Shield and sword in RBS systems - 2, or how to deal with MITM attacks and unauthorized remote access
In January 2013, we already wrote about a universal solution for RBS systems. Over the past year, a number of revisions were carried out aimed at improving protection against theft and increasing usability.
Doing so has prompted us to a sharp increase in the number of attacks on the RBS systems associated with the use of remote access to users' computers. Unfortunately, with this type of attack, ordinary two-factor authentication is in no way capable of protecting the company's financial assets. An obvious countermeasure is the need to create a trusted environment with the inability to use remote control tools.
So, we will remind that such PINPad Ruken . This is a solution of the TrustScreen class that can form a trusted environment and visualize the document being signed before applying the electronic signature. The signature occurs directly on the device itself after the user physically presses the corresponding button on the screen. Thus, we defend ourselves against attacks made using remote control tools, substituting the contents of the document for transfer to the signature (Man-in-the-browser).
')

As you can see, we made a new case with a special stand, completely redesigned the interface design, and also provided the device with additional functionality.
So, the main points:
Now we will show how it all looks when used.
We will proceed to our Demobank, where we will go through the registration process to get started, namely, we will form a request for a certificate .
Choose from the list of connected PINPad devices:

We will invent a login:
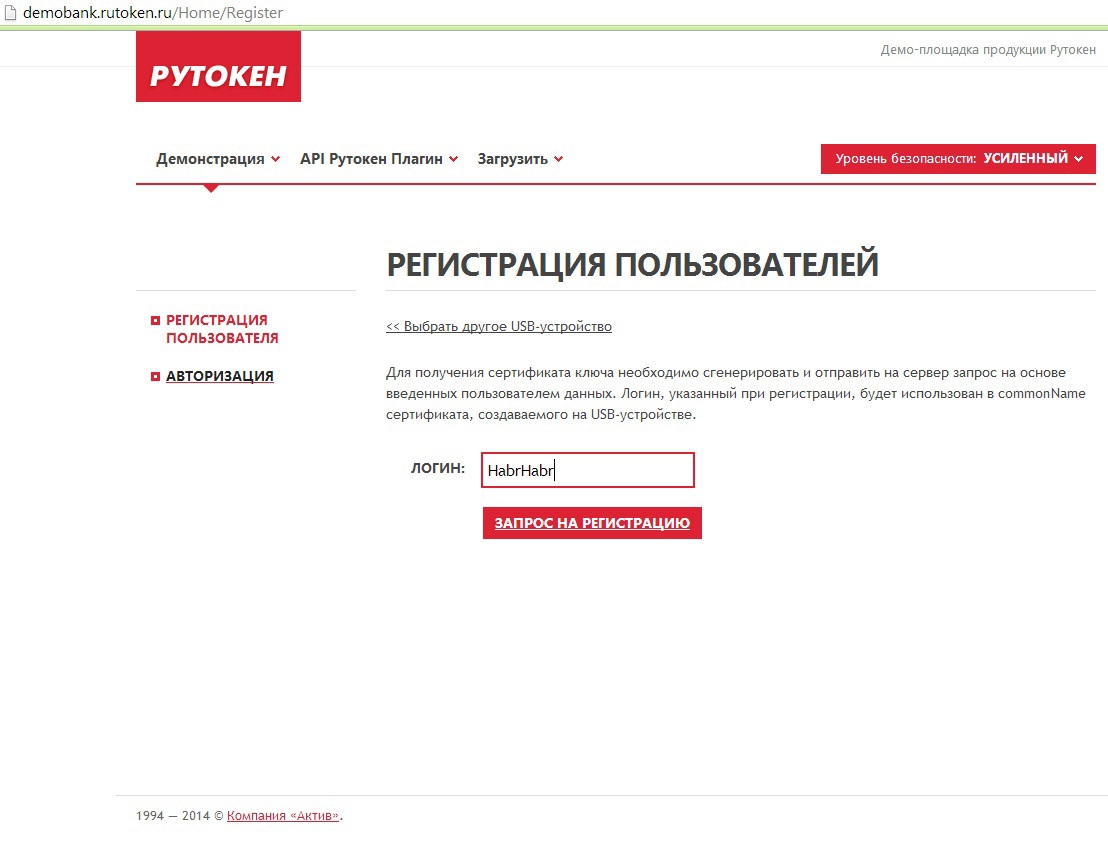
The request is displayed on the screen and, if we agree, click on the check mark and enter the PIN code:


Now authorization . We choose our certificate, we look at the screen with what certificate is the entrance and at what address.
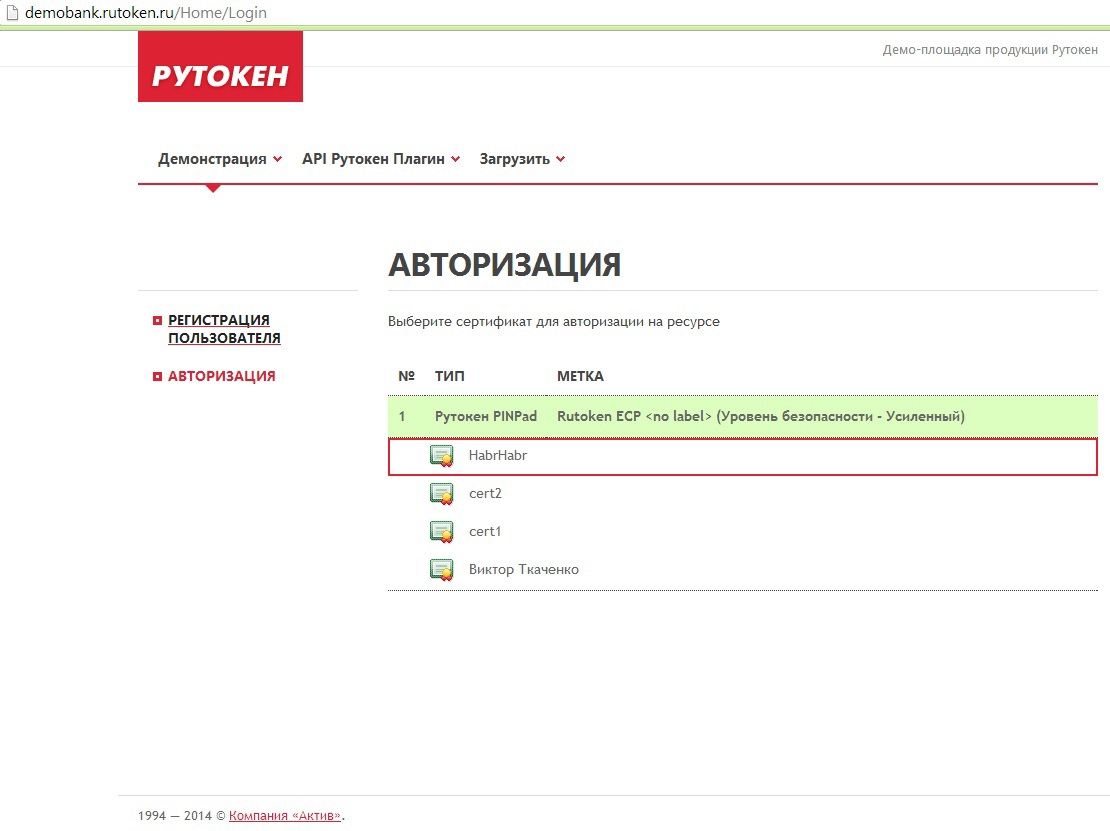
We agree and enter the PIN-code on the device for authorization:

Note that registration and authentication occur by signing random data on the device in the CMS format with the request displayed on the device screen.
In the Demobank there is a white list implementation in which the contractors are listed, with whom we constantly work and trust them completely.

What does the exclamation mark mean for billing? In this case, a visual confirmation of payment for non-white list respondents and a payment confirmation with an amount in excess of 100,000 rubles have been implemented. Such payments require visualization and additional confirmation with the help of Rutoken PINPad.
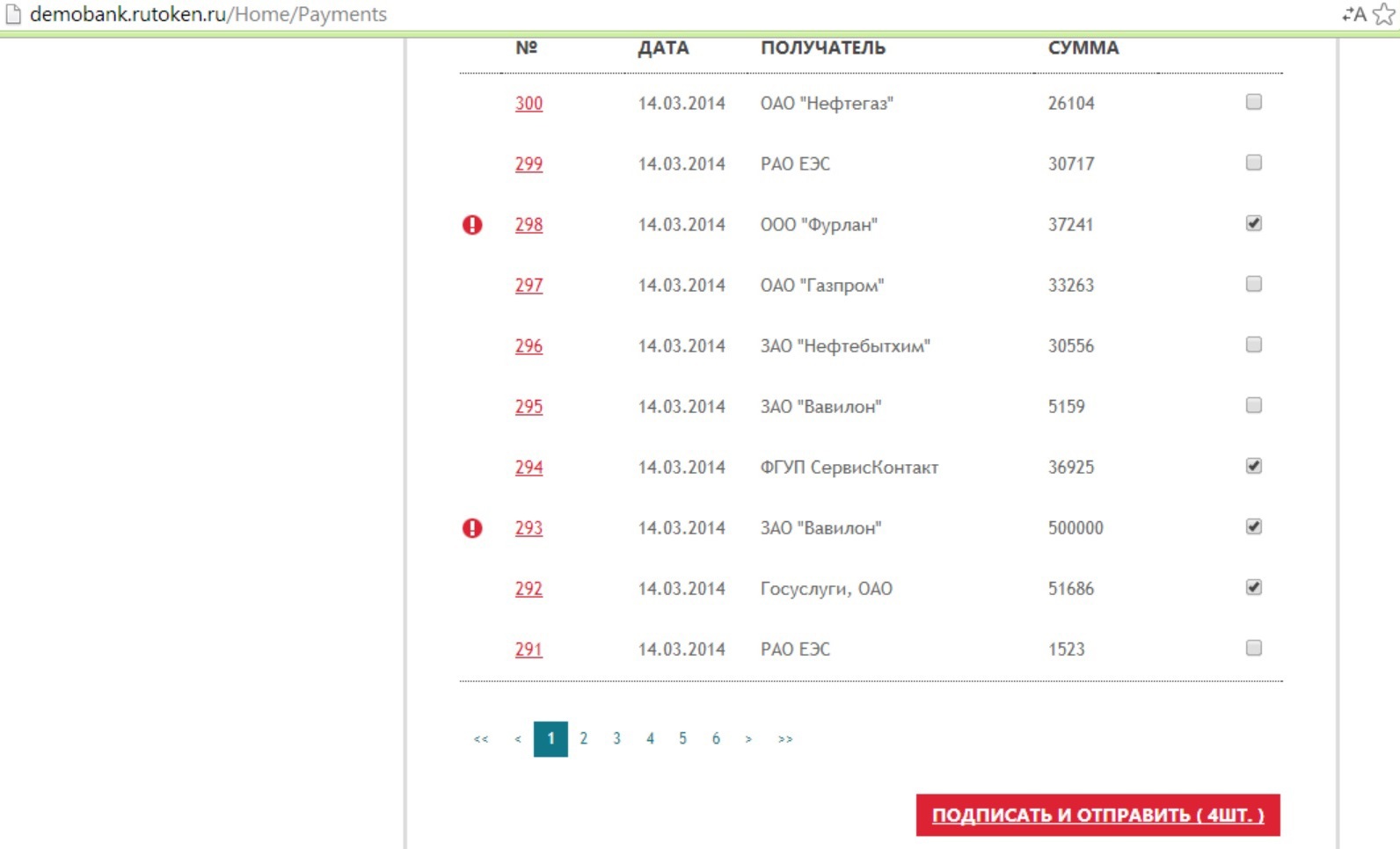
If we make a mass payment of 4 payments, two of them, not marked with an exclamation mark, will be signed without visualization, and the other two will be displayed on the screen of PINPad:

In the case of a substitution of the payment document by the attacker, on the device screen, we notice incorrect details and reject the payment:

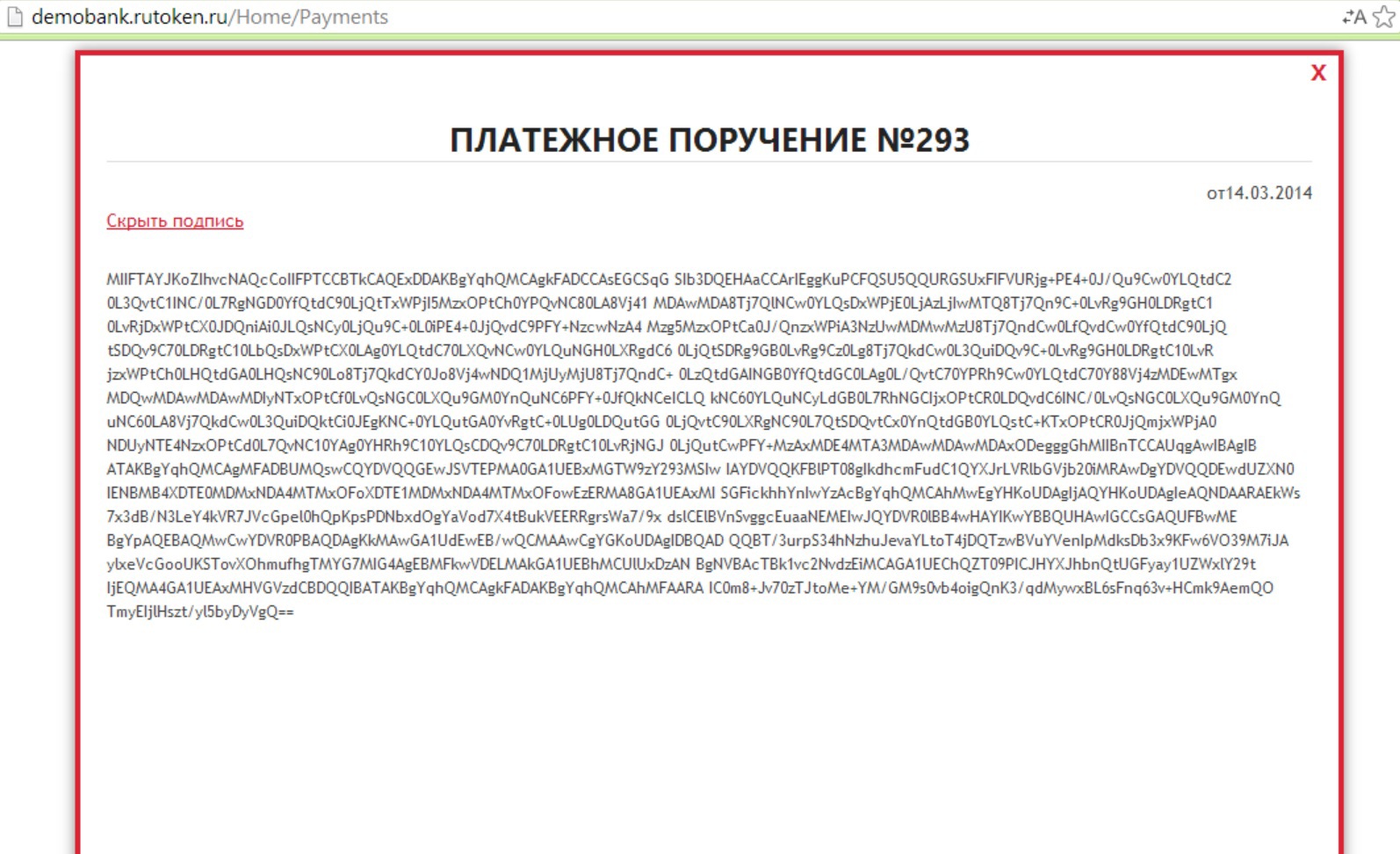
If everything is OK, then we sign the payment order, a signature is formed, then all data is encrypted and sent to the server:

After viewing and confirming the generated signature in the CMS format:

Note that, depending on the security policy chosen, it is possible to cache the PIN during authorization and use this cache in the session without requesting the PIN during each operation.
To conclude:
The presented solution is able to maximally protect user accounts from various types of threats, including those related to remote control and document substitution. PINPad also allows you to make secure mass payments, organize incident investigation.
Currently, Rutoken PINPad is being supported in the most common RBS systems and a number of banks.
Doing so has prompted us to a sharp increase in the number of attacks on the RBS systems associated with the use of remote access to users' computers. Unfortunately, with this type of attack, ordinary two-factor authentication is in no way capable of protecting the company's financial assets. An obvious countermeasure is the need to create a trusted environment with the inability to use remote control tools.
So, we will remind that such PINPad Ruken . This is a solution of the TrustScreen class that can form a trusted environment and visualize the document being signed before applying the electronic signature. The signature occurs directly on the device itself after the user physically presses the corresponding button on the screen. Thus, we defend ourselves against attacks made using remote control tools, substituting the contents of the document for transfer to the signature (Man-in-the-browser).
')

As you can see, we made a new case with a special stand, completely redesigned the interface design, and also provided the device with additional functionality.
So, the main points:
- Visualization of documents and their signature on the device itself
- Implementation of domestic cryptographic algorithms "on board the device"
- Unrecoverable keys
- PIN hardware input on the screen
- The ability to generate and confirm a certificate request in the format PKCS # 10
- X.509 format and PKI support
- Lack of ability to sign unverified data
- The possibility of making mass payments on the "white" lists
- PIN caching option
- Operation log for incident investigation
- Work with any browser through the plugin
- Color touch screen
Now we will show how it all looks when used.
We will proceed to our Demobank, where we will go through the registration process to get started, namely, we will form a request for a certificate .
Choose from the list of connected PINPad devices:

We will invent a login:

The request is displayed on the screen and, if we agree, click on the check mark and enter the PIN code:


Now authorization . We choose our certificate, we look at the screen with what certificate is the entrance and at what address.

We agree and enter the PIN-code on the device for authorization:

Note that registration and authentication occur by signing random data on the device in the CMS format with the request displayed on the device screen.
In the Demobank there is a white list implementation in which the contractors are listed, with whom we constantly work and trust them completely.

What does the exclamation mark mean for billing? In this case, a visual confirmation of payment for non-white list respondents and a payment confirmation with an amount in excess of 100,000 rubles have been implemented. Such payments require visualization and additional confirmation with the help of Rutoken PINPad.

If we make a mass payment of 4 payments, two of them, not marked with an exclamation mark, will be signed without visualization, and the other two will be displayed on the screen of PINPad:

In the case of a substitution of the payment document by the attacker, on the device screen, we notice incorrect details and reject the payment:

If everything is OK, then we sign the payment order, a signature is formed, then all data is encrypted and sent to the server:

After viewing and confirming the generated signature in the CMS format:


Note that, depending on the security policy chosen, it is possible to cache the PIN during authorization and use this cache in the session without requesting the PIN during each operation.
To conclude:
The presented solution is able to maximally protect user accounts from various types of threats, including those related to remote control and document substitution. PINPad also allows you to make secure mass payments, organize incident investigation.
Currently, Rutoken PINPad is being supported in the most common RBS systems and a number of banks.
Source: https://habr.com/ru/post/216087/
All Articles