SIP Security Essay
The Internet is a great medium for communication. Communicating through letters, chat, voice or video. If video calling is new enough, people have been using the phone for a hundred years. With the laying of new Internet highways and the development of programs like the Internet with balloons, access to the network will soon be even among penguins in Antarctica. And since there is such coverage, why use telephone lines? Why not let the voice on the Internet channels?
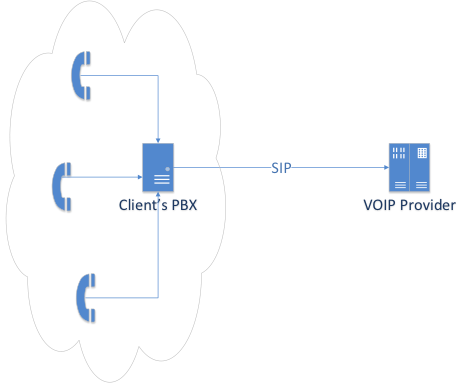
One solution to this problem is the SIP (Session Initiation Protocol) protocol. This is a protocol with an interesting history, but now we will touch only on some of its features. SIP is a session establishment protocol for subsequent data transfer; transmits information in the clear. The data may include subscriber credentials - login, domain, password (in open or hashed form), as well as many other interesting fields. Note that in some cases, authentication may be absent altogether (the connection is configured on both sides as an IP: port pair). Consider several threats that arise when using the SIP protocol, and the ways to implement these threats.
')
Let us turn to the analysis of bad things that can be done using the protocol. Note that for the implementation of some attacks, an attacker must be on the path of traffic from the client to the server (or organize a MITM attack).
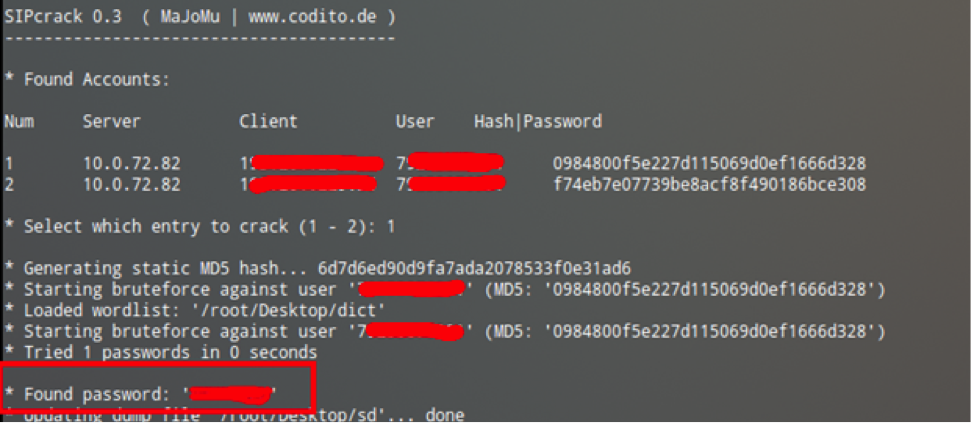
Since the protocol transmits data in the clear, anyone who has the ability to "listen" to traffic coming from us can learn a lot of interesting things. For example, take the authentication process. The password in SIP is hashed using MD5, which, firstly, has long been strongly discouraged from being used anywhere, and secondly, can be picked up (for example, using SIPcrack ). It looks like this:
The obtained credentials can be used in various interesting schemes. If the victim is a Triple Play client, the attacker can gain access to all services the subscriber has subscribed to. What is much more dangerous is that the SIP account obtained can be used in fraudulent schemes with PRS numbers, as well as for running a large number of calls to expensive destinations (the amounts that the subscriber will have to pay for other people's conversations can be very, very significant).
In more detail about selection of the SIP password: www.sipsorcery.com/mainsite/Help/SIPPasswordSecurity
SIP sound itself does not transmit. The real-time transport protocol (RTP) is used to transfer the payload (for example, the audio stream). The protocol is friendly and does not encrypt the transmitted data. Here the question immediately arises: can not a person who is sitting in the middle and “friendly” listen to our traffic - listen to our conversation? Full For example, using Cain , popular in the people, which not only kindly helps to implement the MITM, but also gives you an opportunity to listen to the intercepted conversation. The information thus obtained can obviously be used for the purpose of blackmail or espionage.
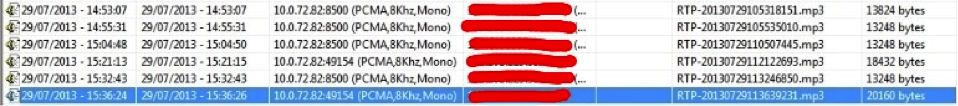
Since the transmitted SIP data is not encrypted, an attacker who has the ability to listen to packets coming from the victim's client can analyze information about calls, including who and when the victim is calling. In the future, this information will be useful, for example, when using social engineering.
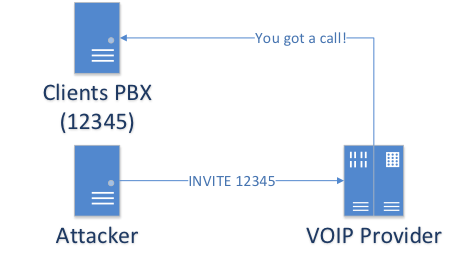
If the client of the victim does not have a white IP address, the attacker who has a public address with him will be able to make calls at the expense of the victim. Such a situation may arise if the Internet provider provides access to the network through NAT, for which, in addition to the legitimate subscriber, there may be a bunch of obscure people.
This is often found in business centers: many small firms go through a local provider’s NAT.
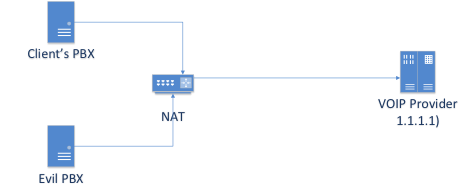
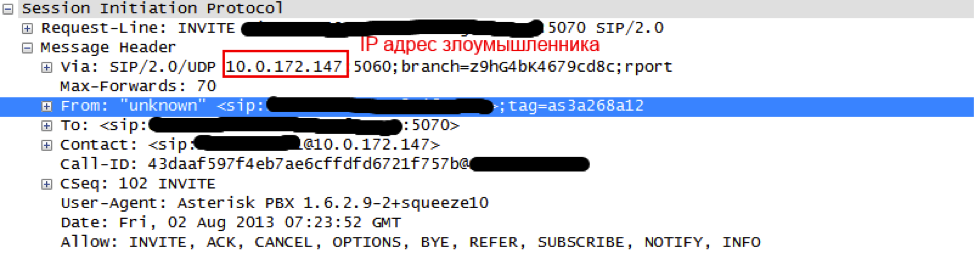
As you can see in the picture, the IP address of the calling party is already in the packet that came to the provider before the broadcast (NAT), but this field is not checked when the connection is established (the white IP address is checked), and there can be both a legitimate subscriber address and address of the attacker.
By attacking a client’s DNS server with a MITM attack or DNS cache poisoning (for example, using a Kaminsky attack ), an attacker can impersonate a provider by sending all calls through his system.
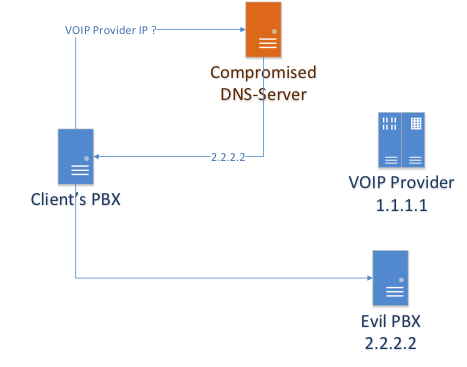
By carrying out an MITM attack, the attacker has the ability to redirect client calls to an arbitrary number, including a non-existent one (leading to DoS).
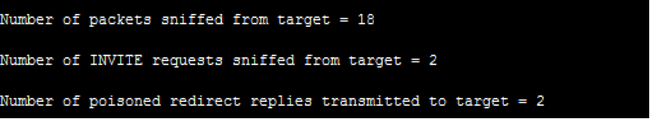
By intercepting INVITE packets, the attacker responds to the request with a packet with code 301 Moved Permanently, redirecting the call.

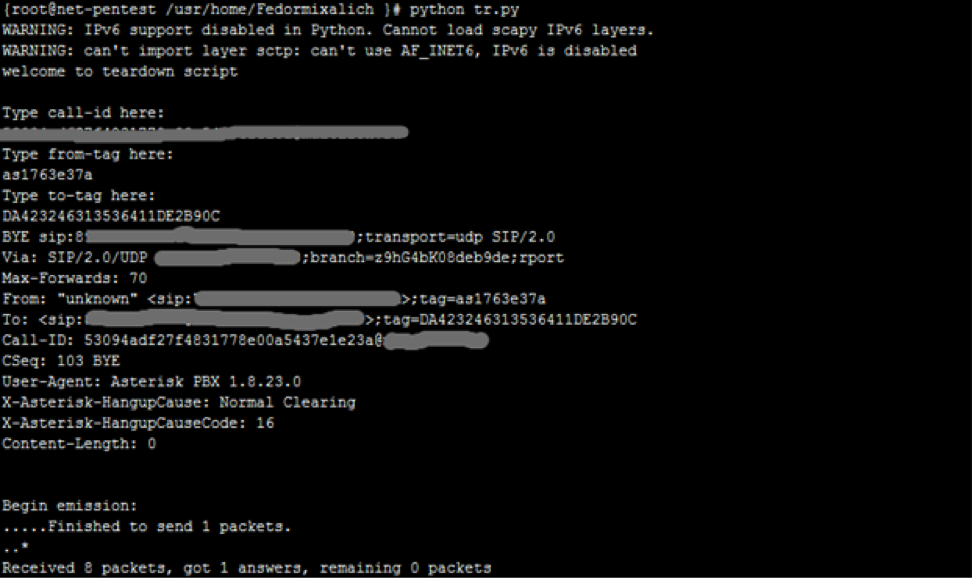
An attacker, knowing or selecting the CallID, FromTag, ToTag, fields, has the ability to terminate active sessions by sending pre-formed malicious packets containing SIP BYE-request, for example, using scapy .

Since SIP uses the UDP protocol most often, various spoofing attacks are possible. For example, you can generate a bunch of requests with a call to the victim subscriber. This leads to a denial of service for the victim’s PBX, paralyzing the entire telephony system.
Unfortunately, despite the fact that there are long-standing methods of protection against most of the listed threats, all market participants - both operators (which is the saddest thing!) And their clients - actively ignore security measures. Therefore, watch your back - the provider will not think for you!
Author : Ilya Safronov.
One solution to this problem is the SIP (Session Initiation Protocol) protocol. This is a protocol with an interesting history, but now we will touch only on some of its features. SIP is a session establishment protocol for subsequent data transfer; transmits information in the clear. The data may include subscriber credentials - login, domain, password (in open or hashed form), as well as many other interesting fields. Note that in some cases, authentication may be absent altogether (the connection is configured on both sides as an IP: port pair). Consider several threats that arise when using the SIP protocol, and the ways to implement these threats.

')
Threats
Let us turn to the analysis of bad things that can be done using the protocol. Note that for the implementation of some attacks, an attacker must be on the path of traffic from the client to the server (or organize a MITM attack).
Identity theft
Since the protocol transmits data in the clear, anyone who has the ability to "listen" to traffic coming from us can learn a lot of interesting things. For example, take the authentication process. The password in SIP is hashed using MD5, which, firstly, has long been strongly discouraged from being used anywhere, and secondly, can be picked up (for example, using SIPcrack ). It looks like this:

The obtained credentials can be used in various interesting schemes. If the victim is a Triple Play client, the attacker can gain access to all services the subscriber has subscribed to. What is much more dangerous is that the SIP account obtained can be used in fraudulent schemes with PRS numbers, as well as for running a large number of calls to expensive destinations (the amounts that the subscriber will have to pay for other people's conversations can be very, very significant).
In more detail about selection of the SIP password: www.sipsorcery.com/mainsite/Help/SIPPasswordSecurity
Wiretap
SIP sound itself does not transmit. The real-time transport protocol (RTP) is used to transfer the payload (for example, the audio stream). The protocol is friendly and does not encrypt the transmitted data. Here the question immediately arises: can not a person who is sitting in the middle and “friendly” listen to our traffic - listen to our conversation? Full For example, using Cain , popular in the people, which not only kindly helps to implement the MITM, but also gives you an opportunity to listen to the intercepted conversation. The information thus obtained can obviously be used for the purpose of blackmail or espionage.

Call tracking
Since the transmitted SIP data is not encrypted, an attacker who has the ability to listen to packets coming from the victim's client can analyze information about calls, including who and when the victim is calling. In the future, this information will be useful, for example, when using social engineering.
NAT attack
If the client of the victim does not have a white IP address, the attacker who has a public address with him will be able to make calls at the expense of the victim. Such a situation may arise if the Internet provider provides access to the network through NAT, for which, in addition to the legitimate subscriber, there may be a bunch of obscure people.
This is often found in business centers: many small firms go through a local provider’s NAT.


As you can see in the picture, the IP address of the calling party is already in the packet that came to the provider before the broadcast (NAT), but this field is not checked when the connection is established (the white IP address is checked), and there can be both a legitimate subscriber address and address of the attacker.
Issuing yourself as a provider (using DNS)
By attacking a client’s DNS server with a MITM attack or DNS cache poisoning (for example, using a Kaminsky attack ), an attacker can impersonate a provider by sending all calls through his system.

Call Forwarding
By carrying out an MITM attack, the attacker has the ability to redirect client calls to an arbitrary number, including a non-existent one (leading to DoS).

By intercepting INVITE packets, the attacker responds to the request with a packet with code 301 Moved Permanently, redirecting the call.

Disconnection
An attacker, knowing or selecting the CallID, FromTag, ToTag, fields, has the ability to terminate active sessions by sending pre-formed malicious packets containing SIP BYE-request, for example, using scapy .


Fake calls
Since SIP uses the UDP protocol most often, various spoofing attacks are possible. For example, you can generate a bunch of requests with a call to the victim subscriber. This leads to a denial of service for the victim’s PBX, paralyzing the entire telephony system.

Conclusion
Unfortunately, despite the fact that there are long-standing methods of protection against most of the listed threats, all market participants - both operators (which is the saddest thing!) And their clients - actively ignore security measures. Therefore, watch your back - the provider will not think for you!
Author : Ilya Safronov.
Source: https://habr.com/ru/post/212839/
All Articles