Chameleon virus spreads via WiFi networks as a common cold among people

A group of security researchers at the University of Liverpool in the United Kingdom provided proof of the concept of infecting WiFi networks at one stroke.
Researchers demonstrated the WiFi virus, which was named Chameleon , which can spread on the network as a “cold” spreads between people. Scientists made it possible to replace the firmware of an access point (Access Point, AP) with an infected version.
Chameleon , in the event of a single access point infecting, propagates itself to the computers connected to it, and searches for new, uninfected Wi-Fi networks, which allows it to spread independently within wireless networks, from point to access point.
Chameleon, is a serious threat to IT security, because the attack scenario uses a WiFi network and the vulnerability lies precisely in the fact that the attack can not be detected by any of the existing protective mechanisms, including antivirus and intrusion detection systems (Wireless intrusion detection system, WIDS).
Thus, this attack is considered the most up-to-date and difficult to detect, since for WIDS, changes in credentials, or traffic, are usually the criteria for detecting an infection by AP.
The spread of the virus is as follows:
1. A list of vulnerable access points in the current location.
2. Performs hacking security encryption on the AP.
3. Bypasses the AP administration interface.
4. A backup copy of the AP configuration is saved.
5. Replaced firmware on vulnerable access points, new firmware, infected with a virus.
6. System settings are restored.
7. The virus multiplies on the connected computers (and again to point 1).
')
To analyze the behavior of the virus, a laboratory experiment was conducted, for which scenarios of the behavior of the virus were modeled in two cities - Belfast (Northern Ireland) and London (England). Their choice is not accidental, as these cities represent a large (London) and medium (Belfast) urban wireless network infrastructure, based on the density of access points.
The following data refer to two regions in which researchers conditionally distributed malware.
Belfast has about 14,553 access points, of which 22% are open, 61% are protected by WPA / WPA 2 encryption and 14% are WEP.
London has about 96,433 access points, of which 24% are open, 48% have WPA / WPA 2 encryption and 19% have WEP.
The infection, starting at random with one of the access points, was able to spread throughout the network through weak access points.
Below is the dynamics of the spread of the virus depending on the radius between the access points:
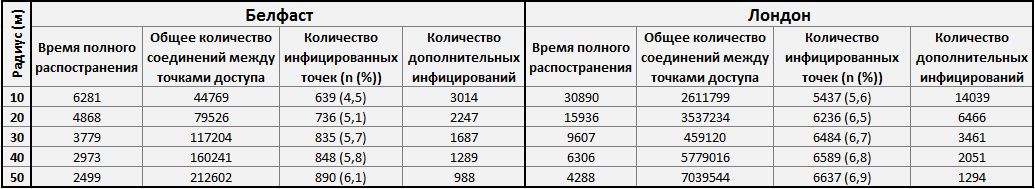
If the model did not change its state for 2 days in a row, the system selected a random access point for additional infection.
This experiment proves that the density of communication between access points is a more important factor in the spread of the virus than vulnerability.
In theory, such geographical areas with high density of access points are more susceptible to infections.
" WiFi connections are becoming a bigger target for hackers because of well-known vulnerabilities that make it difficult to detect and protect against viruses, " says Marshall, one of the authors of Chameleon.

Chameleon progresses rapidly in a completely healthy environment, but it slows down with an increase in the number of infected nodes (this is reflected in the table (the tighter the points, the longer the infection lasts) and on the graph).
The study also presents methods for detecting the Chameleon virus by monitoring Wi-Fi packages. This approach is quite specific, but in any case, it can be adapted to detect malware in the future.
Although Chameleon is just an experimental research product, there is a risk that in the future, cybercriminals will use similar strategies to distribute malicious code.
Research Link - jis.eurasipjournals.com
From the translator : these studies seemed rather vague. It seems that researchers make a bias in practice, but at the same time, the original article provides only a theory, and even then in limited quantities. Afraid to serve as a guide for intruders? So after all, manufacturers of access points also need to fight. Plus, the experiment is quite spherical. It seems to me, opening a new vulnerability of this magnitude, it would be nice to watch it in a “living environment”.
Source: https://habr.com/ru/post/215921/
All Articles