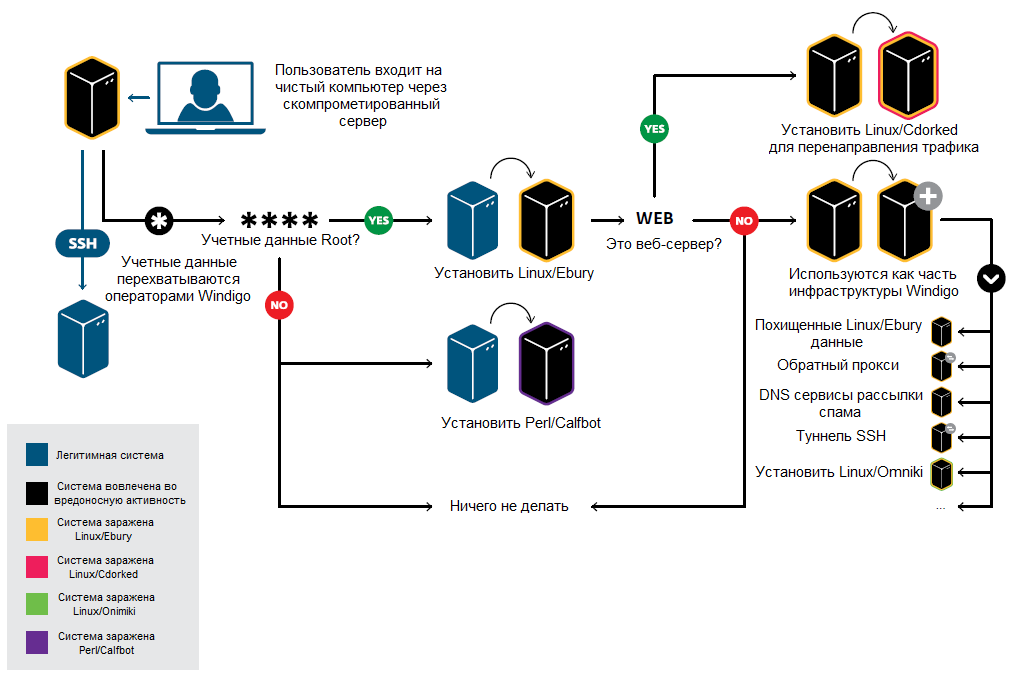
Fig. The scheme of theft of these accounts by operators Windigo.
After stolen account data are in the hands of Windigo operators, they are checked for the level of access that they provide in case of successful login. If the account does not provide root rights, the server may remain intact, i.e. it will not be compromised, or the Perl / Calfbot malware will be installed on it. If the account provides root access, then Linux / Ebury is installed on the server, with which attackers gain access to the server for remote control. In some cases, attackers install Perl / Calfbot even with the root rights received, but this is more of an exception.
Traffic redirection and user infection
If one or several websites are functioning on a compromised server, then Linux / Cdorked will be installed on this system. In addition, attackers can deploy other malicious services on the server. For example, if the server serves the 443rd HTTPS port and is accessible from the Internet, then an instance of the nginx reverse proxy will be installed on this server, it will be used as a link between the Perl / Calfbot bot and the real C & C server.
Web servers infected with Linux / Cdorked redirect users to exploit kits servers that attempt to infect them with malicious code. Below is a diagram of how this happens.
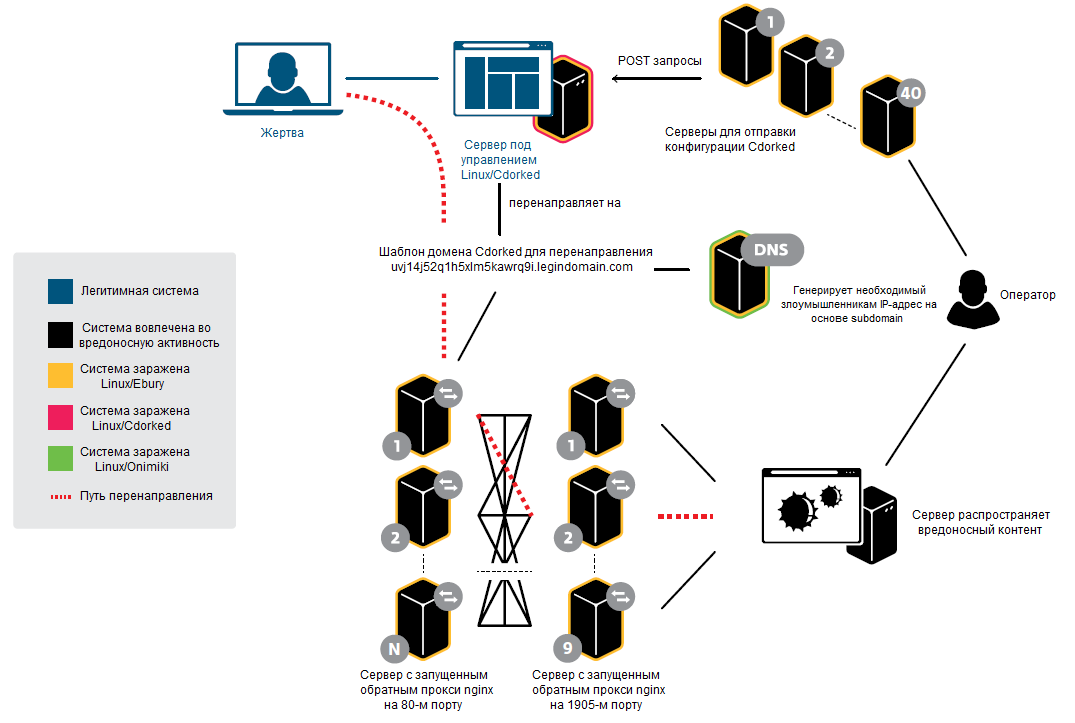
Fig. Infrastructure attackers, which is used to organize the redirection of traffic.
The redirection logic is based on three stages:

Fig. If the victim works under iOS (iPad, iPhone, iPod), she is redirected to porn content (Linux / Cdorked).
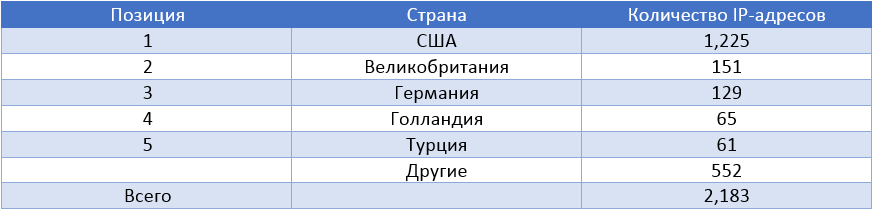
The following table shows the statistics on the IP addresses of infected web servers for the last three months from the time of the report, namely, November 2013, December 2013 and January 2014.

Thus, during these three months, we observed 2,183 unique IP addresses that were seen in the distribution of malicious content (infected with Linux / Cdorked). In this case, 221 of these addresses were active all three months from the beginning of the moment of tracking. The following map shows the geographical distribution of Linux / Cdorked infections.

Fig. Distribution of Linux / Cdorked server infections by country.
The table below shows the countries with the highest number of Linux / Cdorked infections.
Spamming
One of the main ways that Windigo operators can profit from installing malware is sending spam via e-mail. Spam is sent either through servers infected with Perl / Calfbot, or through the PC of users who are infected with Win32 / Glupteba.M. Below we consider the case of spamming with Perl / Calfbot malware.
Fig. An example of spam message.
We used two different approaches to understand the volumes and types of spam generated by Perl / Calfbot bots. The first approach is to create a fake bot that implements the appropriate protocol for working with the C & C server. Using the second approach, we processed the captured network traffic received in January 2014 at one of the reverse C & C proxy servers (C & C reverse proxy server) and, further, extrapolated these results.
The fake client (bot) was developed based on a real Perl / Calfbot bot. It is used to retrieve tasks for sending spam from a C & C server. Spamming tasks consist of several email templates and a mailing list. We analyzed the data from August 2013 to February 2014. During this period of time, our fake customer received 13,422 different tasks for sending spam to generate 20,683,814 unique email addresses. The following histogram shows the domains of the email services that were most often used as email addresses to send spam.
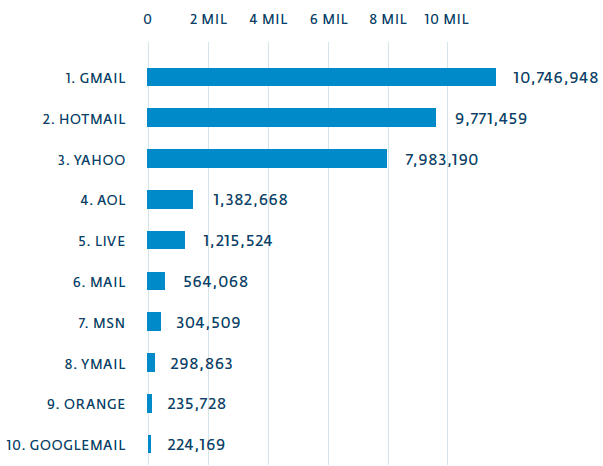
Fig. Email services whose users most often sent spam.
As a result of analyzing the contents of spam messages, we found out that they have several types of content. Most of the message templates are about casinos, bonuses and online dating. Many messages contain words disguised as “unsubscribe” and “report” (report) in the text, which was probably used to avoid detecting spam messages from security tools. Perhaps the attackers recorded the addresses of those users who clicked on these links, marking their addresses as active and using them in subsequent mailings.
Fig. Email entry form for "unsubscribing" from mailing.
The regular spamming task that was delivered to the bot contains a list of 3,000 email addresses and uses English message templates, although we also observed the French, German, Spanish and Russian languages used. All spam message templates contain URLs that point to domains that are served by a compromised TinyDNS server.
The full ESET report on this malicious campaign can be found here .
Drive-by download
Last September, we managed to get network traffic from one of the reverse proxy Linux / Cdorked servers. Despite the fact that this data was obtained from only one proxy server, the analysis of this traffic allowed us to estimate the extent to which users were redirected to malicious content from infected servers. In just a few days, we observed over a million different IP addresses that accessed this server, i.e., just before the user was redirected to the exploit kit page. Some of these users, who were redirected to malicious content, were infected. We managed to get statistics on the OS and browsers of users who were redirected to malicious content during these few days.

Fig. The distribution of OS users who have been victims of websites compromised by Linux / Cdorked.
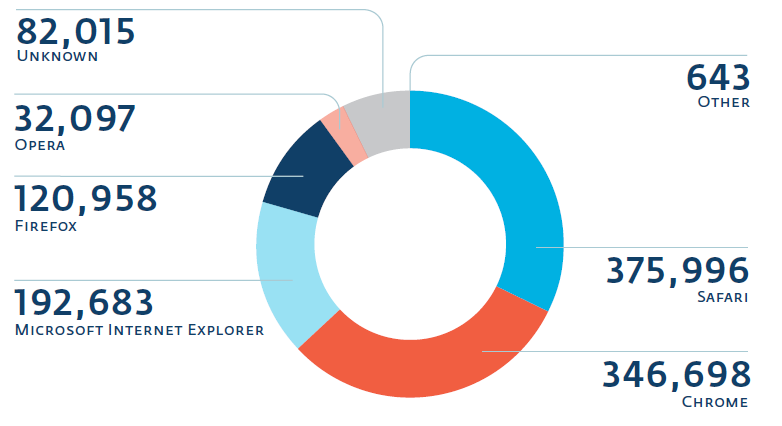
Fig. Distribution of browsers for users who have become victims of websites compromised by Linux / Cdorked.
When the user's computer is redirected to the reverse proxy's external interface, the latter starts a chain of redirects to the server of the exploit kit, which is thus hidden behind the proxy servers that are used for these redirections. The end result of such a redirection will be that a user hits the page with a set of exploits, from where a malicious code will be installed (in case of OS / software vulnerability for one of the exploits used).
At the time of our analysis, the Windigo operators used the Blackhole exploit kit. In November 2013, the operators switched to the Neutrino exploit kit, most likely this was due to the arrest of the author Blackhole, when Paunch’s “clients” began to switch to new means of automatic distribution of malware. We estimate that out of 1.1 million redirected users, the number of infected was 11.108, that is, about 1% (the infection ratio).
We observed two different families of malware, which were thus spread by attackers. Users from the United States, United Kingdom, Canada and Australia were infected with the Win32 / Boaxxe.G malicious code, while others were infected with Win32 / Leechole, a malware that is installed in the Win32 / Glupteba.M system. Malefactors constantly used these families of malware to infect Windows users, at least for the entire time of our tracking of this campaign.
A full analysis of the malware used in the Windigo campaign, indicators of compromise (IOC) and other useful information can be found in our report .

We already partially wrote about the malicious programs that were used in these campaigns, in our reports last year and this year [ 1 , 2 , 3 ], however, now we have a more complete picture of what is happening, as well as an analysis of other malicious programs that used by intruders. Previously, Linux / Ebury and Linux / Cdorked backdoors were mentioned, which were used to steal the credentials of various services on the server, as well as to redirect visitors to web services to malicious resources. In addition to these, the Perl / Calfbot malware was involved in the Windigo operation, with which infected servers could generate millions of spam messages per day.
')
Key findings
- Operation Windigo began at least in 2011
- Over the past two years, more than 25 thousand servers have been compromised.
- The attackers managed to compromise a wide range of operating systems, including Apple OS X, OpenBSD, FreeBSD, MS Windows and Linux.
- Some malware are portable at the OS level. Perl / Calfbot spam bot can work on any OS that has the Perl interpreter installed, and the SSH backdoor can work on both Linux and FreeBSD servers.
- As we noted at the very beginning, such large organizations as the cPanel and the Linux Foundation were victims of this attack.
- Windigo is responsible for sending about 35 million spam messages per day.
- More than 700 web servers currently still redirect users to malicious content.
- Every day, over half a million visitors to Windigo-compromised web resources were redirected to a set of exploits.
- The approximate level of infection of users with malicious code as a result of successful redirection is about 1%.
- Windigo's malicious programs are developed at a fairly high level: they use techniques to hide their presence in the system, portability between different platforms, cryptography, and they also show a high level of knowledge of the attackers in the Linux system.
- HTTP backdoor is portable between Apache httpd, Nginx and lighttpd services.
- The attackers use the resources of the compromised server to the maximum, launching various malware and other activities on it, depending on the level of access that they received.
- To gain access to the servers, the attackers used stolen credentials, as well as backdoored-apps (initially compromised applications) instead of exploiting any vulnerabilities.
general information
Windigo was discovered by ESET with CERT-Bund , SNIC Research Center and the European Organization for Nuclear Research (CERN). To gain access to the attackers' servers, no exploits were used for remote code execution, instead, distributions of various Linux programs that were compromised by malicious content, as well as the authentication credentials of user accounts used to log on to the server, were used. In the future, the database of stolen account data to compromise the new servers was replenished by newly infected machines.
Attackers have benefited from this campaign by performing the following malicious operations:
- spamming;
- infection of users of compromised servers (drive-by);
- redirect users of compromised servers to advertising sites.

Fig. The interaction of various components of malware and services used in Windigo.
The following malware was used by intruders in Operation Windigo:
- Linux / Ebury compromises Linux servers. It provides attackers with full access to the system via the command line (root backdoor shell), and also has the ability to steal SSH credentials.
- Linux / Cdorked compromises Linux web servers. It provides attackers with full access to the system via the command line and is responsible for infecting with malicious code of Windows users (drive-by).
- Linux / Onimiki compromises Linux DNS servers. Responsible for converting domain names that match a specific pattern into the corresponding IP addresses, without the need to modify the configuration settings on the server side.
- Perl / Calfbot compromises the OS, which incorporates the installed Perl interpreter package. Responsible for sending spam (spam bot).
- Win32 / Boaxxe.G is a malicious code for organizing a clickfrod (see Win32 / Boaxxe.BE post ), as well as Win32 / Glupteba.M , used by hackers as a proxy service for Windows. Spread through the drive-by infected servers.

Below is a chronology of events related to Windigo.

Account Data Theft
As we mentioned above, the theft of SSH credentials is the only method found that the attackers used to extend Windigo’s operation and gain access to new victims. There are two typical SSH credential theft scenarios. The first is to steal this data when the user performs a successful login to the infected server. Another scenario involves theft of data when a user (or administrator) uses an infected server to log on to any other system. Linux / Ebury is a key element in the Windigo operation, as it is responsible for stealing account data.

Fig. The scheme of theft of these accounts using Linux / Ebury.
Intercepted Linux / Ebury data is sent to special servers to collect stolen data (exfiltration servers) through special DNS queries. These credentials will then be used by attackers to further spread infections. A group of attackers uses special anonymous tunnel services (anonymizing tunnel services) on one of the compromised servers to perform the connection operation to the servers from which account data was obtained. This allows them to go unnoticed for more time. The server is also used to retrieve stolen account data.

Fig. The scheme of theft of these accounts by operators Windigo.
After stolen account data are in the hands of Windigo operators, they are checked for the level of access that they provide in case of successful login. If the account does not provide root rights, the server may remain intact, i.e. it will not be compromised, or the Perl / Calfbot malware will be installed on it. If the account provides root access, then Linux / Ebury is installed on the server, with which attackers gain access to the server for remote control. In some cases, attackers install Perl / Calfbot even with the root rights received, but this is more of an exception.
Traffic redirection and user infection
If one or several websites are functioning on a compromised server, then Linux / Cdorked will be installed on this system. In addition, attackers can deploy other malicious services on the server. For example, if the server serves the 443rd HTTPS port and is accessible from the Internet, then an instance of the nginx reverse proxy will be installed on this server, it will be used as a link between the Perl / Calfbot bot and the real C & C server.
Web servers infected with Linux / Cdorked redirect users to exploit kits servers that attempt to infect them with malicious code. Below is a diagram of how this happens.

Fig. Infrastructure attackers, which is used to organize the redirection of traffic.
The redirection logic is based on three stages:
- A user visits a legitimate site hosted on an infected Linux / Cdorked server, which then redirects it to a special malicious domain, which is formed based on the original domain (the new subdomain). This redirection is performed through a set of infected Linux / Ebury servers and depends on certain conditions provided by the operators.
- The previously trusted DNS server is already infected by one of the components of Windigo, which is called Linux / Onimiki, and returns the corresponding IP address for subsequent redirection (the required IP address is encoded into the subdomain that was added in the previous step). Since as a result of the redirection, a legitimate domain is used, this makes it possible to hide the fact that the address has been changed to a malicious one, which makes the detection of this operation more difficult. The returned IP address belongs to the reverse proxy server.
- This server is the entry point to the reverse proxy chain, which terminates on a server serving a set of exploits. This last server is responsible for installing malicious code on the user's computer, and can also redirect it to advertising sites.

Fig. If the victim works under iOS (iPad, iPhone, iPod), she is redirected to porn content (Linux / Cdorked).
The following table shows the statistics on the IP addresses of infected web servers for the last three months from the time of the report, namely, November 2013, December 2013 and January 2014.

Thus, during these three months, we observed 2,183 unique IP addresses that were seen in the distribution of malicious content (infected with Linux / Cdorked). In this case, 221 of these addresses were active all three months from the beginning of the moment of tracking. The following map shows the geographical distribution of Linux / Cdorked infections.

Fig. Distribution of Linux / Cdorked server infections by country.
The table below shows the countries with the highest number of Linux / Cdorked infections.

Spamming
One of the main ways that Windigo operators can profit from installing malware is sending spam via e-mail. Spam is sent either through servers infected with Perl / Calfbot, or through the PC of users who are infected with Win32 / Glupteba.M. Below we consider the case of spamming with Perl / Calfbot malware.

Fig. An example of spam message.
We used two different approaches to understand the volumes and types of spam generated by Perl / Calfbot bots. The first approach is to create a fake bot that implements the appropriate protocol for working with the C & C server. Using the second approach, we processed the captured network traffic received in January 2014 at one of the reverse C & C proxy servers (C & C reverse proxy server) and, further, extrapolated these results.
The fake client (bot) was developed based on a real Perl / Calfbot bot. It is used to retrieve tasks for sending spam from a C & C server. Spamming tasks consist of several email templates and a mailing list. We analyzed the data from August 2013 to February 2014. During this period of time, our fake customer received 13,422 different tasks for sending spam to generate 20,683,814 unique email addresses. The following histogram shows the domains of the email services that were most often used as email addresses to send spam.

Fig. Email services whose users most often sent spam.
As a result of analyzing the contents of spam messages, we found out that they have several types of content. Most of the message templates are about casinos, bonuses and online dating. Many messages contain words disguised as “unsubscribe” and “report” (report) in the text, which was probably used to avoid detecting spam messages from security tools. Perhaps the attackers recorded the addresses of those users who clicked on these links, marking their addresses as active and using them in subsequent mailings.

Fig. Email entry form for "unsubscribing" from mailing.
The regular spamming task that was delivered to the bot contains a list of 3,000 email addresses and uses English message templates, although we also observed the French, German, Spanish and Russian languages used. All spam message templates contain URLs that point to domains that are served by a compromised TinyDNS server.
The full ESET report on this malicious campaign can be found here .
Drive-by download
Last September, we managed to get network traffic from one of the reverse proxy Linux / Cdorked servers. Despite the fact that this data was obtained from only one proxy server, the analysis of this traffic allowed us to estimate the extent to which users were redirected to malicious content from infected servers. In just a few days, we observed over a million different IP addresses that accessed this server, i.e., just before the user was redirected to the exploit kit page. Some of these users, who were redirected to malicious content, were infected. We managed to get statistics on the OS and browsers of users who were redirected to malicious content during these few days.

Fig. The distribution of OS users who have been victims of websites compromised by Linux / Cdorked.

Fig. Distribution of browsers for users who have become victims of websites compromised by Linux / Cdorked.
When the user's computer is redirected to the reverse proxy's external interface, the latter starts a chain of redirects to the server of the exploit kit, which is thus hidden behind the proxy servers that are used for these redirections. The end result of such a redirection will be that a user hits the page with a set of exploits, from where a malicious code will be installed (in case of OS / software vulnerability for one of the exploits used).
At the time of our analysis, the Windigo operators used the Blackhole exploit kit. In November 2013, the operators switched to the Neutrino exploit kit, most likely this was due to the arrest of the author Blackhole, when Paunch’s “clients” began to switch to new means of automatic distribution of malware. We estimate that out of 1.1 million redirected users, the number of infected was 11.108, that is, about 1% (the infection ratio).
We observed two different families of malware, which were thus spread by attackers. Users from the United States, United Kingdom, Canada and Australia were infected with the Win32 / Boaxxe.G malicious code, while others were infected with Win32 / Leechole, a malware that is installed in the Win32 / Glupteba.M system. Malefactors constantly used these families of malware to infect Windows users, at least for the entire time of our tracking of this campaign.
A full analysis of the malware used in the Windigo campaign, indicators of compromise (IOC) and other useful information can be found in our report .
Source: https://habr.com/ru/post/216871/
All Articles