IOS 7 keylogger
The problem of keyloggers for mobile applications is becoming more and more noticeable in the world of mobile devices. It has long been known that jailbroken iOS 7 devices may be vulnerable to keyloggers who record and transmit all your gestures and keystrokes to attackers. Now it concerns and not cracked iOS devices.
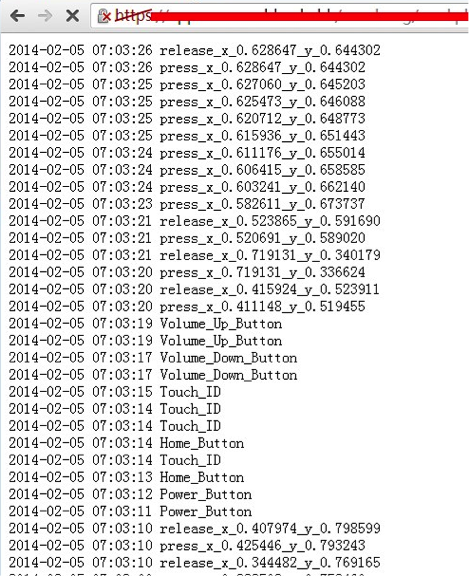
Evidence was presented in a blog by FireEye on the night of Monday, February 24th. The vulnerability is present in versions 7.0.4, 7.0.5, 7.0.6 and 6.1.x. Because of this, it is possible to implement keylogger by phishing or through application vulnerabilities, bypassing the App Store application review system. This vulnerability can record and transmit in the background all sensory gestures, as well as register button presses: “home”, volume rocker and the fact that TouchID is pressed. FireEye has already reported to Apple about this issue.
Users have the opportunity to avoid leakage of personal data. To do this, go to "Settings"> "Basic"> "Update Content" and disable "... in the background, using geolocation services or updating their programs with content ...". Disabling background updates of unnecessary applications helps prevent potential background monitoring. In spite of this, you still have a chance to pick up the keylogger. For example, an application can play music in the background while the content update is turned off in the background. Thus, malicious applications can disguise themselves as a keylogic music application.
')

Before the release of the patch from Apple, FireEye recommend doing the following: close active applications through the application manager:

Apple recently released version 7.0.6 to fix SSL encryption problems used to protect confidential information. Hopefully this vulnerability will be proxy in the next version.

Evidence was presented in a blog by FireEye on the night of Monday, February 24th. The vulnerability is present in versions 7.0.4, 7.0.5, 7.0.6 and 6.1.x. Because of this, it is possible to implement keylogger by phishing or through application vulnerabilities, bypassing the App Store application review system. This vulnerability can record and transmit in the background all sensory gestures, as well as register button presses: “home”, volume rocker and the fact that TouchID is pressed. FireEye has already reported to Apple about this issue.
Users have the opportunity to avoid leakage of personal data. To do this, go to "Settings"> "Basic"> "Update Content" and disable "... in the background, using geolocation services or updating their programs with content ...". Disabling background updates of unnecessary applications helps prevent potential background monitoring. In spite of this, you still have a chance to pick up the keylogger. For example, an application can play music in the background while the content update is turned off in the background. Thus, malicious applications can disguise themselves as a keylogic music application.
')

Before the release of the patch from Apple, FireEye recommend doing the following: close active applications through the application manager:
To view and manipulate active applications, iOS7 users should double-click the home button and drag suspicious and unnecessary applications from the multitasking screen.

Apple recently released version 7.0.6 to fix SSL encryption problems used to protect confidential information. Hopefully this vulnerability will be proxy in the next version.
Source: https://habr.com/ru/post/214327/
All Articles