Interaction of vulnerability scanners with Metasploit. Part 2
Required software: Kali Linux .
Required knowledge: experience with the Linux console (in particular, the Kali Linux distribution) and the Metasploit console .
In the first part, we learned about the modules for authentication vulnerability detection (SMB Login Check, VNC Authentication None Detection) and the plug-in for finding vulnerabilities in web applications (WMAP). In the second part, we will install the Nessus vulnerability scanner on the 32-bit version of Kali Linux system for its subsequent interaction with Metasploit (installation on the 64-bit version is done in the same way).
Metasploit is a favorite tool for hackers and information security specialists, which includes many modules for creating and using exploits. But for the exploitation of vulnerabilities, they must first be identified. The framework functionality for these purposes is not enough, but vulnerability scanners can easily cope with this task. Interaction of vulnerability scanners with Metasploit modules can be implemented using supported plugins. As a result of this integration, we will be able to find vulnerabilities and immediately exploit them.
')
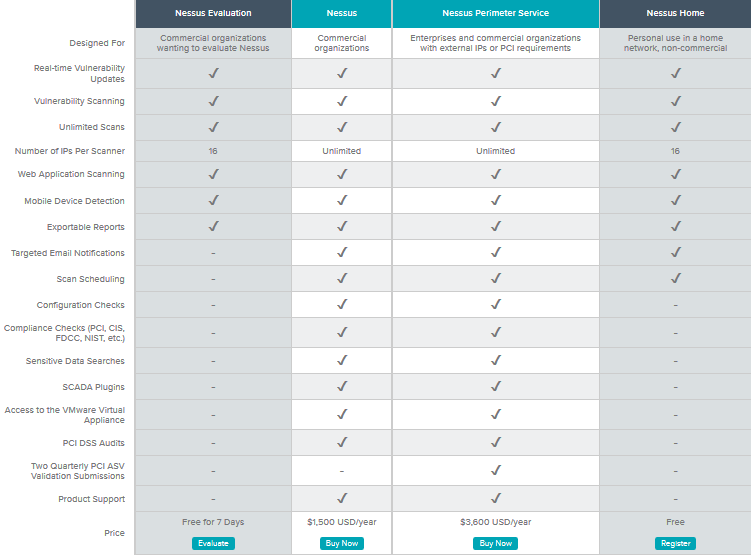
Nessus is one of the most popular vulnerability scanners developed by Tenable Network Security. Until 2005, it was free open source software, and in 2008 a paid version of the product was released. There is also a free "home" version, limited to use in the home network. We will use it for our purposes.
So, let's proceed to the installation.
To begin with, we will download the latest version of the program for the Debian system from the manufacturer’s website (at the time of this writing, Nessus v5.2.5 was relevant).

Run the installation program
after which we activate the Nessus service
/
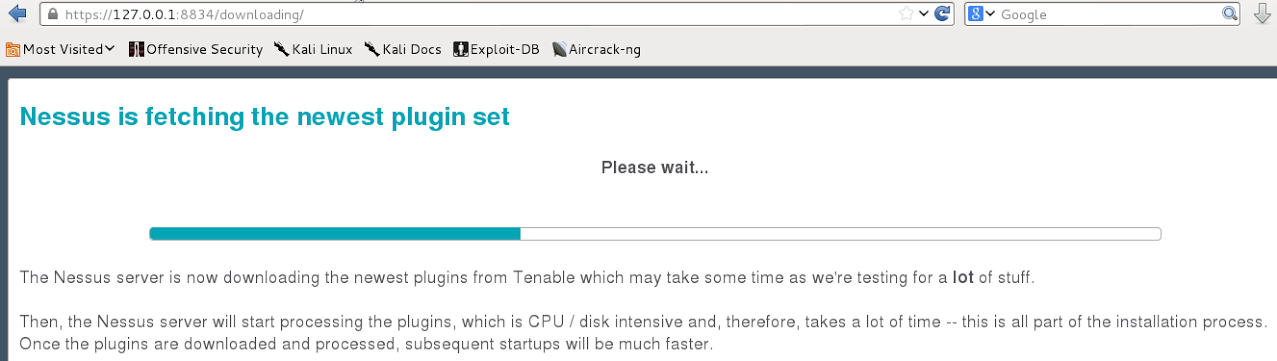
The scanner is controlled via the web interface. To get there, enter in the browser address bar https://127.0.0.1:8834 . Here you need to create an administrator account, specifying a username and password.
In the next step, you must enter the activation code that will come to your e-mail specified on the manufacturer’s website during registration .
The final stage of installation is loading plug-ins.
To save the scan results in the Metasploit database, you need to connect to it
Required knowledge: experience with the Linux console (in particular, the Kali Linux distribution) and the Metasploit console .
In the first part, we learned about the modules for authentication vulnerability detection (SMB Login Check, VNC Authentication None Detection) and the plug-in for finding vulnerabilities in web applications (WMAP). In the second part, we will install the Nessus vulnerability scanner on the 32-bit version of Kali Linux system for its subsequent interaction with Metasploit (installation on the 64-bit version is done in the same way).
Metasploit is a favorite tool for hackers and information security specialists, which includes many modules for creating and using exploits. But for the exploitation of vulnerabilities, they must first be identified. The framework functionality for these purposes is not enough, but vulnerability scanners can easily cope with this task. Interaction of vulnerability scanners with Metasploit modules can be implemented using supported plugins. As a result of this integration, we will be able to find vulnerabilities and immediately exploit them.
')
Installing Nessus Home
Nessus is one of the most popular vulnerability scanners developed by Tenable Network Security. Until 2005, it was free open source software, and in 2008 a paid version of the product was released. There is also a free "home" version, limited to use in the home network. We will use it for our purposes.

So, let's proceed to the installation.
To begin with, we will download the latest version of the program for the Debian system from the manufacturer’s website (at the time of this writing, Nessus v5.2.5 was relevant).

Run the installation program
dpkg -i Nessus-5.2.5-debian6_i386.debafter which we activate the Nessus service
/
etc/init.d/nessusd startThe scanner is controlled via the web interface. To get there, enter in the browser address bar https://127.0.0.1:8834 . Here you need to create an administrator account, specifying a username and password.
In the next step, you must enter the activation code that will come to your e-mail specified on the manufacturer’s website during registration .
The final stage of installation is loading plug-ins.

To save the scan results in the Metasploit database, you need to connect to it
db_connect <user:pass>@<host:port>/

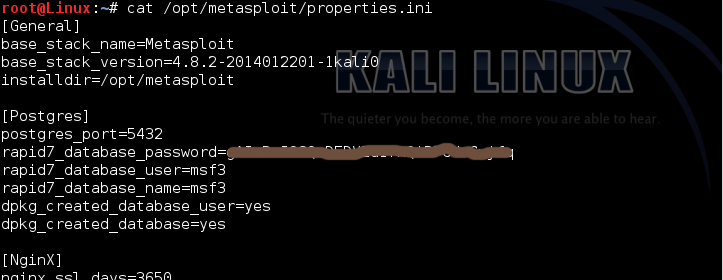
properties.ini
cat /opt/metasploit/properties.ini
,
user = rapid7_database_user
pass = rapid7_database_password
host = 127.0.0.1 ( , Nessus )
port = postgres_port
database = rapid7_database_name
nessus
load nessus

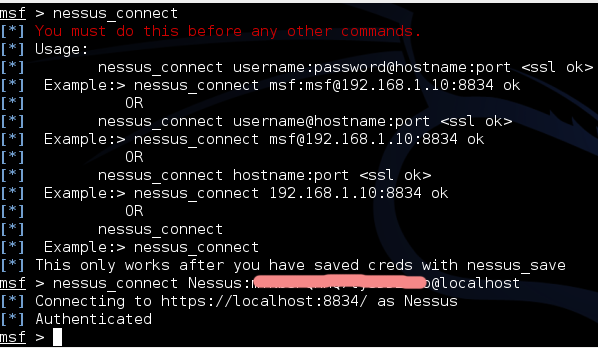
Nessus
nessus_connect username:password@hostname:port
,
username – Nessus
password - Nessus
, Nessus. , , ( ), - . , -.
: Web Application Tests Policy – - , Basic Network Scan Policy – .
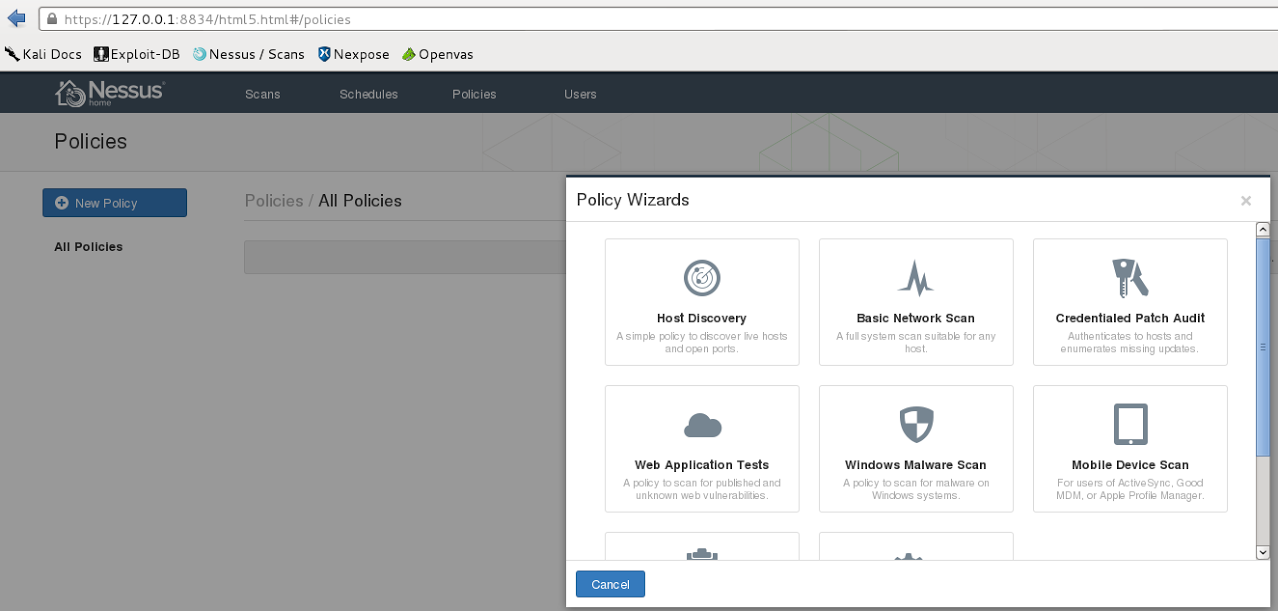
Web Application Tests Policy
127.0.0.1:8834 > Policy > New Policy > Web Application Tests Policy
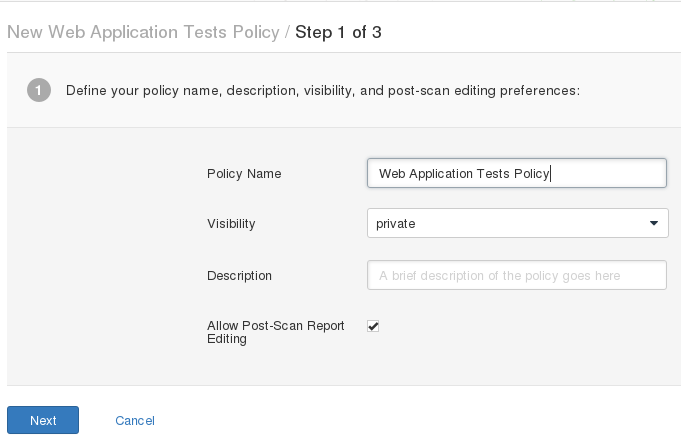
( ) .
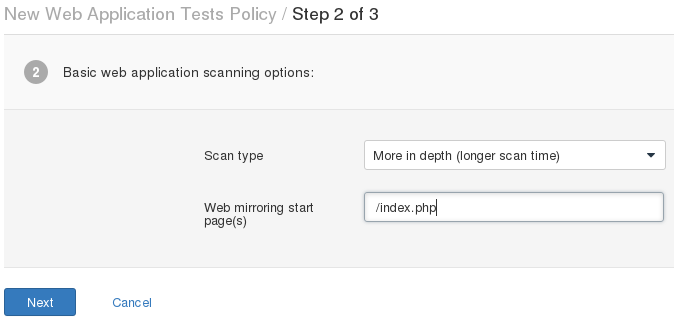
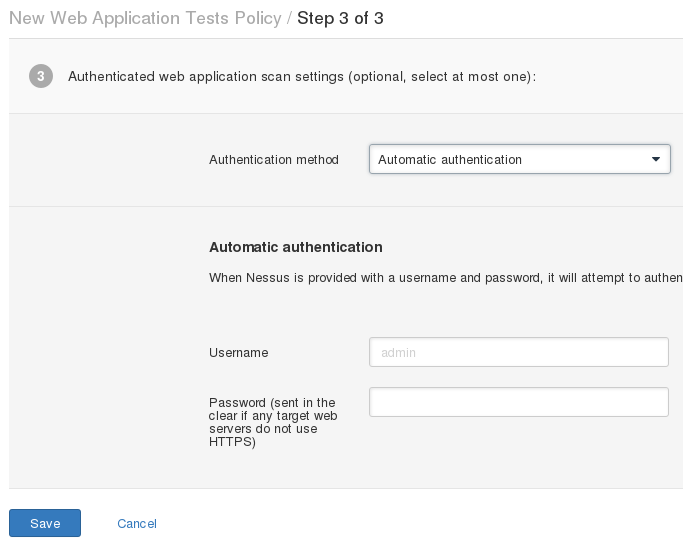
127.0.0.1:8834 > Scans > New Scan
, , ( ).
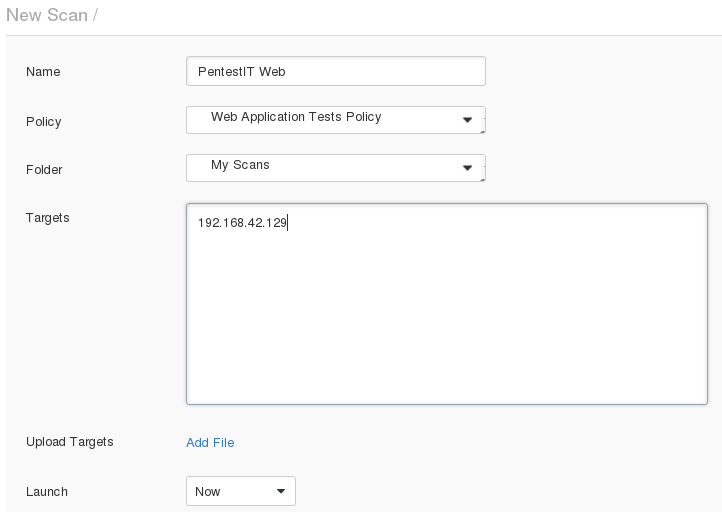
Nessus 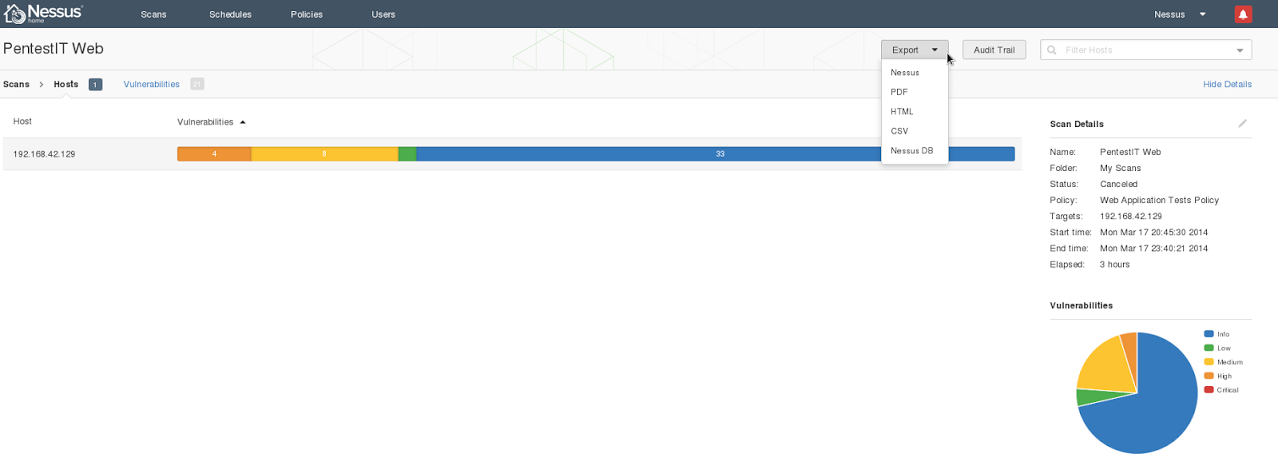
Metasploit
db_import '/root/Desktop/nessus_report_PentestIT_Web.nessus'

Basic Network Scan Policy
msfconsole
, -
127.0.0.1:8834 > Policy > New Policy > Basic Network Scan Policy
,
, , “Internal”, – 'External'

. msfconsole, nessus_policy_list id Nessus,
nessus_scan_new 2 PentestIT 192.168.42.129
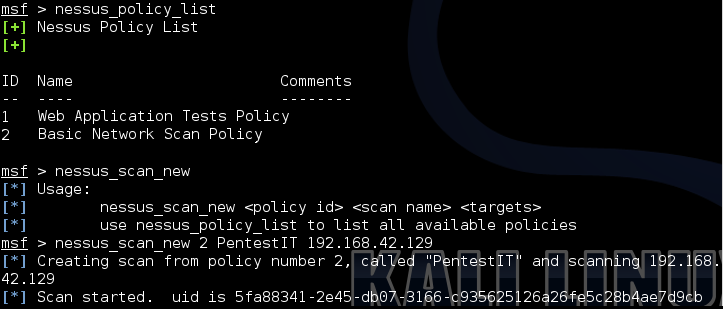
?
nessus_scan_status

Nessus, id
nessus_report_list

, nessus_report_vulns
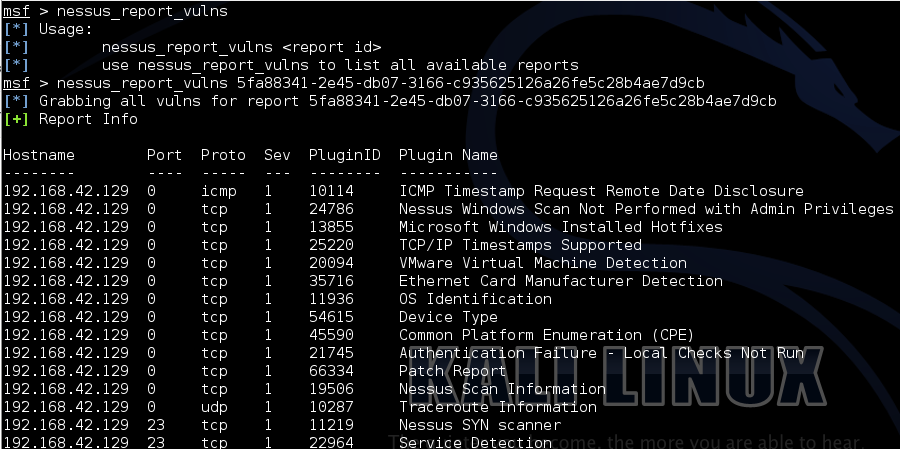
, ,
nessus_report_get 5fa88341-2e45-db07-3166-c935625126a26fe5c28b4ae7d9cb
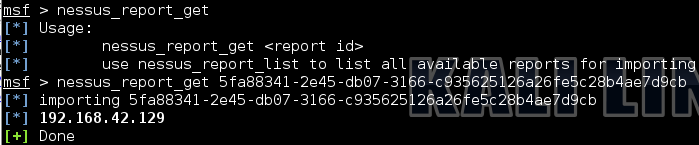
, msfconsole - , Nessus - Metasploit.
...
:
Metasploit Unleashed. Nessus Via Msfconsole
Nessus
Metasploit Penetration Testing Cookbookdb_connect <user:pass>@<host:port>/

properties.ini
cat /opt/metasploit/properties.ini

,
user = rapid7_database_user
pass = rapid7_database_password
host = 127.0.0.1 ( , Nessus )
port = postgres_port
database = rapid7_database_name
nessus
load nessus

Nessus
nessus_connect username:password@hostname:port

,
username – Nessus
password - Nessus
, Nessus. , , ( ), - . , -.
: Web Application Tests Policy – - , Basic Network Scan Policy – .

Web Application Tests Policy
127.0.0.1:8834 > Policy > New Policy > Web Application Tests Policy

( ) .


127.0.0.1:8834 > Scans > New Scan
, , ( ).

Nessus 
Metasploit
db_import '/root/Desktop/nessus_report_PentestIT_Web.nessus'

Basic Network Scan Policy
msfconsole
, -
127.0.0.1:8834 > Policy > New Policy > Basic Network Scan Policy
,

, , “Internal”, – 'External'


. msfconsole, nessus_policy_list id Nessus,
nessus_scan_new 2 PentestIT 192.168.42.129

?
nessus_scan_status

Nessus, id
nessus_report_list

, nessus_report_vulns

, ,
nessus_report_get 5fa88341-2e45-db07-3166-c935625126a26fe5c28b4ae7d9cb

, msfconsole - , Nessus - Metasploit.
...
:
Metasploit Unleashed. Nessus Via Msfconsole
Nessus
Metasploit Penetration Testing Cookbook
db_connect <user:pass>@<host:port>/

properties.ini
cat /opt/metasploit/properties.ini

,
user = rapid7_database_user
pass = rapid7_database_password
host = 127.0.0.1 ( , Nessus )
port = postgres_port
database = rapid7_database_name
nessus
load nessus
Nessus
nessus_connect username:password@hostname:port
,
username – Nessus
password - Nessus
, Nessus. , , ( ), - . , -.
: Web Application Tests Policy – - , Basic Network Scan Policy – .

Web Application Tests Policy
127.0.0.1:8834 > Policy > New Policy > Web Application Tests Policy
( ) .


127.0.0.1:8834 > Scans > New Scan, , ( ).

Nessus

Metasploit
db_import '/root/Desktop/nessus_report_PentestIT_Web.nessus'
Basic Network Scan Policy
msfconsole
, -
127.0.0.1:8834 > Policy > New Policy > Basic Network Scan Policy,

, , “Internal”, – 'External'


. msfconsole, nessus_policy_list id Nessus,
nessus_scan_new 2 PentestIT 192.168.42.129
?
nessus_scan_status
Nessus, id
nessus_report_list
, nessus_report_vulns

, ,
nessus_report_get 5fa88341-2e45-db07-3166-c935625126a26fe5c28b4ae7d9cb
, msfconsole - , Nessus - Metasploit.
...
:
Metasploit Unleashed. Nessus Via Msfconsole
Nessus
Metasploit Penetration Testing Cookbook
db_connect <user:pass>@<host:port>/

properties.ini
cat /opt/metasploit/properties.ini

,
user = rapid7_database_user
pass = rapid7_database_password
host = 127.0.0.1 ( , Nessus )
port = postgres_port
database = rapid7_database_name
nessus
load nessus

Nessus
nessus_connect username:password@hostname:port

,
username – Nessus
password - Nessus
, Nessus. , , ( ), - . , -.
: Web Application Tests Policy – - , Basic Network Scan Policy – .

Web Application Tests Policy
127.0.0.1:8834 > Policy > New Policy > Web Application Tests Policy

( ) .


127.0.0.1:8834 > Scans > New Scan
, , ( ).

Nessus 
Metasploit
db_import '/root/Desktop/nessus_report_PentestIT_Web.nessus'

Basic Network Scan Policy
msfconsole
, -
127.0.0.1:8834 > Policy > New Policy > Basic Network Scan Policy
,

, , “Internal”, – 'External'


. msfconsole, nessus_policy_list id Nessus,
nessus_scan_new 2 PentestIT 192.168.42.129

?
nessus_scan_status

Nessus, id
nessus_report_list

, nessus_report_vulns

, ,
nessus_report_get 5fa88341-2e45-db07-3166-c935625126a26fe5c28b4ae7d9cb

, msfconsole - , Nessus - Metasploit.
...
:
Metasploit Unleashed. Nessus Via Msfconsole
Nessus
Metasploit Penetration Testing Cookbookdb_connect <user:pass>@<host:port>/

properties.ini
cat /opt/metasploit/properties.ini

,
user = rapid7_database_user
pass = rapid7_database_password
host = 127.0.0.1 ( , Nessus )
port = postgres_port
database = rapid7_database_name
nessus
load nessus

Nessus
nessus_connect username:password@hostname:port

,
username – Nessus
password - Nessus
, Nessus. , , ( ), - . , -.
: Web Application Tests Policy – - , Basic Network Scan Policy – .

Web Application Tests Policy
127.0.0.1:8834 > Policy > New Policy > Web Application Tests Policy

( ) .


127.0.0.1:8834 > Scans > New Scan
, , ( ).

Nessus 
Metasploit
db_import '/root/Desktop/nessus_report_PentestIT_Web.nessus'

Basic Network Scan Policy
msfconsole
, -
127.0.0.1:8834 > Policy > New Policy > Basic Network Scan Policy
,

, , “Internal”, – 'External'


. msfconsole, nessus_policy_list id Nessus,
nessus_scan_new 2 PentestIT 192.168.42.129

?
nessus_scan_status

Nessus, id
nessus_report_list

, nessus_report_vulns

, ,
nessus_report_get 5fa88341-2e45-db07-3166-c935625126a26fe5c28b4ae7d9cb

, msfconsole - , Nessus - Metasploit.
...
:
Metasploit Unleashed. Nessus Via Msfconsole
Nessus
Metasploit Penetration Testing Cookbook
db_connect <user:pass>@<host:port>/

properties.ini
cat /opt/metasploit/properties.ini

,
user = rapid7_database_user
pass = rapid7_database_password
host = 127.0.0.1 ( , Nessus )
port = postgres_port
database = rapid7_database_name
nessus
load nessus
Nessus
nessus_connect username:password@hostname:port
,
username – Nessus
password - Nessus
, Nessus. , , ( ), - . , -.
: Web Application Tests Policy – - , Basic Network Scan Policy – .

Web Application Tests Policy
127.0.0.1:8834 > Policy > New Policy > Web Application Tests Policy
( ) .


127.0.0.1:8834 > Scans > New Scan, , ( ).

Nessus

Metasploit
db_import '/root/Desktop/nessus_report_PentestIT_Web.nessus'
Basic Network Scan Policy
msfconsole
, -
127.0.0.1:8834 > Policy > New Policy > Basic Network Scan Policy,

, , “Internal”, – 'External'


. msfconsole, nessus_policy_list id Nessus,
nessus_scan_new 2 PentestIT 192.168.42.129
?
nessus_scan_status
Nessus, id
nessus_report_list
, nessus_report_vulns

, ,
nessus_report_get 5fa88341-2e45-db07-3166-c935625126a26fe5c28b4ae7d9cb
, msfconsole - , Nessus - Metasploit.
...
:
Metasploit Unleashed. Nessus Via Msfconsole
Nessus
Metasploit Penetration Testing Cookbook
db_connect <user:pass>@<host:port>/

properties.ini
cat /opt/metasploit/properties.ini

,
user = rapid7_database_user
pass = rapid7_database_password
host = 127.0.0.1 ( , Nessus )
port = postgres_port
database = rapid7_database_name
nessus
load nessus

Nessus
nessus_connect username:password@hostname:port

,
username – Nessus
password - Nessus
, Nessus. , , ( ), - . , -.
: Web Application Tests Policy – - , Basic Network Scan Policy – .

Web Application Tests Policy
127.0.0.1:8834 > Policy > New Policy > Web Application Tests Policy

( ) .


127.0.0.1:8834 > Scans > New Scan
, , ( ).

Nessus 
Metasploit
db_import '/root/Desktop/nessus_report_PentestIT_Web.nessus'

Basic Network Scan Policy
msfconsole
, -
127.0.0.1:8834 > Policy > New Policy > Basic Network Scan Policy
,

, , “Internal”, – 'External'


. msfconsole, nessus_policy_list id Nessus,
nessus_scan_new 2 PentestIT 192.168.42.129

?
nessus_scan_status

Nessus, id
nessus_report_list

, nessus_report_vulns

, ,
nessus_report_get 5fa88341-2e45-db07-3166-c935625126a26fe5c28b4ae7d9cb

, msfconsole - , Nessus - Metasploit.
...
:
Metasploit Unleashed. Nessus Via Msfconsole
Nessus
Metasploit Penetration Testing CookbookSource: https://habr.com/ru/post/216169/
All Articles