Vulnerabilities of cryptocontainers with remote attack
Today, crypto containers are used to store confidential information on personal computers of users and in the corporate environment of companies and organizations and can be created using virtually any encryption program. Their wide distribution is primarily due to the convenience of working with encrypted files and the ability to implement "encryption on the fly."
However, not all users realize how vulnerable the files in the crypto-container become after they are connected as a logical disk of the operating system and how easy it is to steal them from there. This was the reason for writing this article, in which, using a concrete example, it will be shown how to steal information placed in a cryptocontainer created using practically cult in Runet (and not only) TrueCrypt encryption program. However, the same is true for any other program that allows you to create cryptocontainers and does not have other additional functions to protect the encrypted data stored in them.

Let's consider the following example. Suppose there is a certain AAA organization, which stores on its server (for which a regular PC is used) valuable information to which several employees of this organization have access. Confidential files are stored in a cryptocontainer created using TrueCrypt. In order to allow employees to access this information to work with it throughout the entire working day, the cryptocontainer is mounted at the beginning (for example, by the system administrator of this organization) and dismantled at the end. The company's management is confident that, since their confidential files are stored in an encrypted form on the cryptocontainer, they are reliably protected.
')
In order to understand what danger threatens this organization, let us briefly present ourselves as a not very honest competing company BBB, who wants to acquire confidential information AAA. You can implement your plan in several stages:
1. Download DarkComet RAT is a hidden remote administration utility that was officially created for legitimate control of a remote system. It is difficult to say how clean the thoughts of Jean-Pierre Lesier, the developer of DarkComet, really were. Perhaps, just as Albert Einstein didn’t imagine that the atomic energy discovered by him would find practical application in the atomic bomb for the first time, he also didn’t assume that its development would soon be effectively used by hackers around the world, and the Syrian government, for example, uses program against the opposition in the Syrian conflict .
DarkComet has many features:
- file manager;
- Manager of open windows, running tasks, active processes;
- management of autoload and services;
- remote registry management;
- the installing and deleting of programms;
- the seizure of control of the remote machine using VNC technology;
- taking screenshots from a remote screen;
- interception of sound from a microphone and video from built-in or external cameras, etc.
Of course, all this allows you to use DarkComet as an excellent spyware program and turns it into a powerful weapon in the hands of cybercriminals. Despite the fact that the creator of DarkComet RAT has decided to close his project, its development can still be freely downloaded from the network.
This is what the main program window looks like:
2. After downloading and installing the program, you will need to create a hosting, on which we will download files from the victim's computer.
3. With the help of DarkComet, we create an exe-file (stub) that will be used to infect the victim's computer ( DarkCometRat> ServerModule> FullEditor ). In Network Settings, we register the previously created host and set other necessary settings (more here ). Or order the creation of such a file on the stock exchange (approximately $ 100).
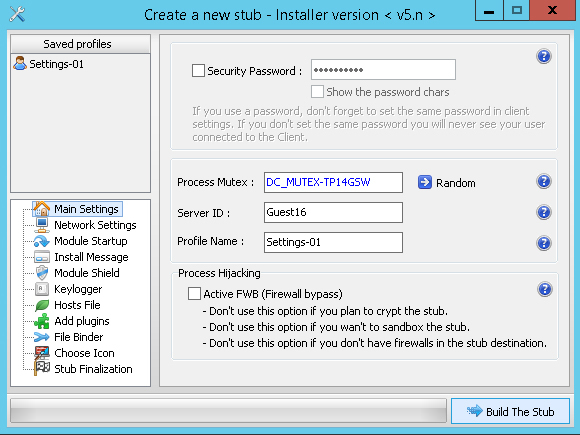
4. Naturally, the executable file created in DarkComet RAT is detected by antivirus software as malware, therefore, in order to successfully infect the victim’s computer, we need to encrypt it using a cryptor (or order it for $ 50-100). With the help of a cryptograph, the source file of the program is encrypted, and its beginning is recorded with a code that, when launched, performs decryption and launch of the main program. Encrypting the program, the cryptor protects it from all the most well-known antiviruses and signature search methods.
5. Make sure that antivirus programs do not regard the encrypted file as a virus. The check can be done on VirusTotal , for example:
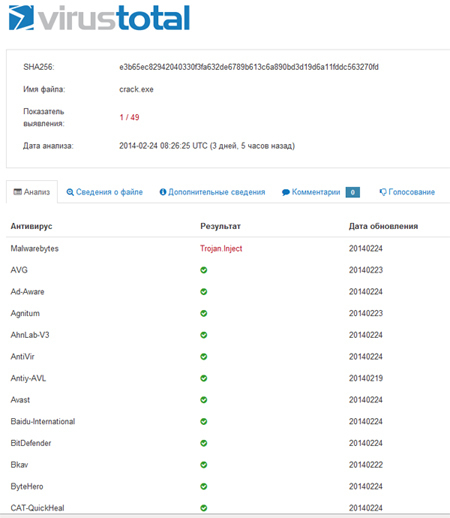
In this article, we do not directly upload the encrypted file so that there are no accusations about the spread of viruses, in particular, from the administration of the Habr. However, if someone has a desire to make sure that at the time of creation, the exe file was not really regarded by antiviruses as a virus, we can give a link to it and you will see for yourself by comparing the hash sums in the video and on the file.
6. Now it is necessary that our virus gets on the victim's computer. There are many different ways to do this.
For example, a computer may be infected by email. During the working day, dozens and even hundreds of emails arrive at the corporate email of employees. Of course, such a flow of correspondence does not allow to give due attention to each letter and the majority of employees treat the processing of such messages as shifting papers from one pile to another, which greatly facilitates the implementation of attacks. When an attacker sends a simple request by mail, his victim very often, on the machine, does what he is asked for without thinking about his actions.
This is just one example. Any other methods of social engineering based on the characteristics of human psychology can be used.
7. As soon as the virus enters the victim’s computer after opening the executable file, the attacker gains full access to the computer being attacked. As you know, any application that accesses an encrypted file located on a connected cryptocontainer receives its copy in decrypted form. The DarkComet file manager will be no exception - with its help you can copy any information from the cryptodisk.

All the files we receive in decrypted form, they are available for reading and editing. After that, you can use them to your advantage. By the way, here is another drawback of cryptocontainers - their large size of hundreds of megabytes, which greatly simplifies the task of the cybercriminal to search for protected files.
That's all. Confidential information is copied and compromised, a competing firm can use it for their own selfish purposes, and the attacked organization does not even suspect that data has been stolen.
More clearly the process of stealing information from a crypto-container TrueCrypt is demonstrated in this video:
Cryptocontainer provides reliable protection of information only when it is disabled (dismantled); at the time of connection (mounting) confidential information from it can be stolen and the attacker will receive it in decrypted form. Therefore, if a cryptocontainer is still used to store valuable data, it should be connected for minimum periods of time and disconnected immediately after completion of the work.
In CyberSafe Files Encryption for added security, we added the System of Trusted Applications , described in detail in this article . The bottom line is that for the folder where encrypted files are stored, CyberSafe additionally assigns a list of trusted programs that can access these files. Accordingly, all other applications will be denied access. Thus, if the DarkComet RAT file manager, another remote administration tool, or any other program that is not included in the trusted group of files accesses the encrypted file, they will not be able to access the protected files.
In the event that CyberSafe is used to encrypt network folders , the files on the server are always stored in encrypted form and are never decrypted on the server side - they are decrypted only on the user side.
However, not all users realize how vulnerable the files in the crypto-container become after they are connected as a logical disk of the operating system and how easy it is to steal them from there. This was the reason for writing this article, in which, using a concrete example, it will be shown how to steal information placed in a cryptocontainer created using practically cult in Runet (and not only) TrueCrypt encryption program. However, the same is true for any other program that allows you to create cryptocontainers and does not have other additional functions to protect the encrypted data stored in them.

Let's consider the following example. Suppose there is a certain AAA organization, which stores on its server (for which a regular PC is used) valuable information to which several employees of this organization have access. Confidential files are stored in a cryptocontainer created using TrueCrypt. In order to allow employees to access this information to work with it throughout the entire working day, the cryptocontainer is mounted at the beginning (for example, by the system administrator of this organization) and dismantled at the end. The company's management is confident that, since their confidential files are stored in an encrypted form on the cryptocontainer, they are reliably protected.
')
In order to understand what danger threatens this organization, let us briefly present ourselves as a not very honest competing company BBB, who wants to acquire confidential information AAA. You can implement your plan in several stages:
1. Download DarkComet RAT is a hidden remote administration utility that was officially created for legitimate control of a remote system. It is difficult to say how clean the thoughts of Jean-Pierre Lesier, the developer of DarkComet, really were. Perhaps, just as Albert Einstein didn’t imagine that the atomic energy discovered by him would find practical application in the atomic bomb for the first time, he also didn’t assume that its development would soon be effectively used by hackers around the world, and the Syrian government, for example, uses program against the opposition in the Syrian conflict .
DarkComet has many features:
- file manager;
- Manager of open windows, running tasks, active processes;
- management of autoload and services;
- remote registry management;
- the installing and deleting of programms;
- the seizure of control of the remote machine using VNC technology;
- taking screenshots from a remote screen;
- interception of sound from a microphone and video from built-in or external cameras, etc.
Of course, all this allows you to use DarkComet as an excellent spyware program and turns it into a powerful weapon in the hands of cybercriminals. Despite the fact that the creator of DarkComet RAT has decided to close his project, its development can still be freely downloaded from the network.
This is what the main program window looks like:

2. After downloading and installing the program, you will need to create a hosting, on which we will download files from the victim's computer.
3. With the help of DarkComet, we create an exe-file (stub) that will be used to infect the victim's computer ( DarkCometRat> ServerModule> FullEditor ). In Network Settings, we register the previously created host and set other necessary settings (more here ). Or order the creation of such a file on the stock exchange (approximately $ 100).

4. Naturally, the executable file created in DarkComet RAT is detected by antivirus software as malware, therefore, in order to successfully infect the victim’s computer, we need to encrypt it using a cryptor (or order it for $ 50-100). With the help of a cryptograph, the source file of the program is encrypted, and its beginning is recorded with a code that, when launched, performs decryption and launch of the main program. Encrypting the program, the cryptor protects it from all the most well-known antiviruses and signature search methods.
5. Make sure that antivirus programs do not regard the encrypted file as a virus. The check can be done on VirusTotal , for example:

In this article, we do not directly upload the encrypted file so that there are no accusations about the spread of viruses, in particular, from the administration of the Habr. However, if someone has a desire to make sure that at the time of creation, the exe file was not really regarded by antiviruses as a virus, we can give a link to it and you will see for yourself by comparing the hash sums in the video and on the file.
6. Now it is necessary that our virus gets on the victim's computer. There are many different ways to do this.
For example, a computer may be infected by email. During the working day, dozens and even hundreds of emails arrive at the corporate email of employees. Of course, such a flow of correspondence does not allow to give due attention to each letter and the majority of employees treat the processing of such messages as shifting papers from one pile to another, which greatly facilitates the implementation of attacks. When an attacker sends a simple request by mail, his victim very often, on the machine, does what he is asked for without thinking about his actions.
This is just one example. Any other methods of social engineering based on the characteristics of human psychology can be used.
7. As soon as the virus enters the victim’s computer after opening the executable file, the attacker gains full access to the computer being attacked. As you know, any application that accesses an encrypted file located on a connected cryptocontainer receives its copy in decrypted form. The DarkComet file manager will be no exception - with its help you can copy any information from the cryptodisk.

All the files we receive in decrypted form, they are available for reading and editing. After that, you can use them to your advantage. By the way, here is another drawback of cryptocontainers - their large size of hundreds of megabytes, which greatly simplifies the task of the cybercriminal to search for protected files.
That's all. Confidential information is copied and compromised, a competing firm can use it for their own selfish purposes, and the attacked organization does not even suspect that data has been stolen.
More clearly the process of stealing information from a crypto-container TrueCrypt is demonstrated in this video:
Conclusion
Cryptocontainer provides reliable protection of information only when it is disabled (dismantled); at the time of connection (mounting) confidential information from it can be stolen and the attacker will receive it in decrypted form. Therefore, if a cryptocontainer is still used to store valuable data, it should be connected for minimum periods of time and disconnected immediately after completion of the work.
Cybersafe
In CyberSafe Files Encryption for added security, we added the System of Trusted Applications , described in detail in this article . The bottom line is that for the folder where encrypted files are stored, CyberSafe additionally assigns a list of trusted programs that can access these files. Accordingly, all other applications will be denied access. Thus, if the DarkComet RAT file manager, another remote administration tool, or any other program that is not included in the trusted group of files accesses the encrypted file, they will not be able to access the protected files.
In the event that CyberSafe is used to encrypt network folders , the files on the server are always stored in encrypted form and are never decrypted on the server side - they are decrypted only on the user side.
Source: https://habr.com/ru/post/214141/
All Articles