More than 162.000 WordPress sites were used for large-scale DDOS attacks.
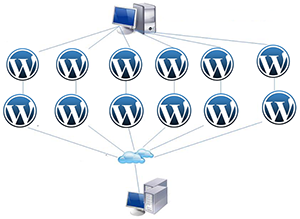 Today I want to tell you about a major DDOS attack, reinforced with the help of thousands of individual sites on the WordPress engine.
Today I want to tell you about a major DDOS attack, reinforced with the help of thousands of individual sites on the WordPress engine.Any WordPress site with Pingback enabled (which, by the way, is enabled by default) can be used in a DDOS attack on other sites. [At the end of the article there is a link to an online service to check your site for already known attacks - note. translator].
Notice, XMLRPC is used for pingbacks, trackbacks, remote access from mobile devices and for many other things that you probably wouldn't want to refuse. But as we shall see, it can be used not only for good purposes.
')
Story
This story happened to the popular WordPress site, which went offline due to the many hours of DDOS attack. When the attack intensified, the hoster turned off their website, and they decided to contact us for help.
After the DNS was moved, we finally saw what was going on: it was a powerful distributed HTTP-flood Layer 7 attack, performing hundreds of requests per second to their server. So these requests looked like:
74.86.132.186 - - [09/Mar/2014:11:05:27 -0400] "GET /?4137049=6431829 HTTP/1.0" 403 0 "-" "WordPress/3.8; http://www.mtbgearreview.com" 121.127.254.2 - - [09/Mar/2014:11:05:27 -0400] "GET /?4758117=5073922 HTTP/1.0" 403 0 "-" "WordPress/3.4.2; http://www.kschunvmo.com" 217.160.253.21 - - [09/Mar/2014:11:05:27 -0400] "GET /?7190851=6824134 HTTP/1.0" 403 0 "-" "WordPress/3.8.1; http://www.intoxzone.fr" 193.197.34.216 - - [09/Mar/2014:11:05:27 -0400] "GET /?3162504=9747583 HTTP/1.0" 403 0 "-" "WordPress/2.9.2; http://www.verwaltungmodern.de" .. You may have noticed that all requests have a random parameter ("? 4137049 = 643182", etc.), due to which requests bypass the cache and require a full page reload each time. All this kills the server very quickly.
But the most interesting thing is that requests come from other noteworthy WordPress sites. Yes, other WordPress sites send a lot of requests with a random parameter and take the victim to offline.
Default unsafe option = very large botnet
In just a few hours, more than 162.000 ordinary WordPress sites attacked their project. Most likely, we would have found more sites, but we decided that we had seen enough and blocked these requests on our firewall, mainly to avoid logging.
One attacker can use thousands of popular non-cracked WordPress sites for DDOS attacks, and at the same time remain in the shadows, and all this is possible thanks to a simple Pingback request to the XML-RPC file:
$ curl -D - "www.anywordpresssite.com/xmlrpc.php" -d '<methodCall><methodName>pingback.ping</methodName><params><param><value><string>http://victim.com</string></value></param><param><value><string>www.anywordpresssite.com/postchosen</string></value></param></params></methodCall>' Yes, a simple Linux command can launch an attack.
Is your website attacking anyone right now?
It may well be, and you have no clue about it. To make sure, check the site logs for the presence of a POST request to the XML-RPC file (see above). If you see a pingback request to a random URL, you will realize that your site is already being used to attack.
93.174.93.72 - - [09/Mar/2014:20:11:34 -0400] "POST /xmlrpc.php HTTP/1.0" 403 4034 "-" "-" "POSTREQUEST:<?xml version=\x221.0\x22 encoding=\x22iso-8859-1\x22?>\x0A<methodCall>\x0A<methodName>pingback.ping</methodName>\x0A<params>\x0A <param>\x0A <value>\x0A <string>http://fastbet99.com/?1698491=8940641</string>\x0A </value>\x0A </param>\x0A <param>\x0A <value>\x0A <string>yoursite.com</string>\x0A </value>\x0A </param>\x0A</params>\x0A</methodCall>\x0A" 94.102.63.238 – - [09/Mar/2014:23:21:01 -0400] "POST /xmlrpc.php HTTP/1.0" 403 4034 "-" "-" "POSTREQUEST:\x0A\x0Apingback.ping\x0A\x0A \x0A \x0A http://www.guttercleanerlondon.co.uk/?7964015=3863899\x0A \x0A \x0A \x0A \x0A yoursite.com\x0A \x0A \x0A\x0A\x0A" For example, in this case, someone tried to use our site-trap for DDOS fastbet99.com and guttercleanerlondon.co.uk.
To prevent your site from being used in attacks, you need to disable XML-RPC Pingback functionality. The best way is to connect the plugin with the following content:
add_filter( 'xmlrpc_methods', function( $methods ) { unset( $methods['pingback.ping'] ); return $methods; } ); Online service to check your site for vulnerability
Since this is a very common problem, we wrote a small scanner that will check if your site participated in the attacks known to us: WordPress DDOS Scanner
Source: https://habr.com/ru/post/215543/
All Articles