We lift the VPN tunnel from the world home bypassing NAT
. 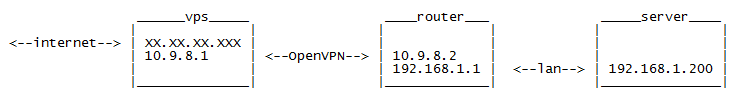
I want to tell you about how having your VPS server on the Internet, you can raise a tunnel to your home network. And do not pay at the same time for a static IP provider, and even being behind a NAT, still make your home services available on the Internet.
First of all, we will install and configure the OpenVPN server on our VPS:
Edit the configuration file:
Here 10.9.8.x will be our VPN network, in which we assign the address 10.9.8.1 to the VPN server and the address 10.9.8.2 to the VPN client.
The last line is a statistical route, which is needed so that our VPS knows that the way to our home network is through a router
')
We also need to generate a key with which our router will connect to the server:
And you can run a daemon:
Now we will install OpenVPN on our router from which we will initialize the VPN connection:
Copy the key to our router using the scp :
Edit the interface configuration:
as alexdob said :
And check whether everything will work for us:
If everything is ok, then launch and add the OpenVPN daemon to autorun:
Now configure the routing.
In order for our router to let our server pass to the home network, and pass machines from the home network to the server, we need to add the following rules to the router.
Create a file and write these rules into it:
Making it executable:
And add it to /etc/rc.local for autorun:
Add before exit 0
In principle, everything is ready.
Our networks are connected, all the machines perfectly each other see and exchange packets.
Now, if you wish, you can configure forwarding of ports from external to internal address.
This is how, for example, the forwarding of an ssh port to one of the machines in my home network looks like:
Where XX.XX.XX.XXX is the external IP of the server, 192.168.1.200 is the IP of my machine within the home network, 666 is the port when accessing that I get on this machine
PS: If something goes wrong with you, make sure that your VPS has and all the necessary kernel modules are connected
When writing the article, I used information from the following sources:
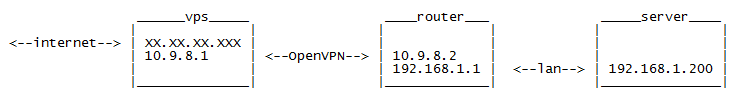
I want to tell you about how having your VPS server on the Internet, you can raise a tunnel to your home network. And do not pay at the same time for a static IP provider, and even being behind a NAT, still make your home services available on the Internet.
Initial data
- Debian VPS server with static real IP
- router with OpenWRT firmware, which is behind provider NAT
- home network with computers and virtual machines in 192.168.1.0/24
Tunnel Tuning
First of all, we will install and configure the OpenVPN server on our VPS:
apt-get update apt-get install openvpn Edit the configuration file:
vi /etc/openvpn/tun0.conf dev tun0 ifconfig 10.9.8.1 10.9.8.2 secret /etc/openvpn/static.key route 192.168.1.0 255.255.255.0 Here 10.9.8.x will be our VPN network, in which we assign the address 10.9.8.1 to the VPN server and the address 10.9.8.2 to the VPN client.
The last line is a statistical route, which is needed so that our VPS knows that the way to our home network is through a router
')
We also need to generate a key with which our router will connect to the server:
openvpn --genkey --secret static.key And you can run a daemon:
service openvpn start Now we will install OpenVPN on our router from which we will initialize the VPN connection:
opkg update opkg install openvpn Copy the key to our router using the scp :
scp root@your-server.org:/etc/openvpn/static.key /etc/openvpn/static.key Edit the interface configuration:
vi /etc/openvpn/tun0.conf remote your-server.org dev tun0 ifconfig 10.9.8.2 10.9.8.1 secret /etc/openvpn/static.key keepalive 60 120 as alexdob said :
keepalive 60 180
It means the following: every 60 seconds, send a ping to a remote host, and if within 180 seconds no packet was received, then restart the tunnel.
And check whether everything will work for us:
openvpn --config /etc/openvpn/tun0.conf If everything is ok, then launch and add the OpenVPN daemon to autorun:
/etc/init.d/openvpn start /etc/init.d/openvpn enable Routing
Now configure the routing.
In order for our router to let our server pass to the home network, and pass machines from the home network to the server, we need to add the following rules to the router.
Create a file and write these rules into it:
vi /etc/iptables.up.rules #!/bin/sh #Allow forwarding via tunnel iptables -I INPUT -i tun0 -j ACCEPT iptables -I FORWARD -i tun0 -j ACCEPT iptables -I OUTPUT -o tun0 -j ACCEPT iptables -I FORWARD -o tun0 -j ACCEPT Making it executable:
chmod +x /etc/iptables.up.rules And add it to /etc/rc.local for autorun:
/etc/iptables.up.rules Add before exit 0
In principle, everything is ready.
Our networks are connected, all the machines perfectly each other see and exchange packets.
Now, if you wish, you can configure forwarding of ports from external to internal address.
This is how, for example, the forwarding of an ssh port to one of the machines in my home network looks like:
# Forward SSH port to server iptables -t nat -A PREROUTING -d XX.XX.XX.XXX -p tcp --dport 666 -j DNAT --to-dest 192.168.1.200:22 iptables -t nat -A POSTROUTING -d 192.168.1.200 -p tcp --dport 22 -j SNAT --to-source 10.9.8.1 Where XX.XX.XX.XXX is the external IP of the server, 192.168.1.200 is the IP of my machine within the home network, 666 is the port when accessing that I get on this machine
PS: If something goes wrong with you, make sure that your VPS has and all the necessary kernel modules are connected
Sources
When writing the article, I used information from the following sources:
Source: https://habr.com/ru/post/216101/
All Articles