Sound attack
One of the well-known strategies for ensuring the security of a computer network, when one of the network machines is infected with malicious code, is a banal disconnection from the network of such a machine. This effectively prevents the spread of malware to other devices. This technology is called “air-gapping" (air gap). Its essence lies in blocking the possibility of data transmission over the network, including "over the air" via wireless networks. In the absence of a communication channel, the malicious code literally has no way to spread on other cars.
But it was so in the past ... Now the malicious code can spread to neighboring, nearby machines by means of sound waves, writes Finly .

“Air” malicious code is characterized by the ability to transmit code using high-frequency sound in order to destroy nearby machines.
Engin Kirda, a professor at Northeastern University and co-founder of Lastline Inc (a company specializing in malicious codes), says: "Recently, scientists have begun to find evidence of the possibility of air leakage using peripheral devices such as microphones and sound cards."
Yes, exactly: sound like a virus. Computer data cannot be transmitted over the air in its original form, but a computer's sound card is more than enough to transmit malicious code in the form of sound that interacts with other machines. And in this case, the code doesn't care what network the computer is connected to.
')
The diagram below is used in the report of the scientists of the Fraunhofer Institute for Communication, Information Processing and Ergonomics by Michael Hanspach and Michael Goetz about malicious codes that are transmitted through the air ( On Covert Acoustical Mesh Networks in Air ). Even if you disconnect the computer from the network, the malicious code will use the physical environment of the machines for distribution.
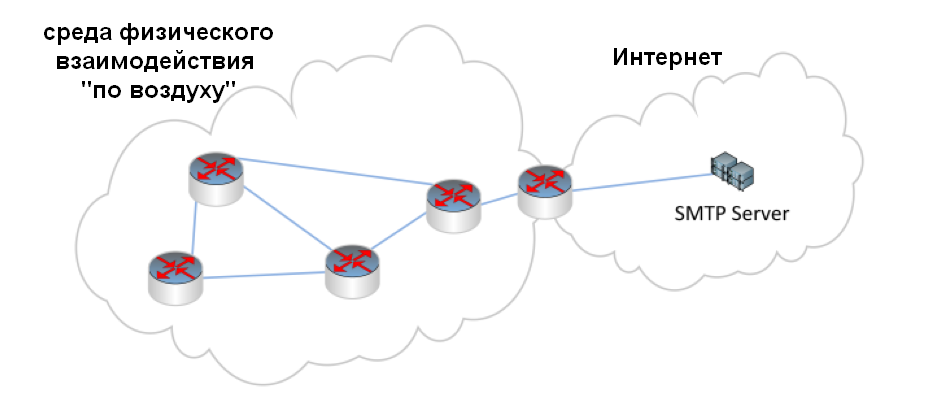
It is not completely known where this technology originates from, but the idea that sound can leak or disclose information from a computer is not new. And it is not at all necessary that the car had any modern technologies. Studies have shown that even the matrix printer sounds can be used to change the content that is being printed. However, the innovation is precisely the use of the program code of this data transmission technology through high-frequency sound.
Should we worry?
For ordinary users, so far there is no threat because According to Professor Kird: "This method of transmitting malicious code is far from trivial ... The level of training of an attacker must be very high in order to crank up something like that." At the moment there is no proven way to actively protect against such attacks. But the methods used in “air attack” are very complex and can only be organized by a very experienced hacker. In other words, this is not the type of malicious code that you can accidentally pick up by installing some kind of ordinary software. This is most likely the case when you can become the specific goal of a very experienced attacker. You can find more books and documentation about network security here .
Original Bisiness Insider .
In the comments I would very much like to hear the opinions of habrovchan, which are directly related to the field of information security.
Source: https://habr.com/ru/post/214915/
All Articles