Hosting provider vs. DDoS attack. REG.RU Solution - Professional Outsourcing
Recently, REG.RU, in cooperation with DDoS Guard, introduced free automatic protection against DDoS attacks. Protection works automatically and is able to withstand an attack at a speed of more than 100 Gbps, which allows you to avoid shutting down servers and sites, and, consequently, the loss of customers and profits.
The problem of combating DDoS-attacks faces all hosting providers without exception. Classical methods of struggle suggest the temporary inaccessibility of the attacked site, but REG.RU and DDoS Guard were able to find solutions to this problem. But first things first.

')
Methods to combat DDoS-attack
Currently, there are several approaches to protecting against DDoS attacks:
The first approach is the use of vendor equipment (Arbor, Cisco, Juniper and others). This approach is usually used in the case when the company is not able to outsource these tasks due to the increased level of information protection.
In this case, we are talking about using ready-made hardware solutions for filtering traffic. At the entrance to the network, a hardware firewall is installed that filters incoming traffic. It uses a certain number of basic rules by which it determines whether to allow traffic further.
The main advantage of this approach is that the equipment has official certification and is guaranteed to cope with certain types of attacks. The hardware specification specifies the maximum attack volume and, if the attack power does not exceed the stated values, all Internet resources will function normally.
Cons of this approach:
• Only one point of presence is available;
• The protection ceiling along the band is limited by the channel coming from the equipment uplinks;
• Relatively low power when working with resource depletion attacks, therefore, it is difficult or impossible to dynamically configure routes and distribute the load;
• The price of professional solutions starts with five-digit amounts (for protection of 10 Gbit / s).
The second approach is the use of a distributed filtering network. This approach is used by industry leaders and looks the most promising.
The essence of this method is to take the attack as close as possible to the place where it is generated. This allows you to optimally use the network infrastructure and not to deliver malicious traffic from one point to another, and immediately block it. In the case of a distributed DDoS attack, when traffic is generated in several countries, it will be redirected along the best routes to the nearest points of presence (POP), filtered and only legitimate, useful traffic will reach the addressee.
The most important advantage of such an organization of protection is incredible flexibility. Because of this, you can balance the traffic between the points of presence and work with filters in real time, setting them up for protection against current techniques of DDoS attacks, which are constantly being modified and modernized. Recently, attackers have become very resourceful - often legitimate traffic can only be distinguished from the attacker, only having specific experience in the field of protection.
How DDoS Guard works
Currently, DDoS-Guard has a distributed network with a total capacity of 200 Gbit / s, which allows you to safely and quickly check the incoming traffic flow.
Main nodes of the network:
- Amsterdam, Netherlands;
- Frankfurt, Germany;
- Kiev, Ukraine;
- Moscow, Russia.
The existing topology makes it possible to confidently receive large volumes of traffic, without creating an excessive load on intermediate operators, to process local traffic in Russia and Ukraine, and has considerable reserves for expanding the available incoming bandwidth. Following the concept of continuous growth, the company is already designing additional points of presence and traffic clearing nodes in North America and Southeast Asia.
The network architecture is designed taking into account the possible threats and risks associated with DDoS attacks in three independently-reserved layers:
- Routing layer:
The main task is reliable routing of large volumes of traffic, ensuring connectivity with the maximum number of external networks.
Reliable and productive routers are used at this level. The maximum design capacity of each traffic processing node is 1400 Gbit / s, the possibility of rapid expansion without switching to 100GbE ports and changing the existing connectivity topology with external networks is 440 Gbit / s.
- Redundant batch processing cluster (batch processing layer):

The main task is distributed inspection of traffic at levels 3-4 of the OSI model under conditions of ultrahigh packet loads and total incoming traffic of 100–200 Gbit / s at each point of presence.
This layer consists of several (2-5, depending on the point of presence) mutually-redundant devices that perform packet traffic checking using DPI methods. The algorithms used are designed directly by engineers at DDoS Guard.
It is necessary to pay special attention to the fact that traffic inspection and routing to the end user occurs directly at the receiving point, which reduces delays to a minimum and creates additional redundancy opportunities.
- Redundant application-level query processing cluster (application layer):
The main task is to implement methods for checking requests for levels 5+ of the OSI model — HTTP, HTTPs, DNS, SMTP, and so on. Here is the decryption, verification and encryption of HTTPs traffic.
The layer is reserved regardless of batch processing and routing and does not lose its performance up to the complete failure of all nodes.
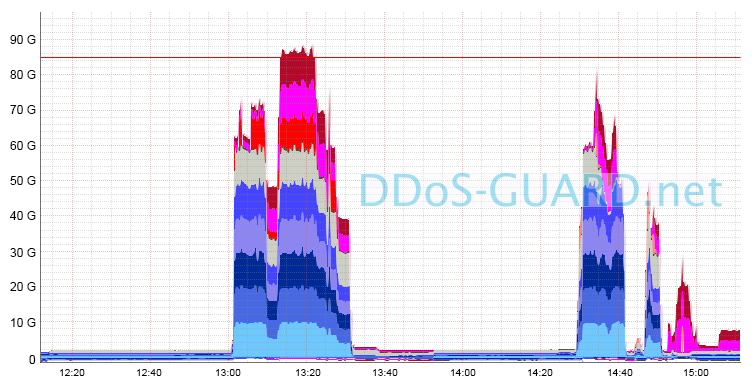
Examples of successfully reflected attacks in the form of channel loading graphs:
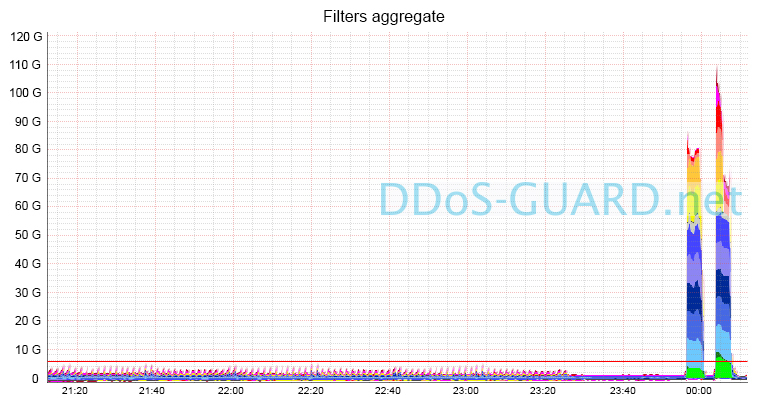

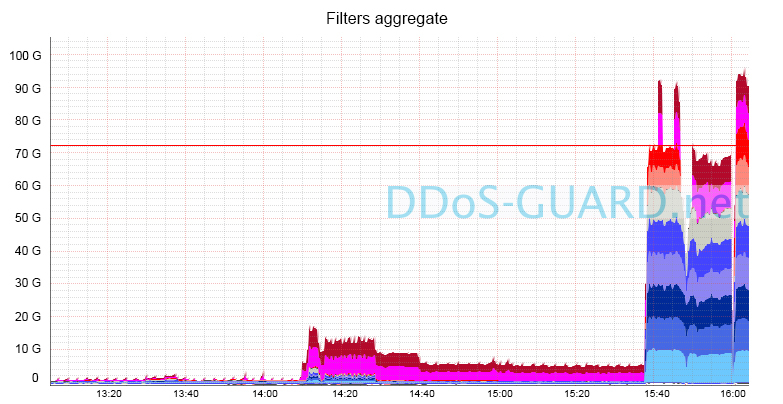
A few words about the BGP integration of REG.RU and DDoS Guard
REG.RU is the first Russian hosting provider to provide the DDoS protection service for free and in automatic mode.

From a technological point of view, the protection of REG.RU clients is as follows:
• REG.RU allocates an address space in which risk clients accumulate.
• Having basic BGP sessions with trunk operators, REG.RU additionally establishes BGP sessions with DDoS Guard and, in the event of an attack, announces a network that needs protection.
• In the future, all traffic that goes to REG.RU passes through a cascade of filters and is delivered in a filtered form.
• From the DDoS Guard side, the protection works constantly, in real time, while all trash traffic is blocked in a fully automatic mode.
• Delivery of traffic along optimal routes ensures low latency for the end user.
Now, within the framework of the partnership REG.RU and DDoS Guard, protection against attacks of the type
ICMP flood, TCP SYN flood, TCP-malformed, UDP flood, DNS query flood. In the near future, support is planned for protection against HTTP / HTTPS flood attacks.
Source: https://habr.com/ru/post/216533/
All Articles