OpenWrt + VPNclient for a router with 4mb ROM
Good day, Habr!
Recently, I have a need to provide Internet access to all users of the home network via OpenVPN. Initially, the ancient IBM NetVista 6646-Q1G with Linux Centos 6 was used for these purposes.
He coped with this task well, but, as they say, there is no limit to perfection. I wanted to replace it with something more compact. Initially, the choice fell on the Raspberry Pi Model B , but confused by the price of $ 50, because with the task that he had to perform, the current server successfully coped. I started exploring alternatives. And I found, as it seemed to me, the ideal solution - the router + firmware DD-WRT , which contains the OpenVPN client. Then came the turn of the choice of the router. I stopped at TP-Link WR841N . A database search revealed that DD-WRT supports it.
')
Literally on the same day, the device was purchased and flashed. But here I was disappointed - in the web interface on the VPN tab there was no possibility to configure the OpenVPN client. The google helped to find the cause of this unfairness very quickly: “ OpenVPN is only available (except the Broadcom VPN build.) ”.
As they say the wisest, carefully read thecontract documentation.
Okay, so even more interesting. A quick search for alternative firmware led me to OpenWRT . Its difference from DD-WRT is that it has an opkg package manager with a good repository and the ability to flexibly configure the system to fit your needs. In fact, this is a very lightweight version of linux.
In OpenWRT, OpenVPN could not be configured out of the box - the problem is the same as with DD-WRT. But, thanks to the architecture of this firmware, there was a hope that everything will turn out. Quite a lot of free space was found in tmpfs:
As the name implies, the memory of the router is mounted in / tmp. A few minutes of googling led me to a page with a solution to this issue.
Unfortunately, it didn’t work for me, since after installing the kmod-tun, liblzo and libopenssl packages in the root file system, there is critically little space left. Therefore, it was decided to slightly upgrade this manual. Here's what I got.
1. Connect to the router via ssh and execute the commands:
2. Edit the init script:
3. Copy the configuration file (in our case my.conf), certificates and key into the / etc / openvpn folder.
4. Run openvpn:
If everything went well, then if you run the ifconfig command, you will see a new tun or tap interface. Example:
If the connection is not established, you can try to find the error with the command:
Next, you need to add a network interface and configure the firewall in order to allow client traffic through a VPN. This can be done using the web interface. Examples in the screenshots below:
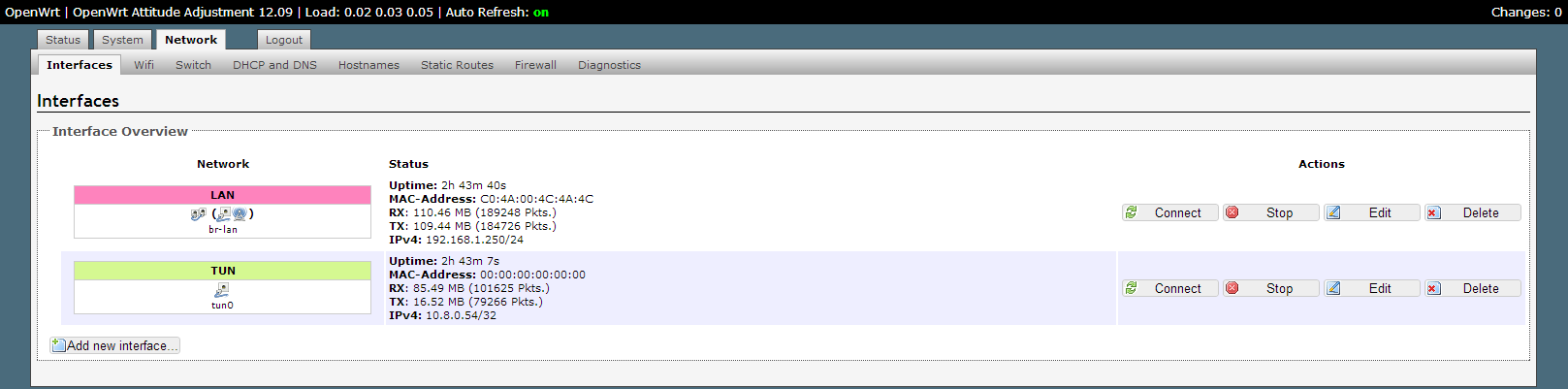
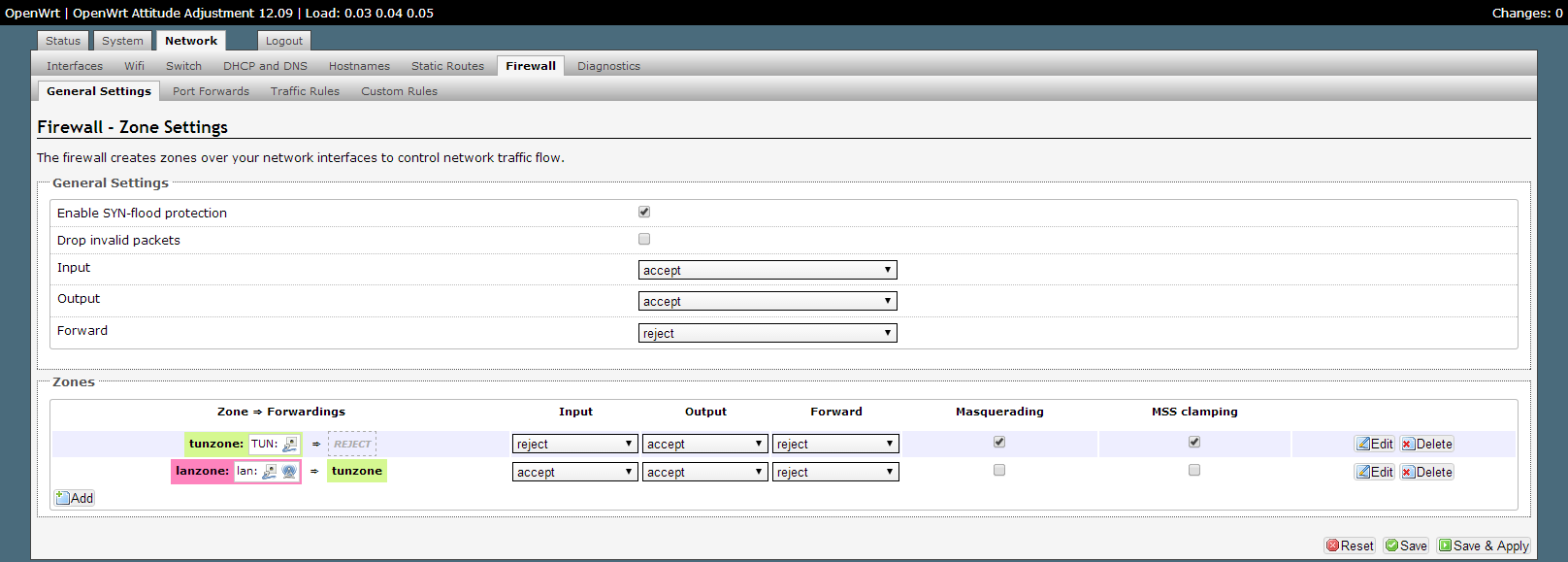
This solution has been successfully tested and works on the TP-Link WR841N router; it is also suitable for other devices supported by OpenWRT that have a ROM of 4 megabytes.
Recently, I have a need to provide Internet access to all users of the home network via OpenVPN. Initially, the ancient IBM NetVista 6646-Q1G with Linux Centos 6 was used for these purposes.
He coped with this task well, but, as they say, there is no limit to perfection. I wanted to replace it with something more compact. Initially, the choice fell on the Raspberry Pi Model B , but confused by the price of $ 50, because with the task that he had to perform, the current server successfully coped. I started exploring alternatives. And I found, as it seemed to me, the ideal solution - the router + firmware DD-WRT , which contains the OpenVPN client. Then came the turn of the choice of the router. I stopped at TP-Link WR841N . A database search revealed that DD-WRT supports it.
')
Literally on the same day, the device was purchased and flashed. But here I was disappointed - in the web interface on the VPN tab there was no possibility to configure the OpenVPN client. The google helped to find the cause of this unfairness very quickly: “ OpenVPN is only available (except the Broadcom VPN build.) ”.
As they say the wisest, carefully read the
Okay, so even more interesting. A quick search for alternative firmware led me to OpenWRT . Its difference from DD-WRT is that it has an opkg package manager with a good repository and the ability to flexibly configure the system to fit your needs. In fact, this is a very lightweight version of linux.
In OpenWRT, OpenVPN could not be configured out of the box - the problem is the same as with DD-WRT. But, thanks to the architecture of this firmware, there was a hope that everything will turn out. Quite a lot of free space was found in tmpfs:
root@OpenWrt:~# df Filesystem 1K-blocks Used Available Use% Mounted on rootfs 1088 352 736 32% / /dev/root 2048 2048 0 100% /rom tmpfs 14608 3256 11352 22% /tmp tmpfs 512 0 512 0% /dev /dev/mtdblock3 1088 352 736 32% /overlay overlayfs:/overlay 1088 352 736 32% / As the name implies, the memory of the router is mounted in / tmp. A few minutes of googling led me to a page with a solution to this issue.
Unfortunately, it didn’t work for me, since after installing the kmod-tun, liblzo and libopenssl packages in the root file system, there is critically little space left. Therefore, it was decided to slightly upgrade this manual. Here's what I got.
1. Connect to the router via ssh and execute the commands:
opkg update opkg install kmod-tun zlib liblzo mkdir /etc/openvpn touch /etc/init.d/openvpn chmod +x /etc/init.d/openvpn 2. Edit the init script:
vi /etc/init.d/openvpn #!/bin/sh /etc/rc.common START=99 start() { local TMPPATH=/tmp/openvpn [ ! -d ${TMPPATH} ] && mkdir ${TMPPATH} cd ${TMPPATH} opkg update || exit 1 tar xzf $(opkg download libopenssl | grep Downloaded | cut -d\ -f4 | sed '$s/.$//') tar xzf data.tar.gz tar xzf $(opkg download openvpn | grep Downloaded | cut -d\ -f4 | sed '$s/.$//') tar xzf data.tar.gz rm -f pkg.tar.gz data.tar.gz control.tar.gz debian-binary getopenvpn.sh for i in $(ls ${TMPPATH}/usr/lib) do [ ! -f /usr/lib/$i ] && ln -s /tmp/openvpn/usr/lib/$i /usr/lib/$i done ${TMPPATH}/usr/sbin/openvpn --writepid /tmp/ovpn_ciberterminal.pid --daemon --cd /etc/openvpn --config my.conf } stop() { PIDOF=$(ps | egrep openvpn | egrep -v grep | awk '{print $1}') kill ${PIDOF} } 3. Copy the configuration file (in our case my.conf), certificates and key into the / etc / openvpn folder.
4. Run openvpn:
/etc/init.d/openvpn start If everything went well, then if you run the ifconfig command, you will see a new tun or tap interface. Example:
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 inet addr:10.8.0.54 PtP:10.8.0.53 Mask:255.255.255.255 UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1 RX packets:100558 errors:0 dropped:0 overruns:0 frame:0 TX packets:78362 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:100 RX bytes:85115045 (81.1 MiB) TX bytes:16184384 (15.4 MiB If the connection is not established, you can try to find the error with the command:
logread -f Next, you need to add a network interface and configure the firewall in order to allow client traffic through a VPN. This can be done using the web interface. Examples in the screenshots below:


This solution has been successfully tested and works on the TP-Link WR841N router; it is also suitable for other devices supported by OpenWRT that have a ROM of 4 megabytes.
Source: https://habr.com/ru/post/211174/
All Articles