Managing Firefox and Thunderbird from Group Policy

Foreword
One of the drawbacks of Mozilla software products is their poor focus on the corporate user segment. Unfortunately, there are not many tools for managing Mozilla product installations in large companies. They are built on the basis of:
- Getting some of the configuration from a web server - Mozilla AutoConfig (https://developer.mozilla.org/en-US/docs/MCD,_Mission_Control_Desktop_AKA_AutoConfig)
- Integration of a part of the configuration into the distribution kit of the product (product plug-in)
- CCK (https://addons.mozilla.org/en-US/firefox/addon/cck/) - Getting some of the settings from GPO GPOFirefox (https://addons.mozilla.org/ru/firefox/addon/gpo-for-firefox/)
I like the latter approach more: it allows you to flexibly bind settings to different groups of computers and users, and all settings can be made from the group policy console without going into writing any scripts (in AutoConfig, you can also create settings based on user data, but it requires server-side scripting). In addition, to implement management from Group Policy, you do not need to deploy additional fault-tolerant servers.
Unfortunately, the GPOFirefox plugin is implemented only for Firefox and does not have some of the necessary functionality, so I had to write my own, suitable for both Firefox and Thunderbird, which I decided to share with the community.
Opportunities
Here is a list of features embedded in the plugin:
- Single plugin support for both Firefox and Thunderbird
- Setting from group policy both default settings (defaultPref) and settings blocked for users (lockPref). Actually all Mozilla product configuration systems have this functionality.
- The ability to use in the settings of some placeholder strings, which, when the settings are applied, is replaced by the value of the user's environment variables In particular, the following environment variables are supported:% username%,% userdomain%,% userdnsdomain%,% userprofile%,% computername%.
- Manage root certificates in user profile. In particular, it supports the installation and removal of root certificates.
- Logging of all plugin actions in the error console. Undoubtedly, when diagnosing the use of GPO, it is useful to have a log that shows which settings were applied from the policy
- ADMX group policy template, which allows you to customize any Firefox and Thunderbird settings without editing the template. The only restriction is that you can simultaneously install no more than 10 root certificates and delete no more than 10 root certificates. (I wanted to do any number, but faced with restrictions of the syntax of group policy templates: for the text element, the maximum length can be changed, but for the list this feature is not available.)
Now in detail about each opportunity.
Single plugin support for both Firefox and Thunderbird
In my opinion it is logical that in a company where Firefox is used as a browser, Thunderbird will be used as an email client. Create a plugin for each program when the approach to the settings is completely identical - it makes no sense. At the same time, sometimes settings that are called the same in both programs must be different in them. Therefore, the plug-in at startup determines which program it is running (by unique identifier) and reads the settings from the relevant part of the policy.
')
Setting from group policy both default settings (defaultPref) and settings blocked for users (lockPref).
All settings are accessible from the policy management console.
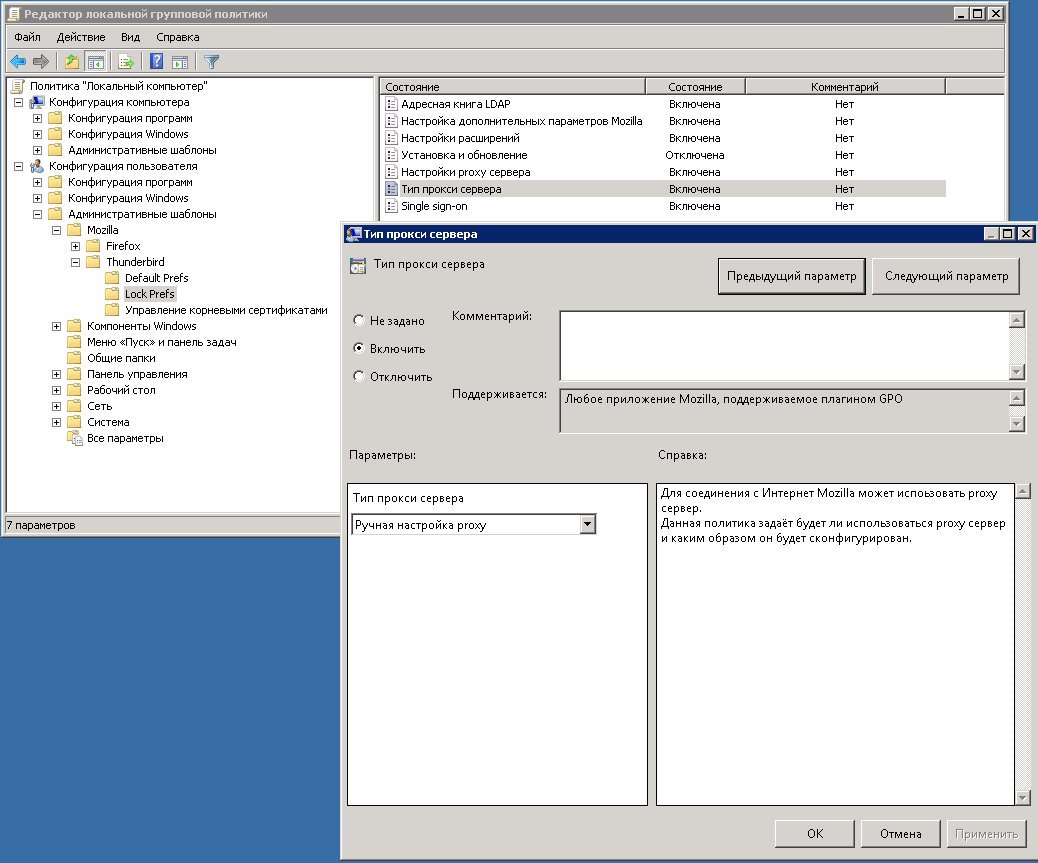
The ability to use in the settings of some wildcards
In my opinion, when configuring such network.negotiate-auth.trusted-uris parameters, it is convenient to use the value of the% userdnsdomain% variable set by the user.
Also, using the% username%,% userdomain%,% userdnsdomain% user variable values, it is convenient to generate default settings for the user’s mail profile (so that when the user first starts Thunderbird, the user has already configured his mailbox, and if necessary, the user can adjust these settings. )
Logging of all plugin actions in the error console.
Perhaps the only setting that is inaccessible from the group policy and is applied only from the user profile is extensions.gpo.enablelog - it includes logging of the plug-in actions in the error console. This setting is read before the group policy is read and therefore it is impossible to influence its value from the GPO.
The console log looks like this:

ADMX group policy template, which allows you to customize any Firefox and Thunderbird settings without editing the template.
With the ADMX template I had to tinker badly, but it was worth it. ADMX templates have several advantages over older adm:
- Automatically loaded when you start the console editing the group policy
- It is possible to organize a central repository of these templates and they will be accessible from any administrator workstation.
- They are well localized and localization is automatically loaded depending on the OS language.
Unfortunately, the FullArmor ADMX Migrator offered for download from microsoft.com "breaks" the policy templates a bit. Therefore, we had to arm ourselves with documentation and bring the ADMX to a working state manually.
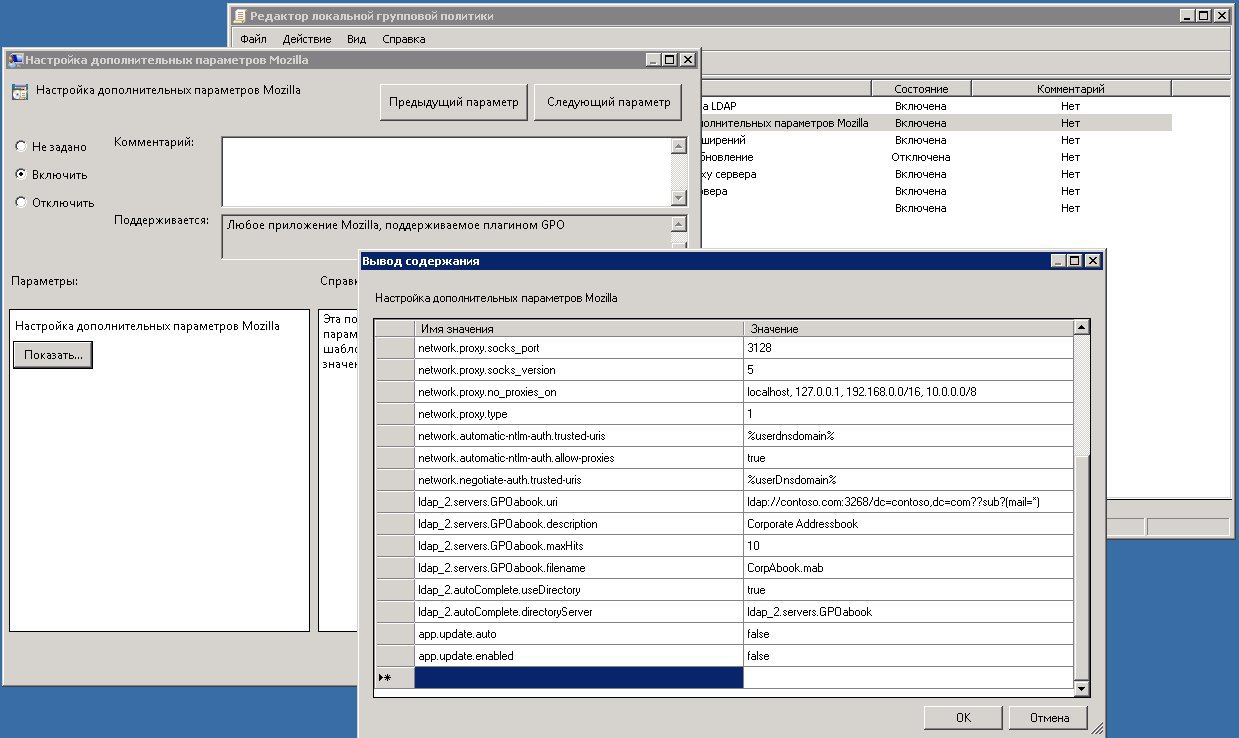
In order to be able to set the value of any parameter, the “Configure additional Mozilla settings” policy is introduced, where, at the expense of the list element, you can view the parameters set by other policies and set any parameters that were not originally included in the template.
Manage root certificates in user profile.
When the company’s root certificate is self-signed, the administrator has the task of distributing it to user profiles. It would be possible to install it in a self-made distribution or use CCK to install the certificate. But the certificate can be compromised and then it will have to be changed to a new one.
Initially, I was hoping to implement adding certificates through the list element — just like when editing additional parameters (then you could install and delete any number of certificates), but this element has a limit on the length of the text value — 1033 characters, and for the text element, the maximum length can be set. Therefore, the certificate management window looks like:
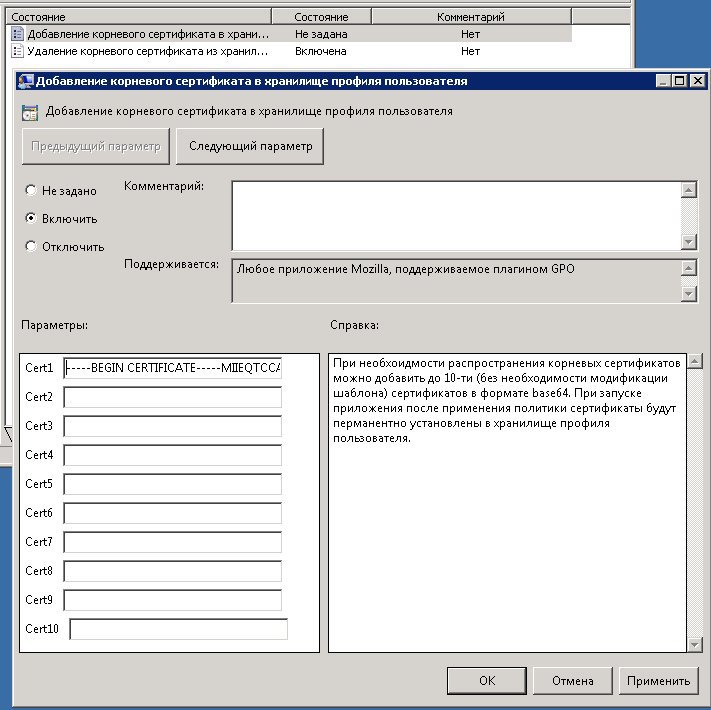
You can add or remove up to 10 certificates at the same time. To add / remove a certificate, it is necessary to insert its body in base64 encoding (in this format it can, for example, be exported from the Windows certificate store ) into one of ten fields (any) in the corresponding policy. Certificates are permanently installed, i.e. when the policy is no longer applied to the user / computer, then certificates remain in the profile.
Deleting a certificate works in a similar way - you just need to add the base64 certificate body to the value of one of the 10 fields - the next time you start the program with the plugin after applying the policy - the certificate will be deleted.
Installing plugin + policy templates.
While the plug-in on addons.mozilla.org is not published (I plan to do this after the community has expressed its opinion - maybe before the official publication I will make some adjustments in accordance with the wishes).
You can download the plugin and policy templates from the project page at sourceforge: mozillagpo.sourceforge.io
There is also a brief documentation and some recommendations for use.
To install the policy templates, simply unpack the contents of the PolicyTemplate.zip archive into the% systemroot% \ PolicyDefinitions folder on the administrator’s computer. Or use the instructions for creating a central repository of policy templates .
Plugin can be installed:
- Classic way from xpi file
- Put in one of the installation locations of plug-ins , after pre-setting the parameter extensions.autoDisableScopes
- Integrate the plugin into your own Firefox and Thunderbird distributions
Source: https://habr.com/ru/post/216675/
All Articles