3G / 4G Access Network Security
Backhaul network is a network for connecting base stations (in 3G terminology, NodeB) to radio network controllers (RNC).

The cost of connecting base stations is one of the significant components of the operator's costs, so the costs associated with the construction and operation of these networks are trying to reduce, in particular, using new technologies. Evolution has gone from ATM connections to SDH / SONET, DSL, IP / MPLS and metro Ethernet. Today all traffic goes in IP packets.
')
As a result, when a large metro network is built, it is a pity to use it only to connect base stations, so it also provides channels to legal entities and, in some places, broadband Internet access to home users. Normal converged network. And in converged networks, security is always an issue.

Mobile voice and GPRS packet data in the network segment between the NodeB and the RNC are transmitted in encrypted form. But what about traffic control, which protocols are used directly to control the NodeB? All manufacturers have different ways: it can be either HTTP / HTTPS, Telnet / SSH, or different MML (man-machine language) variants.
Unfortunately, protocols that transmit data in unencrypted form are often used to control network elements.

What happens if an attacker gains access to this network segment? Can he intercept the data? How will he do it?
Today, all devices have an IP management interface and an Ethernet port for connecting to the network. Base stations are no exception.
Once in the network, an attacker using a banal ARP spoofing can intercept the credentials used by technicians to control network devices.
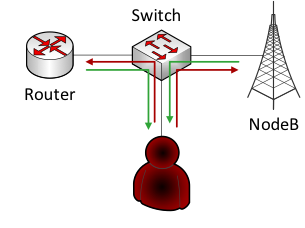
An example of an MML session shows how simple it is.

If you go further, it will become clear: this is very bad. By gaining access to one base station, you can access the others, since the control IP addresses are freely routed, at least within the boundaries of one network.
An important point: the cellular operator has hundreds of base stations in one city. What if the connection with one is lost and you have to go and do work right on the spot? To do this, there is always an account in the local device database, often the same on all devices.
This means that an attacker can take control of hundreds of devices!
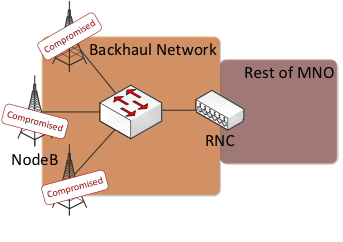
There was a time when the telephone network was an exclusively isolated and controlled system. It seems that today it is not so ... The question is whether telecommunication companies understand this.

Author: Dmitry Kurbatov, Positive Research .

The cost of connecting base stations is one of the significant components of the operator's costs, so the costs associated with the construction and operation of these networks are trying to reduce, in particular, using new technologies. Evolution has gone from ATM connections to SDH / SONET, DSL, IP / MPLS and metro Ethernet. Today all traffic goes in IP packets.
')
As a result, when a large metro network is built, it is a pity to use it only to connect base stations, so it also provides channels to legal entities and, in some places, broadband Internet access to home users. Normal converged network. And in converged networks, security is always an issue.

Mobile voice and GPRS packet data in the network segment between the NodeB and the RNC are transmitted in encrypted form. But what about traffic control, which protocols are used directly to control the NodeB? All manufacturers have different ways: it can be either HTTP / HTTPS, Telnet / SSH, or different MML (man-machine language) variants.
Unfortunately, protocols that transmit data in unencrypted form are often used to control network elements.

What happens if an attacker gains access to this network segment? Can he intercept the data? How will he do it?
Today, all devices have an IP management interface and an Ethernet port for connecting to the network. Base stations are no exception.
Once in the network, an attacker using a banal ARP spoofing can intercept the credentials used by technicians to control network devices.

An example of an MML session shows how simple it is.

If you go further, it will become clear: this is very bad. By gaining access to one base station, you can access the others, since the control IP addresses are freely routed, at least within the boundaries of one network.
An important point: the cellular operator has hundreds of base stations in one city. What if the connection with one is lost and you have to go and do work right on the spot? To do this, there is always an account in the local device database, often the same on all devices.
This means that an attacker can take control of hundreds of devices!

There was a time when the telephone network was an exclusively isolated and controlled system. It seems that today it is not so ... The question is whether telecommunication companies understand this.

Author: Dmitry Kurbatov, Positive Research .
Source: https://habr.com/ru/post/214445/
All Articles