Openness API Telegram

Security correspondence has already become a widely discussed topic . As you know, Telegram written by Petersburgers is widely known in this field. The team says 146% security, but if you have already used this messenger, you should know that at least the names of your chats are already compromised. At the time of publication, the vulnerability is already closed (which is nice, closed less than fifteen minutes after the report).
Since the API is available to everyone, in addition to the official versions for apples and robots, there are a number of third-party clients . In this case, I researched a semi-official webogram - a web version of a telegram based on JavaScript. Why semi-official? Because despite the unofficial status, his ex-employee of the VC, Igor Zhukov , writes to whom I later wrote about vulnerability, he also has a bearing on the telegram.
So, when we open a conversation, we see the following kind of url:
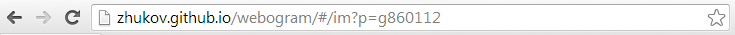
What comes first to mind? Right! We change strange tsiferki for others and a miracle happens here:
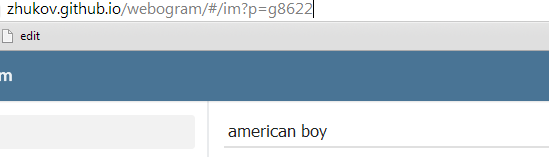
')
Yes, that's right, incredible, we see the name of someone else's conversation. And this is in the “most protected” messenger!
Well, still playing with tsiferki we can get acquainted with the cultures of distant countries:
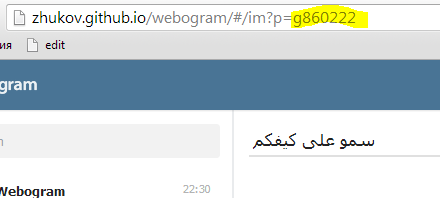
And a little less distant:
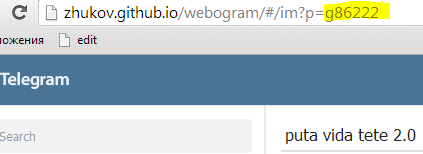
This was quite enough to understand that there is a problem. I immediately wrote a report.
The answer came in just three minutes:
Repaired, surprisingly, just ten minutes:

Security is great. And, of course, I also wish telegram developers all the best. But, as we see, now there are still no safe and time-tested similar solutions. Trust no one.
UPD Igor Zhukov is currently not working in VC, thanks for the hint TakeThat
Source: https://habr.com/ru/post/212245/
All Articles