HP will pay a record $ 150K for an exploit at Pwn2Own 2014
Recently, HP announced information about the upcoming Pwn2Own contest and its rules. Traditionally, Pwn2Own is a competition for security writers or teams, where you can demonstrate the work of exploits for software vulnerabilities and make good money on it. As a test, participants are invited to remotely execute the code either directly through a vulnerability in the latest version of one of the browsers, or through a vulnerability in one of the plug-ins to it (Remote Code Execution).

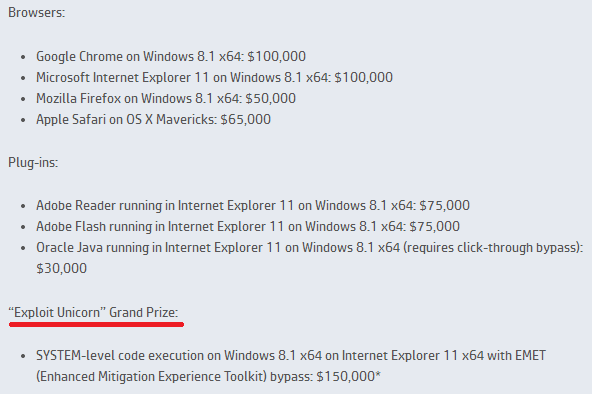
This year the contest organizers prepared a special big fee for the so-called. "Exploit Unicorn". Participants are invited to demonstrate the work of the exploit, which can be used to remotely execute code in the latest Internet Explorer 11 x64 browser on Windows 8.1 x64 and then increase their privileges in the system (Local Privilege Escalation, LPE), i.e. to run their code in kernels bypassing OS (user-mode restrictions). At the same time, MS EMET must be active in the operating system. The attack on the system must be carried out using two vulnerabilities, one RCE vulnerability in the browser for remote code execution and another in the OS component to go beyond the sandbox (aka IE11 EPM) . Both exploits must work with EMET enabled.
')
The operating software and OS will be delivered with the latest updates, i.e. up-to-date. Introduced vulnerability must be previously unknown - 0day.
We have repeatedly written (see links above) about the new security capabilities of IE11 and about EMET. In the case of Exploit Unicorn, we are talking about the most secure mode of operation of the Internet Explorer 11 x64 browser on Windows 8.1 x64, because there it can reveal its full potential, unlike, for example, its use on Windows 7. At the same time, it is completely clear whether the Enhanced Protected Mode (EPM) and 64-bit processes tabs modes are included in the test browser configuration and OS. EPM on Windows 8.1 x64 makes IE11 x64 launch its tabs in full sandboxing isolation mode (AppContainer), and the 64-bit configuration tabs setting includes using 64-bit processes for browser tabs (otherwise they work in the context of 32-bit processes that facilitates heap spray for attackers).
At last year's Pwn2Own, researchers from MWR Labs demonstrated an approach similar to Exploit Unicorn, but then Google Chrome was used, which has only version x32 and EMET was not present on the system (Windows 7 x32). RCE in Chrome was performed using a vulnerability in the browser, and privilege escalation through a closed MS13-053 vulnerability in Win32k (Google Chrome full sandbox bypass w / win32k, WebKit / Blink flaws via CVE-2013-0912, CVE-2013-1300).

This year the contest organizers prepared a special big fee for the so-called. "Exploit Unicorn". Participants are invited to demonstrate the work of the exploit, which can be used to remotely execute code in the latest Internet Explorer 11 x64 browser on Windows 8.1 x64 and then increase their privileges in the system (Local Privilege Escalation, LPE), i.e. to run their code in kernels bypassing OS (user-mode restrictions). At the same time, MS EMET must be active in the operating system. The attack on the system must be carried out using two vulnerabilities, one RCE vulnerability in the browser for remote code execution and another in the OS component to go beyond the sandbox (aka IE11 EPM) . Both exploits must work with EMET enabled.
')

The operating software and OS will be delivered with the latest updates, i.e. up-to-date. Introduced vulnerability must be previously unknown - 0day.
It will be installed in its default configurations (Windows 8.1 x64 and OS X Mavericks).
We have repeatedly written (see links above) about the new security capabilities of IE11 and about EMET. In the case of Exploit Unicorn, we are talking about the most secure mode of operation of the Internet Explorer 11 x64 browser on Windows 8.1 x64, because there it can reveal its full potential, unlike, for example, its use on Windows 7. At the same time, it is completely clear whether the Enhanced Protected Mode (EPM) and 64-bit processes tabs modes are included in the test browser configuration and OS. EPM on Windows 8.1 x64 makes IE11 x64 launch its tabs in full sandboxing isolation mode (AppContainer), and the 64-bit configuration tabs setting includes using 64-bit processes for browser tabs (otherwise they work in the context of 32-bit processes that facilitates heap spray for attackers).
At last year's Pwn2Own, researchers from MWR Labs demonstrated an approach similar to Exploit Unicorn, but then Google Chrome was used, which has only version x32 and EMET was not present on the system (Windows 7 x32). RCE in Chrome was performed using a vulnerability in the browser, and privilege escalation through a closed MS13-053 vulnerability in Win32k (Google Chrome full sandbox bypass w / win32k, WebKit / Blink flaws via CVE-2013-0912, CVE-2013-1300).
Source: https://habr.com/ru/post/211262/
All Articles