Microsoft released a set of updates, February 2014
Microsoft has released a series of updates for its products, which close 31 unique vulnerabilities (4 fixes with Critical status and 3 fixes with Important status). The extended vulnerability notification notice released on February 6th did not contain information about updates for the Internet Explorer browser. However, yesterday Microsoft included two critical fixes (Internet Explorer & VBScript flaw) on Patch Tuesday, one of which MS14-010 closes 24 Remote Code Execution (RCE) vulnerabilities in all versions of IE6-11 on WinXP-8.1 x32 / x64. The second MS14-011 fixes the critical RCE vulnerability (VBScript Scripting Engine) in all versions of WinXP-8.1 OS. A reboot is required to apply fixes.

A detailed report on closed vulnerabilities, product components and their versions can be found on the corresponding page of security bulletins. Updates cover vulnerabilities in Windows, Internet Explorer, .NET Framework and Security Software. Note that earlier, last week, MS updated the Flash Player as part of IE10 + through Windows Update to close CVE-2014-0497 (Adobe APSB14-04).
')
Last week we wrote about Pwn2Own 2014, in which participants are invited to remotely execute code through Internet Explorer 11 x64 on Windows 8.1 x64 with EMET enabled, and then elevate their privileges to system ones. One of the security rewriters, 0xdabbad00, indicated in his post that, in reality, the EMET settings are mostly useless in the case of IE10 + x64, since most of them are already included in Windows 8 x64. Thus, in fact, through EMET it is better to protect the 32-bit version of IE (or other similar software).
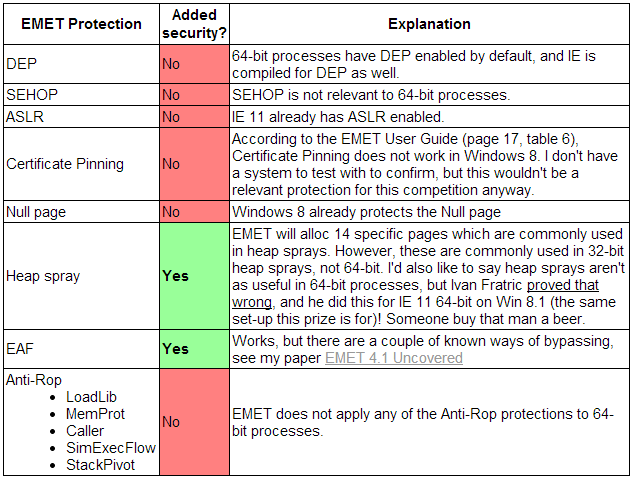
Fig. EMET vs. x64 MS-compiled files on Win8 / 8.1 x64, screenshot from the blog 0xdabbad00 .
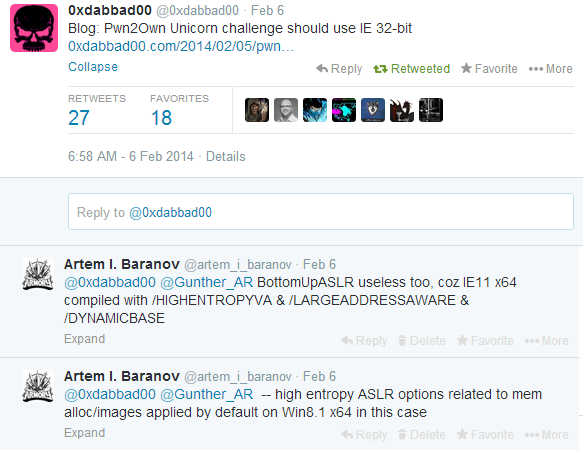
For users, this information does not carry a significant payload, since we still recommend using EMET as a free means of protection against exploits, including on Windows 8+ x64 . To date, not all browsers or software use native 64-bit modules (Google Chrome has sandbox capabilities, but comes only in the 32-bit version, Mozilla Firefox also does not have 64-bit Windows support), not to mention support HEASLR ( / HIGHENTROPYVA).
Microsoft
The MS14-010 update closes 24 vulnerabilities in all versions of Internet Explorer 6-11. Vulnerabilities are of the type Remote Code Execution (memory-corruption) and can be used by attackers for remote code delivery via a specially crafted web page (drive-by). One of the vulnerabilities CVE-2014-0268 can be used by attackers to increase their privileges in the system (Elevation of Privilege). Critical.
Update MS14-011 closes the RCE vulnerability CVE-2014-0271, which is present in all versions of Windows XP - 8.1 x32 / x64. The vulnerability is present in the VBScript engine component (v.5.6 - 5.8) and allows attackers to remotely execute code through a browser (Internet Explorer). Critical. Exploit code would be difficult to build .
Update MS14-007 closes the RCE vulnerability CVE-2014-0263 (memory-corruption) in the Direct2D component on Windows 7 - 8 - 8.1 / RT 8.1. Vulnerability can be used by hackers to remotely deliver code through Internet Explorer. Critical. Exploit code likely .
The MS14-008 update fixes the RCE vulnerability CVE-2014-0294 in the Microsoft Forefront Protection for Exchange 2010 product. Attackers can execute arbitrary code in the system by sending a specially generated mail message (if MS Forefront Protection is active in the system). Critical. Exploit code likely .
The MS14-009 update fixes two vulnerabilities of the Elevation of Privilege type in all versions of the .NET Framework 1.0 SP3 - 4.5.1 component on all WinXP-8.1 OS and one Security Type Bypass vulnerability CVE-2014-0295 (ASLR improvements for vsavb7rt.dll) . Vulnerabilities can be exploited through specially formed web pages, while attackers can upgrade their privileges to system ones. Important. CVE-2014-0295 is operated in-the-wild .
Update MS14-005 fixes one Information Information Disclosure vulnerability CVE-2014-0266 in Microsoft XML Core Services 3.0. Important. Vulnerability is exploited in-the-wild .
Update MS14-006 fixes the CVE-2014-0254 type Denial of Service vulnerability in the TCP / IP Version 6 (IPv6) subsystem, attackers can cause the target system to hang (Windows 8 / RT) by sending a large number of specially crafted IPv6 packets. Important. Exploit code unlikely .
1 - Exploit code likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploit code would be difficult to build
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend our users to install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (by default this option is enabled).

be secure.

A detailed report on closed vulnerabilities, product components and their versions can be found on the corresponding page of security bulletins. Updates cover vulnerabilities in Windows, Internet Explorer, .NET Framework and Security Software. Note that earlier, last week, MS updated the Flash Player as part of IE10 + through Windows Update to close CVE-2014-0497 (Adobe APSB14-04).
')
Last week we wrote about Pwn2Own 2014, in which participants are invited to remotely execute code through Internet Explorer 11 x64 on Windows 8.1 x64 with EMET enabled, and then elevate their privileges to system ones. One of the security rewriters, 0xdabbad00, indicated in his post that, in reality, the EMET settings are mostly useless in the case of IE10 + x64, since most of them are already included in Windows 8 x64. Thus, in fact, through EMET it is better to protect the 32-bit version of IE (or other similar software).

Fig. EMET vs. x64 MS-compiled files on Win8 / 8.1 x64, screenshot from the blog 0xdabbad00 .

For users, this information does not carry a significant payload, since we still recommend using EMET as a free means of protection against exploits, including on Windows 8+ x64 . To date, not all browsers or software use native 64-bit modules (Google Chrome has sandbox capabilities, but comes only in the 32-bit version, Mozilla Firefox also does not have 64-bit Windows support), not to mention support HEASLR ( / HIGHENTROPYVA).
February 11 is the Internet for 2014. This year, we’re online. While I’m suggesting that I’ve been reading this, I’m guessing that I’m reading my opinion. The version of the Enhanced Mitigation Experience Toolkit (EMET).
Microsoft
The MS14-010 update closes 24 vulnerabilities in all versions of Internet Explorer 6-11. Vulnerabilities are of the type Remote Code Execution (memory-corruption) and can be used by attackers for remote code delivery via a specially crafted web page (drive-by). One of the vulnerabilities CVE-2014-0268 can be used by attackers to increase their privileges in the system (Elevation of Privilege). Critical.
Update MS14-011 closes the RCE vulnerability CVE-2014-0271, which is present in all versions of Windows XP - 8.1 x32 / x64. The vulnerability is present in the VBScript engine component (v.5.6 - 5.8) and allows attackers to remotely execute code through a browser (Internet Explorer). Critical. Exploit code would be difficult to build .
Update MS14-007 closes the RCE vulnerability CVE-2014-0263 (memory-corruption) in the Direct2D component on Windows 7 - 8 - 8.1 / RT 8.1. Vulnerability can be used by hackers to remotely deliver code through Internet Explorer. Critical. Exploit code likely .
The MS14-008 update fixes the RCE vulnerability CVE-2014-0294 in the Microsoft Forefront Protection for Exchange 2010 product. Attackers can execute arbitrary code in the system by sending a specially generated mail message (if MS Forefront Protection is active in the system). Critical. Exploit code likely .
The MS14-009 update fixes two vulnerabilities of the Elevation of Privilege type in all versions of the .NET Framework 1.0 SP3 - 4.5.1 component on all WinXP-8.1 OS and one Security Type Bypass vulnerability CVE-2014-0295 (ASLR improvements for vsavb7rt.dll) . Vulnerabilities can be exploited through specially formed web pages, while attackers can upgrade their privileges to system ones. Important. CVE-2014-0295 is operated in-the-wild .
Update MS14-005 fixes one Information Information Disclosure vulnerability CVE-2014-0266 in Microsoft XML Core Services 3.0. Important. Vulnerability is exploited in-the-wild .
Update MS14-006 fixes the CVE-2014-0254 type Denial of Service vulnerability in the TCP / IP Version 6 (IPv6) subsystem, attackers can cause the target system to hang (Windows 8 / RT) by sending a large number of specially crafted IPv6 packets. Important. Exploit code unlikely .
1 - Exploit code likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploit code would be difficult to build
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend our users to install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (by default this option is enabled).

be secure.
Source: https://habr.com/ru/post/212037/
All Articles