Vulnerability of the Flash Player is used to target
At the end of last week, Adobe closed the vulnerability in Flash Player CVE-2014-0502 through the update APSB14-07 . According to FireEye, several public and large private websites were compromised by a malicious iframe and redirected visitors to a web page with an exploit to the 0day vulnerability. Exploit takes advantage of legacy libraries compiled without ASLR support to create stable and portable ROP chains for DEP bypass. In the case of Windows XP, ROP gadgets are configured using msvcrt.dll. In the case of Windows 7, the hxds.dll library is used, which comes in Microsoft Office 2007 & 2010 (see MS13-106 Security Feature Bypass), as well as out-of-date Java 1.6 & 1.7 with msvcr71.dll. For more information on operating these DLLs, see the table .

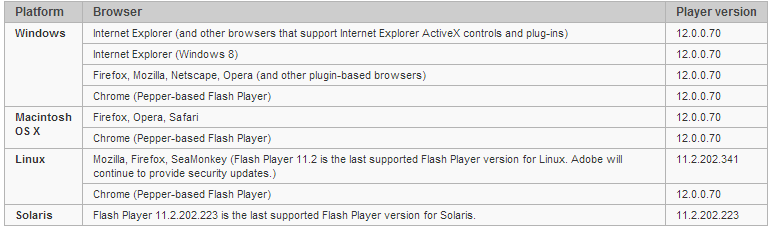
After successful operation, malicious .swf loads the PlugX RAT remote access tool (ESET: Win32 / Korplug.BX , Microsoft: Backdoor: Win32 / Plugx.H ) into the user's system. The exploit itself is detected by ESET as SWF / Exploit.CVE-2014-0502.A (Microsoft: Exploit: SWF / CVE-2014-0502.A , Symantec: Trojan.Swifi ). Browsers such as Internet Explorer (10 & 11 on Windows 8 / 8.1 via Windows Update) and Google Chrome updated their versions of Flash Player automatically. For IE, see the updated Security Advisory 2755801 . Check your version of Flash Player for relevance here , the table below shows these versions for various browsers.
')
The exploit does not contain the ability to bypass the sandbox mechanisms in IE or Chrome. Our usual recommendations in this case:

be secure.

After successful operation, malicious .swf loads the PlugX RAT remote access tool (ESET: Win32 / Korplug.BX , Microsoft: Backdoor: Win32 / Plugx.H ) into the user's system. The exploit itself is detected by ESET as SWF / Exploit.CVE-2014-0502.A (Microsoft: Exploit: SWF / CVE-2014-0502.A , Symantec: Trojan.Swifi ). Browsers such as Internet Explorer (10 & 11 on Windows 8 / 8.1 via Windows Update) and Google Chrome updated their versions of Flash Player automatically. For IE, see the updated Security Advisory 2755801 . Check your version of Flash Player for relevance here , the table below shows these versions for various browsers.
')

The exploit does not contain the ability to bypass the sandbox mechanisms in IE or Chrome. Our usual recommendations in this case:
- Use browsers with sandboxing support.
- Regularly update the software & OC.
- Use EMET or security products with the ability to block and timely detect actions of exploits. Yesterday Microsoft released the 5th version of EMET v5 Technical Preview, which can be downloaded here .

be secure.
Source: https://habr.com/ru/post/213947/
All Articles