The service approach of publishing or transmitting data is strictly not earlier than the specified date and / or only in a certain geolocation
Hello,
I want to discuss with you the concept of the service of publishing or transmitting data strictly not earlier than the specified date and / or only in a certain geolocation. I am waiting for any (except for obvious ) criticism and pro-emotionally remarks (fears, experiences, unexpected cases, etc.). This is primarily an approach, but further, for simplicity, I will call it a service.
At the root of the service architecture, with a pent-up distrust of all intermediaries, is encryption of the source data, splitting into the largest possible number of pieces (meaning nothing by themselves) and their subsequent “spraying” on participants. With a sufficiently large number of participants, a variety of operating systems, devices, and jurisdictions, attempts to intervene will be either meaningless or noticeable enough to take appropriate measures locally.
')
With the most stringent settings, the control over the impact of “pieces” (hereinafter iprates - information particles ) is architecturally on the devices themselves, in other words, “I will not give it, it is still early”.
Illustration of the approach:
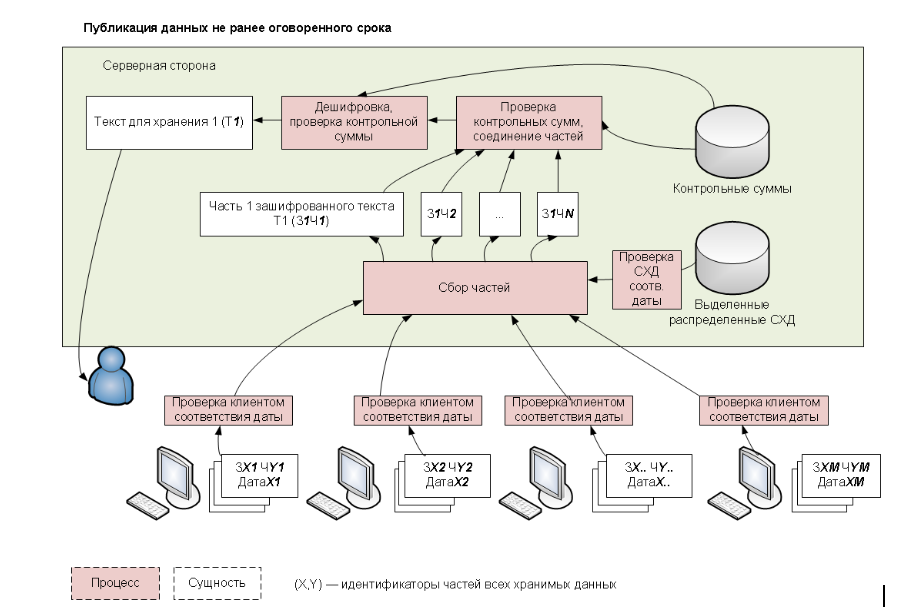
Before listing the scenarios, for clarity, I would like to mention the possible criteria for controlling the subsequent transfer of data to the service before leaving - service, date, geolocation and the list of recipients, including “for all”.
Despite the fact that there is both motivation and best practices and experience in project management, the project is too voluminous and sensitive to the way and time of the announcement and public promises to be limited to free time. In addition, after a brief reflection, it is more important for me that it is generally heard, understood and in demand. And the purpose of this post is to first of all tell about this approach and get your opinion. And if there is interest and like-minded people: applied mathematicians, developers, information security specialists, then it is a matter of time to translate into English, record a video and go to Boom- or Kickstarter with illustrations and an openvisor repository.
I want to discuss with you the concept of the service of publishing or transmitting data strictly not earlier than the specified date and / or only in a certain geolocation. I am waiting for any (except for obvious ) criticism and pro-emotionally remarks (fears, experiences, unexpected cases, etc.). This is primarily an approach, but further, for simplicity, I will call it a service.
I'm not paranoid - what made me think about it
I live in a non-native city for a long time. Having accumulated some capital, including social capital, at some point I realized that a lot of information that was essential for friends and relatives would have disappeared nowhere if I could not tell about it for one reason or another. This is not only the keys to important social services, but also information about the accounts, which, because of the limited insurance part, were scattered across several banks. And, perhaps most importantly, what I have always wanted to say, but did not say, because of the possible distortion of the current context, by possible consequences. I developed this thought.
I looked for tools and solutions, considered deferred sending, pre-encryption with a known key, ready-made services — but they were either too narrowly specialized, or too cumbersome, or did not respond to reasonable distrust of the human factor.
I felt the approach two years ago, but after discussing with friends and for reasons of political commitment, I abandoned it - it would have remained in my drafts if it were not for recent events and changing views on the transfer and interpretation of knowledge between generations. I am sure that a relatively short lifespan is the last obstacle to a truly impressive leap towards technological singularity. Therefore, the transfer of knowledge, devoid of unnecessary emotional experiences, paradoxical attempts to protect through concealment and without replacing the true causes of the incident - the necessary crutch. Or in another way - another step in the transition from the post-industrial society to the information one.
Access to information should not be a matter of influence, fear or whim. It must be a matter of time.
I looked for tools and solutions, considered deferred sending, pre-encryption with a known key, ready-made services — but they were either too narrowly specialized, or too cumbersome, or did not respond to reasonable distrust of the human factor.
I felt the approach two years ago, but after discussing with friends and for reasons of political commitment, I abandoned it - it would have remained in my drafts if it were not for recent events and changing views on the transfer and interpretation of knowledge between generations. I am sure that a relatively short lifespan is the last obstacle to a truly impressive leap towards technological singularity. Therefore, the transfer of knowledge, devoid of unnecessary emotional experiences, paradoxical attempts to protect through concealment and without replacing the true causes of the incident - the necessary crutch. Or in another way - another step in the transition from the post-industrial society to the information one.
Access to information should not be a matter of influence, fear or whim. It must be a matter of time.
At the root of the service architecture, with a pent-up distrust of all intermediaries, is encryption of the source data, splitting into the largest possible number of pieces (meaning nothing by themselves) and their subsequent “spraying” on participants. With a sufficiently large number of participants, a variety of operating systems, devices, and jurisdictions, attempts to intervene will be either meaningless or noticeable enough to take appropriate measures locally.
')
With the most stringent settings, the control over the impact of “pieces” (hereinafter iprates - information particles ) is architecturally on the devices themselves, in other words, “I will not give it, it is still early”.
Illustration of the approach:

Before listing the scenarios, for clarity, I would like to mention the possible criteria for controlling the subsequent transfer of data to the service before leaving - service, date, geolocation and the list of recipients, including “for all”.
Usage scenarios:
- Diaries, blogs "in the table"what for?Interest for participants in a deliberately absent broadcast and, if initially desired, the inability to edit / recall. How many times have we copied, limited or even sent to drafts or non-existence something important that we wanted to communicate. Judging by the number of chicken breast recipes in the ribbons - there are people completely devoid of sound self-criticism. But I’m not the only one who, inadmissibly, often takes into account a changed or overly wide audience, or a possible personal rethinking of events by myself in the future. Key events, reactions and decisions should be recorded as is. Not looking at anything at all, but knowing that this is not an eccentric beating of the drum “look - I'm alive”. You will agree that generation after generation, again and again, it strikes the same emotional rake: something is forgotten, and something is deliberately avoided because of painful conclusions or attempts to “save”. No matter how euphorically the story sounds, the genes, the environment and the stages of development go nowhere. Reading exciting fictional novels or outstanding biographies is useful, but reading a true story of the development of your parents without embellishment is a hundred times more useful. To follow or not to follow the described experience - the children themselves will understand on the basis of the new context. But letting, without giving a choice, beating your forehead into the same walls - in my opinion, a manifestation of some neglect and irresponsibility
- Messages to specific people, with certain geocoordinates, in a specified period of time - meaningful use does not occur to the head, unless just for fun for treasures in a modern way
- Digital testament, letters to the future, etc. - it is in one form or another already represented on the Internet, but represented pale. But the spread of the official digital signature of an individual will breathe new life into all of this.
- Psychological discharge is a means of maximally anonymous recognition or expression of feelings of any hue, when you want to say it is irresistible, but you can't
- The use of free space on the disks of personal computers in organizations . In the workplace, users, as a rule, have a lot of unused space, but it stands idle with a fair distrust of each particular PC or their groups. But parts of encrypted archives / backups of medium and lower importance can be easily scattered around, leaving only separate parts on key storage systems. However, this can be achieved without too much shamanism now, by combining encryption and synchronization tools.
Obvious difficulties and approaches to solving them:
- Critical mass of users . Type of recruitment: positioning, marketing, public guarantees / opensource, provided word of mouth by “design”
- The constant presence of compromising agents, “honeypot-on the contrary” and the loss, the rotation of participants. The way to minimize the impact:
- mathematical distribution model, allowing up to 50% of unreliable participants
- development of trust criteria, including a public chain of signed recommendations
- decentralized and anonymous entry points: address transfer of iprates via Tor / DHT-p2p
- iprates affiliation - each of them only knows neighbors (left / right or, in the case of a three-dimensional representation of the source data, also up-down)An example of course iprates in Thrift definitions
struct IprateSelfAwareness { 1: optional string leftIprateUuid, 2: optional Checksum leftIprateCS, 3: optional string rightIprateUuid, 4: optional Checksum rightIprateCS, 5: optional i64 position, } struct Iprate { 1: string uuid, 2: EncodedValue encodedValue, 3: optional Date creationDate, 4: optional Date publishDate, 5: optional string lastPingDate, 6: optional i32 publishIfNoPingCntMonths, 7: optional string tomeUuid, 8: optional IprateSelfAwareness selfAwareness, 9: optional auth.User owner, 10: optional IprateExtra extra }
- Attack on key servers. It makes sense only at the stage of proof-of-concept alpha testing. The admission of decentralized distribution, as well as the absence of obstacles to obtaining raw data "when you can" by anyone else - eliminates the concept of a key server, such a server can raise any
- Obsolescence of technologies and means of cryptography. Except for the mass and local control of the end devices, I did not invent a way to level this risk. Including because it is impossible not to consider the most important risk
Why is it here
Despite the fact that there is both motivation and best practices and experience in project management, the project is too voluminous and sensitive to the way and time of the announcement and public promises to be limited to free time. In addition, after a brief reflection, it is more important for me that it is generally heard, understood and in demand. And the purpose of this post is to first of all tell about this approach and get your opinion. And if there is interest and like-minded people: applied mathematicians, developers, information security specialists, then it is a matter of time to translate into English, record a video and go to Boom- or Kickstarter with illustrations and an open
Source: https://habr.com/ru/post/212141/
All Articles